HIPAA vs. Massachusetts Privacy Laws
Post Summary
Healthcare providers in Massachusetts must follow both federal HIPAA regulations and stricter state privacy laws. HIPAA sets the baseline for protecting health information, focusing on healthcare-related data like medical records and billing. Massachusetts, however, expands these protections to include personal information such as Social Security numbers and financial details. State laws also require stronger security measures, faster breach notifications, and additional safeguards for mental health records.
Key Takeaways:
- HIPAA: Protects health information (PHI) nationwide, covering healthcare providers, insurers, and their vendors.
- Massachusetts Laws: Broaden protections to include personal information (PI) and enforce stricter rules like encryption, written security plans (WISP), and faster breach reporting.
- Overlap: When state laws are stricter, they take precedence over HIPAA.
Quick Comparison:
| Criteria | HIPAA | Massachusetts Laws |
|---|---|---|
| Scope | Health-related data (PHI) | Personal data (PI), including non-health info |
| Who Must Comply | Healthcare entities and business associates | Any entity handling PI of MA residents |
| Security Standards | Flexible, risk-based | Specific measures like encryption, WISP |
| Breach Notification | 60 days to notify affected individuals | Stricter timelines; notify state agencies |
To comply, providers should integrate both frameworks into a single program, prioritizing the stricter requirements.
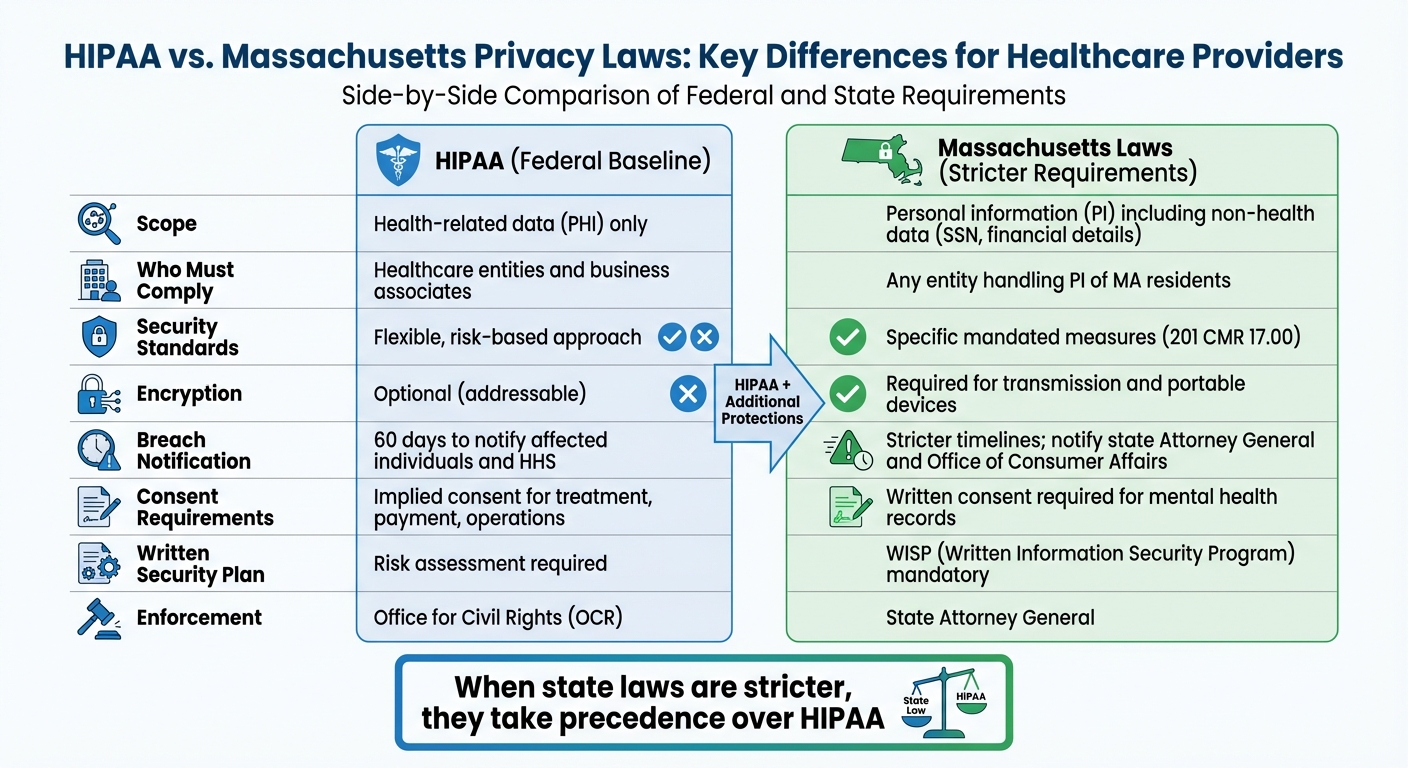
HIPAA vs Massachusetts Privacy Laws Comparison Chart for Healthcare Providers
HIPAA Requirements for Massachusetts Healthcare Providers
Main HIPAA Requirements
HIPAA establishes three core frameworks to safeguard patient information: the Privacy Rule, the Security Rule, and the Breach Notification Rule. Each plays a distinct role in protecting patient data:
- The Privacy Rule regulates how Protected Health Information (PHI) can be used and disclosed. It permits routine uses like treatment, payment, and healthcare operations without needing patient authorization. However, written consent is required for activities like marketing, research, or sharing records with non-treating third parties [8].
- The Breach Notification Rule outlines the steps to follow in case of an unauthorized disclosure of unsecured PHI. Covered entities must evaluate whether there’s a "low probability of compromise" and, if necessary, notify affected individuals, the Department of Health and Human Services (HHS), and sometimes the media, all within specific timeframes [5][8].
- The Security Rule focuses on protecting electronic PHI (ePHI) through various safeguards:
- Administrative measures: Risk analyses, management plans, workforce training, and contingency planning.
- Physical controls: Procedures for facility access and secure disposal of devices.
- Technical safeguards: Implementing unique user IDs, role-based access, encryption, and secure transmission protocols [8].
Who Must Follow HIPAA?
HIPAA applies to two main groups:
- Covered entities: This includes most licensed healthcare providers who electronically transmit health information as part of standard transactions. Examples are hospitals, community health centers, physician and dental practices, behavioral health providers, and telehealth services [8]. Health plans and healthcare clearinghouses are also classified as covered entities.
- Business associates: These are vendors or third parties that handle PHI on behalf of covered entities. Business associates must sign a Business Associate Agreement (BAA), which legally binds them to comply with HIPAA’s privacy and security requirements [8].
HIPAA as a Minimum Standard
HIPAA sets a federal baseline for protecting patient information, but Massachusetts healthcare providers often have stricter rules to follow. For instance, state laws may impose additional requirements for mental health records or data security measures [1][7][8]. When Massachusetts law offers stronger privacy protections or grants individuals greater rights, those state laws take precedence over HIPAA under its preemption rules [1][7].
For Massachusetts providers, HIPAA is not the ceiling - it’s the foundation. Compliance means adhering to HIPAA’s requirements and any additional state mandates that ensure even greater protection for patients [1][7][8].
Next, we’ll explore how Massachusetts-specific laws build on these federal requirements to enhance privacy and security measures.
Massachusetts Privacy and Data Security Laws
Main Massachusetts Laws and What They Cover
Massachusetts has taken HIPAA’s baseline safeguards a step further, adding specific requirements that healthcare providers must follow. Key regulations include 201 CMR 17.00 for data security, M.G.L. c. 93H for breach notifications, and additional protections for mental health records [3][2].
201 CMR 17.00 applies to any organization handling personal information about Massachusetts residents, including healthcare providers. It requires the implementation of a Written Information Security Program (WISP) with detailed administrative, technical, and physical safeguards [3]. This law is among the strictest in the U.S., mandating measures like encryption, access controls, firewalls, and employee training [3].
M.G.L. c. 93H addresses data breaches involving personal information. Organizations must notify affected residents, the Attorney General, and the Office of Consumer Affairs and Business Regulation when specific data elements are compromised [3][5]. In 2023, over 2,000 breach notifications were filed under this law, with healthcare ranking as one of the top industries reporting incidents.
Massachusetts also enforces stricter confidentiality protections for mental health and psychotherapy records. Written patient consent is often required for disclosure, even in situations where HIPAA would allow sharing for treatment purposes [2][4]. In legal cases like custody disputes or criminal proceedings, Massachusetts law may demand both a court order and patient consent, placing tighter restrictions than HIPAA [4].
Together, these laws establish a framework of rigorous data security and privacy standards.
What Information Is Covered
Massachusetts law focuses on "personal information" (PI), defined as a resident’s first and last name (or first initial and last name) combined with identifiers like Social Security numbers, driver’s license or state ID numbers, or financial account details with access codes [3][5]. This definition is narrower than HIPAA’s "protected health information" (PHI), which covers a broader range of health-related identifiers.
That said, there’s considerable overlap. Many HIPAA identifiers, such as Social Security numbers or billing details, also qualify as PI under Massachusetts law [6]. This overlap means healthcare providers must ensure compliance with both HIPAA and Massachusetts requirements [3][6].
The distinction lies in context: HIPAA focuses on health-related data within a healthcare setting, while Massachusetts PI laws aim to protect against identity theft and financial fraud, regardless of the sector [6]. For example, a healthcare provider managing a marketing list with names and emails (unrelated to health) wouldn’t be handling PHI, but that data could still fall under Massachusetts PI laws [6].
State Security Requirements
Massachusetts sets detailed security standards to protect personal information, going beyond HIPAA’s flexible, risk-based approach. Under 201 CMR 17.00, organizations are required to create and maintain a WISP that outlines administrative, technical, and physical safeguards tailored to their size and operations [3].
Key elements of a WISP include appointing security officers, conducting risk assessments, establishing data access policies, providing employee training, implementing physical controls, documenting incident response plans, and ensuring third-party vendors comply with security standards [3]. Healthcare providers can align HIPAA’s Security Rule with their WISP to meet both state and federal requirements.
Massachusetts also mandates encryption for personal information transmitted over public networks or stored on portable devices [3]. This is stricter than HIPAA’s optional encryption standard. Other requirements include firewall protection, up-to-date system security patches, strong access controls with unique user IDs, and continuous monitoring to ensure compliance [3].
Vendor management is another critical area. Under 201 CMR 17.00, vendors handling Massachusetts PI must maintain security measures that meet state requirements [3]. This aligns with HIPAA’s Business Associate Agreements but applies to any vendor managing Massachusetts PI, even if they’re not considered HIPAA business associates. Many healthcare organizations use tools like Censinet RiskOps™ to streamline vendor risk assessments, track compliance, and maintain WISP documentation that satisfies both state and federal standards for PHI and related systems.
How HIPAA and Massachusetts Laws Compare
This section breaks down how HIPAA and Massachusetts laws differ, helping providers navigate their overlapping responsibilities.
Coverage and Who Must Comply
HIPAA applies to covered entities like healthcare providers, insurers, and their business associates, focusing on health-related data in a healthcare context. Massachusetts law, however, casts a wider net, covering anyone handling personal information. For instance, a Massachusetts hospital must secure clinical PHI under HIPAA while also applying state rules to HR files, patient billing data, and other personal details that may not qualify as PHI. Even vendors handling a resident’s name alongside key identifiers must comply with Massachusetts regulations. Essentially, while HIPAA zeroes in on healthcare data, Massachusetts law aims to combat identity theft and financial fraud, requiring providers to adhere to the stricter standard when both sets of rules overlap [3].
Consent and Disclosure Requirements
HIPAA generally allows healthcare providers to rely on implied consent for routine activities like treatment, payment, and operations, avoiding the need for written authorization. Massachusetts law, however, is more cautious in certain areas. For example, written consent is mandatory before sharing sensitive mental health information - even between providers. Additionally, while HIPAA permits disclosures of PHI in response to subpoenas under specific conditions, Massachusetts often requires a HIPAA-compliant authorization or a formal court order before such information can be shared. This stricter approach ensures greater privacy protections in sensitive cases [2].
Security Controls and Risk Management
HIPAA’s Security Rule takes a flexible, risk-based approach, requiring safeguards that are “reasonable and appropriate” based on a thorough risk analysis. Massachusetts law, on the other hand, is more specific. Under 201 CMR 17.00, organizations must develop a Written Information Security Program (WISP) that includes detailed measures like assigning security officers, enforcing role-based access, using firewalls and malware protection, and encrypting personal information during transmission or when stored on portable devices. Providers in Massachusetts must align HIPAA’s adaptable safeguards with the state’s explicit requirements. Many organizations now use platforms like Censinet RiskOps™ to streamline risk assessments and continuously monitor compliance with both federal and state mandates [3].
Breach Notification Requirements
The two frameworks also differ in how they handle breach notifications. HIPAA requires reporting breaches of unsecured PHI when the privacy or security of the data is compromised. Notifications must go out to affected individuals and the U.S. Department of Health and Human Services within 60 days of discovering the breach. Massachusetts law, however, has stricter timelines and broader requirements. Breaches involving personal information of state residents must be reported to affected individuals, the state Attorney General, and the Office of Consumer Affairs and Business Regulation. If more than 1,000 residents are impacted, consumer reporting agencies must also be notified. Additionally, Massachusetts often requires earlier notifications and free credit monitoring when sensitive data, like Social Security numbers or financial account details, is exposed. For example, if a Massachusetts hospital experiences a ransomware attack affecting both PHI and financial data, it must fulfill the reporting obligations of both HIPAA and state law [3].
Enforcement and Penalties
HIPAA enforcement falls under the Office for Civil Rights (OCR) within the U.S. Department of Health and Human Services. Penalties include tiered fines and corrective action plans, which might involve policy updates, enhanced training, and ongoing monitoring. In Massachusetts, enforcement is handled by state authorities like the Attorney General, with penalties issued under privacy, data security, and consumer protection laws. These state penalties can stack on top of HIPAA fines. Massachusetts regulators often focus on failures to implement required measures, such as the absence of a WISP or inadequate vendor contracts. This dual enforcement highlights the importance of integrated compliance strategies, as providers must document their adherence to both sets of laws to avoid overlapping penalties [3].
sbb-itb-535baee
How to Comply with Both HIPAA and Massachusetts Laws
Balancing compliance with HIPAA and Massachusetts laws means creating a unified framework that adheres to the stricter standard. By aligning your program with both federal and state requirements, you can ensure comprehensive protection of sensitive data.
Creating a Combined Privacy and Security Program
Start by mapping where you store protected health information (PHI) and Massachusetts personal data, such as names paired with Social Security numbers, driver’s license details, or financial information. This inventory should cover everything from electronic health records and billing systems to patient portals, cloud applications, email, backup systems, and even paper records [6][10]. Once mapped, conduct a risk assessment to identify vulnerabilities and document potential threats to both PHI and Massachusetts-specific data [8][10].
Develop a written information security program (WISP) that merges HIPAA safeguards with Massachusetts requirements. This should include encryption for portable devices, role-based access controls, and vendor oversight [5]. Instead of managing separate policies for HIPAA and state law, create a policy matrix that aligns the requirements side by side. Highlight overlaps and note where Massachusetts law imposes stricter standards [5][8]. Update your HIPAA policies to explicitly reference both sets of regulations, and train your workforce on this integrated approach.
To meet both HIPAA and Massachusetts standards, implement controls like role-based access with unique user IDs, strong authentication measures, and regular access log reviews [5][10]. Additional practices might include routine software patching, endpoint protection, network segmentation for critical systems, multi-factor authentication for remote access, and well-tested disaster recovery plans [10].
Finally, ensure third-party and vendor compliance to maintain seamless data security.
Managing Third-Party and Vendor Risks
Healthcare providers in Massachusetts should maintain a centralized inventory of vendors, clearly distinguishing HIPAA business associates (those handling PHI) from other service providers who deal with Massachusetts personal data but may not qualify as business associates [6][10]. For each vendor, conduct a risk-based assessment that evaluates their security controls, incident response capabilities, and compliance with both HIPAA and Massachusetts standards [5][8].
Vendor agreements should include state-specific clauses alongside HIPAA business associate agreements. These should cover key areas such as WISP adherence, encryption, subcontractor requirements, and breach notification timelines [1][5]. Additionally, set measurable expectations for security and performance, such as audit rights, security frameworks, and regular reporting.
Tools like Censinet RiskOps™ can simplify vendor risk management by centralizing assessments and monitoring compliance. These platforms allow organizations to benchmark vendor security, prioritize remediation efforts, and track risk mitigation actions in real time. For example:
Terry Grogan, CISO at Tower Health, shared that using Censinet RiskOps™ allowed the reallocation of 3 full-time equivalents (FTEs) to other roles while increasing the volume of risk assessments with just 2 FTEs [9].
Similarly, James Case, VP & CISO at Baptist Health, noted that adopting Censinet eliminated the need for spreadsheets in risk management and fostered collaboration among hospitals, strengthening their overall security [9].
By documenting and continuously monitoring these practices, you can maintain compliance over the long term.
Documentation and Ongoing Monitoring
Maintaining a well-organized documentation system is key. This library should include your WISP, HIPAA Privacy and Security policies, sanctions policy, incident response plans, breach notification playbooks, and workforce training records [5][10]. It should also house risk assessments (both initial and periodic), vendor contracts and risk assessments, data maps, system inventories, and logs of security events. To show active compliance, keep meeting minutes from privacy and security committees, records of policy reviews, and documentation from incident response drills or tabletop exercises [10].
Set a monitoring schedule that includes an annual comprehensive risk assessment and quarterly reviews of high-risk systems and vendors [8][10]. Continuous monitoring should involve reviewing security logs, access reports for PHI and personal data, and alerts from intrusion detection systems. Establish clear thresholds for triggering incident responses. A governance body, such as a privacy and security steering committee, should regularly review regulatory updates, adapt policies as needed, and document decisions and timelines [2][8]. Before rolling out any changes to systems, vendors, or workflows, conduct a privacy and security impact review to ensure compliance.
Conclusion
Healthcare providers in Massachusetts navigate a unique dual compliance landscape: adhering to HIPAA's foundational rules while meeting the state's stricter requirements. The bottom line? HIPAA sets the minimum standard, but Massachusetts law often demands more. When state rules offer greater protections, they take precedence, requiring providers to merge both frameworks into a unified compliance program rather than juggling separate checklists [8].
Massachusetts law broadens the scope of protected personal data and enforces stricter technical measures like encryption, access controls, and thorough monitoring - areas where HIPAA is more flexible [2]. The state's 201 CMR 17.00 regulation also imposes faster breach notification timelines and mandates additional steps, such as informing the Attorney General.
By adopting the strictest standards from both HIPAA and Massachusetts law, providers not only strengthen their data protection efforts but also streamline operations. A unified program simplifies staff training, minimizes legal risks, and fosters trust with patients. This approach ensures sensitive data is safeguarded while maintaining compliance with all applicable regulations.
Ultimately, compliance goes beyond avoiding fines - it's about ensuring safe care, fostering trust, and supporting a resilient healthcare system. Prioritizing the highest level of data protection demonstrates that privacy and cybersecurity are essential components of modern healthcare [2].
FAQs
How do Massachusetts privacy laws offer additional protections compared to HIPAA?
Massachusetts privacy laws set a higher bar than HIPAA by implementing stricter rules around consent and notification, along with broader definitions of what qualifies as health information. Unlike HIPAA, which focuses specifically on protected health information (PHI), Massachusetts extends privacy protections to all health-related data.
The state also demands stronger measures to safeguard patient data and enforces tougher penalties for violations. These provisions create a heightened level of accountability and ensure sensitive health information is better protected within Massachusetts.
What are the key differences between Massachusetts breach notification rules and HIPAA requirements?
Massachusetts has breach notification laws that set a higher bar compared to HIPAA. While HIPAA allows up to 60 days to notify after a breach, as long as it’s done "without unreasonable delay", Massachusetts law is stricter. It requires notification within 60 days of discovering the breach - whether or not protected health information (PHI) was accessed or acquired.
On top of that, Massachusetts law mandates notifying not just the affected individuals but also the Massachusetts Attorney General. It also outlines specific rules about the timing and details of these notifications, which often exceed HIPAA’s federal requirements. For healthcare organizations operating in Massachusetts, staying compliant with both sets of regulations is absolutely essential.
What are the main requirements for a Written Information Security Program (WISP) under Massachusetts law?
A Written Information Security Program (WISP), mandated by Massachusetts law, is designed to protect sensitive data, such as personal and health information. It outlines specific measures organizations must take, including:
- Establishing detailed policies for data protection, access controls, and handling security incidents.
- Conducting regular risk assessments to pinpoint and address potential vulnerabilities.
- Providing employee training to promote security awareness and ensure compliance with protocols.
- Using encryption to safeguard data during transmission and storage.
- Developing incident response plans and clear breach notification procedures.
- Implementing vendor management practices to evaluate and minimize risks posed by third-party providers.
These steps not only help businesses meet legal requirements but also protect sensitive data from breaches or unauthorized access.


