Biometric Data Risks in Healthcare: Mitigation Strategies
Post Summary
Biometric data risks include breaches, identity theft, unauthorized access to medical records, and compliance challenges with laws like HIPAA and BIPA.
It protects sensitive patient information, ensures compliance with regulations, and prevents misuse of immutable biometric identifiers like fingerprints or facial scans.
Challenges include securing centralized databases, addressing compliance costs, mitigating authentication errors, and managing vendor risks.
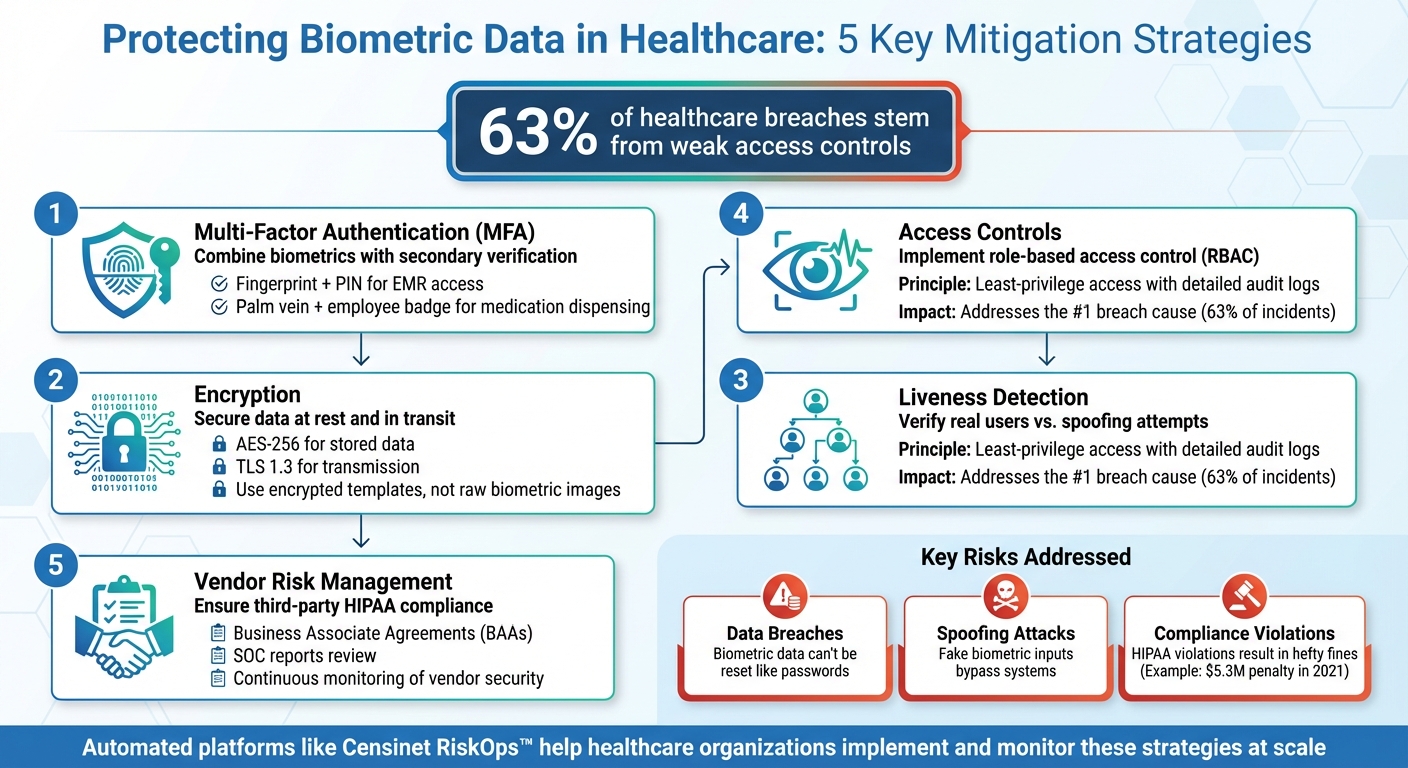
Best practices include implementing encryption (AES-256/TLS), multi-factor authentication (MFA), liveness detection, strict access controls, and vendor risk management.
Compliance can be achieved by adhering to HIPAA’s Security Rule, conducting risk assessments, and implementing safeguards required by laws like BIPA.
Vendors must provide secure systems, comply with regulations, and sign Business Associate Agreements (BAAs) to ensure accountability.
Biometric systems are increasingly used in healthcare for tasks like patient identification, securing health records, and medication safety. While these systems enhance security compared to passwords, they come with risks. Biometric data is permanent, and breaches can lead to identity theft, fraud, and patient safety issues. In 2023, 63% of healthcare breaches stemmed from weak access controls, including vulnerabilities in biometric systems.
Key risks include:
To mitigate these risks:
Healthcare organizations are urged to adopt automated tools like Censinet RiskOps™ for vendor assessments and continuous monitoring to address these challenges effectively.
5 Essential Strategies to Mitigate Biometric Data Risks in Healthcare
Risks of Biometric Data in Healthcare
Healthcare organizations face a range of challenges when handling biometric data, including security threats, privacy concerns, ethical dilemmas, and regulatory compliance issues [2][4]. These risks are deeply interconnected, meaning a single vulnerability can snowball into widespread exposure, potentially jeopardizing patient safety, financial stability, and public trust. Below, we’ll explore some specific attack methods and compliance hurdles tied to biometric data.
Data Breaches and Unauthorized Access
Biometric systems are often praised for enhancing security, but when they’re compromised, the fallout can be severe. Unlike passwords, biometric identifiers - such as fingerprints or iris scans - are permanent and cannot be reset. If attackers gain access to a biometric database, they can use this data to bypass security measures and access clinical applications or patient records [2][3].
The consequences of such breaches go beyond privacy violations. Stolen biometric data can lead to identity theft, fraudulent insurance claims, and even the manipulation of medical histories, which could directly affect treatment outcomes [2][3]. Operationally, compromised systems can disrupt medication dispensing, delay surgeries, or block access to critical care areas, putting patient safety at risk [4][5]. For instance, in 2021, a hospital faced a $5.3 million penalty after failing to secure a biometric-enabled medication system properly [5].
Several factors make protecting biometric data particularly challenging. Common issues include storing raw biometric images instead of encrypted templates, weak encryption during data transmission, outdated sensors, and unpatched mobile apps. Additionally, poorly designed access controls - such as shared accounts or excessive user privileges - compound the risk of breaches [2][4][5].
Spoofing and Replay Attacks
Spoofing attacks occur when an attacker uses fake biometric traits, such as high-resolution images or synthetic samples, to trick sensors into granting access [2][7]. In healthcare, this could target mobile health apps, clinician devices, or access systems for pharmacies, data centers, and operating rooms [2][4]. A successful spoofing attempt might allow unauthorized individuals to enter restricted zones, access patient records, or tamper with medication dispensing systems and connected medical devices [2][4][6]. The risk is especially high for older or budget-friendly devices that lack advanced liveness detection - technology designed to verify that the biometric sample comes from a live person [2][7][9].
Replay attacks present another serious concern. In these cases, attackers intercept biometric data or authentication signals - like a fingerprint template sent from a device to a server - and reuse the captured information to impersonate the original user [2][7]. These attacks exploit weak security measures, such as unprotected communication channels and compromised devices [2][7]. Replay attacks can unlock clinician accounts, breach patient portals, or bypass biometric locks on sensitive areas like medication storage or research labs [2][4][7].
Compliance and Regulatory Challenges
On top of technical vulnerabilities, healthcare organizations must navigate stringent regulatory requirements. Under HIPAA, biometric identifiers linked to health data are classified as protected health information and must comply with both the Security and Privacy Rules [4][5]. Common compliance pitfalls include weak access controls, insufficient encryption of biometric databases, failure to establish Business Associate Agreements with vendors, poor data disposal practices, and inadequate consent and notification processes for biometric data collection [5]. Breaches involving biometric data often lead to hefty fines, corrective action plans, and increased regulatory scrutiny, as these identifiers cannot be changed once compromised [4][5][8].
Transparency and consent are critical but often overlooked aspects of compliance. Patients and staff must be clearly informed about what biometric data is collected, how it will be used, how long it will be stored, and who will have access to it. Failure to provide this information can result in violations of HIPAA transparency rules and state privacy laws [4][5][8]. Healthcare organizations without updated privacy policies for biometric data - such as those used in check-in kiosks or mobile apps - risk facing regulatory investigations and even class-action lawsuits. Several lawsuits have already accused providers of sharing biometric data with third-party vendors without obtaining proper consent [5][8].
Mitigation Strategies for Biometric Data Risks
Protecting biometric data requires a multi-layered approach, combining advanced technical measures, strict access controls, and vigilant oversight of third-party vendors. These steps help ensure compliance with HIPAA and other U.S. regulations while safeguarding sensitive information.
Liveness Detection and Multi-Factor Authentication
Liveness detection is a key tool in biometric security. It confirms that the biometric input comes from a real, living person rather than a replica, using signals like blood flow or pulse to distinguish live users from spoofing attempts. This is particularly relevant in healthcare, where 55% of consumers now rely on biometrics for access [2].
Since biometric identifiers can't be changed like passwords, pairing them with an additional layer of security is essential. Multi-factor authentication (MFA) provides this extra layer by requiring a second verification method, such as a PIN, password, smart card, or mobile token. For instance, accessing an electronic medical record (EMR) might involve both a fingerprint scan and a six-digit PIN, while medication dispensing systems could combine palm vein recognition with an employee badge. This dual-layer approach aligns with HIPAA’s requirement for "reasonable and appropriate" safeguards, reducing risks tied to improper access controls - an issue linked to 63% of healthcare data breaches [5].
Encryption and Secure Data Storage
Encryption plays a critical role in securing biometric data. Healthcare organizations should implement advanced encryption standards like AES-256 for stored data and TLS 1.3 for data in transit. These measures help prevent attackers from intercepting or misusing biometric information. The Office for Civil Rights has frequently highlighted insufficient encryption as a factor in HIPAA violations, emphasizing the need for robust cryptographic protections [5].
Equally important is how biometric data is stored. Instead of retaining raw images or scans, systems should use encrypted biometric templates - mathematical representations created through one-way transformations that cannot be reverse-engineered. Advanced systems may also employ cancelable biometrics, which allow compromised templates to be replaced, addressing the permanent nature of biometric vulnerabilities. Additionally, encryption keys should be securely managed using Hardware Security Modules (HSMs) and rotated regularly. These steps form a strong foundation for access controls and vendor oversight.
Access Controls and Vendor Risk Management
Role-based access control (RBAC) ensures that only authorized individuals can access or manage biometric systems and data. For example, doctors might use patient biometrics for EMR authentication, while nurses have limited access for identity verification during medication dispensing. Given that 63% of healthcare breaches are tied to improper access controls, enforcing least-privilege principles and maintaining detailed audit logs for biometric activities is crucial [5].
Vendor risk is another major concern, as third-party providers often handle sensitive biometric data. To address this, healthcare organizations should establish Business Associate Agreements (BAAs) with biometric solution providers, clearly outlining responsibilities for encryption, access controls, incident response, and data retention. Security reviews should include examining vendors' SOC reports, HIPAA compliance status, and history of incidents. These steps ensure a comprehensive approach to managing vendor risks.
Platforms like Censinet RiskOps™ simplify the process of managing third-party risks. By centralizing risk assessments, automating security questionnaires, and tracking remediation efforts, Censinet helps healthcare organizations monitor and manage risks tied to biometric technologies, patient data, and medical devices. As Terry Grogan, CISO at Tower Health, shared:
"
.
sbb-itb-535baee
Using Risk Management Platforms for Biometric Security
The constant threat of data breaches, spoofing attacks, and compliance failures makes managing biometric security a serious challenge. Handling these risks manually - using spreadsheets or questionnaires - just doesn’t cut it anymore, especially when dealing with a multitude of biometric vendors. Healthcare organizations need automated tools that can evaluate vendors at scale, track ongoing issues, and provide real-time monitoring. These platforms bring all risk data into one place, streamline assessments, and help security teams stay ahead of threats targeting biometric systems used for patient identification, medication tracking, EHR access, and facility security. This is where platforms like Censinet RiskOps™ step in, offering a solution that combines vendor assessments with continuous threat tracking.
Censinet RiskOps™ for Biometric Security
Censinet RiskOps™ is purpose-built for healthcare, offering tools to assess and manage risks associated with biometric vendors. It uses standardized security questionnaires tailored for healthcare, covering key areas like encryption, access controls, liveness detection, incident response, and HIPAA compliance. Organizations can also ensure vendors have proper Business Associate Agreements (BAAs) and follow clear protocols for breach notifications and data disposal.
As a cloud-based platform, Censinet RiskOps™ connects healthcare organizations with a network of over 50,000 vendors and products. This shared ecosystem enables healthcare providers to compare biometric vendors against industry benchmarks, evaluating controls like encryption standards, audit logging, and multi-factor authentication. Security teams can identify high-risk vendors, assign tasks to address vulnerabilities (e.g., implementing stronger liveness detection or removing default credentials), and track progress through a unified dashboard. Matt Christensen, Sr. Director GRC at Intermountain Health, emphasizes the platform’s healthcare focus:
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare"
.
By building on standardized assessments, the platform also leverages AI to take vendor risk monitoring to the next level.
AI-Powered Risk Assessment and Monitoring
Censinet AI™ simplifies and accelerates risk assessments. Vendors can complete detailed security questionnaires in seconds, while the AI generates summaries of vendor documentation and compiles risk reports based on the data collected. It analyzes vendor policies, audit reports, and other materials to extract critical details about biometric data protection, flagging red flags like the storage of raw biometric images or incomplete responses. This process cuts down on manual review time while maintaining thoroughness, whether the assessments involve fingerprint scanners, facial recognition systems, or palm-vein technology.
The platform doesn’t stop at initial assessments. Its AI-driven continuous monitoring integrates data from threat intelligence feeds, public breach reports, software vulnerability disclosures, and vendor updates. For instance, if a widely used biometric SDK reveals a critical flaw that could enable replay attacks, the platform identifies affected vendors and internal systems, prioritizes them for immediate action, and alerts the relevant teams. It also tracks changes in a vendor’s security practices - such as weakened encryption or recurring audit issues - and initiates reassessments when necessary. This dynamic approach ensures biometric security adapts to new threats and vendor changes in real time, moving beyond one-off evaluations to provide ongoing protection.
Conclusion
The need for strong biometric safeguards in healthcare is more pressing than ever. The risks tied to biometric data breaches go far beyond what traditional credentials like passwords or PINs can address. After all, you can reset a password, but you can't change your fingerprint or facial scan. A breach of this nature leaves patients exposed to identity theft and unauthorized access to their sensitive medical records - permanently.
To protect patient privacy and meet regulatory demands, effective mitigation strategies are non-negotiable. Tools like liveness detection help prevent spoofing attacks, encryption secures data during storage and transmission, and strict access controls ensure only authorized personnel can access sensitive information. Yet, despite these measures, 63% of healthcare data breaches still stem from inadequate access controls [5]. Relying on outdated manual processes or spreadsheets simply can't keep up with the rapidly evolving threat landscape.
This is where specialized platforms come into play. For example, Censinet RiskOps™ is designed specifically for healthcare's complex environment. It automates vendor assessments, monitors biometric security measures like encryption and audit logging, and uses AI to continuously identify new vulnerabilities. These capabilities make scalable and effective risk management a reality.
Protecting biometric data requires proactive, automated solutions. With the stakes so high - both in terms of patient trust and the financial penalties tied to breaches - healthcare organizations need tools that can address the unique challenges of securing biometric systems, whether it's for patient identification, electronic health record access, or facility security.
FAQs
What are the long-term impacts of a biometric data breach in healthcare?
A breach involving biometric data in healthcare can have far-reaching and lasting impacts for both individuals and organizations. For patients, the exposure of biometric details - like fingerprints or facial recognition data - can lead to identity theft, fraud, and an enduring loss of privacy. Unlike passwords, biometric information can’t simply be reset, making the consequences particularly severe.
Healthcare organizations face their own set of challenges. These include legal repercussions, hefty financial fines, and damage to their reputation. A breach can also make them more vulnerable to future cyberattacks, often forcing them to invest heavily in upgraded security systems to protect sensitive patient information and regain public trust. Addressing these risks head-on is essential to ensure both the safety of patient data and the stability of the organization.
What is liveness detection, and how does it enhance biometric security in healthcare?
Liveness detection is a security measure designed to confirm that a biometric sample - like a fingerprint or facial scan - comes from a real, living person, not a fake or replicated source. This technology helps block spoofing attempts, such as using photos, masks, or other deceptive methods to trick biometric systems.
In the healthcare field, liveness detection is essential for protecting sensitive patient data and ensuring secure access to clinical systems. By confirming that only authorized, living individuals can log in, it minimizes the risk of breaches and enhances the overall security of critical information.
Why is multi-factor authentication important when using biometrics in healthcare?
Multi-factor authentication (MFA) plays a crucial role in healthcare security by adding an extra layer of protection beyond just biometric data. While biometrics, like fingerprints or facial recognition, are highly individualized and secure, they aren't entirely foolproof. Threats like spoofing or data breaches still pose risks.
MFA strengthens security by pairing biometrics with an additional factor, such as a password or a one-time code. This combination makes it much harder for unauthorized users to access protected health information (PHI) or sensitive patient data. In an industry where privacy is paramount, implementing MFA is a key step in protecting healthcare systems and meeting strict compliance standards.
Related Blog Posts
- HIPAA Compliance and Biometric Data in Clinical Apps
- How Multi-Factor Authentication Prevents Healthcare Breaches
- Telehealth Security: Identity Proofing vs. Authentication
- Checklist for Implementing Biometric Solutions in Healthcare
{"@context":"https://schema.org","@type":"FAQPage","mainEntity":[{"@type":"Question","name":"What are the long-term impacts of a biometric data breach in healthcare?","acceptedAnswer":{"@type":"Answer","text":"<p>A breach involving biometric data in healthcare can have <strong>far-reaching and lasting impacts</strong> for both individuals and organizations. For patients, the exposure of biometric details - like fingerprints or facial recognition data - can lead to identity theft, fraud, and an enduring loss of privacy. Unlike passwords, biometric information can’t simply be reset, making the consequences particularly severe.</p> <p>Healthcare organizations face their own set of challenges. These include <strong>legal repercussions, hefty financial fines, and damage to their reputation</strong>. A breach can also make them more vulnerable to future cyberattacks, often forcing them to invest heavily in upgraded security systems to protect sensitive patient information and regain public trust. Addressing these risks head-on is essential to ensure both the safety of patient data and the stability of the organization.</p>"}},{"@type":"Question","name":"What is liveness detection, and how does it enhance biometric security in healthcare?","acceptedAnswer":{"@type":"Answer","text":"<p>Liveness detection is a security measure designed to confirm that a biometric sample - like a fingerprint or facial scan - comes from a real, living person, not a fake or replicated source. This technology helps block spoofing attempts, such as using photos, masks, or other deceptive methods to trick biometric systems.</p> <p>In the healthcare field, liveness detection is essential for protecting sensitive patient data and ensuring secure access to clinical systems. By confirming that only authorized, living individuals can log in, it minimizes the risk of breaches and enhances the overall security of critical information.</p>"}},{"@type":"Question","name":"Why is multi-factor authentication important when using biometrics in healthcare?","acceptedAnswer":{"@type":"Answer","text":"<p>Multi-factor authentication (MFA) plays a crucial role in healthcare security by adding an extra layer of protection beyond just biometric data. While biometrics, like fingerprints or facial recognition, are highly individualized and secure, they aren't entirely foolproof. Threats like spoofing or data breaches still pose risks.</p> <p>MFA strengthens security by pairing biometrics with an additional factor, such as a password or a one-time code. This combination makes it much harder for unauthorized users to access <strong>protected health information (PHI)</strong> or sensitive patient data. In an industry where privacy is paramount, implementing MFA is a key step in protecting healthcare systems and meeting strict compliance standards.</p>"}}]}
Key Points:
What are biometric data risks in healthcare?
- Definition: Biometric data risks in healthcare include breaches, identity theft, unauthorized access to medical records, and misuse of personal health information. These risks are heightened due to the immutable nature of biometric identifiers like fingerprints, facial scans, and iris patterns.
- Examples of Risks:
- Breaches of centralized biometric databases.
- Unauthorized access to sensitive patient data.
- Compliance challenges with laws like HIPAA and BIPA.
Why is biometric data security important in healthcare?
Importance:
- Protects sensitive patient information from breaches and misuse.
- Ensures compliance with regulations like HIPAA, which mandates safeguards for electronic protected health information (ePHI).
- Prevents misuse of immutable biometric identifiers, which cannot be changed if compromised.
- Builds trust with patients by demonstrating a commitment to data security.
What are the challenges of managing biometric data in healthcare?
Challenges:
- Securing Centralized Databases: Centralized storage of biometric data increases the risk of breaches.
- Compliance Costs: Adhering to laws like BIPA and HIPAA can be resource-intensive.
- Authentication Errors: Environmental factors or system limitations can lead to failures in biometric authentication, delaying patient care.
- Vendor Risks: Third-party vendors may introduce vulnerabilities if they fail to comply with security standards.
What are the best practices for mitigating biometric data risks?
Best Practices:
- Encryption: Use AES-256 encryption for data at rest and TLS for data in transit.
- Multi-Factor Authentication (MFA): Combine biometrics with additional authentication factors to enhance security.
- Liveness Detection: Prevent spoofing attacks by verifying that biometric inputs come from live individuals.
- Access Controls: Implement strict access controls to limit who can access biometric data.
- Vendor Risk Management: Assess and monitor vendors to ensure they comply with security and regulatory requirements.
How can healthcare organizations ensure compliance with biometric data regulations?
Compliance Strategies:
- Adhere to HIPAA’s Security Rule by implementing technical, administrative, and physical safeguards.
- Conduct regular risk assessments to identify vulnerabilities in biometric systems.
- Follow state-specific laws like BIPA, which require informed consent and robust security measures.
- Maintain detailed documentation of compliance efforts, including vendor agreements and security protocols.
What role do vendors play in biometric data security?
Vendor Responsibilities:
- Provide secure systems with features like encryption, secure boot loaders, and firmware authenticity verification.
- Sign Business Associate Agreements (BAAs) to ensure accountability for HIPAA compliance.
- Collaborate with healthcare organizations to address vulnerabilities and ensure secure device lifecycle management.


