Academic Medical Center Vendor Risk Management: Research, Education, and Clinical Challenges
Post Summary
Academic Medical Centers (AMCs) face growing challenges in managing risks tied to vendors across research, education, and clinical care. With thousands of vendor relationships, the stakes are high: data breaches, compliance issues, and operational disruptions can jeopardize patient safety, research funding, and institutional reputation. Here's what you need to know:
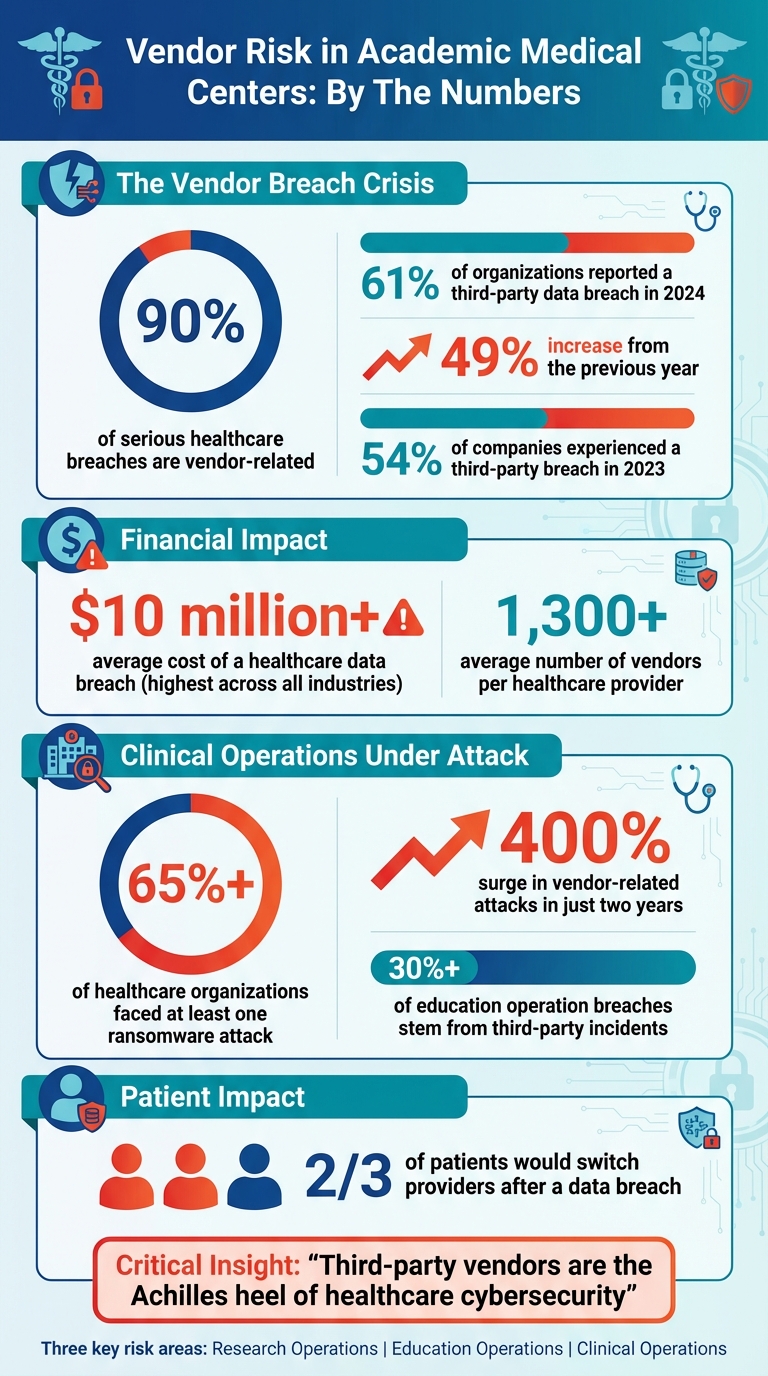
- Research Risks: Vendors handling clinical trials and data analytics often expose sensitive research data and intellectual property. Over 90% of severe healthcare breaches are vendor-related, with the average data breach costing over $10 million.
- Education Risks: Learning management platforms and tele-education tools are vulnerable to breaches, risking student and faculty data. Compliance with FERPA and other regulations adds complexity.
- Clinical Risks: EHR systems and medical device vendors introduce vulnerabilities. Over 65% of healthcare organizations have faced ransomware attacks, often via vendor systems.
Key Takeaways:
- Maintain a complete vendor inventory, including third- and fourth-party relationships.
- Implement continuous monitoring to address evolving risks.
- Use tools like Censinet RiskOps™ for centralized assessments and real-time updates.
Managing vendor risks effectively is critical to protecting sensitive data, ensuring compliance, and supporting AMCs’ missions in patient care, education, and research.
Academic Medical Center Vendor Risk Statistics: Breaches, Costs, and Attack Trends
Vendor Risk Challenges in Research Operations
Academic Medical Centers (AMCs) rely heavily on a wide range of vendors for clinical trials, data analytics, and laboratory supplies. While essential, this reliance also exposes sensitive research data and intellectual property to potential risks. Alarmingly, 90% of serious healthcare breaches are vendor-related, and 55% of healthcare organizations experienced third-party breaches in 2022 [4]. For research-focused AMCs, the stakes are even higher, as these breaches can jeopardize not only patient data but also proprietary research findings, grant-funded projects, and intellectual property that may have taken years to develop.
The financial consequences are equally staggering. The average healthcare data breach costs over $10 million - the highest across all industries [4]. Beyond immediate financial losses, compromised research data can tarnish an AMC's reputation, potentially threatening future funding and partnerships. Recognizing these risks, Duke University has implemented a Service Provider Security Assessment for any external party handling University data, especially "Sensitive" or "Restricted" data. Vendors are required to complete the Higher Education Community Vendor Assessment Toolkit (HECVAT) and provide SOC 2 Type 2 reports [7]. The following sections explore these risks in detail, from gaps in vendor inventories to challenges in safeguarding critical data, all of which demand robust oversight.
Incomplete Vendor Inventories and Fourth-Party Risks
One of the biggest hurdles for AMCs is maintaining a comprehensive view of their vendor networks. On average, healthcare providers work with more than 1,300 vendors [4], and research operations often add hundreds of specialized service providers to this count. The complexity grows when primary vendors outsource work to fourth-party vendors, creating blind spots that can harbor hidden vulnerabilities.
"Assess risk beyond the third party. Consider fourth- and fifth-party relationships, as each layer introduces additional complexity and risk." – AHA Knowledge Exchange [8]
The data highlights this escalating issue: 61% of organizations reported a third-party data breach or cybersecurity incident in 2024, a sharp 49% increase from the previous year [5]. For AMCs engaged in grant-funded research, the risks are even more pronounced. Collaborative projects often involve multiple institutions and vendors sharing data through intricate arrangements. If a research vendor entrusts data storage or analytics to a fourth party with weaker security controls, the AMC remains legally accountable for any resulting breach - even if they were unaware of the fourth party's involvement. This cascading risk underscores the need for meticulous vendor management.
Protecting Research Data and Intellectual Property
Vendors often have access to highly sensitive materials, including clinical trial data, proprietary methodologies, and intellectual property. Unfortunately, many third-party vendors lack the robust security measures typically found within AMCs, making them attractive targets for cybercriminals seeking research data and trade secrets.
"Third-party vendors are the Achilles heel of healthcare cybersecurity." – Intraprise Health [4]
The risks are compounded when vendors are granted excessive access privileges to research systems. An employee with unnecessary permissions could, either accidentally or intentionally, expose years of research. Weak data protection policies, outdated cybersecurity infrastructure, and insufficient cybersecurity training for vendor staff further increase the likelihood of intellectual property theft. A notable example of proactive risk management comes from the Mayo Clinic, which was featured in a 2020 NIST case study for its efforts in managing cyber supply chain risks [6]. This case highlights how forward-thinking strategies can safeguard valuable research assets. However, AMCs remain legally responsible for any vendor-related breaches [4], making the security practices of their vendors an integral part of their own risk management strategy.
Vendor Risk Challenges in Education Operations
Academic Medical Centers (AMCs) face unique vendor risks because they also train future healthcare professionals. Systems like learning management platforms, tele-education tools, and student health services depend heavily on vendors to handle sensitive data. When a vendor fails, the consequences can be severe, including legal repercussions. In fact, over 30% of data breaches in education operations stem from third-party incidents [1].
A disruption in a learning management system or tele-education platform can throw entire coursework schedules, faculty plans, and even accreditation processes into chaos. The situation becomes even trickier with fourth-party risks. For example, if a fourth-party cloud service has weak security measures, it could jeopardize the entire educational tech ecosystem. Because educational technology is so interconnected, a single vendor’s lapse can affect multiple departments and programs. Addressing these risks requires strategies specifically designed for the complexities of education operations.
Protecting Student and Faculty Data
The sensitivity of data in education cannot be overstated. Vendors often handle personal information for students, faculty, and staff, including academic records, financial aid details, health information from student health services, and employment data. Alarmingly, 54% of surveyed companies reported experiencing a third-party breach in 2023 [1].
The risk grows when vendors lack strong internal controls. For instance, a vendor employee with too much access could unintentionally expose thousands of student records. Weak data protection policies, outdated cybersecurity systems, and insufficient training create vulnerabilities that cybercriminals can exploit. When a vendor’s failure leads to a data breach or service disruption, the damage to trust among students, faculty, and the wider academic community can be swift and severe [1]. For AMCs, which compete to attract top medical students and faculty, such reputational damage can directly impact their financial standing.
Meeting FERPA and Other Education Regulations
As with research and clinical operations, maintaining strict vendor oversight in education is essential for regulatory compliance. AMCs operate within a web of regulations, including the Family Educational Rights and Privacy Act (FERPA), which safeguards student education records. Additionally, they must comply with the Gramm-Leach-Bliley Act (GLBA) for financial data, the Payment Card Industry Data Security Standard (PCI DSS) for payment card information, and potentially HIPAA for health information from student health services [10][12][13]. Vendors must navigate these overlapping and sometimes conflicting rules.
Higher education institutions also need to manage third-party risks tied to Federal Trade Commission (FTC) Safeguards and Department of Education requirements [13][14]. Non-compliance can lead to steep penalties, lawsuits, and reputational harm [9][12][15]. If a vendor mishandles sensitive data, the AMC bears the ultimate responsibility [11]. To mitigate these risks, AMCs should thoroughly review vendors’ security practices and require detailed security documentation before granting access to university systems or data [10]. Contracts should include clear confidentiality clauses, require breach notifications within 24 hours, and prohibit vendors from storing or transmitting protected data outside the U.S. without explicit permission [10][14].
Vendor Risk Challenges in Clinical Operations
Managing vendor risks is a critical aspect of clinical operations. Electronic Health Records (EHR) systems, medical device vendors, and supply chain partners play a vital role in delivering patient care, but they also introduce potential vulnerabilities. Disruptions in these systems can lead to delays in care and negatively impact patient outcomes. These risks are not hypothetical - they manifest in tangible disruptions, as illustrated below.
Consider this: Over 65% of healthcare organizations have faced at least one ransomware attack, with vendor systems frequently serving as the weak link [2]. Even more alarming, vendor-related attacks have surged by over 400% in just two years [2]. These incidents not only disrupt patient care but also expose medical records and result in significant financial losses.
Reducing PHI Exposure and Cybersecurity Threats
Protecting Protected Health Information (PHI) is a top priority within clinical settings. PHI flows through various vendor systems, including EHR platforms, imaging services, laboratory systems, and billing services. Under HIPAA, healthcare organizations are legally responsible for ensuring that third-party vendors handle PHI securely [2]. When a vendor's security is breached, the consequences ripple back to the healthcare provider, creating both operational and compliance challenges.
One effective way to address these risks is by implementing modern cybersecurity practices. A Zero Trust framework, combined with Multi-Factor Authentication (MFA), is particularly effective for safeguarding sensitive data, especially in interactions involving EHR software supply chains [2]. The financial fallout from a breach can extend beyond regulatory fines, encompassing forensic investigations, credit monitoring for affected patients, legal expenses, and long-term reputational damage.
Managing Vendor Dependencies and Operational Disruptions
Vendor risk isn’t just about data security - it’s also about maintaining operational continuity. Relying heavily on a single vendor can lead to significant issues, such as EHR downtime, which delays access to critical patient information like histories, medication lists, and treatment plans. In healthcare, these delays can have dire consequences, including postponed procedures, medication errors, and compromised patient outcomes [2].
The problem is further complicated by the lack of quick alternatives when a vendor fails. Switching to a new EHR system or medical device platform requires extensive planning, staff training, and data migration - none of which can be done quickly in an emergency. To address this, healthcare organizations must take a proactive approach to vendor risk management. This includes identifying potential risks, implementing preventative measures, and continuously monitoring for emerging threats [16]. By treating vendor oversight with the same care as patient safety, organizations can reduce vulnerabilities and ensure smoother operations.
sbb-itb-535baee
How Censinet RiskOps™ Simplifies Vendor Risk Management for AMCs
Academic Medical Centers (AMCs) juggle unique challenges when it comes to compliance, data protection, and managing responsibilities across research, education, and clinical care. Tackling these areas separately often leads to inefficiencies, with silos and duplicated efforts slowing progress. That's where Censinet RiskOps™ steps in - streamlining vendor risk management by unifying these processes under one centralized system. This cohesive approach lays the groundwork for advanced tools that simplify assessments and monitoring.
Smarter Assessments with Censinet AITM
Traditional vendor risk assessments can feel like a slog - manually combing through questionnaires, documentation, and risk reports eats up valuable time. Enter Censinet AITM, which takes the heavy lifting off your plate. It automates the process by summarizing security questionnaires, capturing integration details, and identifying fourth-party risks. The result? Comprehensive risk reports without the manual grind, allowing teams to maintain oversight while boosting efficiency.
Real-Time Monitoring and Task Prioritization
Staying ahead of vendor risks requires more than periodic check-ins - it demands constant vigilance. With continuous monitoring, Censinet RiskOps™ provides real-time updates on vendor security. A centralized dashboard brings all risk data together in one place, helping teams quickly identify and address the most pressing issues. This streamlined approach ensures critical risks are handled promptly, keeping operations secure and efficient.
Steps to Build a Vendor Risk Management Program
When developing a vendor risk management program for an AMC (Academic Medical Center), it’s crucial to address the unique demands of research, education, and clinical operations. Understanding who your partners are and the risks they bring to the table helps safeguard sensitive data and ensures compliance with regulations. The foundation of this process? A thorough vendor inventory.
Creating Complete Vendor Inventories
A solid vendor inventory is where it all begins. AMCs must document every third-party connection within their network. This includes everything from cloud storage providers supporting research initiatives to learning management systems managing student information. Once documented, categorize these vendors based on their access levels and how critical they are to operations. Assigning responsibility for maintaining this inventory is equally important - clear ownership ensures each department (research, education, and clinical) remains accountable.
Historical trends highlight the risks that come with overlooking vendors’ sub-processors. Before bringing any new partner on board, conduct a detailed risk assessment. This should cover their security practices, encryption protocols, compliance with regulations, and any history of security incidents. Don’t stop there - carefully review service agreements to confirm they outline system boundaries, data protection measures, and procedures for handling security incidents, especially those involving sub-processors.
"Real visibility and protection must include a complete understanding of every connected asset. Without awareness of every third-party vendor or connection, the attack surface can continue to stretch until something breaks."
Setting Up Continuous Monitoring Frameworks
Inventories alone won’t cut it - vendor risks are constantly changing. While a comprehensive inventory offers essential visibility, continuous monitoring ensures you stay ahead of evolving threats. Real-time monitoring and periodic audits are key. For vendors dealing with sensitive data, like protected health information or research records, more frequent assessments are a must. Use standardized frameworks such as NIST SP 800-53, ISO/IEC 27001, or SOC 2 Trust Services Criteria to maintain consistency in evaluations.
Automation can make this ongoing process more manageable. Tools for vulnerability scanning, real-time threat alerts, and continuous application monitoring can save time and improve accuracy. Keep all contracts, risk assessments, and compliance documents in a centralized, time-stamped repository to simplify audits and promote accountability. Lastly, establish clear incident response plans with predefined escalation paths and communication protocols. This way, your team can act swiftly to contain and mitigate any issues that arise.
Conclusion
Academic Medical Centers (AMCs) face a complex web of vendor-related risks spanning their research, education, and clinical care operations. Each of these areas presents its own challenges - whether it’s safeguarding protected health information, student records, and research data, or ensuring uninterrupted patient care. With thousands of vendor relationships to manage, the stakes are high, especially as breach incidents have surged by 49% year over year [16][5].
The financial and reputational risks are equally daunting. Data breaches can lead to multi-million-dollar expenses and hefty HIPAA penalties [17][3]. More alarming, two-thirds of patients say they would switch healthcare providers after a breach [17], jeopardizing an AMC's reputation and its ability to fulfill its mission. These realities highlight the pressing need for a robust, proactive approach to vendor risk management.
What does effective vendor risk management look like? It starts with maintaining comprehensive vendor inventories, implementing continuous monitoring, and leveraging automated assessments. These measures not only help AMCs identify risks from third and fourth parties but also minimize disruptions to critical operations.
"Without proactive monitoring, our privacy/compliance team was spending countless hours manually investigating alerts." - Blaine Kerr, Chief Privacy Officer, Jackson Health System [3]
As Blaine Kerr points out, proactive monitoring doesn’t just save time - it strengthens compliance and safeguards sensitive data. Vendor risk management needs to be seamlessly integrated into daily workflows across research, education, and clinical departments. It’s not just a compliance checkbox; it’s a foundational element of operational excellence. By fostering a culture of risk awareness and using automation to scale oversight, AMCs can protect critical data, uphold regulatory standards, and ensure the financial stability essential to advancing their missions in research, education, and patient care.
FAQs
What strategies can academic medical centers use to manage vendor risks in research operations?
Academic medical centers can better handle vendor risks in research by conducting thorough risk assessments before bringing vendors on board. This means clearly outlining cybersecurity expectations in contracts and paying special attention to vendors that deal with high-risk or critical tasks.
Using real-time monitoring systems is another key step. These systems allow organizations to keep an eye on vendor performance and quickly spot any potential issues. By also weaving vendors into the center’s overall security framework, sensitive data stays protected, and compliance standards are upheld. Together, these measures help create a proactive and effective strategy for managing third-party risks.
How can academic medical centers safeguard student and faculty data in their educational operations?
Academic medical centers can safeguard sensitive student and faculty data by adopting a few essential measures. Start with thorough risk assessments of vendors to review their cybersecurity practices and confirm they meet strict security requirements. It's also crucial to include specific data protection clauses in vendor contracts to ensure accountability.
Leverage continuous monitoring tools to keep an eye on vendor performance and quickly identify any weaknesses. Clearly define roles and responsibilities within your institution so everyone knows their part in protecting sensitive information. Implementing a vendor risk scoring system can help you focus on vendors that pose higher risks, and having robust offboarding processes ensures sensitive data is securely managed when a vendor relationship ends.
How does Censinet RiskOps™ help academic medical centers manage vendor risks effectively?
Censinet RiskOps™ takes the hassle out of vendor risk management for academic medical centers by automating risk assessments, providing real-time monitoring, and bringing compliance and cybersecurity data into one place. This efficient system is designed to tackle the unique third-party risks faced in healthcare settings.
With its emphasis on automation and ongoing monitoring, Censinet RiskOps™ helps safeguard sensitive data, meet regulatory standards, and reduce operational interruptions. This allows academic medical centers to stay focused on what truly matters - advancing research, educating future professionals, and delivering exceptional patient care.


