Disaster Recovery for Patient Data: Best Practices
Post Summary
Healthcare organizations can't afford system downtime - it risks patient safety and regulatory penalties. A solid disaster recovery plan ensures quick restoration of critical systems like electronic health records (EHRs) and protects sensitive patient data. Here's what you need to know:
- Key Risks: Cyberattacks, hardware failures, human errors, and natural disasters can disrupt healthcare operations.
- Regulatory Requirements: HIPAA mandates contingency plans, including data backups, disaster recovery, and emergency operations.
- Backup Strategies: Use the 3-2-1 rule - three copies of data, two on different media, one offsite. Encrypt and test backups regularly.
- Recovery Priorities: Conduct a Business Impact Analysis (BIA) to classify systems by importance and set recovery objectives.
- Communication: Have clear escalation protocols and redundant communication methods to keep teams informed during outages.
Disaster recovery is an ongoing process. Regular testing, risk assessments, and vendor oversight are critical to maintaining system resilience and ensuring uninterrupted patient care.
Healthcare Disaster Recovery Plan: 5 Core Components for HIPAA Compliance
Core Elements of a Patient Data Disaster Recovery Plan
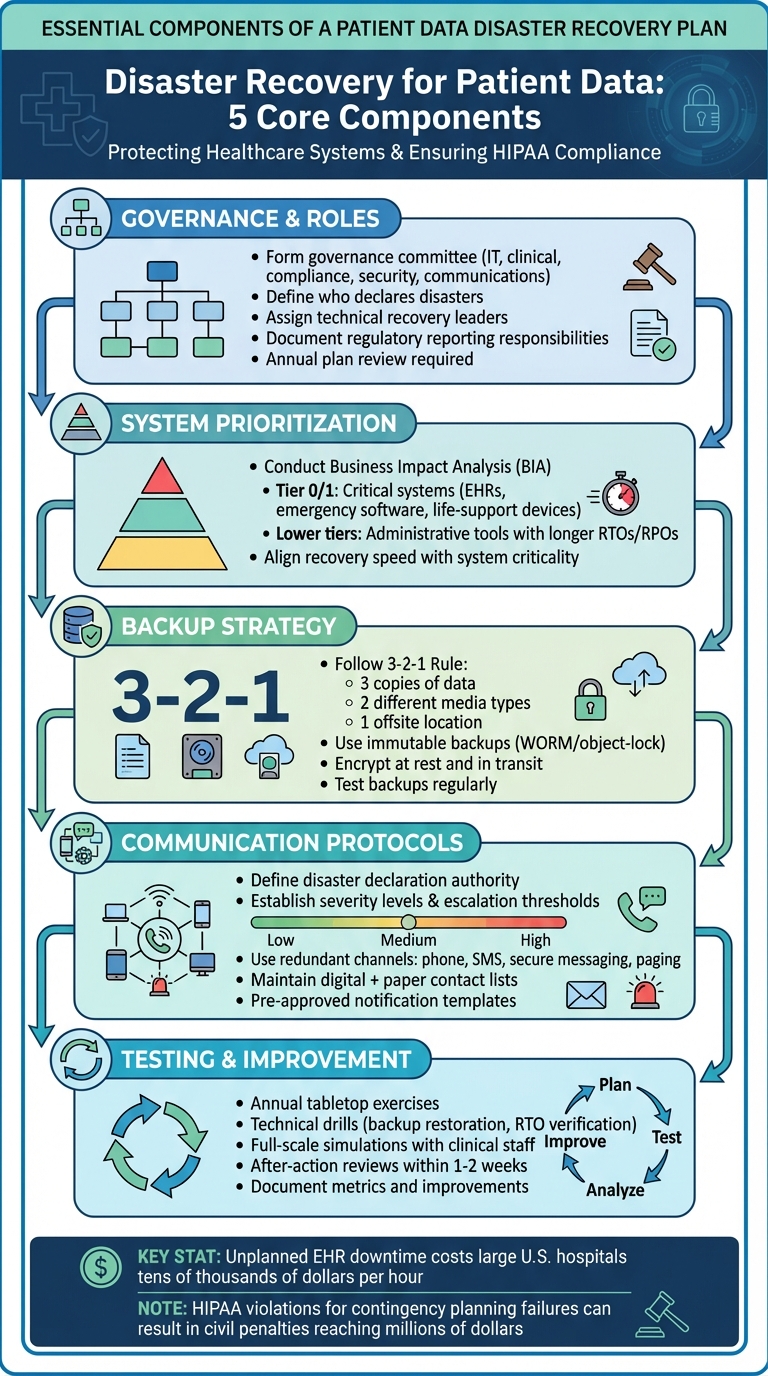
To effectively navigate the risks and regulatory requirements tied to patient data, healthcare organizations need a well-structured disaster recovery plan. This plan must align with HIPAA's contingency requirements and gain approval from leadership [6][7]. While HIPAA doesn’t mandate specific technologies, it requires covered entities to implement essential components under the Security Rule's contingency standard [6][7]. Without a documented plan addressing these critical elements, organizations risk operational breakdowns during incidents, alongside hefty penalties [6][7].
Governance Structure and Team Responsibilities
A solid governance framework is essential for disaster recovery. Form a governance committee that includes representatives from IT, clinical operations, compliance, security, and communications. This committee should review and approve the recovery plan annually [2][5][11]. The plan must clearly define roles and responsibilities, such as:
- Who declares a disaster and activates the plan
- Who leads technical recovery efforts
- Who adjusts clinical workflows
- Who manages regulatory reporting and external communications [2][5][11]
Failure to assign and document these roles can lead to delays in recovery efforts, potentially compromising patient safety.
How to Prioritize Systems and Data
Start by conducting a Business Impact Analysis (BIA) to identify and classify systems based on their importance to patient care, safety, revenue, and compliance. This analysis forms the foundation of a tiered recovery strategy. For example:
- Tier 0/Tier 1 systems: Critical systems like electronic health records (EHRs), emergency department software, and life-supporting medical devices require the fastest recovery methods, such as immediate failover, replication, or frequent backups.
- Lower-tier systems: Administrative tools and less critical systems have longer recovery time objectives (RTOs) and recovery point objectives (RPOs).
Platforms like Censinet RiskOps™ can streamline this prioritization process by centralizing risk assessments. These tools provide visibility into risks posed by vendors and internal systems, enabling governance teams to align recovery efforts with quantified risks and ensure RTOs and RPOs match the criticality of each system [10].
Communication Plans and Escalation Protocols
Effective communication is vital during a disaster. Organizations need detailed communication and escalation plans that outline:
- Who has the authority to declare a disaster
- Severity levels and escalation thresholds
- Step-by-step notification procedures [3][9][11]
Redundant communication channels (e.g., phone trees, SMS, secure messaging apps, overhead paging, and paper backups) should be in place to notify IT teams, clinical leaders, executives, vendors, regulators, and, when necessary, patients. This ensures compliance with HIPAA breach notification laws [3][9][11].
Maintain updated contact lists in both digital and paper formats. Define primary and backup communication methods, and use pre-approved notification templates vetted by compliance and public relations teams [3][9][11]. Additionally, integrating third-party management tools can help by consolidating vendor contacts, service-level agreements (SLAs), and response commitments, ensuring smoother coordination during recovery efforts [10].
Data Backup Strategies for Healthcare
A well-planned backup strategy is essential for ensuring quick data restoration, which is crucial for maintaining uninterrupted patient care. Backups are the backbone of disaster recovery. Without them, healthcare organizations risk losing critical patient data to ransomware attacks, hardware malfunctions, or natural disasters. One commonly recommended method is the 3-2-1 backup rule: keep three copies of your data, store them on two different types of media, and ensure one copy is offsite. This approach helps protect against localized failures, large-scale disasters, and cyberattacks [3][8]. By integrating these strategies into their disaster recovery plans, healthcare providers can better safeguard patient data against a wide range of threats.
Backup Architecture Options
Healthcare organizations generally rely on one of three backup architectures: onsite, offsite, or hybrid.
- Onsite backups use local storage solutions like disk arrays, network-attached storage (NAS), or tape libraries. These backups offer quick restore times and high data transfer speeds since they don’t depend on internet connectivity. However, they are vulnerable to physical disasters, theft, and ransomware that can spread within internal networks.
- Offsite backups, stored in remote data centers or cloud repositories, add geographic redundancy and protect against physical disasters. However, restoring large datasets from offsite locations can be slower due to bandwidth limitations.
- Hybrid backups combine the strengths of both. For example, a hospital might keep local backups for recent patient data while transferring daily snapshots to a cloud repository. This hybrid approach aligns with the 3-2-1 rule, balancing fast recovery times with robust disaster protection [3].
Using Immutable and Encrypted Backups
To defend against ransomware, many healthcare organizations are turning to immutable backups. These use technologies like write-once, read-many (WORM) or object-lock features, ensuring that data cannot be altered or deleted during a set retention period [8]. An immutable backup or air-gapped copy remains secure even if the primary systems are compromised.
Encryption is equally critical. Backups containing protected health information (PHI) should be encrypted both at rest and in transit to comply with HIPAA regulations and protect patient confidentiality. Strong encryption practices include storing encryption keys separately from the backup data and implementing strict access controls, such as dedicated administrator accounts and least-privilege permissions [2][4][8]. Regular testing ensures these measures remain effective.
Testing and Validating Backups
Testing backups isn’t just a best practice - it’s essential for ensuring disaster recovery readiness. Regularly restoring backups and documenting the process helps meet audit requirements and identify areas for improvement. Modern tools now enable application-consistent snapshots, allowing near-instant recovery of complex systems like electronic health records [12].
Additionally, healthcare organizations can use third-party risk management platforms - like Censinet RiskOps™ - to verify that vendors follow best practices, including maintaining immutable and encrypted backups [10]. These validation efforts ensure that backup strategies remain reliable and effective when they’re needed most.
Executing Disaster Recovery in Clinical Settings
When disaster strikes in healthcare, the difference between order and chaos often comes down to preparation and clear protocols. Healthcare organizations face unique challenges during system outages because patient safety can't be put on hold while IT systems are being restored. HIPAA regulations require these organizations to have robust backup and recovery plans in place, ensuring critical operations continue even when systems are down - not just after they're restored [7][8].
Incident Response and Recovery Steps
The first hour after discovering a major clinical system outage is absolutely crucial. IT and clinical teams need to act quickly to assess the scope of the incident. Which facilities, clinical areas, and systems are affected? What immediate patient safety risks exist, especially in high-stakes areas like the emergency department, operating rooms, ICU, labor and delivery, oncology, and dialysis units [2][10]? Based on this assessment, the organization must decide whether to fail over to a secondary data center or cloud environment, operate in a read-only mode, or switch entirely to downtime procedures.
In cases of ransomware attacks, the response must include engaging the security team immediately. Evidence preservation is critical, as is involving legal and compliance teams, and possibly law enforcement or cyber insurance responders [8][10]. According to the HIPAA Journal, failures in contingency planning and disaster recovery are among the most common reasons for HIPAA violations, often resulting in civil monetary penalties that can reach into the millions of dollars for large breaches [7]. Communication is key during such crises - clinicians, executives, and external partners need to be kept informed about what systems are affected, how long the outage might last, and what workarounds are in place [4][11][10]. These initial steps lay the groundwork for maintaining patient care during extended outages.
Maintaining Patient Care During System Outages
Once recovery efforts are underway, the focus shifts to ensuring patient care continues without interruption. Pre-printed downtime forms and standardized kits should be readily available in every clinical unit to maintain accurate records and deliver safe care during outages [4][11].
For medications, having printed or locally stored formularies and dose guides for common drugs, including weight-based pediatric dosing, is essential. Manual checks between pharmacy and nursing teams - via phone or secure radio - help ensure accuracy [4]. For labs and imaging, downtime requisition forms should include all necessary identifiers, clinical indications, priorities, and locations. Paper requisitions and specimens can be transported using courier or runner workflows between units and labs or radiology [11]. Critical lab results should be communicated directly to clinicians via phone, with documented read-backs to replace electronic alerts [4]. It's worth noting that unplanned EHR downtime can cost large U.S. hospitals tens of thousands of dollars per hour due to lost revenue, patient diversions, and overtime.
Data Reconciliation After Recovery
Once systems are restored and verified as safe, the next step is data reconciliation to ensure patient records are complete. The American Health Information Management Association (AHIMA) stresses that even after a disaster, organizations must meet their obligations to patients - this includes providing access to records, making amendments, and tracking disclosures. These tasks depend on accurate reconciliation of documents created during downtime [11].
To streamline this process, organizations should use unique downtime encounter numbers or labels to match paper records with the appropriate patients and visits [11]. Priority should be given to entering time-sensitive information - like medication records, procedure notes, critical results, and discharge summaries - before addressing less urgent documentation. Quality checks, such as random sampling, peer reviews of reconciled records, and reports flagging missing information (e.g., allergies, medications, or visit documentation), help ensure everything is accurate and complete [4][11]. This isn't just about administrative efficiency - it’s a compliance requirement that safeguards patient safety and shields the organization from regulatory penalties.
sbb-itb-535baee
Testing, Improvement, and Third-Party Risk Management
A disaster recovery plan is only as good as its most recent test. For healthcare organizations, a structured testing process is essential - not just to meet compliance standards but to ensure that systems, teams, and processes can withstand real-world challenges.
How to Test and Improve Your Disaster Recovery Plan
Adopting a tiered testing strategy is a practical way to cover all bases. Start with annual tabletop exercises that bring together leadership, clinicians, IT staff, and compliance teams. These sessions simulate scenarios like ransomware attacks, EHR outages, or data center failures, helping to clarify roles, improve communication, and validate decision-making - all without disrupting daily operations [13].
On the technical side, drills should verify that backups can be restored within Recovery Time Objectives (RTOs), authentication systems function properly, and network connectivity remains stable. For a more realistic test, conduct full-scale simulations where clinical staff practice using downtime procedures, reconciling paper records, and directly communicating with patients. These exercises provide a hands-on opportunity to evaluate how well the plan works under pressure.
For systems with short RTO/RPO targets, high volumes of Protected Health Information (PHI), or direct patient-care implications, testing should occur more frequently. After every test or real-world incident, record key metrics like success rates, failures, clinical impacts, and response times. Within one to two weeks, hold a formal after-action review involving IT, clinical, compliance, and vendor representatives. This review identifies what worked, what didn’t, and outlines necessary improvements, ensuring the disaster recovery plan stays accurate and effective. Regular testing not only sharpens response protocols but also strengthens overall system resilience, ensuring uninterrupted patient care.
Managing Vendor and Third-Party Risks
Internal testing is just one piece of the puzzle. Managing risks from third-party vendors is equally vital. Vendors often pose significant security challenges in healthcare, so they must be integrated into the disaster recovery strategy. Start by maintaining a detailed inventory of vendors that handle electronic protected health information (ePHI) and categorize them based on their importance to your operations.
For critical vendors, review their disaster recovery plans, evidence of testing, uptime Service Level Agreements (SLAs), and security certifications. Contracts and business associate agreements should clearly specify expectations, such as minimum uptime requirements, RTO/RPO commitments, backup schedules, geographic redundancy, and incident notification timelines. Reassess high-risk vendors annually or after significant changes. Incorporating vendor reviews into your incident management process ensures that any vendor-related incidents trigger a joint post-incident review and risk reassessment.
Using Censinet RiskOps™ for Risk Management
Managing third-party risks across numerous vendors can quickly become overwhelming, especially with traditional spreadsheet-based methods. Purpose-built platforms like Censinet RiskOps™ simplify the process by centralizing and streamlining vendor risk management. This cloud-based solution allows healthcare organizations to distribute standardized security and disaster recovery questionnaires, collect supporting evidence, and evaluate risks using healthcare-specific criteria.
For example, in 2025, Tower Health’s Chief Information Security Officer (CISO), Terry Grogan, highlighted the platform’s efficiency:
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required." [1]
The platform also provides a centralized repository for risk registers, remediation plans, vendor attestations, and other documentation - making audits and executive reporting much easier. As James Case, VP & CISO of Baptist Health, shared in 2025:
"Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with." [1]
Additionally, Censinet RiskOps™ offers cybersecurity benchmarking tools to measure an organization’s maturity and resilience against industry peers. Faith Regional Health’s CIO, Brian Sterud, emphasized in 2025:
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters." [1]
Conclusion
Safeguarding patient data through effective disaster recovery isn't just a technical necessity - it’s a critical component of ensuring patient safety, maintaining uninterrupted care, and adhering to HIPAA regulations. Downtime can disrupt access to vital records and communication systems, creating risks that no healthcare organization can afford.
Preparation is key. Clearly document recovery roles, and establish realistic Recovery Time Objectives (RTOs) and Recovery Point Objectives (RPOs) to avoid the pitfalls of reactive responses. These plans must be paired with secure backup strategies for all critical systems. Redundant, encrypted, and immutable backups are non-negotiable. Without reliable and tested backups, even the most detailed recovery plans are destined to fail. This isn’t a one-and-done effort - regular testing and risk reassessment are essential to keep plans relevant and effective.
Disaster recovery is a continuous journey. Healthcare organizations must prioritize regular risk assessments, conduct drills, and strengthen the security of their backup systems. Oversight of third-party vendors is equally crucial, as their missteps can directly compromise access to protected health information. Platforms like Censinet RiskOps™ simplify these challenges by centralizing third-party risk assessments, benchmarking cybersecurity practices, and managing risks across clinical systems, medical devices, and supply chains. Such tools can transform cumbersome manual processes into efficient, centralized workflows, ensuring improvements are both data-driven and aligned with regulatory standards.
To build a resilient recovery framework, assign clear executive ownership, evaluate your HIPAA contingency readiness, invest in secure backup systems, define achievable RTOs and RPOs, and maintain strict oversight of third-party vendors. As Matt Christensen aptly stated:
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare."
FAQs
What are the essential components of a disaster recovery plan for healthcare organizations?
A robust disaster recovery plan is essential for healthcare organizations to protect patient data and ensure operations bounce back swiftly during disruptions. Here’s what a solid plan should include:
- Risk assessment and impact analysis: Pinpoint critical systems and identify weak spots that could be exploited or fail during a crisis.
- Data backup and recovery protocols: Safeguard sensitive patient information and ensure it can be restored without delays.
- Clear incident response procedures: Lay out actionable steps to address emergencies immediately and effectively.
- Effective communication plans: Keep staff, patients, and regulatory bodies informed with clear, timely updates.
- Regulatory compliance: Adhere to legal standards like HIPAA to maintain trust and meet ethical obligations.
- Regular testing and staff training: Test the plan frequently and train personnel to ensure everyone knows their role when it counts.
To strengthen their defenses, healthcare organizations can leverage specialized tools like Censinet RiskOps™. These platforms simplify risk management and enhance cybersecurity, ensuring a more resilient approach to disaster recovery.
What steps can healthcare organizations take to stay HIPAA-compliant during system outages?
To ensure HIPAA compliance during system outages, healthcare organizations need a strong disaster recovery plan. This involves several critical steps: utilizing secure, encrypted backup systems to safeguard patient data, performing regular risk assessments to pinpoint potential vulnerabilities, and creating detailed breach response procedures to enable quick and effective action when necessary.
Tools such as Censinet RiskOps™ can streamline the process of managing risks and monitoring compliance. These platforms help organizations protect sensitive information and stay operationally prepared during unforeseen disruptions.
How can healthcare organizations protect patient data from cyberattacks and natural disasters?
Healthcare organizations can safeguard patient data by adopting detailed disaster recovery plans and strong cybersecurity strategies. This involves using advanced tools, such as AI-based risk management platforms, performing regular cybersecurity audits, and adhering to healthcare regulations like HIPAA.
Organizations should also implement clear response protocols for handling cyberattacks and natural disasters. Key steps include maintaining data backups, utilizing secure storage systems, and continuously monitoring risks to reduce vulnerabilities and protect sensitive patient information.


