HIPAA Compliance for IoT Medical Devices
Post Summary
HIPAA compliance for IoT medical devices ensures that connected devices handling electronic protected health information (ePHI) meet privacy and security standards.
It protects sensitive patient data, prevents breaches, ensures regulatory compliance, and mitigates risks associated with outdated or insecure devices.
Challenges include incomplete device inventories, limited device capabilities for encryption and logging, and managing third-party risks.
Best practices include maintaining accurate device inventories, implementing encryption, using compensating controls for legacy devices, and conducting continuous risk assessments.
Organizations can secure devices by enforcing access controls, encrypting data in transit and at rest, and leveraging tools like Censinet RiskOps™ for risk management.
Vendors must adhere to HIPAA requirements, provide secure device designs, and sign Business Associate Agreements (BAAs) to ensure compliance.
IoT medical devices like infusion pumps and wearables revolutionize healthcare by collecting and transmitting patient data in real time. However, this data - classified as electronic protected health information (ePHI) - requires strict safeguards under HIPAA regulations. With growing cybersecurity threats, outdated device capabilities, and overlapping FDA requirements, healthcare organizations face mounting challenges in securing IoT ecosystems.
Here’s what you need to know:
Key solutions include:
Problem: Larger Attack Surface and Poor Device Visibility
Difficulty Tracking All IoT Devices
The rapid expansion of IoT medical devices in U.S. healthcare has created a daunting challenge: keeping track of them all. Hospitals now manage thousands of devices - everything from infusion pumps to wearables - spread across clinical networks. Each one that processes electronic protected health information (ePHI) becomes a potential target for cyberattacks. Yet many organizations struggle to maintain accurate inventories of these devices.
One of the main issues is that devices often connect to networks without proper registration. New devices might be added without IT teams being notified, resulting in unregistered equipment operating outside established security measures. To make matters worse, responsibility for these devices is often split between biomedical engineering, IT, and clinical departments. This lack of clear ownership means no single team has a complete understanding of what’s connected or how ePHI flows between devices. As a result, risk analysis efforts fall short.
Many healthcare organizations still rely on manual spreadsheets or outdated configuration management databases (CMDBs) to track devices. These methods quickly become outdated as devices are moved, loaned, or replaced. Surveys reveal that 60% of organizations lack comprehensive IoT inventories, leaving critical gaps in their security defenses.
Without a clear inventory, monitoring these devices becomes even harder.
Insufficient Monitoring and Audit Logs
Even when devices are accounted for, monitoring them effectively is a major hurdle. IoT medical devices are scattered across various network segments, making it difficult to centralize logs and correlate security events. Many devices lack robust logging capabilities, and their physical accessibility makes them vulnerable to tampering or unauthorized use.
This lack of monitoring creates compliance headaches. HIPAA mandates regular reviews of system activity under §164.308(a)(1)(ii)(D) and §164.312(b). However, when devices like infusion pumps fail to log access attempts or patient monitors don’t track configuration changes, it becomes nearly impossible for security teams to investigate breaches or demonstrate compliance.
Solutions: Complete Device Inventories and Continuous Risk Assessment
Addressing these challenges requires a unified approach to device discovery and risk assessment. Start with passive network monitoring and agentless scanners to automatically identify every device connected to clinical networks, including older, legacy equipment.
Automated discovery tools can track devices using MAC addresses and traffic patterns, feeding real-time data into a centralized CMDB. This ensures all ePHI touchpoints - whether on-premise or in the cloud - are documented and ready for HIPAA risk analysis.
For monitoring, leverage network telemetry and flow logs from firewalls and switches to approximate device activity when native logging isn’t available. Centralizing this data in a SIEM or security analytics platform allows for automated alerts on unusual behavior, such as unexpected protocols, off-hours activity, or communication with suspicious destinations.
Continuous risk assessments should replace outdated annual reviews. Assess devices during onboarding, after major changes, and periodically to keep up with evolving threats. Evaluate each device based on its exposure to ePHI, vulnerability status, and importance to patient care. Tools like Censinet RiskOps™ streamline this process by centralizing device assessments, automating compliance documentation, and managing remediation tasks. By addressing risks across PHI, medical devices, and supply chains, this platform helps bridge the gap between regulatory requirements and the realities of managing IoT devices.
Issue
HIPAA Impact
Practical Consequence
Incomplete device inventory
Undermines risk analysis and management for systems handling ePHI
Increases exposure to unknown devices; weakens patching and incident response
Unregistered IoT devices
ePHI may be processed outside documented safeguards
Devices may bypass security reviews, reducing visibility and increasing vulnerabilities
Distributed devices without logs
Hinders compliance with audit controls
Makes breach investigations and system activity reviews challenging
Problem: Meeting HIPAA Technical Safeguards with Limited Device Capabilities
Many IoT medical devices aren't equipped to handle the security demands required by HIPAA. Let's break down how healthcare organizations address these limitations by shifting critical security measures elsewhere. Devices like older infusion pumps, bedside monitors, and imaging systems often lack the processing power, memory, or advanced operating systems needed for encryption, robust authentication, or detailed logging [1]. These limitations make it tough - or even impossible - to implement HIPAA's technical safeguards, such as access controls, audit trails, data integrity measures, and secure data transmission, directly on the device [1][3].
Legacy equipment poses an even greater challenge. A 2022 Ponemon Institute study revealed that 56% of healthcare organizations experienced at least one cyberattack involving IoT or IoMT devices, many of which lacked modern security features [4]. Additionally, a large portion of medical devices in use today are over 5–10 years old. These older devices often lack native encryption, have limited mechanisms for updates, and rely on vendor-controlled firmware [4]. These shortcomings significantly increase the risk of exposing electronic protected health information (ePHI) and falling out of HIPAA compliance.
Since replacing all outdated devices isn't feasible overnight, healthcare organizations rely on compensating controls. By offloading demanding security tasks - like encryption and logging - to gateways, proxies, or backend systems, they ensure critical protections are in place without overburdening the devices themselves [1][2].
Implementing Access Controls and User Authentication
HIPAA requires that every individual accessing ePHI has a unique identifier, but many IoT devices can't support advanced access controls or user-specific logins. Small devices like sensors or monitors often lack the interfaces or processing capacity for such features, leading to shared logins on older equipment.
To work around this, organizations shift access control to centralized systems. For instance, device access can be tied to authenticated sessions on workstations or mobile apps, managed through directory services like Active Directory or LDAP [1][2]. Clinicians could log in via an EHR system, which then authorizes device commands. This ensures accountability without requiring complex logins on the devices themselves [2].
Multi-factor authentication (MFA) is another critical step. Deploying MFA at key entry points - such as remote management tools, VPNs, or clinical systems - adds a layer of security without disrupting workflows [2]. For example, clinicians might log in once per shift using MFA, with features like time-limited sessions or auto-logoff on shared workstations helping maintain compliance without unnecessary interruptions [1][2]. When direct device logins are unavoidable, techniques like smart cards or proximity badges paired with short PINs can provide secure and efficient authentication options [1][3].
Encrypting Data in Transit and at Rest
Once access controls are addressed, encryption becomes essential to protect data. While HIPAA treats encryption as "addressable", in practice, strong encryption is often expected - especially when transmitting ePHI over public or shared networks [1][3]. However, many older devices can't handle encryption protocols without sacrificing performance or battery life [1].
For data in transit, organizations should enforce TLS 1.2 or higher for all connections involving ePHI [1]. If a device can't support modern TLS, an edge gateway can terminate the encrypted session and communicate with the device over a secure, isolated network segment [1][2]. This strategy, combined with strict network segmentation, ensures data remains protected even when older devices are in use [1][2].
For data at rest, devices capable of encryption should use AES-256 for full-disk or volume-level encryption, covering both internal storage and removable media [1][2]. When full-disk encryption isn't an option, encrypting specific files or databases with AES-256 is a practical alternative. Keys should be stored securely, such as in hardware-backed keystores [1]. For devices with extremely limited storage, ePHI should be offloaded to secure servers as quickly as possible, with this process documented in risk assessments [1][3].
Network segmentation also plays a crucial role. Placing IoT devices on dedicated VLANs, controlling traffic with firewalls, and using micro-segmentation to fine-tune communication pathways all help meet HIPAA's technical safeguards. These measures reduce the potential impact of a breach and prevent vulnerable devices from becoming gateways to more sensitive systems [1][2][5].
Securing Firmware Updates and Software Supply Chains
Firmware updates are another critical area of vulnerability. To ensure device integrity, manufacturers should implement secure boot processes that verify cryptographic signatures on firmware before execution. This prevents tampered code from running [1][2]. Firmware must be digitally signed with strong keys stored in protected environments, and devices should only accept updates that pass signature validation and meet approved version baselines [1][2].
A secure firmware update process combines encrypted transport, robust authentication, and rollback capabilities. Updates should be delivered over TLS or IPsec from trusted servers, with devices verifying authenticity and integrity before applying changes [1]. In U.S. hospitals, updates are typically tested in non-production environments before being rolled out during scheduled maintenance windows to avoid disrupting patient care [2]. Rollback mechanisms ensure devices can revert to a stable version if an update fails, maintaining availability - a key HIPAA requirement [1][2].
Software Bills of Materials (SBOMs) are becoming essential for tracking third-party and open-source components in device software. This transparency helps identify vulnerabilities that could compromise ePHI [1][2]. The FDA now expects manufacturers to provide SBOMs for medical devices, enabling healthcare providers to assess risks, prioritize fixes, and implement protective measures. Platforms like Censinet RiskOps™ centralize SBOM data, offering continuous monitoring of risks across medical devices and clinical systems [1][2].
Challenge
HIPAA Requirement
Practical Solution
Limited CPU/memory for authentication
Unique user identification and access control
Authenticate at the workstation/app layer; use directory services (AD/LDAP) for centralized identity
Cannot support TLS natively
Transmission security (encryption in transit)
Terminate TLS at an edge gateway; isolate the device on a secure VLAN
Minimal storage for logs
Audit controls
Forward logs to a centralized SIEM; use network telemetry as a proxy
No encryption at rest
Encryption safeguard
Offload PHI rapidly to encrypted servers; implement physical safeguards and document risk
Vulnerable firmware updates
Integrity controls
Require signed updates, secure boot, and rollback protection; maintain SBOMs
Problem: Aligning HIPAA with FDA Requirements and 2025 Updates
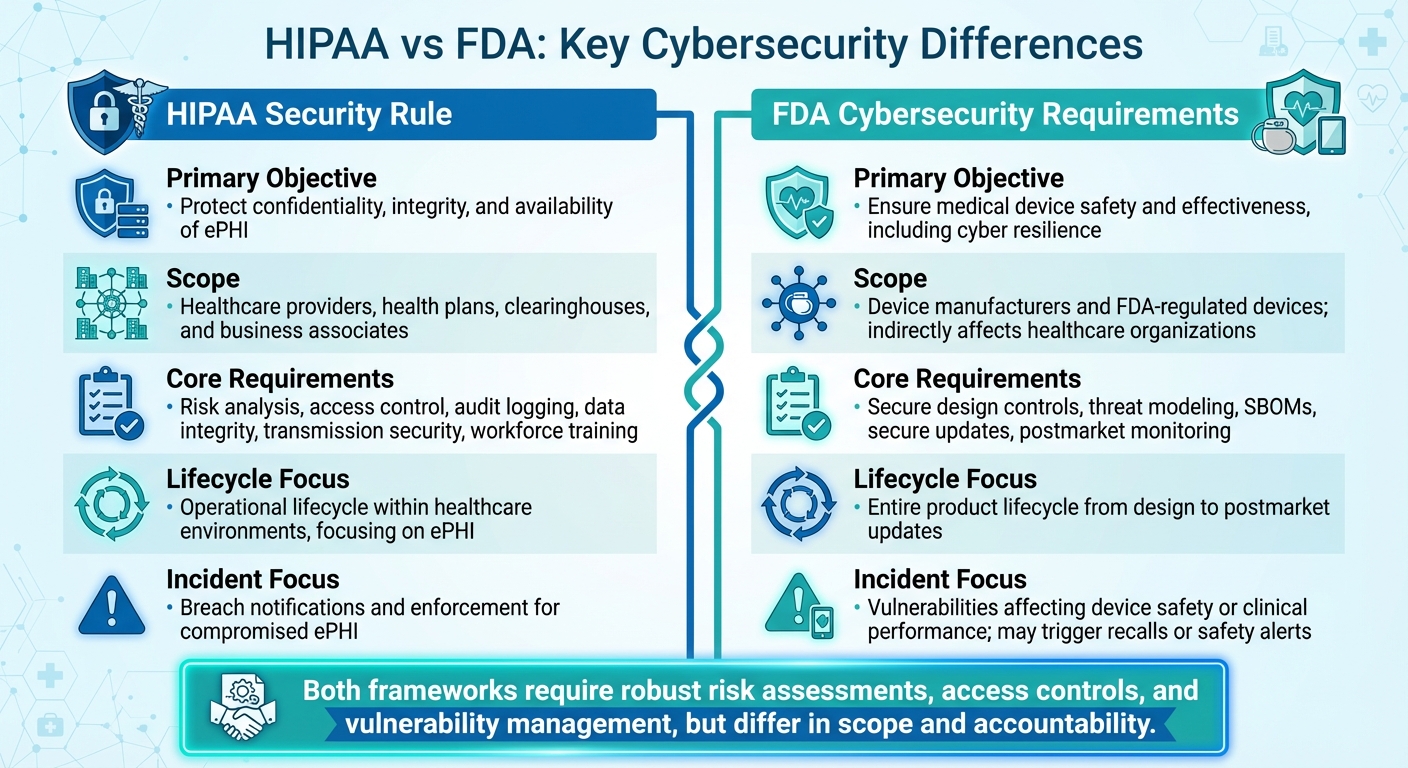
HIPAA vs FDA Cybersecurity Requirements for IoT Medical Devices
IoT medical devices face the dual challenge of complying with both HIPAA safeguards for electronic protected health information (ePHI) and FDA cybersecurity standards. HIPAA requires healthcare organizations to protect ePHI across their systems, while the FDA mandates that manufacturers prioritize cybersecurity throughout a device's lifecycle. Although these frameworks share common ground in areas like risk assessment, access control, and vulnerability management, their scope and accountability differ significantly. HIPAA focuses on securing ePHI within healthcare organizations, while the FDA emphasizes device safety and holds manufacturers responsible for secure engineering and lifecycle management.
In September 2023, the FDA released new guidance, "Cybersecurity in Medical Devices: Quality System Considerations and Content of Premarket Submissions." This update classifies cybersecurity issues as potential quality defects under the Quality System Regulation, making inadequate security grounds for enforcement actions. Manufacturers are now required to provide detailed threat models, Software Bills of Materials (SBOMs), secure update mechanisms, and postmarket vulnerability management processes. Meanwhile, HIPAA standards are tightening further, with 2025 updates emphasizing vulnerability scanning, continuous risk management, and robust documentation for networked assets, including IoT devices. To meet these evolving expectations, organizations must integrate FDA-provided documentation - such as SBOMs and security whitepapers - into their HIPAA risk analyses and ensure medical devices are part of enterprise vulnerability scanning, asset inventories, and incident response plans. The following sections explore the differences between HIPAA and FDA requirements, strategies for collaboration, and steps for maintaining compliance.
Understanding HIPAA and FDA Cybersecurity Differences
HIPAA and FDA regulations address distinct but overlapping concerns. HIPAA aims to protect the confidentiality, integrity, and availability of ePHI, requiring safeguards like risk analysis, access controls, audit logging, and transmission security. On the other hand, the FDA focuses on ensuring device safety and effectiveness by embedding cybersecurity into every stage of a device's lifecycle, from design and development to postmarket monitoring.
While both frameworks demand robust risk assessments, access controls, and quick responses to vulnerabilities, their priorities diverge. HIPAA is technology-neutral and outcome-focused, while FDA guidance is more detailed, specifying engineering controls such as secure update mechanisms and threat modeling. HIPAA emphasizes breach notifications to the Department of Health and Human Services (HHS) and the Office for Civil Rights (OCR), whereas the FDA prioritizes threats that could compromise patient safety or device functionality, potentially requiring regulatory reporting or even recalls.
A common challenge arises when healthcare delivery organizations (HDOs) deploy FDA-cleared devices but fail to integrate them into enterprise logging or access control systems, creating gaps in HIPAA compliance. Conversely, aggressive security measures like restrictive network controls or frequent patching may conflict with FDA requirements, potentially affecting device performance or voiding manufacturer support.
Aspect
HIPAA Security Rule
FDA Cybersecurity Requirements
Primary Objective
Protect the confidentiality, integrity, and availability of ePHI.
Ensure medical device safety and effectiveness, including resilience against cyber threats.
Scope
Applies to healthcare providers, health plans, clearinghouses, and business associates.
Focuses on device manufacturers and FDA-regulated devices; indirectly affects healthcare organizations.
Core Requirements
Risk analysis, access control, audit logging, data integrity, transmission security, and workforce training.
Secure design controls, threat modeling, SBOMs, secure updates, and postmarket monitoring.
Lifecycle Focus
Covers operational lifecycle within healthcare environments, focusing on ePHI.
Encompasses the entire product lifecycle, from design to postmarket updates.
Incident/Breach Focus
Centers on breach notifications and enforcement for compromised ePHI.
Focuses on vulnerabilities that could affect device safety or clinical performance, potentially triggering recalls or safety alerts.
These differences highlight the need for a coordinated approach to governance.
Building Cross-Functional Governance Teams
Aligning HIPAA and FDA requirements requires collaboration across departments. Governance teams should include representatives from IT/security, clinical engineering, compliance/privacy, legal/regulatory, procurement, and clinical leadership. Each group plays a critical role:
Establishing formal workflows for evaluating devices, scoring risks, and responding to incidents is essential. Create a single intake process for new IoT devices that triggers security reviews, clinical evaluations, and regulatory assessments before purchase. Regular governance meetings should review risk dashboards, vendor performance, and regulatory updates. Tools like centralized risk platforms (e.g., Censinet RiskOps™) can consolidate device inventories, vendor assessments, and control evidence, streamlining audits and investigations.
When procuring devices, require vendors to demonstrate FDA cybersecurity compliance and align their documentation with HIPAA controls. Include security criteria in RFPs and procurement checklists, such as encryption, authentication, logging, patching, and secure update mechanisms. Standardized security questionnaires and third-party risk assessments can further evaluate how well vendors support HIPAA requirements. Configuration baselines, like network segmentation and mandatory password changes, should align with both HIPAA and FDA recommendations.
Maintaining Ongoing Compliance
Staying compliant involves continuous risk assessments, regular vulnerability scanning, patch tracking, and thorough documentation. Key performance metrics include:
Tracking these metrics on a centralized dashboard demonstrates due diligence for both HIPAA and FDA expectations. Maintain documentation that links each IoT device to risk assessments, technical controls, and vendor attestations. For HIPAA, this serves as evidence of safeguards and risk management. For FDA, detailed records of device behavior, mitigations, and vendor communications support coordinated vulnerability responses and protect patient safety.
Avoid misalignments by conducting joint reviews between IT/security, clinical engineering, and compliance before changing network or patching strategies. Follow manufacturer and FDA guidance when designing controls, and document risk-justified compensating measures when ideal configurations aren't feasible. A unified compliance strategy ensures both HIPAA and FDA standards are met, strengthening IoT security and safeguarding patient data and device performance.
sbb-itb-535baee
Problem: Third-Party and Supply Chain Security Risks
IoT medical devices operate within intricate networks involving manufacturers, cloud providers, software vendors, component suppliers, and integration partners. This interconnected environment increases the risk of cyberattacks and complicates compliance with HIPAA regulations. For example, an infusion pump manufacturer might depend on a third-party cloud platform for remote monitoring, or a patient monitoring system could integrate with several analytics vendors. Each of these connections opens up potential vulnerabilities that may expose electronic protected health information (ePHI). Healthcare organizations are responsible for ensuring that every entity handling patient data adheres to HIPAA requirements, even when those entities are multiple layers removed from the primary device vendor.
The challenge intensifies when organizations learn that their device vendors rely on sub-processors they haven't vetted. For instance, a cardiac monitor might transmit data through the manufacturer’s cloud provider, which could then outsource data storage or analytics to additional vendors. Under HIPAA's Security Rule (45 CFR §164.308), healthcare providers must assess risks across the entire supply chain, even if they lack direct visibility into all parties involved. Adding to this complexity, the FDA’s September 2023 guidance mandates that Software Bills of Materials (SBOMs) list every third-party component in a device, potentially uncovering unpatched vulnerabilities. These realities demand rigorous vendor evaluations and a more streamlined approach to managing these risks.
Conducting Consistent Vendor Security Assessments
HIPAA requires healthcare organizations to conduct regular risk assessments for all vendors handling ePHI. However, inconsistent evaluations often leave gaps. While primary device manufacturers may undergo thorough scrutiny, other critical players - like cloud platforms, maintenance contractors, or software providers - are sometimes overlooked. This selective assessment approach can lead to breaches caused by inadequately vetted partners.
To enforce vendor compliance, healthcare organizations should use Business Associate Agreements (BAAs). Any entity that creates, receives, maintains, or transmits ePHI on behalf of a healthcare provider must sign a BAA outlining its responsibilities to protect patient data. In IoT ecosystems, this includes device manufacturers, cloud hosting providers, remote monitoring services, and even sub-vendors involved in data analytics. Standardized security questionnaires can help ensure vendors meet key security benchmarks, such as employing strong encryption (e.g., TLS 1.2+ for data in transit and AES-256 for data at rest), implementing multi-factor authentication, maintaining detailed audit logs, and managing vulnerabilities effectively. These assessments should be conducted annually or after major changes, such as deploying new devices or acquiring new vendors. Integrating these reviews into procurement policies and training staff to recognize IoT-specific risks further strengthens the process.
Managing Sub-Vendor and Integration Risks
Sub-vendors and integration partners often introduce hidden vulnerabilities. For example, a device manufacturer might outsource cloud storage or connect with an external analytics platform, creating opportunities for unauthorized access or breaches. Mapping data flows across all integration points is essential to identify vulnerabilities and document every entity interacting with ePHI within the IoT ecosystem.
SBOMs can be particularly useful in uncovering third-party components embedded in medical devices. These documents list software libraries, firmware modules, and open-source packages used by manufacturers. Reviewing SBOMs for known vulnerabilities and setting up processes - like quarterly reviews - can help organizations stay updated on potential risks. Conducting interoperability assessments at integration points can also highlight issues, ensuring encrypted communication, properly configured access controls, and detailed audit logs are in place. Maintaining an inventory of sub-processors and requiring BAAs that mandate disclosure of sub-processors provide additional visibility and enable timely risk mitigation. To manage these fragmented risks effectively, centralized platforms become a necessity.
Using Centralized Platforms for Vendor Risk Management
Managing vendor risks manually - using spreadsheets and scattered documentation - creates compliance gaps, especially for healthcare organizations dealing with dozens or even hundreds of IoT devices and their associated vendors. Centralized platforms can simplify this process by automating risk assessments, standardizing evidence collection, and offering real-time visibility into remediation efforts.
One such solution is Censinet RiskOps™, which streamlines third-party risk assessments across a network of over 50,000 vendors and products in the healthcare industry. The platform allows vendors to complete security questionnaires and upload supporting documentation - like SBOMs, attestation reports, and security certifications - which can then be shared with multiple healthcare clients. This collaborative approach reduces redundant assessments while ensuring thorough and consistent vendor evaluations.
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required." - Terry Grogan, CISO, Tower Health
"Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with." - James Case, VP & CISO, Baptist Health
The platform's automated workflows help track remediation tasks, send alerts for assessment renewals, and maintain a centralized repository of documentation to demonstrate HIPAA compliance. For IoT medical devices, organizations can link device inventories to vendor assessments, map data flows across supply chains, and generate reports showing how technical safeguards address risks. Cybersecurity benchmarking features also allow organizations to compare their vendor risk management practices against industry standards, identify weaknesses, and demonstrate due diligence. For healthcare providers navigating the challenges of HIPAA compliance, FDA regulations, and IoT security, platforms like Censinet RiskOps™ offer the scalability and collaborative tools needed to manage third-party and supply chain risks effectively.
Conclusion: Building Better IoT Security for HIPAA Compliance
Securing IoT medical devices under HIPAA involves tackling four key challenges: managing a broad attack surface, implementing technical safeguards on devices with limited capabilities, aligning HIPAA requirements with changing FDA cybersecurity standards, and addressing third-party supply chain risks. These factors directly influence the likelihood of data breaches, the potential for OCR enforcement, and patient safety in critical clinical environments.
The strategies discussed here emphasize a comprehensive risk management approach. Start by creating a complete inventory of devices using automated discovery tools and configuration baselines. For legacy devices with limited security capabilities, deploy compensating controls like network segmentation, secure gateways, and encryption offloading. Establish cross-functional governance teams to align HIPAA, FDA, and internal policies. Standardize vendor assessments with IoT-specific security requirements, enforce Business Associate Agreements, and continuously monitor high-risk vendors. These foundational steps are essential for effective risk management.
Once accurate inventories and structured controls are in place, continuous monitoring becomes critical for quick detection and response. Integrate device inventories with tools like SIEM, behavioral analytics, and network detection systems to identify anomalies promptly. Conduct regular vulnerability assessments tailored to medical devices, apply risk-based patching, and stay updated on FDA postmarket cybersecurity notices to address emerging vulnerabilities swiftly.
Platforms like Censinet RiskOps™ bring everything together by consolidating device inventories, vendor assessments, and control evidence into a centralized system mapped to HIPAA requirements. The platform’s collaborative risk network - encompassing over 50,000 vendors and products in the healthcare sector - enables standardized security questionnaires, automated remediation tracking, and executive-level reporting on IoT-related risks. By streamlining processes across security, compliance, clinical engineering, and procurement teams, Censinet RiskOps™ supports the scalable risk management model that IoT medical device environments require.
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare." - Matt Christensen, Sr. Director GRC, Intermountain Health
Treat IoT security as an integral part of clinical infrastructure with measurable KPIs such as the percentage of devices inventoried and classified, time-to-remediate critical vulnerabilities, and vendor assessment coverage. Plan for the entire device lifecycle - from procurement to secure decommissioning - and regularly test incident response plans with IoT-specific scenarios, adjusting controls as FDA and HHS guidelines evolve. Strengthening these capabilities not only enhances resilience but also transforms HIPAA compliance into a strategic asset that supports clinical excellence.
FAQs
What steps can healthcare organizations take to meet both HIPAA and FDA compliance for IoT medical devices?
Healthcare organizations can ensure compliance with both HIPAA and FDA regulations for IoT medical devices by focusing on cybersecurity and risk management strategies that address the unique demands of the healthcare sector. This involves conducting regular risk assessments, keeping documentation current, and ensuring that device security aligns with HIPAA's privacy and security rules alongside the FDA's safety requirements.
Tools like Censinet RiskOps™ can simplify this process by offering features such as continuous risk monitoring, vulnerability scanning, and collaborative risk management. Additionally, fostering clear communication among IT, clinical, and regulatory teams is essential. This ensures that security protocols not only meet regulatory standards but also protect patient data and maintain device performance.
How can IoT medical devices that don’t fully meet HIPAA's technical safeguards be secured?
To protect IoT medical devices that may fall short of meeting HIPAA's technical safeguards, it's essential to implement layered security measures. These can include strategies like network segmentation to isolate devices, robust access controls to limit who can interact with the system, and encryption to protect data both during transmission and while stored. Regular monitoring and vulnerability assessments are equally important to spot and address potential security gaps.
A risk management platform such as Censinet RiskOps™ can simplify this process. By offering tools for continuous risk assessments and addressing vulnerabilities, it helps safeguard patient data and Protected Health Information (PHI), even when the devices themselves have limited security features.
How can healthcare organizations address third-party and supply chain risks linked to IoT medical devices?
Healthcare organizations can address third-party and supply chain risks tied to IoT medical devices by using specialized risk management platforms tailored for the healthcare sector. These platforms provide tools for continuous monitoring, detailed risk assessments, and industry-standard benchmarking, helping to quickly identify and address potential vulnerabilities.
In addition to simplifying third-party evaluations, these solutions enhance collaboration, ensuring compliance with HIPAA regulations while protecting sensitive patient information and securing connected medical devices. Using such tools can greatly minimize risks throughout the supply chain and strengthen overall cybersecurity defenses.
Related Blog Posts
- 7 Critical Medical Device Security Risks in Healthcare
- NIST SP 800-213 for Medical Devices: What to Know
- How IoT Breaches Impact Healthcare Operations
- NIST CSF vs IoT Device Risks in Healthcare
{"@context":"https://schema.org","@type":"FAQPage","mainEntity":[{"@type":"Question","name":"What steps can healthcare organizations take to meet both HIPAA and FDA compliance for IoT medical devices?","acceptedAnswer":{"@type":"Answer","text":"<p>Healthcare organizations can ensure compliance with both HIPAA and FDA regulations for IoT medical devices by focusing on <strong>cybersecurity and risk management</strong> strategies that address the unique demands of the healthcare sector. This involves conducting regular risk assessments, keeping documentation current, and ensuring that device security aligns with HIPAA's privacy and security rules alongside the FDA's safety requirements.</p> <p>Tools like <strong>Censinet RiskOps™</strong> can simplify this process by offering features such as continuous risk monitoring, vulnerability scanning, and collaborative risk management. Additionally, fostering clear communication among IT, clinical, and regulatory teams is essential. This ensures that security protocols not only meet regulatory standards but also protect patient data and maintain device performance.</p>"}},{"@type":"Question","name":"How can IoT medical devices that don’t fully meet HIPAA's technical safeguards be secured?","acceptedAnswer":{"@type":"Answer","text":"<p>To protect IoT medical devices that may fall short of meeting HIPAA's technical safeguards, it's essential to implement <strong>layered security measures</strong>. These can include strategies like network segmentation to isolate devices, robust access controls to limit who can interact with the system, and encryption to protect data both during transmission and while stored. Regular monitoring and vulnerability assessments are equally important to spot and address potential security gaps.</p> <p>A risk management platform such as Censinet RiskOps™ can simplify this process. By offering tools for continuous risk assessments and addressing vulnerabilities, it helps safeguard patient data and Protected Health Information (PHI), even when the devices themselves have limited security features.</p>"}},{"@type":"Question","name":"How can healthcare organizations address third-party and supply chain risks linked to IoT medical devices?","acceptedAnswer":{"@type":"Answer","text":"<p>Healthcare organizations can address third-party and supply chain risks tied to IoT medical devices by using <strong>specialized risk management platforms</strong> tailored for the healthcare sector. These platforms provide tools for <strong>continuous monitoring</strong>, <strong>detailed risk assessments</strong>, and <strong>industry-standard benchmarking</strong>, helping to quickly identify and address potential vulnerabilities.</p> <p>In addition to simplifying third-party evaluations, these solutions enhance collaboration, ensuring compliance with HIPAA regulations while protecting sensitive patient information and securing connected medical devices. Using such tools can greatly minimize risks throughout the supply chain and strengthen overall cybersecurity defenses.</p>"}}]}
Key Points:
What is HIPAA compliance for IoT medical devices?
Definition: HIPAA compliance for IoT medical devices involves ensuring that connected devices handling electronic protected health information (ePHI) meet the privacy and security standards outlined in the HIPAA Privacy and Security Rules. This includes implementing safeguards to protect patient data during collection, transmission, and storage.
Why is HIPAA compliance important for IoT medical devices?
Importance:
- Protects sensitive patient data from breaches and unauthorized access.
- Ensures compliance with HIPAA regulations, avoiding penalties and reputational damage.
- Mitigates risks associated with outdated or insecure devices, such as legacy infusion pumps or monitors.
- Builds trust with patients and stakeholders by demonstrating a commitment to data security.
What are the key challenges of HIPAA compliance for IoT devices?
Challenges:
- Incomplete Device Inventories: Many healthcare organizations struggle to track all IoT devices, leaving gaps in security.
- Limited Device Capabilities: Older devices often lack encryption, robust logging, or advanced access controls.
- Third-Party Risks: Vendors and manufacturers may not fully comply with HIPAA requirements, increasing vulnerabilities.
- Distributed Devices: IoT devices scattered across networks make centralized monitoring and compliance difficult.
What are the best practices for ensuring HIPAA compliance for IoT medical devices?
Best Practices:
- Maintain Accurate Device Inventories: Use automated tools to track all connected devices and their ePHI touchpoints.
- Implement Encryption: Encrypt data in transit (TLS 1.2 or higher) and at rest (AES-256) to protect sensitive information.
- Use Compensating Controls: For legacy devices, offload security tasks like encryption and logging to secure gateways or proxies.
- Conduct Continuous Risk Assessments: Regularly evaluate devices for vulnerabilities, exposure to ePHI, and compliance gaps.
- Align HIPAA and FDA Requirements: Establish cross-functional governance teams to address overlapping regulatory standards.
How can healthcare organizations secure IoT medical devices?
Securing Devices:
- Access Controls: Enforce unique user authentication and multi-factor authentication (MFA) for device access.
- Network Segmentation: Isolate IoT devices on secure network segments to limit exposure to threats.
- Monitoring and Logging: Use centralized platforms to collect and analyze device activity logs for compliance and threat detection.
- Patch Management: Regularly update device firmware and software to address known vulnerabilities.
What role do vendors play in HIPAA compliance for IoT devices?
Vendor Responsibilities:
- Provide secure device designs with features like encryption, secure boot loaders, and firmware authenticity verification.
- Sign Business Associate Agreements (BAAs) outlining their responsibilities for HIPAA compliance.
- Offer documentation and certifications (e.g., ISO 27001) to demonstrate adherence to security standards.
- Collaborate with healthcare organizations to address vulnerabilities and ensure secure device lifecycle management.


