Hidden Risks in Vendor Certification for Healthcare
Post Summary
Vendor certifications in healthcare, like SOC 2, ISO 27001, and HITRUST, may not provide the security you think they do. Many organizations rely on these certifications without deeper analysis, leaving critical gaps that can lead to breaches, financial losses, and compliance issues.
Key points include:
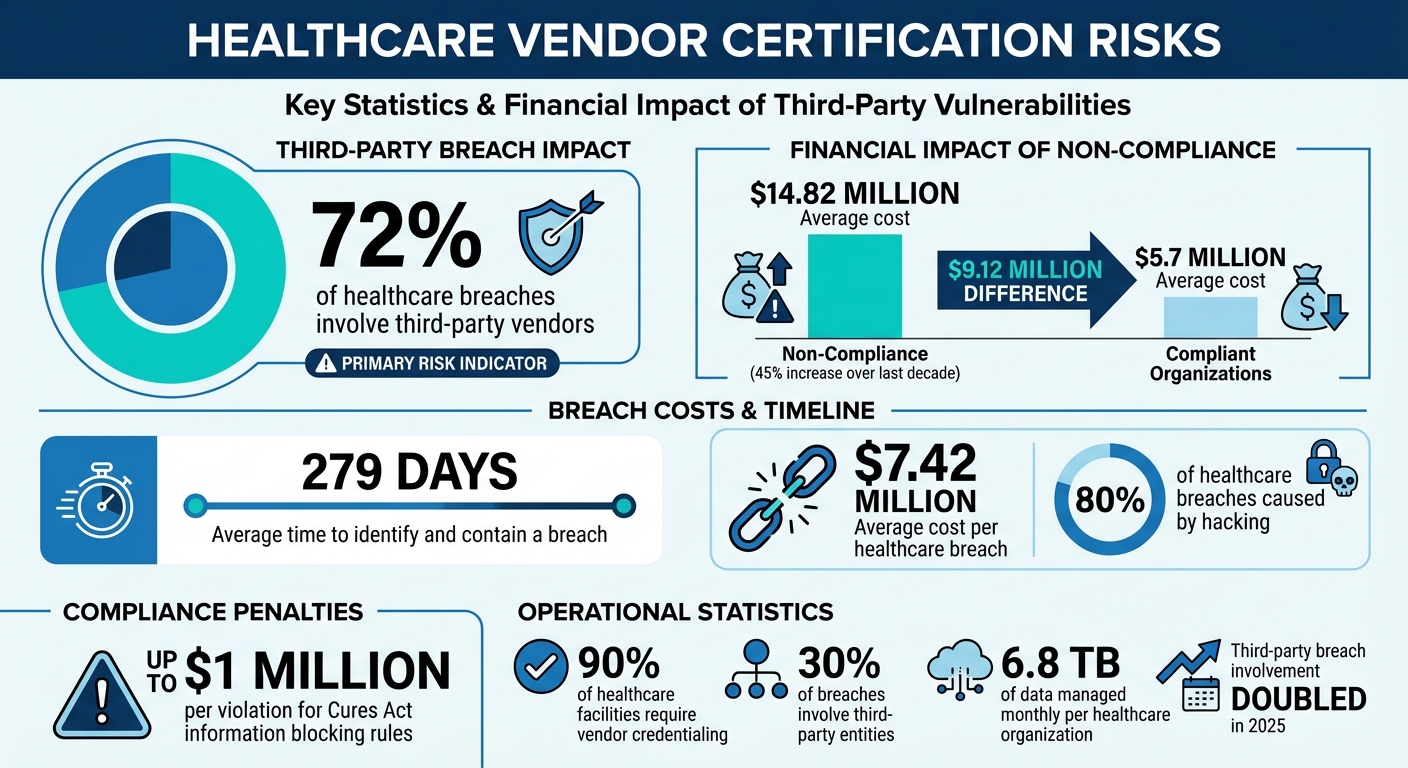
- 72% of healthcare breaches involve third-party vendors.
- Certifications often focus on a single point in time, ignoring evolving risks.
- Fourth-party vendors (subcontractors) create unseen vulnerabilities.
- Inconsistent standards across states and systems delay processes and increase costs.
- Non-compliance costs average $14.82 million, compared to $5.7 million for compliant organizations.
To tackle these risks, healthcare providers need centralized, continuous vendor risk management, leveraging tools like Censinet RiskOps™ for automated assessments, real-time alerts, and streamlined processes. Without proper oversight, outdated certifications can create a false sense of security, putting patient data and organizational integrity at risk.
Healthcare Vendor Certification Risks: Key Statistics and Compliance Costs
Inconsistent Certification Standards
Lack of Standardization Across Organizations
In the U.S., healthcare facilities operate without a unified federal standard for certification, instead relying on varied guidelines from organizations like The Joint Commission, the CDC, and the American College of Surgeons [3]. This fragmented approach means that even facilities within the same hospital system can enforce different policies, creating a patchwork of requirements.
Alana Smart from NMS Health highlights the issue:
"There is no official federal standard, and at times these requirements can differ slightly depending on the organization." [3]
Adding to the complexity, vendors must navigate state-specific regulations, as licensure and enforcement vary significantly across all 50 states [4][5]. On top of that, many healthcare organizations use different vendor credentialing platforms that don’t communicate with one another [3]. This forces vendors to repeatedly submit the same documentation for each facility or system they work with, wasting time and resources. To mitigate these inefficiencies, organizations can automatically answer security questionnaires using centralized documentation.
Operational Impacts of Inconsistent Standards
These inconsistencies create a host of operational headaches. While 90% of healthcare facilities require vendor credentialing, the lack of standardization often delays the process by weeks [3]. Vendors frequently encounter unexpected credentialing demands, which can delay critical services [3].
The financial toll is steep. Non-compliance costs have soared to an average of $14.82 million - up 45% over the last decade - compared to $5.7 million for organizations that maintain proper compliance [5]. Many facilities still rely on manual, paper-based systems, which increase the risk of human error and make it nearly impossible to keep track of certification expirations across multiple vendors [2].
These delays don’t just drain administrative resources - they also heighten certification vulnerabilities. Without streamlined processes, healthcare organizations face greater healthcare supply chain security challenges, underscoring the need for more effective risk management solutions.
sbb-itb-535baee
Risks in Point-in-Time Certifications
False Security from One-Time Audits
Imagine trusting a vendor's security because they passed an audit in January, only to discover that their security posture has deteriorated by July. This is the reality of point-in-time certifications - they provide a snapshot of a vendor's security at a specific moment, but they don't account for the ongoing risks that emerge as time passes. Factors like staff turnover or a software update introducing vulnerabilities can quickly undermine that initial certification, creating a false sense of security.
The stakes are especially high in healthcare, where breaches now average $7.42 million per incident and take an average of 279 days to identify and contain[6]. Even more concerning, third-party involvement in breaches doubled in 2025, with seven of the largest U.S. breaches happening in organizations that were technically compliant[6]. Island Networks captures this disconnect perfectly:
"Compliance validates that controls exist. It does not guarantee that those controls align to real world behavior across users, devices, applications, and third parties."[6]
This growing gap between perceived and actual security is particularly alarming, given that hacking is now responsible for about 80% of healthcare breaches[6]. The illusion of safety from outdated certifications highlights the urgent need for standards tailored to healthcare's unique challenges.
Mapping General Certifications to Healthcare Standards
Another issue with certifications is their scope. General certifications like SOC 2 focus on overall data security but don’t ensure compliance with healthcare-specific regulations like HIPAA. For example, a vendor may excel in general security practices but fall short when it comes to handling protected health information (PHI) in a way that meets HIPAA requirements.
The lack of a unified healthcare-specific standard forces vendors to chase multiple certifications to meet the diverse demands of different healthcare clients. This not only increases costs but also adds unnecessary complexity. Worse, these certifications often evaluate general security measures without addressing the unique risks tied to specific healthcare products or services.
This misalignment can lead organizations to prioritize vendors based on size or spending rather than the actual volume of sensitive electronic protected health information they handle. Such mismatched assessments leave supply chains vulnerable to breaches that could have been avoided with a proactive response strategy[6]. These gaps make managing healthcare data even more challenging, piling on operational risks that are already difficult to navigate.
Supply Chain and Fourth-Party Risks
Exposure Through Subcontractors and Supply Chains
When healthcare organizations certify a vendor, they often only see a fraction of the full picture. The real risk lies in the unseen layers - fourth-party vendors working behind the primary suppliers. Each API, data connector, or plugin represents a potential entry point for attackers, yet these integrations are rarely included in standard audits. These hidden vulnerabilities can directly compromise efforts to safeguard protected health information (PHI).
Supply-chain attacks have surged, nearly doubling in 2025, as hackers increasingly target vendors to infiltrate critical healthcare networks [1]. The widespread adoption of AI-driven SaaS tools and cloud services has introduced "shadow services", where subcontractors may handle PHI without proper Business Associate Agreements (BAAs). Inherent Security highlights this concern:
"As a vendor, you're not just a tech supplier, you're part of a larger ecosystem. Your security posture includes your vendors' vendors." [1]
This interconnected complexity is driving new regulatory expectations.
Increased Scrutiny with Evolving Regulations
With these hidden risks in mind, regulators have expanded their focus to cover the entire vendor ecosystem. Updates like the HTI-1 EHR certification requirements now emphasize the need for transparency in how electronic health information is exchanged and secured across all levels of the supply chain. Certification processes that once centered on a single vendor are no longer sufficient.
Healthcare systems are now employing detailed PHI data-flow diagrams to map out their vendor ecosystems and identify blind spots in vendor risk. Without this level of visibility, organizations face a higher likelihood of breaches - incidents that could often be avoided with a clearer understanding of who has access to their most sensitive data.
How Smart Hospitals Manage Vendor Access Safely: Credentialing, Compliance & Bedside Control
How Censinet RiskOps™ Reduces Certification Risks
Censinet RiskOps™ tackles certification challenges with automated, continuous solutions for managing vendor risks effectively.
Automated Third-Party Risk Assessments
Censinet RiskOps™ streamlines vendor evaluations by automating much of the process. Its Digital Risk Catalog™ provides instant access to security data and risk scores for 50,000 pre-assessed vendors, eliminating the need to duplicate evaluations.
With the 1-Click Sharing feature, vendors can fill out standardized questionnaires once and share them with unlimited healthcare customers. When vendors update their security posture, Delta-Based Reassessments focus only on the changes, cutting reassessment times to less than a day[7].
The platform also includes Automated Corrective Action Plans (CAPs), which identify security gaps from questionnaire responses and suggest remediation steps. These plans are tracked directly within the platform, ensuring quick action. Additionally, longitudinal risk records in the Cybersecurity Data Room™ replace static, one-time snapshots with a continuous history of security updates.
This level of automation lays the groundwork for improved visibility across the entire network.
Collaborative Risk Management and Compliance Monitoring
Beyond automation, Censinet RiskOps™ fosters collaboration to enhance risk visibility throughout the vendor ecosystem. With Nth Party Monitoring, organizations can track risks not only from direct vendors but also from fourth-party entities like cloud providers, addressing hidden vulnerabilities in the supply chain. Over 100 provider and payer facilities actively participate in the Censinet Risk Network, allowing organizations to share intelligence and strengthen their assessments.
The platform’s Risk Flags & Filters highlight missing compliance documents, such as Business Associate Agreements (BAAs), and identify vulnerabilities across the vendor portfolio. Real-time breach alerts notify users immediately of ransomware or data breaches affecting their vendors, eliminating the need for manual tracking. A centralized dashboard offers a comprehensive view of residual risks, making it easier to communicate compliance status to executives through a single, unified interface.
Strategies for Maintaining Certification Compliance
Centralized Risk Management Processes
To tackle certification vulnerabilities effectively, healthcare organizations need a centralized approach to risk management. A key step is centralizing vendor tracking by identifying weaknesses in manual workflows and categorizing vendors based on risk levels - critical, high, medium, or low. This ensures resources are allocated where they’re needed most. It’s important to remember that even low-risk vendors can pose significant threats, as about 30% of breaches now involve third-party entities[13].
Vendor questionnaires should be standardized, and contracts must clearly define cybersecurity obligations. Healthcare organizations are legally responsible for the actions of their vendors[10]. These contracts should include detailed compliance expectations, such as documented plans, codes of conduct, training programs, policies, conflict of interest disclosures, monitoring systems, audit protocols, and annual risk assessments[8].
Tracking KPIs and Certification Expirations
Maintaining compliance is an ongoing process that requires consistent monitoring of certifications and critical documentation. For instance, Business Associate Agreements (BAAs) and Notices of Privacy Practices must be regularly updated to align with HIPAA requirements for safeguarding electronic protected health information (ePHI)[11]. Keeping track of certification expiration dates, credential renewals, and access permissions is essential to avoid any compliance gaps.
Annual reviews of HIPAA protocols should include staff training, implementing encryption and multi-factor authentication (MFA), and updating BAAs in a timely manner. Additionally, organizations must prepare robust incident response plans and secure cyber insurance to mitigate risks[12]. Non-compliance with the Cures Act’s information blocking rules can result in fines of up to $1 million per violation[9], making it clear that tracking compliance metrics is not just a regulatory necessity - it’s a financial safeguard.
Given the scale of these requirements, relying solely on manual processes is no longer practical.
Using Technology for Scalability
With healthcare organizations managing an average of 6.8 TB of data each month, manual tracking systems are quickly becoming obsolete. Platforms like Censinet RiskOps™ offer the automation and centralization needed to handle these complexities. By addressing gaps in vendor certification risks, this technology ensures more efficient oversight. Its AI-powered governance dashboard routes critical findings to the right stakeholders, such as AI governance committees, enabling continuous monitoring. Real-time alerts replace outdated annual assessments, providing immediate visibility into emerging vendor risks.
Conclusion
Managing healthcare vendor certification is a serious compliance challenge that goes far beyond simple audits. The risks tied to inconsistent certifications, one-off audits, and untracked supply chains can lead to severe consequences - ranging from major breaches to hefty regulatory fines and operational chaos. With penalties climbing as high as $1 million per violation[9], lapses in vendor oversight are simply not an option.
To tackle these challenges, healthcare organizations must move away from outdated manual systems and embrace HIPAA-compliant vendor risk management. Modern tools allow for continuous monitoring, offering real-time insights into how vendor security measures evolve over time. This approach makes manual, static processes a thing of the past.
Censinet RiskOps™ steps into this gap by automating vendor risk assessments to overcome vendor adoption challenges and ensuring constant oversight across all vendor relationships. Its platform not only flags critical issues for the right stakeholders but also keeps oversight centralized. With AI-powered tools, organizations can scale their risk management efforts while still retaining the necessary human touch. This shift turns vendor certification into a proactive and strategic advantage, rather than a mere compliance checkbox.
The stakes are too high to delay action. Hidden risks in certification can lead to financial losses and damage to an organization’s reputation. To safeguard against these vulnerabilities, healthcare providers need to conduct detailed vendor audits, establish strong incident response plans, and secure cyber insurance as part of their core defenses[12]. By adopting risk-based strategies and leveraging specialized technology, organizations can protect patient data, meet regulatory requirements, and ensure their operations remain resilient across the entire vendor network.
In today’s environment of escalating threats and stricter regulations, the real question isn’t whether to modernize vendor certification - it’s how quickly organizations can adopt the tools and strategies needed to stay ahead of emerging risks.
FAQs
What should I check beyond a vendor’s SOC 2, ISO 27001, or HITRUST report?
When assessing a vendor, don't stop at reviewing their SOC 2, ISO 27001, or HITRUST reports. Take a closer look at their cybersecurity measures, HIPAA compliance, encryption protocols, incident response strategies, and risk management processes. It's equally important to confirm that their safeguards stay effective over time, adapting to new and emerging threats.
How can we continuously monitor vendor and fourth-party risk after onboarding?
To keep an eye on vendor and fourth-party risk effectively, healthcare organizations should rely on real-time tools. These tools help track vendor activities, their security measures, and compliance status. Automated platforms, combined with AI-driven analytics, can offer alerts and dashboards that provide a clear view of potential risks as they arise.
In addition, regular reassessments and a structured approach to managing issues are essential. This ensures any changes in vendor risk are handled quickly, helping organizations stay aligned with regulations like HIPAA while safeguarding patient data in the ever-evolving healthcare landscape.
What contract terms best protect PHI when vendors use subcontractors?
To keep Protected Health Information (PHI) secure, contracts should mandate that vendors make sure their subcontractors follow HIPAA regulations and protect PHI. This involves setting up HIPAA Business Associate Agreements (BAAs), which clearly define compliance responsibilities and data protection requirements for subcontractors.
Related Blog Posts
- How to Conduct Effective Third-Party Risk Assessments
- Beyond Vetting: Continuous Monitoring Strategies for Third-party Risk Management Excellence
- Healthcare Business Continuity Planning: Managing Vendor Dependencies and Risks
- Insurance and Benefits Administration Vendor Risk for Healthcare Organizations


