Key Certifications for Healthcare Cloud Vendors in 2025
Post Summary
Healthcare organizations rely on certifications to ensure cloud vendors securely manage Protected Health Information (PHI) and comply with regulations like HIPAA and HITECH. Certifications such as HITRUST, SOC 2 Type 2, ISO 27001, FedRAMP, and CSA STAR simplify vendor evaluations, reduce compliance risks, and streamline procurement processes. While these certifications validate a vendor’s security controls, healthcare organizations must still implement their own safeguards and manage shared responsibility.
Key Takeaways:
- HITRUST i1/r2: Covers HIPAA, HITECH, and NIST requirements; supports scalable vendor assessments.
- SOC 2 Type 2: Verifies operational effectiveness of controls over time.
- ISO 27001: Establishes a security management framework; extensions like ISO 27017 and 27018 address cloud-specific needs.
- FedRAMP: Required for federal healthcare contracts; ensures compliance with NIST SP 800-53.
- CSA STAR: Focuses on cloud-specific security and maps to multiple frameworks like HIPAA and ISO.
Tools like Censinet RiskOps™ automate certification management, enabling healthcare organizations to track, verify, and integrate certifications into their workflows. However, certifications are not a guarantee of full compliance - organizations must maintain their own technical, administrative, and physical safeguards.
Regulations Driving Healthcare Cloud Certifications
Healthcare cloud providers must navigate a maze of federal regulations that define key certification requirements. At the heart of this regulatory landscape are HIPAA and HITECH, which demand strict safeguards to protect electronic protected health information (ePHI). These laws apply to any entity handling ePHI, including cloud service providers acting as business associates. While they don’t mandate specific technologies or certifications, they do require continuous risk analysis and robust administrative, physical, and technical measures to secure patient data. To meet these expectations, cloud vendors often rely on certifications like HITRUST, SOC 2, and ISO 27001, which provide a structured, auditable way to demonstrate compliance with the HIPAA Security Rule (45 C.F.R. §164.308–316). Below, we’ll explore how HIPAA, NIST, ONC, and OCR influence these certification requirements.
HIPAA and HITECH Requirements
The HIPAA Security Rule outlines essential safeguards for ePHI, including risk analysis and management, access controls, audit capabilities, data integrity protections, secure transmission, and contingency planning. HITECH builds on this by increasing penalties for non-compliance and expanding liability for business associates, which has pushed cloud vendors to adopt recognized certification frameworks. These certifications help vendors prove they’ve implemented the necessary controls to meet HIPAA’s mandates, making it easier for healthcare organizations to justify vendor selection during audits or investigations by the Office for Civil Rights (OCR).
Certifications take HIPAA’s flexible, risk-based requirements and translate them into structured frameworks with clear assessment criteria and evidence types - such as penetration testing reports, access logs, and change management documentation. This approach benefits both healthcare organizations and cloud vendors: organizations gain a verified foundation for their own risk analysis and vendor oversight, while vendors can demonstrate compliance in a standardized, repeatable way rather than relying on informal assurances.
NIST Frameworks and Healthcare Alignment
The NIST Cybersecurity Framework (CSF) and NIST SP 800-53 provide the technical backbone for many healthcare cloud certifications. NIST CSF organizes security into five core functions - Identify, Protect, Detect, Respond, and Recover - which align closely with the lifecycle of managing ePHI risks in the cloud. Meanwhile, NIST SP 800-53 offers a detailed catalog of security and privacy controls, covering areas like access management, audit logging, incident response, and system integrity, all of which are critical for cloud environments hosting PHI.
Certifications such as HITRUST and FedRAMP often reference these NIST frameworks, which are widely recognized by regulators and auditors. By using NIST as a foundation, cloud vendors can show that their controls align with established federal guidance, simplifying compliance efforts and making it easier to map controls to HIPAA requirements. For healthcare organizations, NIST-based control catalogs serve as a practical checklist when designing cloud systems for PHI, addressing key areas like identity and access management, encryption, logging, vulnerability management, and business continuity planning.
ONC and OCR Guidance
The Office of the National Coordinator for Health IT (ONC) plays a key role in setting certification criteria for health IT systems, including cloud-hosted electronic health record (EHR) modules and APIs. ONC certification focuses on interoperability, security, and privacy, assuming that the underlying cloud environments meet industry-standard security requirements. This assumption underscores the importance of certifications that verify these foundational controls.
Meanwhile, the Office for Civil Rights (OCR), which enforces HIPAA, provides guidance on risk analysis, business associate oversight, and technical safeguards for cloud services. While OCR doesn’t endorse specific certifications, its enforcement actions often highlight failures in basic controls like access management and audit logging. As a result, healthcare organizations increasingly look for vendors with robust third-party certifications to ensure these areas have been independently assessed. During OCR investigations or compliance reviews, certifications with clear control mappings and assessor attestations can help healthcare organizations demonstrate due diligence, especially in shared-responsibility cloud models. These reports clarify which controls are managed by the vendor and which require action from the healthcare organization, reducing ambiguity and saving valuable time.
Key Certifications for Healthcare Cloud Vendors in 2025
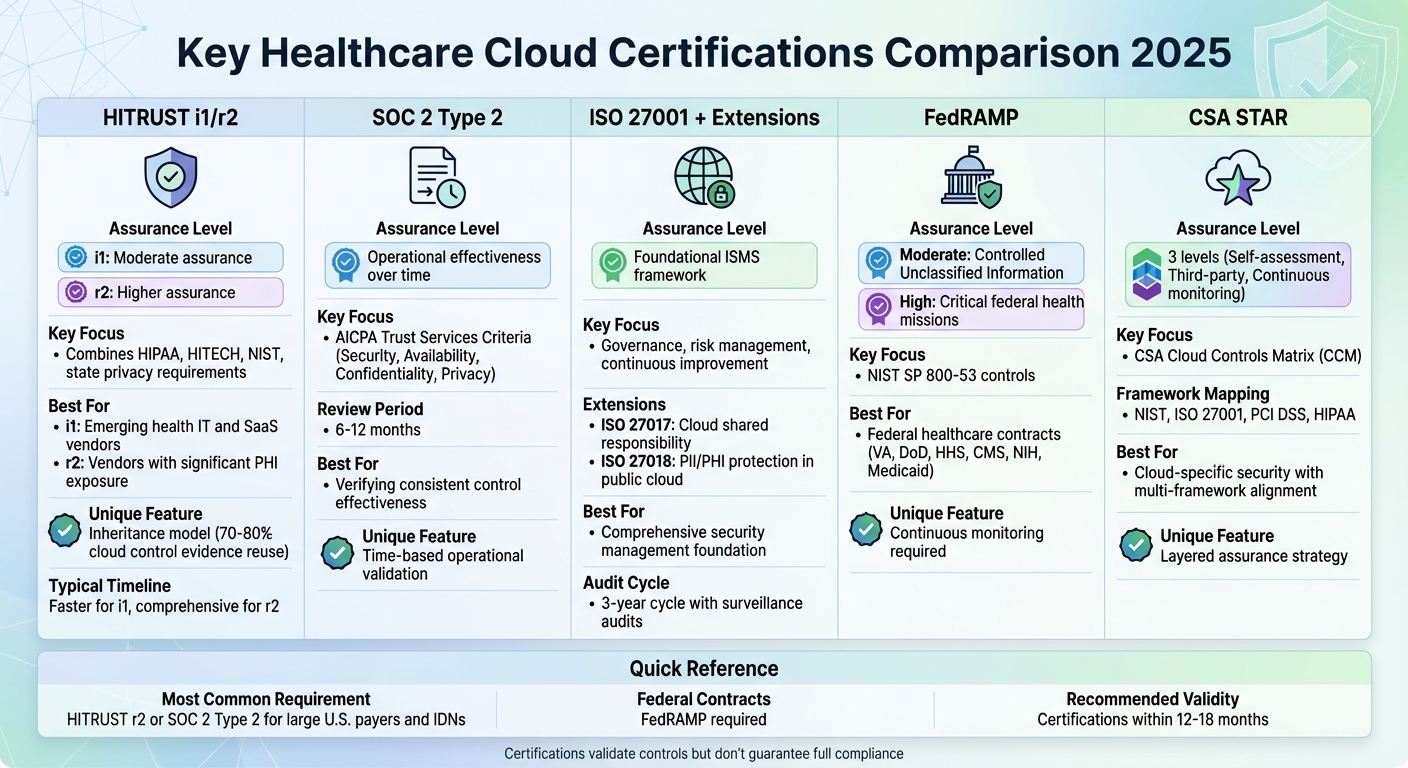
Comparison of 5 Key Healthcare Cloud Security Certifications for 2025
Certifications play a crucial role in healthcare cloud security, proving that vendors comply with standards like HIPAA, NIST, and other federal regulations. For healthcare organizations evaluating cloud vendors in 2025, these certifications are indispensable. They ensure that security measures align with regulatory expectations, simplify due diligence, and standardize the evaluation process. Many large U.S. payers and integrated delivery networks now require certifications such as HITRUST r2 or SOC 2 Type 2 when considering cloud solutions that handle Protected Health Information (PHI). Below, we break down five certifications that have become essential in this space.
HITRUST i1 and r2 Certifications

The HITRUST CSF framework combines HIPAA, HITECH, NIST, and state privacy requirements into one certifiable standard. This unified approach allows healthcare organizations to conduct a single, comprehensive assessment rather than juggling multiple audits. HITRUST certifications simplify vendor evaluations and save time during risk assessments.
HITRUST offers two main certification levels:
- HITRUST i1: A moderate assurance certification with a predefined control set, designed for faster certification timelines. It’s ideal for emerging health IT and SaaS vendors.
- HITRUST r2: A higher-assurance certification tailored to meet specific regulatory and contractual obligations, making it better suited for vendors managing significant PHI exposure or complex systems.
One of HITRUST's standout features is its inheritance model, which allows vendors to reuse up to 70–80% of cloud control evidence. This is particularly helpful for multi-tenant SaaS solutions hosted on large-scale cloud platforms. For example, startups often start with i1 certification and later upgrade to r2 as their customer base and compliance needs grow. HITRUST reports have become a key part of vendor onboarding, helping vendors respond efficiently to security questionnaires and risk reviews.
SOC 2 Type 2 Reports
A SOC 2 Type 2 report evaluates both the design and operating effectiveness of a vendor’s controls over a specific review period, usually six to twelve months. It uses the AICPA Trust Services Criteria, focusing on areas like Security, Availability, and Confidentiality - critical for protecting electronic PHI. Privacy is also a key consideration for healthcare cloud services.
Healthcare organizations often require SOC 2 Type 2 reports during vendor assessments to verify that security controls are consistently effective. To ensure the report meets their needs, buyers check its scope, look for any warnings (like qualified opinions or exceptions), and confirm the review period is up-to-date. For example, a U.S. hospital might align the report's findings with its internal security policies and incident response protocols. This process can speed up cloud adoption and reduce the need for custom security evaluations.
ISO 27001 and Related Extensions
ISO/IEC 27001 sets the standard for an Information Security Management System (ISMS), providing a strong foundation for managing security risks in healthcare cloud environments. It emphasizes governance, risk management, and continuous improvement across people, processes, and technology.
Several related extensions enhance ISO 27001 for cloud-specific needs:
- ISO 27017: Focuses on shared responsibility, tenant isolation, and virtualization controls.
- ISO 27018: Addresses the protection of personally identifiable information (PII) in public cloud environments, aligning closely with PHI requirements.
Healthcare organizations should confirm that a vendor’s ISO certifications cover the relevant legal entities, services, and data centers. Understanding how ISO controls align with HIPAA’s administrative, physical, and technical safeguards is also important. ISO certification often serves as a foundational layer, which, when paired with frameworks like HITRUST, supports a more comprehensive approach to vendor risk management.
FedRAMP Authorization

FedRAMP standardizes the security authorization process for cloud services used by U.S. federal agencies, based on NIST SP 800-53 controls.
- FedRAMP Moderate: Required for systems hosting Controlled Unclassified Information.
- FedRAMP High: Reserved for systems supporting critical federal health missions, offering the highest level of security assurance.
This certification is particularly relevant for vendors working with agencies like the VA, DoD, HHS, CMS, NIH, or state Medicaid programs. Vendors with FedRAMP Moderate or High certifications typically have rigorous documentation, robust security controls, and continuous monitoring in place. For those targeting federal healthcare contracts, designing systems to be FedRAMP-ready from the start can open doors to new opportunities.
Cloud Security Alliance (CSA) STAR

The CSA STAR program builds on ISO 27001 and uses the CSA Cloud Controls Matrix (CCM) for a detailed, multi-level assurance framework. It offers three levels:
- Level 1: Self-assessments.
- Level 2: Third-party certification or attestation.
- Level 3: Continuous monitoring.
The CCM maps to standards like NIST, ISO 27001, PCI DSS, and HIPAA, helping healthcare organizations evaluate whether a vendor’s controls meet regulatory requirements. For example, a U.S. health system might review a vendor’s CSA STAR listing and use CCM mappings to check alignment with its internal policies. Combining CSA STAR Level 2 certification with HITRUST or SOC 2 reports often creates a strong, layered assurance strategy for cloud solutions handling PHI. This approach ensures critical areas like identity and access management, data protection, and application security are properly addressed, strengthening overall vendor risk assessments.
sbb-itb-535baee
Using Certifications in Vendor Risk Assessments
Certifications play a key role in vendor risk assessments, and following best practices ensures their effective use.
Certification Verification Best Practices
When verifying certifications, focus on their authenticity, scope, recency, and the credibility of the assessor. Always obtain certificates directly from secure portals or official assessor links. Cross-check details like certificate numbers, organization names, and issuance dates against the issuing body’s official registry. Ensure the scope specifically covers the systems, cloud regions, and services relevant to processing Protected Health Information (PHI). For SOC 2 reports, review the system description to confirm which trust service categories are included. Similarly, for ISO 27001 assessments, examine the Statement of Applicability to ensure the scope aligns with your specific needs.
Establish clear guidelines for how recent certifications should be - typically within 12–18 months for reports like SOC 2 Type 2 and HITRUST - and monitor for required surveillance audits, especially for certifications like ISO 27001, which follow a three-year audit cycle. Be cautious of certifications that only address Type 1 controls, have a narrow focus excluding critical platforms, or include major unresolved exceptions. Opt for certifications issued by trusted assessors such as HITRUST-approved auditors, AICPA-licensed CPA firms (for SOC 2), ISO-accredited bodies, or recognized third-party organizations for certifications like FedRAMP. [2]
Mapping Certifications to HIPAA Safeguards
To align certifications with HIPAA Security Rule standards, use a control matrix that maps certifications like HITRUST, SOC 2, ISO 27001, and FedRAMP to HIPAA's administrative, physical, and technical safeguards for electronic protected health information (ePHI). This process allows teams to pre-credit controls during vendor assessments, focusing instead on any remaining gaps. A centralized crosswalk - such as HIPAA → NIST 800-53 → HITRUST → SOC 2 → ISO 27001 → CSA CCM - can simplify vendor questionnaires by enabling validated certifications to address or downgrade related questions to simple verification. However, unique HIPAA requirements, such as workforce training or clinical workflow controls, should still be addressed separately. This mapped approach creates a consistent framework for managing certifications across platforms. [2]
Using Censinet RiskOps™ for Certification Management

Censinet RiskOps™ streamlines vendor certification management by automating workflows to handle the collection, monitoring, and renewal of certifications. Healthcare organizations can use the platform to gather certifications - like HITRUST, SOC 2, ISO 27001, FedRAMP, and CSA STAR - directly within vendor assessments. Certifications are stored centrally, along with key details such as scope, issuance dates, and assessor information.
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required." - Terry Grogan, CISO, Tower Health [1]
The platform automates the entire process, from intake and review to approvals and periodic recertifications. It tracks certification expiration dates and sends alerts for upcoming renewals or lapses. Additionally, Censinet RiskOps™ enables benchmarking of vendors against healthcare-specific security baselines and peer performance. By moving away from manual spreadsheet tracking to automated monitoring, organizations can shift from one-time assessments to continuous evidence monitoring. Automated feeds and renewal cycles ensure certifications stay up to date.
"Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with." - James Case, VP & CISO, Baptist Health [1]
Conclusion
By 2025, certifications like HITRUST i1/r2, SOC 2 Type 2, ISO 27001, FedRAMP, and CSA STAR will remain critical for vendors handling protected health information. These certifications translate frameworks such as HIPAA/HITECH, NIST, and ONC/OCR guidelines into actionable, auditable controls.
For healthcare organizations, these certifications provide more than just regulatory compliance - they help reduce risks. Controls like multi-factor authentication, least-privilege access, encryption, and regular testing all contribute to minimizing potential breach vectors. That said, certifications are not a silver bullet. They validate specific controls within a defined scope but don’t guarantee full compliance or eliminate all risks. Healthcare delivery organizations (HDOs) still need to maintain their own technical, administrative, and physical safeguards to ensure comprehensive protection.
This has led to a growing focus on continuous compliance. Instead of viewing audits as isolated events, many HDOs now integrate certifications into their daily workflows. This includes real-time tracking of renewal dates, addressing exception findings, and monitoring remediation efforts. This proactive approach not only reduces audit fatigue but also strengthens resilience and keeps organizations aligned with evolving threats and regulatory requirements.
Platforms like Censinet RiskOps™ are helping drive this shift by simplifying certification management. These tools centralize vendor certifications, automate renewal reminders, and provide benchmarking across clinical systems, medical devices, and supply chain partners. By replacing outdated spreadsheets with automated processes, HDOs can focus on strategic risk management rather than administrative tasks. Choosing the right certifications aligned with regulatory needs can also improve market access and reduce barriers in the sales process.
As healthcare embraces cloud technologies and innovations like AI and confidential computing, certification frameworks will need to keep pace with these advancements and regulatory shifts. Organizations that combine modern certifications with specialized risk management tools will be better equipped to safeguard patient trust, foster innovation, and navigate the increasingly complex regulatory environment.
FAQs
What’s the difference between HITRUST i1 and r2 certifications?
The HITRUST i1 certification is tailored for organizations aiming for a simplified path to basic security and compliance. It emphasizes core controls that establish a solid foundation for security readiness.
On the other hand, the HITRUST r2 certification provides a broader framework for risk management. It assesses the maturity of an organization’s security practices and includes advanced measures to tackle emerging threats. This certification is well-suited for organizations needing strong, continuous risk management while aligning with top industry standards.
How do SOC 2 Type 2 and ISO 27001 certifications help healthcare organizations comply with HIPAA?
SOC 2 Type 2 and ISO 27001 certifications play a critical role in helping healthcare organizations meet HIPAA requirements. These certifications confirm that a vendor has established stringent controls to protect sensitive information, including protected health information (PHI).
Adhering to these frameworks allows healthcare organizations to strengthen their risk management strategies, improve cybersecurity defenses, and show adherence to HIPAA's privacy and security standards.
Why is continuous compliance essential for healthcare cloud vendors?
Continuous compliance plays a critical role for healthcare cloud vendors, ensuring they keep up with evolving regulations to protect patient data and protected health information (PHI). By staying ahead of risks and maintaining compliance, vendors not only safeguard sensitive information but also strengthen trust with healthcare organizations, while steering clear of hefty fines.
Beyond regulatory alignment, continuous compliance also boosts cybersecurity efforts and supports adherence to key industry standards. Tools like Censinet RiskOps™ help vendors simplify risk assessments and take a proactive stance on managing vulnerabilities, creating a secure and dependable foundation for healthcare operations.


