Healthcare Third-Party Risk Management Trends 2025: What's Changing and Why It Matters
Post Summary
Cybersecurity in healthcare faces unprecedented challenges in 2025. With the rise of ransomware, supply chain attacks, and evolving regulations, healthcare organizations must adopt continuous monitoring, AI-driven tools, and stricter vendor oversight to protect patient data and maintain operations. Key highlights include:
- Ransomware-as-a-Service (RaaS): Easier access for criminals has increased attacks, targeting smaller vendors with weaker defenses.
- Cloud and M&A Risks: Complex vendor networks from cloud adoption and mergers introduce hidden vulnerabilities.
- AI in Risk Management: Predictive analytics and automation are transforming how vendors are assessed and monitored.
- Regulatory Pressure: Stricter HIPAA rules demand active monitoring and compliance with updated standards.
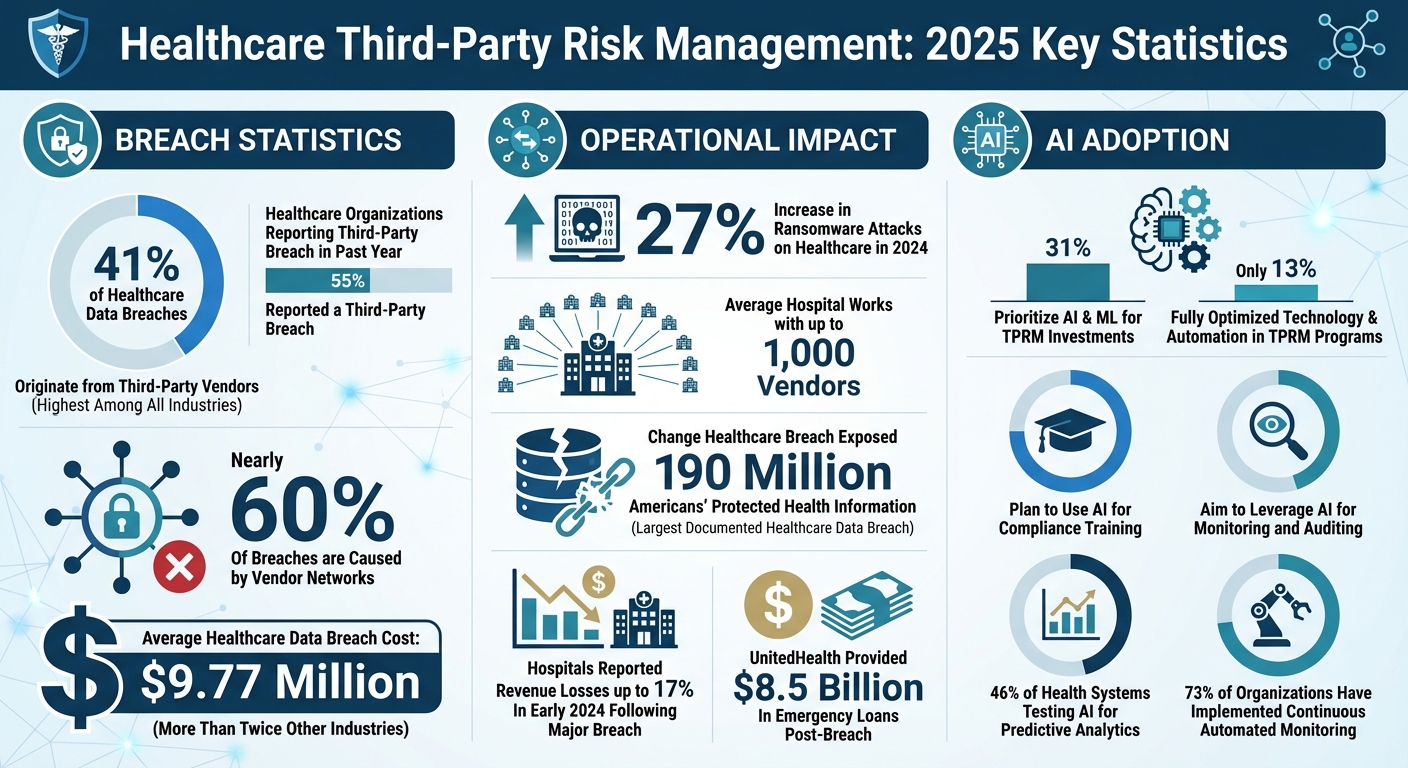
- Patient Safety at Risk: 41% of healthcare breaches stem from third-party vendors, with an average breach cost of $9.77 million.
Healthcare leaders need integrated strategies like zero trust architecture, real-time monitoring, and AI-powered assessments to address these risks effectively. Platforms like Censinet RiskOps™ simplify risk management, offering centralized tools for vendor assessment and compliance.
Healthcare Third-Party Risk Management Statistics 2025
Major Trends in Healthcare Third-Party Risk Management for 2025
Rising Ransomware and Supply Chain Attacks
Ransomware attacks are becoming a growing concern for healthcare organizations. The rise of Ransomware-as-a-Service (RaaS) has made it much easier for cybercriminals to launch attacks, even with minimal technical expertise [4]. Smaller healthcare supply chain businesses, often with weaker defenses, have become prime targets [4].
A significant challenge lies in the underdeveloped third-party risk management practices within many healthcare organizations. Without consistent controls or real-time monitoring, changes in a vendor's security posture - or even breaches - can go unnoticed for extended periods, leaving organizations vulnerable [3].
The complexity of modern supply chains further complicates these risks. Healthcare providers are now contending with "nth-party risks", where vulnerabilities extend beyond direct third-party relationships [2]. Cybercriminals are exploiting these extended networks, and experts predict that AI will increasingly be used to supercharge supply chain attacks. Tools like real-time mapping and self-evolving malware are expected to make these threats even more sophisticated [4]. These challenges are compounded by additional risks stemming from cloud migrations and mergers.
Cloud Adoption and M&A Risks
The growing reliance on cloud-based systems and a surge in healthcare mergers and acquisitions have reshaped the risk landscape. These changes have created a sprawling and intricate web of third-party relationships, making it difficult to track and manage every vendor [5][7]. Cloud transitions and acquisitions often introduce new vulnerabilities, many of which can remain hidden.
A stark example of these interconnected risks is the February 2024 ransomware attack on Change Healthcare. Stolen employee credentials and the absence of multi-factor authentication allowed cybercriminals to disrupt prescription drug processing nationwide for weeks. This breach exposed the protected health information of 190 million Americans, marking it as the largest documented healthcare data breach to date. The fallout was severe - UnitedHealth had to provide $8.5 billion in emergency loans, and hospitals reported revenue losses of up to 17% in early 2024 [5].
Kapish Vanvaria, EY Global Risk Consulting Leader, remarked, “Third-party relationships have never been more complex and more numerous” [7].
This growing complexity calls for a more integrated approach to risk management. Effective collaboration across departments like information security and procurement is essential [7]. In this environment, AI is emerging as a key tool to navigate and address these challenges.
AI Integration in Third-Party Risk Management
Artificial intelligence is transforming how healthcare organizations manage vendor risks. AI-powered tools now enable predictive analytics, integrate threat intelligence, monitor domains, and provide automated alerts - all within vendor risk dashboards that offer real-time insights [2].
This shift is reflected in investment priorities. In a recent survey, 31% of organizations identified AI and machine learning capabilities for tasks like enhanced due diligence and contract monitoring as their top focus for future investments in third-party risk management (TPRM) [8]. Monitoring third parties through data-driven methods ranked second at 28%, followed by automating due diligence processes at 27% [8].
Despite this progress, adoption of AI in TPRM remains in its early stages. Only 13% of companies have fully optimized technology and automation in their programs [8]. However, momentum is building - 75% of healthcare providers plan to use AI for compliance training and education, and 45% aim to leverage AI for monitoring and auditing activities [9].
The real promise of AI lies not just in automating existing processes but in completely rethinking how risks are identified, tracked, and managed across the entire third-party ecosystem. By addressing vulnerabilities in cloud systems and supply chains, AI is helping healthcare organizations stay ahead of emerging threats [8].
How Regulatory Changes Affect Third-Party Risk Management
HIPAA and OCR Updates for 2025
Healthcare organizations are now under heightened pressure to manage their third-party relationships more effectively, thanks to updated HIPAA enforcement rules. Under these changes, covered entities can be held responsible for violations by their business associates if those violations were either known or could have been reasonably identified[1]. This shift means that occasional vendor reviews are no longer enough - ongoing, active monitoring is now a must to ensure the protection of sensitive health information.
Another critical update involves Business Associate Agreements (BAAs). If a BAA doesn’t fully comply with HIPAA standards, it’s deemed invalid. In such cases, any sharing of patient data under that agreement would be considered an unauthorized disclosure, potentially leading to serious violations[1].
These new HIPAA and OCR guidelines mark a significant shift, signaling broader changes in how third-party risk management is regulated across the healthcare sector.
What These Changes Mean for Healthcare Organizations
The rise in cyber threats has already pushed healthcare organizations to strengthen their risk management strategies. These new regulatory updates add another layer of urgency, requiring organizations to adopt continuous, organization-wide risk management programs. Instead of addressing risks in isolated areas, healthcare providers are now moving toward integrated strategies that improve compliance across multiple regulations. This approach not only enhances oversight but can also reduce the complexity of meeting various regulatory demands[1].
U.S. agencies like the SEC are also stepping up their expectations, calling for more detailed documentation and monitoring practices to align with stricter global compliance standards[2]. To keep up with these evolving requirements, many healthcare organizations are turning to automated platforms. These tools are designed to adapt in real time to new regulatory changes, making it easier for organizations to stay compliant while managing the growing complexities of third-party risks[2].
Why Third-Party Risk Trends Matter: Effects on Patient Safety and Healthcare Operations
The growing complexity of third-party risks in healthcare is more than just a cybersecurity concern - it’s a direct threat to patient safety and operational stability. These risks highlight the need for stronger risk management strategies to protect both patients and healthcare systems.
Patient Safety and PHI Breaches
Third-party vendors have become a major weak point for healthcare data security. In 2024, 41% of all healthcare data breaches originated from third-party vendors - a higher percentage than any other industry sector[12]. With the average cost of a healthcare data breach hitting $9.77 million, healthcare remains the most expensive industry for data breaches[11][12].
These aren’t just numbers - they represent real patients whose care can be disrupted. 55% of healthcare organizations reported a third-party breach in the past year, directly affecting patient safety and continuity of care[11].
The problem becomes even more daunting when you realize that the average hospital works with up to 1,000 vendors, many of whom rely on their own subcontractors[10]. This creates a ripple effect, known as "nth-party risk", where vulnerabilities multiply across the supply chain. Hospitals also depend on thousands of connected devices, with larger facilities managing tens of thousands. Many of these devices are outdated or unsupported, further expanding the attack surface[10].
These vulnerabilities don’t just risk data exposure - they lead to operational breakdowns that can endanger lives.
Operational and Financial Impacts
When third-party systems are compromised, the consequences extend far beyond data breaches. Ransomware attacks on healthcare increased by 27% in 2024, with cybercriminals targeting third-party providers to amplify their reach and maximize ransom demands[12].
Operational disruptions are inevitable when vendor systems fail. For example, outdated, paper-based prior authorization processes - often outsourced to third parties - slow down care delivery and waste valuable resources for both providers and payers[13]. Additionally, siloed health information from disconnected vendor systems limits an organization’s ability to anticipate patient needs or provide proactive care[13].
The financial toll is staggering. Healthcare organizations face higher compliance costs and risk regulatory fines under stricter HIPAA enforcement rules. To mitigate these risks, they must invest in continuous monitoring, thorough due diligence, and robust incident reporting systems. On top of that, the reputational damage from a breach or service disruption can be long-lasting and costly to repair[11].
sbb-itb-535baee
How to Address Healthcare Third-Party Risks in 2025
To effectively manage third-party risks, healthcare organizations need to move from a reactive stance to a model of continuous monitoring. The Change Healthcare incident serves as a stark reminder that system segmentation, reliable backups, and regularly tested business continuity plans are essential to avoid disruptions[5]. This shift requires rethinking traditional vendor assessments and adopting more proactive, ongoing strategies.
Risk Management Tactics That Work
Effective third-party risk management begins with continuous monitoring and predictive analytics[5][7]. The old approach of static, periodic assessments is no longer sufficient. Instead, healthcare systems must adopt real-time monitoring to track vendor behavior, data exchanges, and any warning signs of potential issues[2]. This involves keeping tabs on vendor performance throughout the year, not just during annual reviews.
Layered defenses are also critical. Network segmentation helps limit lateral movement within systems, reducing the risk of widespread breaches. Backup systems ensure that critical patient data remains accessible, even during ransomware attacks. And business continuity plans? They need to be more than just paperwork - they should be tested regularly to ensure they work when it matters most[5]. Together, these measures create multiple layers of protection against third-party vulnerabilities.
Another key element is implementing strong access controls to further safeguard sensitive data.
Using Zero Trust Architecture for Vendors
Zero Trust principles operate on a simple but powerful idea: no vendor should be trusted by default, even if they've had a flawless track record in the past. Every access request must be verified, and permissions should be limited to only what's absolutely necessary for the vendor to do their job. This is especially important in today’s multicloud environments, where data flows across various platforms and providers[15].
Given the high value of patient data, healthcare systems are frequent targets for cyberattacks[15]. Zero Trust architecture reduces the attack surface by limiting vendor access points and continuously verifying credentials. By ensuring vendors can only access the systems they need - and nothing more - the risk of damage from a compromised account drops significantly.
Using AI and Automation for Third-Party Assessments
AI and machine learning are changing the game for vendor risk assessments in healthcare. These technologies offer advanced capabilities like anomaly detection, real-time data analysis, and automated identification of inconsistencies in vendor documentation[7]. Automation speeds up the assessment process, enabling quicker, data-driven decisions and reducing the potential for human error or bias[2].
That said, automation works best when paired with human oversight. AI tools can handle routine tasks like processing vendor questionnaires in seconds, but human expertise is still crucial for evaluating complex risks and making the final call. This blend of automation and human judgment allows risk teams to focus on high-priority issues while maintaining accuracy and efficiency. It’s a scalable approach that keeps pace with the growing demands of third-party risk management.
How Censinet RiskOps™ Addresses 2025 Healthcare Third-Party Risk Trends
Censinet RiskOps™ is designed to tackle the growing challenges of third-party risks in healthcare. Instead of relying on fragmented tools or manual processes, it offers a centralized platform that manages every aspect of cyber risk. From vendor assessments to organization-wide risk visualization, this unified solution addresses the key issues healthcare systems face in 2025: increasing cyberattacks, complex vendor networks, and the demand for quicker, more precise risk management. Let’s explore how its components simplify the process.
Accelerating Vendor Assessments with Censinet AITM
Censinet AITM transforms how vendor assessments are conducted. Vendors can now complete security questionnaires in seconds, cutting down what used to take days or even weeks. The system automatically summarizes vendor evidence and documentation, removing the need for time-consuming manual reviews. It also identifies critical integration details and fourth-party risks, uncovering vulnerabilities hidden in vendors' supply chains.
Beyond assessments, Censinet AITM generates detailed risk summary reports by analyzing all relevant data. This gives risk teams a complete picture without the manual workload. The result? Healthcare organizations can mitigate risks faster, allowing them to oversee more vendors without requiring larger teams.
AI Governance and Risk Visualization
Censinet AI acts like air traffic control for AI governance, ensuring that key findings and tasks are routed to the right people for review and approval. It automates routine tasks - like validating evidence and drafting policies - while leaving critical decisions in the hands of governance teams.
The platform’s intuitive AI risk dashboard brings real-time data into one place, offering a clear view of all AI-related risks, policies, and tasks across the organization. This centralized visibility ensures that the right teams address the right issues promptly. With configurable rules and review processes, automation complements human judgment, keeping risk teams in control.
Adapting to Organizational Needs with Scalable Solutions
Censinet provides three flexible options to fit the unique needs of healthcare organizations. Systems can choose to use the Censinet RiskOps™ platform internally, outsource entirely with managed services, or opt for a hybrid model that blends software with expert support. This adaptability ensures organizations can scale their risk management efforts based on their staffing, budget, and operational priorities - adjusting as their needs change without being tied to a rigid service model.
Conclusion: Managing Healthcare Third-Party Risk in 2025 and Beyond
Key Takeaways for Healthcare Leaders
Managing third-party risks in healthcare is no longer a task that can be handled with occasional check-ins. It requires constant vigilance and proactive strategies. With 55% of healthcare organizations reporting a third-party breach and the average cost of a healthcare data breach now reaching $9.77 million - more than twice the average for other industries - the urgency is clear [6]. The fallout from incidents like the Change Healthcare breach highlights how a single compromised vendor can disrupt entire systems.
To address these challenges, continuous and automated monitoring is the way forward. Already, 73% of organizations have implemented such solutions [3]. Instead of relying on generic questionnaires, healthcare systems must adopt risk assessments tailored to each vendor’s specific role and the type of data they handle. This shift reflects the broader move from periodic evaluations to real-time monitoring. As Ross Anderson, a recognized leader in healthcare cybersecurity, aptly put it:
Risks cannot be managed better until they can be measured better [5].
These strategies emphasize the importance of leveraging advanced tools to safeguard healthcare operations effectively.
How Technology Helps Secure the Future
Technology is at the heart of modernizing risk management in healthcare. With vendor networks responsible for nearly 60% of breaches [14], the need for advanced solutions is undeniable. Tools powered by AI, already being tested by 46% of health systems for predictive analytics [7], offer capabilities that go beyond manual oversight. They can analyze data in real time, detect patterns, and predict potential threats before they escalate.
Platforms like Censinet RiskOps™ tackle these challenges by combining speed, accuracy, and scalability. Whether deployed as a standalone platform, a managed service, or a hybrid approach, these solutions centralize risk management, automate repetitive tasks, and ensure human oversight remains focused on critical decisions. As regulations tighten and vendor ecosystems grow more intricate, adopting such technologies becomes essential for maintaining patient safety and ensuring uninterrupted operations in the years ahead.
FAQs
How is AI transforming third-party risk management in healthcare?
AI is transforming how third-party risk is managed in healthcare by simplifying complex processes and improving decision-making. It allows for real-time risk evaluations, automates vendor assessments, and flags unusual patterns that might slip through the cracks. Through predictive analytics, AI can even anticipate potential risks, giving organizations the chance to act before problems arise.
This technology not only boosts the efficiency and precision of risk management but also helps healthcare providers protect sensitive information and stay aligned with regulatory standards. By leveraging AI, teams can dedicate more time to high-level strategies while cutting down on manual tasks and reducing the likelihood of errors.
What are the updated HIPAA rules for managing vendor relationships in 2025?
The 2025 updates to HIPAA rules bring some important changes to how organizations manage their vendor relationships. Among the new requirements are mandatory data inventories, enhanced risk assessments, and tighter control over vendors and subcontractors. To bolster data security, organizations must now adopt measures like multi-factor authentication, encryption, and formal incident response plans.
Another key update is the introduction of annual compliance audits and more stringent terms for Business Associate Agreements (BAAs). These agreements now require vendors to report any breaches within 24 hours. These changes are designed to provide stronger safeguards for sensitive health information and ensure vendors adhere to higher security expectations.
Why is continuous monitoring crucial for cybersecurity in healthcare?
Continuous monitoring plays a crucial role in healthcare cybersecurity by spotting and addressing threats in real time. Early detection of vulnerabilities allows organizations to act quickly, shielding sensitive patient information and keeping their systems secure.
This forward-thinking strategy enables healthcare providers to adapt to emerging risks without delay, reducing operational disruptions and preserving trust in their services. In a field where patient safety and privacy are non-negotiable, continuous monitoring serves as a vital line of defense against cyber threats.
Related Blog Posts
- How to Conduct Effective Third-Party Risk Assessments
- Beyond Vetting: Continuous Monitoring Strategies for Third-party Risk Management Excellence
- Healthcare Third-Party Risk Management Trends 2025: What's Changing and Why It Matters
- Why 89% of Healthcare Data Breaches Involve Third-Party Vendors (And How to Prevent Them)


