Children's Hospital Vendor Risk: Pediatric-Specific Safety and Compliance Requirements
Post Summary
Children's hospitals face higher stakes when managing vendor risks due to the unique needs of pediatric patients and stricter regulations like HIPAA, COPPA, and FDA standards. With vendor-related cyberattacks increasing by 400% over two years and healthcare breaches costing nearly $10 million on average, the need for specialized risk management is critical.
Key points for managing vendor risks in pediatric care:
- Stricter Regulations: Vendors must comply with laws like HIPAA, COPPA, and FDA standards for pediatric medical devices.
- Sensitive Data Protection: Pediatric PHI demands higher security, including encryption, multi-factor authentication, and role-based access controls.
- Vendor Tiering: Classify vendors by data sensitivity and impact on pediatric care to allocate resources effectively.
- Continuous Monitoring: Use tools to track vendor compliance, detect risks, and ensure safety protocols are followed.
- Specialized Requirements: Vendors must use non-toxic materials, understand pediatric-specific safety protocols, and adhere to age-appropriate medical standards.
Effective vendor risk management protects sensitive pediatric data, ensures compliance, and reduces risks to patient safety. Tools like Censinet RiskOps™ can help automate assessments, monitor compliance, and streamline processes tailored to pediatric hospital needs.
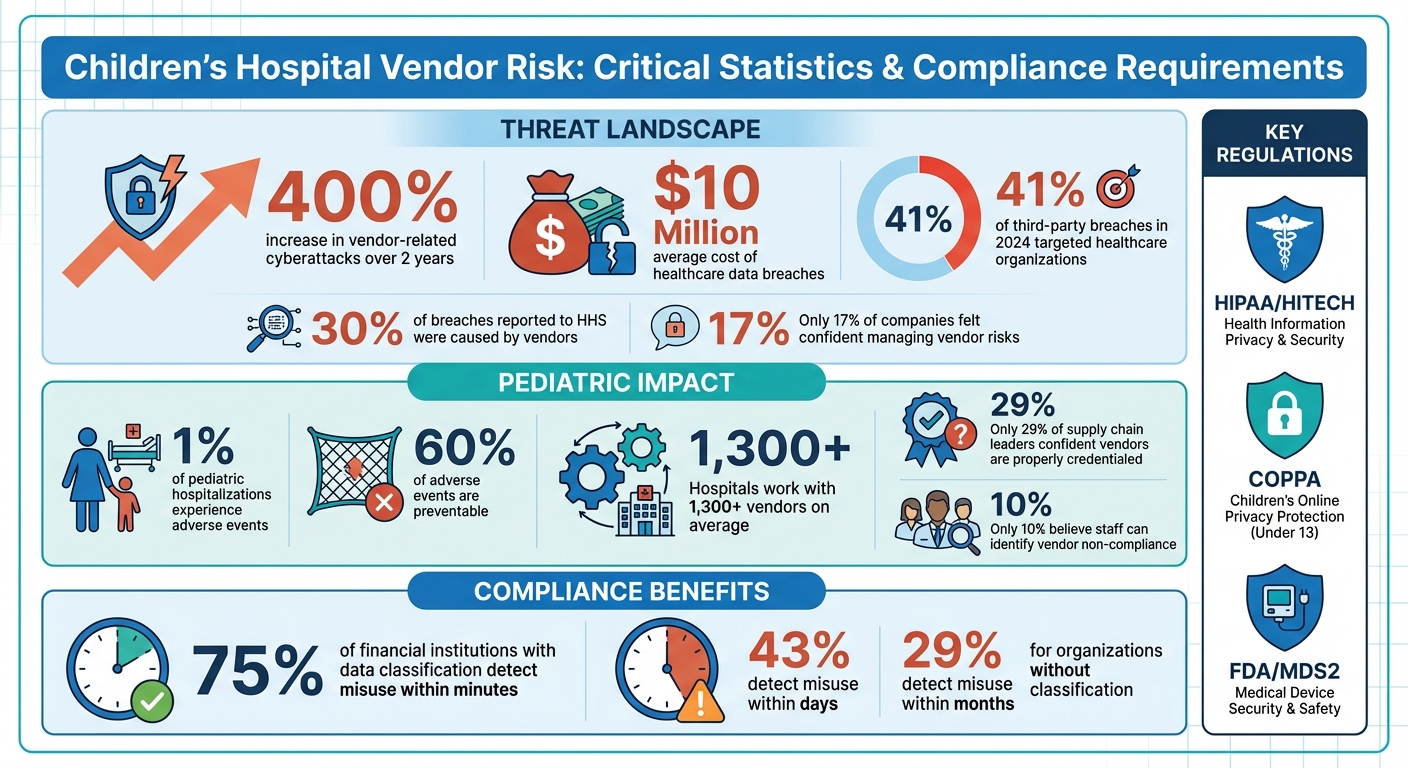
Children's Hospital Vendor Risk Statistics and Key Compliance Requirements
Pediatric Regulations and Compliance Standards
Children's hospitals operate within a particularly intricate regulatory environment, going beyond the usual healthcare standards. Vendors working with these institutions must carefully navigate a web of rules designed to safeguard pediatric patients. A clear understanding of these regulations is essential for building responsible and effective vendor relationships. Below, we explore some of the key regulations that shape vendor responsibilities in pediatric care.
HIPAA and HITECH for Pediatric PHI Protection
Under HIPAA, parents or legal guardians typically act as representatives for minors. However, there are exceptions - such as cases involving abuse or neglect - where disclosure rules differ. For example, HIPAA allows the disclosure of a child’s PHI without the guardian's authorization if state laws mandate reporting or suspicion of abuse or neglect [5][6][7]. Vendors must ensure their systems are designed to handle these nuanced access requirements appropriately.
The HITECH Act adds another layer by increasing penalties and extending HIPAA's Security Rule to include Business Associates. It also emphasizes enhanced access to electronic health records (EHRs), requiring vendors to implement secure data segmentation and robust EHR functionalities [8][9]. This becomes even more complex under the 21st Century Cures Act Interoperability Final Rule, which demands data-sharing capabilities. Vendors face challenges when EHR systems cannot properly segment data - especially when a parent's health information is intertwined with their child’s in the same record set [5][6].
COPPA for Pediatric Data Privacy
The Children's Online Privacy Protection Act (COPPA) governs commercial websites and online services that cater to children under 13 or knowingly collect their personal information [10][11]. Vendors offering digital health tools for pediatric use must comply with COPPA by securing parental consent, limiting the scope of data collection, and maintaining strict privacy measures to protect children’s information.
FDA and MDS2 Requirements for Pediatric Medical Devices
Vendors producing medical devices for pediatric use must adhere to FDA cybersecurity standards, particularly for devices that rely on software [12]. To ensure transparency and safety, vendors are required to provide MDS2 (Manufacturer Disclosure Statement for Medical Device Security) documentation. This documentation outlines the device's security features and any known vulnerabilities, helping to protect the safety of pediatric patients.
Vendor Risk Assessment and Tiering for Children's Hospitals
In pediatric healthcare, where compliance demands are particularly stringent, having a detailed vendor risk assessment and tiering process is essential. Risks associated with vendors can vary significantly, so it’s crucial to classify vendors based on the sensitivity of pediatric data they access and the potential impact on patient care. This approach helps allocate resources effectively.
Under various data privacy laws, all personal information related to children is automatically considered sensitive. This means stricter requirements for data consent and usage apply [16]. Protected Health Information (PHI) in pediatric settings includes a wide range of identifiers like patient names, addresses, birth dates, phone numbers, email addresses, Social Security numbers, medical record numbers, health plan details, biometric data, and any unique identifying codes [17].
"Cyber risk is the most important vendor risk to manage in the modern era." - Grant Slinger, Responsible for the Consulting Services LOB, IQX Business Solutions [14]
A 2017 report revealed that vendors were responsible for 30% of breaches reported to the Department of Health and Human Services (HHS), yet only 17% of companies felt confident in managing these risks [22]. For children's hospitals, safeguarding sensitive pediatric information is non-negotiable, making a systematic vendor classification process even more critical.
Classifying Vendors by Data Sensitivity and Pediatric Impact
To classify vendors effectively, focus on two main factors: the sensitivity of the data they handle and the potential consequences of their failure on pediatric care. Vendors with access to highly sensitive information should be evaluated against stringent criteria, including cybersecurity insurance, breach history, and adherence to privacy standards [13]. Consider how breaches or data corruption might affect confidentiality, data availability, and patient safety [17].
Clearly defining access levels within your vendor policy is equally important. A survey found that only 29% of supply chain leaders were very confident that vendor representatives entering their facilities were properly credentialed, and just 10% believed their staff could reliably identify and address vendor non-compliance [21].
Cybersecurity should be the top priority when tiering vendors. Those handling Electronic PHI (ePHI) need to meet rigorous standards, such as:
- A formal cybersecurity program
- Multi-factor authentication
- Regular vulnerability testing
- "Least Privilege" access practices
- SOC 2 compliance
- Data encryption (in transit and at rest)
- Cybersecurity insurance
- Intrusion prevention and detection systems
- Cybersecurity awareness training
- A solid history of preventing data breaches [13]
In pediatric healthcare, reputational risk is particularly impactful. A data breach involving children's medical records often generates heightened public concern compared to breaches in other sectors [14].
Organizations that implement effective data classification systems see tangible benefits. For example, 75% of financial institutions with data classification can detect misuse within minutes, while those without such systems often take days (43%) or even months (29%) [17]. Establish a classification framework that categorizes data into levels like public, internal, confidential, and restricted, ensuring the most sensitive pediatric information is prioritized for protection [16].
Evaluating Pediatric Device and IT System Risks
Beyond data access, pediatric hospitals must also assess risks associated with medical devices and IT systems. Vendor risk management programs should address the unique physiological, developmental, and emotional needs of pediatric patients [18][20].
For device vendors, evaluate their compliance with pediatric-specific regulations, quality management systems, and safety standards at every stage of the device lifecycle [18]. Risk mitigation should emphasize secure design, robust safety features, and clear user instructions [19].
IT system vendors require thorough verification. Ensure they maintain written information security policies, encrypt data during transit and storage (including backups), and securely manage encryption keys. Disaster recovery programs must align with HIPAA standards [22]. Additionally, enforce role-based access control for systems containing ePHI, implement two-factor authentication for high-risk users, and require security certifications like SOC 2, HITRUST CSF, or PCI-DSS [22].
Integrating vendor risk assessment into your onboarding process allows for early risk detection, better vendor selection, enhanced compliance, and stronger relationships with vendors [14]. Use structured risk assessment scales - such as three-, four-, or five-point scales - to evaluate risks based on their likelihood and potential impact. These scales often feed into a risk matrix, providing consistency across your vendor portfolio and helping justify resource allocation to hospital leadership [15].
Ongoing monitoring and auditing are essential to detect unauthorized access or unusual activity in real time. Regularly test backup restoration processes and maintain encrypted backups of sensitive pediatric data in secure storage solutions [16].
Building Pediatric-Focused Vendor Risk Management Processes
Managing vendors in children's hospitals requires careful planning and oversight, from onboarding to offboarding. With hospitals typically working with over 1,300 vendors and 41% of third-party breaches in 2024 targeting healthcare organizations, the stakes are high - especially for pediatric facilities, where patient vulnerability adds another layer of responsibility [23]. Below, we’ll explore how to establish effective processes tailored to pediatric needs.
Vendor Onboarding with Pediatric Data Flow Mapping
Onboarding is where vendor risk management begins. Focus on vendors critical to patient care and ensure their cybersecurity standards align with or exceed your hospital’s requirements [23].
Before granting access, conduct a thorough risk assessment. Scrutinize how vendors and their subcontractors handle pediatric data, including their protocols for collecting, storing, processing, transmitting, and accessing this sensitive information [23][24].
"In today's digitally interconnected health care landscape, a health system's cybersecurity is only as robust as its weakest link - often found in third-party vendors, mission-critical technologies, and the broader digital supply chain."
– AHA Knowledge Exchange [24]
Incorporate cybersecurity and compliance requirements into contracts and BAAs. These agreements should outline specific security measures like data encryption, access controls, retention policies, and breach notification procedures for pediatric PHI. They should also address how data will be returned or destroyed during offboarding [23][25].
Real-world examples emphasize the importance of these measures. At Children’s National Hospital, all vendors must follow a Vendor Code of Conduct as part of the hospital’s vendor management program. This program ensures patient privacy and facility safety, with the Supply Chain Department overseeing procurement, contracting, and compliance. Vendors are also required to complete annual safety training [1].
Similarly, Texas Children’s Hospital introduced a vendor program in February 2023. It enforces strict compliance policies, requiring valid 10-digit Purchase Order numbers on invoices and mandating vendor registration through Green Security for onsite visits. Registration fees are determined by the vendor’s risk profile [26].
To strengthen oversight, maintain a detailed vendor inventory and establish clear governance with executive sponsorship for third-party risk management. Independent third-party assessments are also critical, as they provide an objective evaluation of vendor compliance, going beyond self-certifications [23].
Continuous Monitoring for Compliance and Safety
Effective vendor management doesn’t stop at onboarding. Continuous monitoring is essential to ensure compliance and safety throughout the vendor relationship. Automated systems can track vendor data in real time, using analytics and AI to detect anomalies and predict compliance risks [28]. These tools can also manage contracts, certifications, and flag missing documentation [27].
For example, Children’s National Hospital conducts monthly screenings of all vendors against exclusion and debarment lists, such as the Office of Inspector General’s database, to ensure ongoing compliance. Vendors must also complete training on safety, HIPAA privacy and security, and the hospital’s Vendor Code of Conduct. For those with frequent onsite visits, additional requirements like drug tests, TB screenings, and immunizations (e.g., MMR, Varicella, Tdap, and Hepatitis B) are enforced [3].
Vendors should also be integrated into the hospital’s core security programs, including incident response plans, disaster recovery testing, and business continuity planning. Establish a Plan of Action and Milestones (POA&M) to address and resolve identified risks over time.
For pediatric-specific needs, verify that vendors meet requirements such as using non-toxic, latex-free, and lead-free materials, as well as providing age-appropriate devices. Non-compliance can result in hefty financial penalties - up to $10,000 per violation [2]. Tools like safety dashboards and incident reports can help track improvements and highlight areas needing attention. A 2019 report revealed that 41% of healthcare facilities experienced breaches, often due to phishing, system vulnerabilities, or poorly managed third-party vendors [27].
"Managing third-party risk isn't about eliminating all risk - it's about reducing it to an acceptable and manageable level."
– Pondurance [23]
Real-time dashboards can also enhance physical security by monitoring who is onsite, which is especially useful for vendors requiring facility access. These systems can generate documentation for governing bodies like the Joint Commission [2].
Secure Vendor Offboarding Protocols
Offboarding vendors is a critical phase, often fraught with risks. Over the past two years, vendor-related attacks in healthcare supply chains have surged by over 400%, with the average cost of a data breach in healthcare nearing $10 million [4]. Risks during offboarding include leftover access permissions, data theft, and failures to delete patient data as required by HIPAA [4].
A comprehensive offboarding checklist is essential. Revoke all vendor access to systems, including VPNs, applications, badges, and APIs. Change passwords for systems the vendor previously accessed [4].
Extra precautions should be taken when offboarding vendors with administrator-level access or those handling sensitive data. Confirm the destruction of patient records, and request a signed statement from the vendor verifying data deletion. Past breaches highlight the importance of these measures [27].
sbb-itb-535baee
Using Censinet RiskOps™ for Pediatric Vendor Risk Management
Children's hospitals face unique challenges in managing vendor risks. From safeguarding pediatric PHI to meeting regulations like HIPAA, COPPA, and FDA standards, the stakes are high. Censinet RiskOps™ is purpose-built for healthcare, providing tools that simplify workflows and alleviate the pressure on risk management teams. Its automation and monitoring features are designed to tackle the specific safety concerns tied to pediatric care.
Automating Vendor Assessments with Censinet AI™
Manual vendor assessments can drain resources and slow down risk management efforts. Tower Health, which includes St. Christopher's Hospital for Children, managed to cut their assessment time to under a week, all while reallocating staff and tripling their productivity[32].
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required."
– Terry Grogan, MIS, CISM, Chief Information Security Officer, Tower Health[29][32]
Censinet AI™ streamlines the assessment process by enabling vendors to complete security questionnaires in seconds. It automatically summarizes evidence, highlights key integration details, and identifies fourth-party risks. Using standardized, best-practice-aligned questionnaires, the platform ensures compliance with pediatric healthcare regulations, including HIPAA, COPPA, and FDA requirements for medical devices[30][31]. Vendors only need to complete these questionnaires once, after which they can share them with unlimited customers through one-click sharing. This efficiency allowed Tower Health to achieve same-day responses from vendors[32].
The platform also maintains a comprehensive risk record, documenting all Corrective Action Plans (CAP) and remediation activities. This auditable trail is essential for HIPAA compliance and provides a reliable resource for responding to security incidents, ensuring consistent oversight of vendor compliance.
Real-Time Risk Dashboards for Pediatric Compliance
In children's hospitals, any risk to patient safety or data security can have serious consequences. Censinet RiskOps™ addresses this by offering a cloud-based platform with real-time monitoring. Automated risk scoring adjusts residual risk ratings as vendor data changes, keeping risk teams informed through alerts and scheduled reassessments[30].
Vendors are categorized based on their potential impact on business and clinical operations, including their access to sensitive pediatric data. This prioritization helps hospitals focus on the most critical risks. Additionally, the shared intelligence within the Censinet Risk Network speeds up risk mitigation, while vendors maintain up-to-date risk data in the Cybersecurity Data Room™. Hospitals gain actionable insights into overdue remediations and open risks, enabling targeted interventions to protect pediatric patients. For example, Dayton Children's improved their third-party risk management program with Censinet, effectively addressing rising cyber threats and securing their care operations[33].
Custom Solutions for Children's Hospitals
Censinet provides deployment options tailored to the specific needs of children's hospitals. These options - Platform, Hybrid, or Managed Services - are designed to accommodate varying hospital sizes and budgets.
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare."
– Matt Christensen, Sr. Director GRC, Intermountain Health[29]
Conclusion
Managing vendor risks in children's hospitals is essential to safeguard young patients and ensure compliance with regulatory standards. With thousands of vendor interactions and a high rate of breaches, pediatric care faces unique challenges. These include developmental communication barriers and the absence of evidence-based treatments for many conditions, making strong vendor oversight a necessity.
Adverse events impact 1% of pediatric hospitalizations, with 60% of these being preventable [34]. The risks increase when third-party vendors handle sensitive pediatric PHI, manage medical devices, or support critical IT systems. As highlighted by the American Hospital Association following the Change Healthcare cyberattack, “the national consequences of cyberattacks targeting mission-critical third-party providers can be even more devastating than when hospitals or health systems are attacked directly” [23]. These realities emphasize the need for vendor risk practices tailored to pediatric care.
To address these risks, constant vigilance in vendor management is a must. This includes prioritizing vendors based on their impact on patient care, embedding strong cybersecurity measures into contracts, conducting thorough due diligence during onboarding, and maintaining detailed vendor inventories. Additionally, risks from indirect relationships - such as fourth- and fifth-party vendors - must also be accounted for [24].
Vendors should be fully integrated into incident response, disaster recovery, and business continuity plans, with the same level of preparation as other disaster-planning efforts. Collaboration across departments like procurement, legal, compliance, IT, and cybersecurity ensures that everyone is prepared to respond effectively when threats arise [23][24].
Weaknesses in vendor security protocols can compromise overall cybersecurity. This makes pediatric-specific risk management essential - not just to protect sensitive data but also to ensure the safety of the vulnerable patients who depend on secure and reliable care.
FAQs
What regulations do vendors need to follow when working with children's hospitals?
Vendors collaborating with children's hospitals must follow a range of regulations designed to protect patient safety and ensure compliance. Key among these are HIPAA, which safeguards sensitive patient information, and federal laws such as the False Claims Act, Stark Law, and the Anti-Kickback Statute. Beyond these, hospitals often have their own specific requirements, including credentialing processes, safety protocols, and rules governing vendor access.
For those working in pediatric care, it’s also crucial to align with standards tailored to child-focused healthcare, particularly when it comes to pediatric medical devices and IT systems. Adhering to these regulations isn’t just about compliance - it’s about prioritizing the safety and unique needs of young patients.
How can children's hospitals identify and manage risks associated with their vendors?
Children's hospitals can tackle vendor risks more effectively by prioritizing pediatric-specific safety and compliance requirements. A good starting point is to evaluate vendors based on the level of risk they bring to the table. Before onboarding, conduct detailed risk assessments, examine security measures, and confirm that vendors adhere to healthcare regulations tailored to pediatric care. It's also critical to verify that their medical devices and IT systems meet safety standards designed for children.
To ensure long-term safety and compliance, establish regular monitoring routines and schedule periodic reviews. This can involve updating vendor credentials, auditing their performance, and keeping up with changes in healthcare regulations. These proactive steps not only help safeguard sensitive pediatric patient data but also minimize the risks associated with third-party partnerships.
What makes protecting pediatric patient data especially challenging?
Protecting pediatric patient data is no small task. This information is incredibly sensitive, not just because it pertains to minors, but also because children are especially vulnerable to risks like identity theft and data misuse. To keep this data safe, healthcare providers must implement strong cybersecurity systems, maintain constant monitoring, and enforce strict access controls to prevent breaches or unauthorized access.
On top of that, healthcare organizations must navigate complex regulations like HIPAA and FDA standards, which add another layer of responsibility. Children's hospitals, in particular, deal with unique challenges: they need to ensure medical devices and supplies are suitable for kids, account for pediatric-specific issues like precise dosing, and create a care environment that reduces anxiety for young patients. All these factors highlight the importance - and complexity - of safeguarding pediatric patient data.


