How Legacy IT Impacts Healthcare Cybersecurity
Post Summary
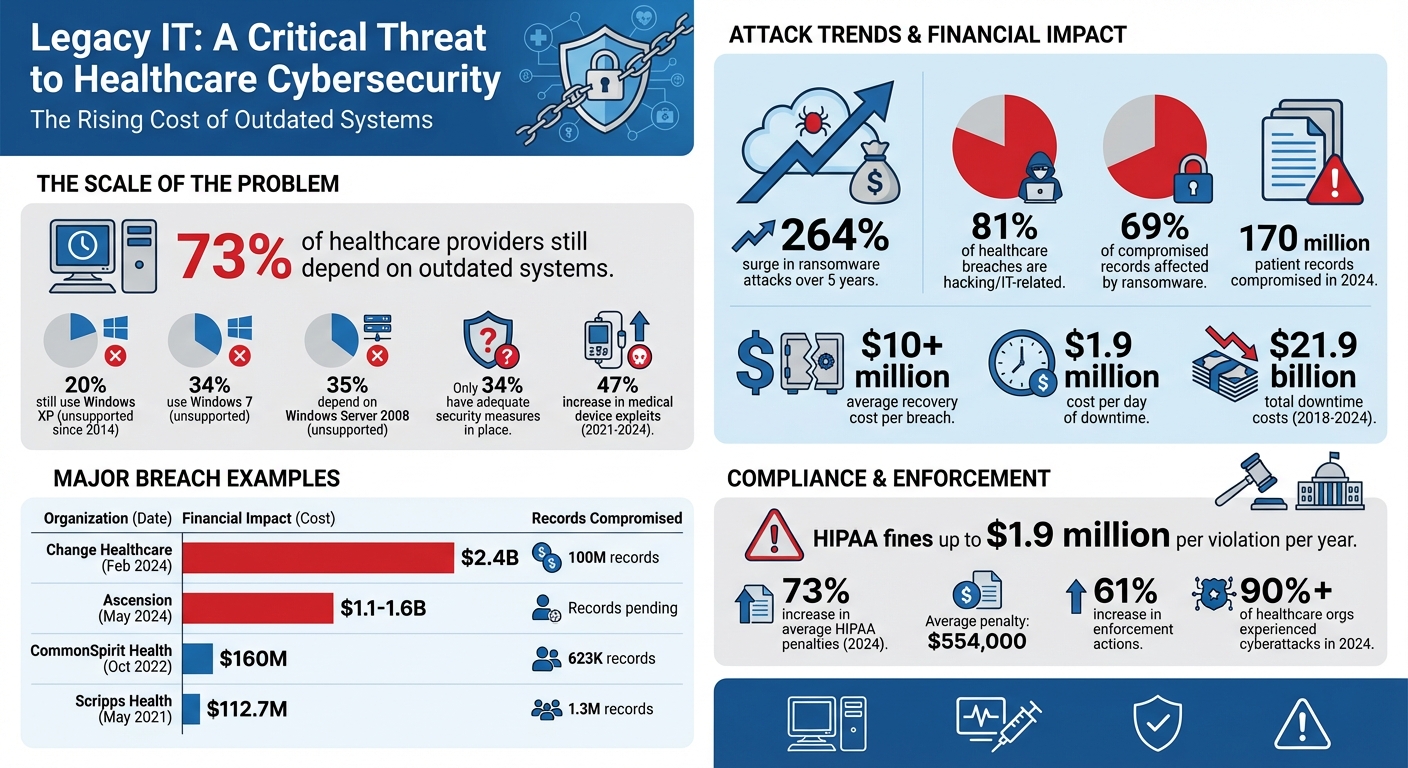
Legacy IT systems in healthcare are a major cybersecurity risk. 73% of healthcare providers still depend on outdated systems, which lack security updates and are vulnerable to attacks. This reliance exposes sensitive patient data, increases ransomware incidents, and disrupts hospital operations. For example, ransomware attacks surged by 264% in five years, with recovery costs exceeding $10 million per breach. Organizations can follow specific steps to prevent ransomware attacks to avoid these financial and operational burdens. Legacy systems also fail to meet HIPAA standards, risking fines and compliance penalties.
Key issues include:
- Outdated software: No patches or updates, leaving systems open to exploitation.
- Integration challenges: Legacy systems struggle to work with modern networks, widening attack surfaces.
- Medical device security risks: Devices like MRI machines outlive their software support, creating vulnerabilities.
- Operational disruptions: Attacks cause delays in surgeries, diagnostics, and patient care.
To reduce risks, healthcare organizations can:
- Implement network segmentation to limit attack spread.
- Use encryption and multifactor authentication for better security.
- Maintain detailed IT asset inventories to identify and manage vulnerabilities.
Addressing legacy IT risks is critical to safeguarding patient data, ensuring compliance, and maintaining trust in healthcare systems.
Legacy IT Cybersecurity Risks in Healthcare: Key Statistics and Costs
Main Cybersecurity Risks from Legacy IT Systems
Outdated Software Without Security Updates
Legacy systems often operate without critical security patches. Once software reaches its end-of-life, vendors stop issuing updates, leaving systems exposed to known vulnerabilities that attackers can exploit with ease.
The statistics paint a grim picture. About 20% of healthcare organizations still rely on Windows XP, an operating system that lost Microsoft support in 2014 [3]. Additionally, 34% use Windows 7, and another 35% depend on Windows Server 2008 - platforms that are no longer supported [7]. Alarmingly, only 34% of healthcare organizations report having current and sufficient hardware and software security measures in place [3].
"These outdated operating systems are leaving sensitive data out in the open and extremely vulnerable to attack."
– Mikko Hypponen, Chief Research Officer, F-Secure [7]
Medical devices face similar challenges. For example, while an MRI machine may remain operational for up to 30 years, its software often receives support for only 3 to 7 years [4]. This mismatch creates a dangerous gap, leaving functional hardware unprotected. Between 2021 and 2024, medical device exploits surged by 47%, with attackers targeting these unpatched systems [4].
Legacy systems also struggle with modern security protocols. Many cannot support multi-factor authentication (MFA) and rely on outdated encryption methods like SHA-1 or TLS 1.0 [5]. Some devices even come with hard-coded backdoors or default factory credentials that can't be changed, making them easy targets for brute-force attacks [4]. According to the FBI Cyber Division, these vulnerabilities provide attackers with extended windows of opportunity to exploit weaknesses [4].
Beyond software issues, integration challenges add another layer of risk.
Integration Problems and Larger Attack Surfaces
When outdated systems connect to modern networks, they create significant security gaps. Legacy platforms often weren't built to integrate with current technology, leading to vulnerabilities that can compromise patient data. Many older healthcare devices use outdated communication protocols like HL7 v2 or DICOM, which lack the security features of modern alternatives [4]. These outdated systems often serve as unmonitored entry points for attackers.
Healthcare networks are particularly complex, with nearly 1,000 unique applications spanning various legacy systems [1]. A typical health system may simultaneously maintain 30 to 40 legacy platforms [1]. Once an attacker breaches one outdated system, weak security protocols can allow them to move laterally across the network [1] [4].
A real-world example highlights this risk: the Contec CMS8000 patient monitor was found to have an embedded Network File System (NFS) backdoor that redirected patient data to unauthorized IP addresses. This vulnerability was hard-coded and couldn't be removed [4]. Moreover, legacy systems often lack detailed audit logs, leaving security teams blind to suspicious activity. They also struggle to integrate with modern security tools like Endpoint Detection and Response (EDR) or Security Information and Event Management (SIEM) systems [5]. On average, healthcare organizations have around 31,000 sensitive files accessible to most internal users, a result of legacy systems prioritizing convenience over security [1].
"Newer IT teams fear breaking undocumented legacy dependencies during migration."
– Tony Jaros, CEO, Legacy Data Access [4]
This reluctance to upgrade keeps outdated systems in place, widening the attack surface. Network servers running legacy software are a key target, accounting for more than half of all hacking-related breaches in healthcare [1].
HIPAA and Regulatory Compliance Failures
Legacy systems also present significant challenges for meeting regulatory standards. Many of these systems fail to comply with modern requirements for safeguarding patient data. For instance, the HIPAA Security Rule mandates encryption, access controls, and audit capabilities - features that are often missing or poorly implemented in legacy platforms [1] [2]. When software reaches end-of-life, its lack of updates further undermines compliance efforts.
Regulatory agencies sometimes complicate matters. For example, the FDA may approve the continued use of legacy medical devices based on hardware safety, even if the software is no longer secure [4]. This leads to situations where devices meet clinical safety standards but fall short of HIPAA requirements for data protection.
The risks are not just regulatory. Non-compliance with HIPAA can result in fines of up to $1.9 million per violation per year [5]. Beyond financial penalties, breaches of legacy systems can expose sensitive data like X-rays, MRI scans, and private doctor-patient communications, leading to identity theft, blackmail, or worse. Ransomware attacks can cripple hospital operations, forcing providers to revert to paper records - a move that increases the likelihood of medical errors and treatment delays. Such disruptions often trigger regulatory investigations, adding to the workload of already stretched compliance teams. In 2024, over 90% of healthcare organizations reported experiencing a cyberattack, with 70% noting disruptions to patient care [6].
The financial burden of maintaining legacy systems is immense. The U.S. federal healthcare system alone spends approximately $337 million annually just to keep these outdated platforms running [4]. These funds could be redirected to modernizing infrastructure and improving compliance with current security standards.
sbb-itb-535baee
Actual Consequences of Legacy IT Vulnerabilities
Data Breaches and Ransomware Incidents
The vulnerabilities in outdated IT systems have escalated into serious cyberattacks with widespread consequences, particularly in healthcare. For instance, in February 2024, Change Healthcare faced a ransomware attack that exposed the protected health information of 100 million individuals and led to a staggering $2.4 billion in response costs [9].
Similarly, in May 2024, Ascension - a network of 140 hospitals - was hit by a ransomware attack that disrupted electronic health records (EHRs), delayed lab results, and caused medication errors. The recovery costs for this incident ranged between $1.1 billion and $1.6 billion [11]. Another significant case occurred in October 2022, when CommonSpirit Health experienced a ransomware attack that forced 140 hospitals to revert to paper charting for over a month. The financial impact of this attack was estimated at $160 million [10].
These incidents are part of a growing trend. In 2024, hacking and IT-related breaches accounted for 81% of all healthcare data breaches. Ransomware alone affected 69% of the patient records compromised, totaling 170 million records that year [9].
Financial Costs and Operational Disruptions
The financial impact of these vulnerabilities goes far beyond ransom payments. A single day of downtime after a ransomware attack costs the average healthcare organization approximately $1.9 million [11]. Between 2018 and 2024, downtime due to such incidents cost the U.S. healthcare sector an estimated $21.9 billion, with the average downtime lasting over 17 days [11].
| Organization | Date of Incident | Estimated Total Cost | Records Impacted |
|---|---|---|---|
| Change Healthcare | Feb 2024 | $2.4 Billion | 100 Million |
| Ascension | May 2024 | $1.1–$1.6 Billion | Not Finalized |
| CommonSpirit Health | Oct 2022 | $160 Million | 623,774 |
| Scripps Health | May 2021 | $112.7 Million | 1.3 Million |
| Ardent Health Services | Nov 2023 | $74 Million | 23,686 |
For example, Scripps Health was targeted in May 2021, leading to a four-week EHR system outage and notifications to 1.3 million individuals. The recovery costs were $112.7 million [11]. Likewise, Ardent Health Services needed nine days to restore its electronic medical record systems after a November 2023 attack, reporting a pre-tax financial impact of $74 million [11].
The scale of these attacks is growing. In 2021, 70% of ransomware attacks impacted multiple facilities at once, and the average number of patient records exposed per attack rose to 229,000 [10].
Beyond the financial burden, these attacks disrupt hospital operations and compromise patient care.
Patient Safety and Trust Issues
When outdated systems fail, the consequences go beyond financial and operational setbacks - they directly affect patient safety and trust. For example, operational disruptions often force hospitals to implement "ambulance diversion", where emergency vehicles are redirected to other facilities. This can delay life-saving care [10].
Outdated medical devices also introduce risks. Internet of Medical Things (IoMT) devices like infusion pumps and pacemakers can be compromised, potentially altering dosages or falsifying vital signs, which poses immediate threats to patients’ lives [12]. These incidents erode trust in healthcare organizations' ability to protect sensitive health information and provide safe care.
Adding to the challenges, regulatory penalties are on the rise. In 2024, the average HIPAA enforcement penalty exceeded $554,000, marking a 73% increase from the previous year. Enforcement actions for HIPAA violations also surged by 61% compared to 2023 [8]. Alarmingly, about 20% of healthcare ransomware attacks go unreported to the Department of Health and Human Services (HHS), often because organizations assume there’s a "low probability" that data was exfiltrated - a dangerous miscalculation that leaves patients unaware of potential risks [10].
House Hearing on Cybersecurity Vulnerabilities in Legacy Medical Devices
Methods to Reduce Legacy IT Risks in Healthcare
Healthcare organizations face significant risks from outdated systems, but tackling these challenges doesn’t always mean replacing every piece of legacy equipment. Instead, they can implement targeted measures to reduce vulnerabilities and limit potential damage.
Network Segmentation and Improved Monitoring
Segmenting networks is a powerful way to limit attacker movement during a breach. For example, the Health Service Executive (HSE) of Ireland experienced a ransomware attack in 2021, exposing a critical flaw: their National Healthcare Network lacked segmentation. This allowed attackers to move freely across the network, affecting multiple systems and organizations simultaneously [13].
Virtual Local Area Networks (VLANs) are an effective solution for dividing traffic by function. Here’s how VLANs can be structured:
- A PHI/Clinical VLAN for electronic health records and medical devices handling protected health information.
- A Guest VLAN offering isolated, internet-only access for visitors.
- An IoT/Security VLAN to manage devices like security cameras and building automation systems without exposing patient data [14].
"Critical life-support systems should never be connected to the internet. There's no need to expose yourself to that risk."
For even more control, micro-segmentation can apply security policies at a granular level. This approach ensures that only authorized endpoints can access specific applications or data, which is especially useful for protecting unpatchable legacy medical devices [13]. By limiting the "blast radius" of an attack, micro-segmentation helps safeguard patient outcomes and contain malicious traffic [13].
By securing network boundaries and closely monitoring access, organizations establish a solid foundation for protecting sensitive data and user accounts.
Data Encryption and Multifactor Authentication
Beyond network controls, securing user access is key. Stolen credentials remain a common entry point for attacks on legacy systems. Implementing multifactor authentication (MFA) adds an extra layer of defense, requiring users to verify their identity through multiple methods before accessing critical systems [6].
For legacy systems that lack modern encryption capabilities, organizations should isolate these systems on local networks and avoid hosting external-facing web applications [3]. When internal resources are stretched, Managed Detection and Response (MDR) services can help monitor and respond to threats [3].
Automation also plays a crucial role in addressing vulnerabilities. Automated patching minimizes the workload on security teams, which is vital since 73% of health systems rely on medical equipment running legacy operating systems, and only 34% of healthcare organizations report having adequate hardware and software security protections [3].
Comprehensive IT Asset Inventories
You can’t secure what you don’t know exists. Maintaining a detailed inventory of IT assets is essential for identifying and managing legacy systems. This inventory should include each device’s type, model, operating system version, hostname, IP address, and physical location [13]. Such documentation helps pinpoint vulnerable systems that require immediate attention.
Asset inventories should also map communication flows. This means identifying the resources each device interacts with, the protocols used (e.g., HTTPS, TLS, or SSH), and whether the data is clinical or non-clinical [13]. Gaining this visibility is critical, especially when dealing with legacy systems that often run unsupported operating systems.
Despite these clear benefits, only 9% of healthcare organizations have made removing legacy systems a core cybersecurity priority [3]. At the very least, maintaining accurate inventories enables organizations to enforce least privilege policies, ensuring devices have only the connectivity needed to perform their functions [13].
Using Censinet RiskOps for Legacy IT Risk Management

Censinet RiskOps™ is a cloud-based solution tailored for healthcare organizations grappling with outdated systems and modern cybersecurity threats. It tackles both external risks from third-party vendors and internal weaknesses tied to legacy infrastructure that can't be easily updated [15]. The platform simplifies these challenges, enabling quicker assessments and more accurate comparisons.
Faster Risk Assessments and Benchmarking
Risk assessments traditionally take weeks - or even months - leaving systems vulnerable while evaluations drag on. Censinet RiskOps™ shortens this timeline, making it possible to quickly address both third-party and internal risks, which is especially crucial for unsupported legacy software [15][2]. The platform also organizes asset inventories to pinpoint legacy systems and electronic protected health information (ePHI) [2].
In addition to speed, the platform offers benchmarking tools through collaborations with industry leaders like KLAS. Healthcare CISOs and CIOs can measure their cybersecurity readiness against established standards such as NIST CSF 2.0, HHS HPH Cybersecurity Performance Goals, and the HICP 2023 framework [15]. These insights help organizations see how they compare to peers and focus on areas needing improvement.
AI-Powered Risk Management Tools
The Censinet AI™ tool automates key tasks like identifying, evaluating, and mitigating risks tied to legacy IT systems. It speeds up processes by completing security questionnaires, summarizing vendor documentation, and generating risk reports. While automation enhances efficiency, human oversight ensures final decisions remain in the hands of risk teams, who can customize rules and review processes.
For legacy systems that can't be retired immediately, the platform supports compensating controls such as network segregation, advanced audit logging, and restricted access [2]. Its AI-powered routing system acts like "air traffic control" for governance, directing critical findings to the right stakeholders for timely action. A real-time dashboard aggregates data, keeping teams informed and enabling proactive security measures.
Flexible Plans for Different Organization Sizes
Censinet understands that healthcare organizations face unique challenges with legacy IT, so it offers flexible service plans to meet varying needs. The Platform option is ideal for organizations with in-house teams managing risks independently. The Hybrid Mix adds extra support for those needing occasional help. For systems with limited internal resources, Managed Services provides full-service risk management, handling everything from assessments to reporting.
This adaptability ensures that both small community hospitals and large health systems can tackle legacy IT risks effectively, regardless of their resources or expertise. Using benchmarking data, organizations can also determine when maintaining outdated systems becomes more of a liability than an asset, helping them plan for eventual upgrades or replacements [2].
Conclusion
Legacy IT systems create serious risks for healthcare organizations. Despite advancements, many providers still rely on outdated platforms. Between 2021 and 2024, medical device exploits surged by 47% [4], with older systems often serving as weak points for attackers. These vulnerabilities put critical devices like pacemakers and infusion pumps at risk [4], leading to severe financial and operational challenges.
The cost of maintaining these systems is immense - U.S. federal healthcare spends hundreds of millions annually. Beyond the financial strain, data breaches and ransomware attacks can disrupt clinical operations and erode patient trust [4]. The FBI Cyber Division highlights that "medical device hardware often remains active for 10-30 years, however, underlying software life cycles are specified by the manufacturer... allowing cyber threat actors time to discover and exploit vulnerabilities" [4].
Addressing these risks requires proactive measures. Healthcare organizations must adopt strategies like network segmentation, enhanced monitoring, restricted access, and maintaining accurate asset inventories. The HIPAA Security Rule mandates thorough assessments of risks to electronic protected health information (ePHI) across all systems, including legacy infrastructure [2].
Censinet RiskOps™ provides a centralized platform to manage these challenges effectively. By streamlining risk assessments, integrating AI-powered automation with human oversight, and offering flexible service plans, the platform helps healthcare leaders reduce cybersecurity risks while ensuring operational stability. Whether through network segmentation, compensating controls, or planned modernization, tackling legacy IT vulnerabilities is essential for safeguarding patient safety and ensuring uninterrupted care delivery.
FAQs
What cybersecurity risks do outdated IT systems pose to healthcare organizations?
Outdated IT systems, often called legacy systems, bring serious cybersecurity challenges to healthcare organizations. These systems often run on unpatched software and no longer receive support, making them easy targets for cyberattacks that exploit well-known vulnerabilities. On top of that, they usually lack essential modern security measures like encryption, multi-factor authentication, and strong access controls. This creates a higher risk of data breaches and unauthorized access to sensitive patient data, including Protected Health Information (PHI).
Beyond security risks, legacy systems can cause operational headaches. They often struggle to integrate with newer technologies, creating gaps in data exchange that can serve as entry points for attackers. These weaknesses have been linked to the growing number of ransomware attacks, which can disrupt patient care, delay critical treatments, and cause financial and reputational damage. Upgrading IT infrastructure and implementing thorough risk management strategies are crucial steps for tackling these vulnerabilities head-on.
What steps can healthcare organizations take to secure outdated medical devices?
Healthcare organizations can strengthen the security of outdated medical devices by taking deliberate steps to address their vulnerabilities. The first step is to conduct a comprehensive inventory of all legacy devices. This helps identify risks and prioritize the devices that pose the highest threats to both patient safety and data security. Knowing the limitations of these older devices is key to managing risks effectively.
To reduce exposure, organizations should isolate legacy devices from the primary network, enforce robust network security measures, and monitor for any suspicious activity. For devices that cannot be updated or patched, implementing compensating controls is essential. This could include strict access controls and ongoing monitoring to detect and respond to potential issues. These measures are especially critical when manufacturer support is no longer available.
Using tools like Censinet's platform can also simplify risk assessments and bolster cybersecurity efforts. By integrating asset management, network isolation, and forward-thinking strategies, healthcare organizations can better tackle the challenges tied to legacy devices. This approach not only reduces cybersecurity risks but also safeguards patient data and essential systems.
How can healthcare organizations ensure legacy systems meet HIPAA compliance?
To bring legacy systems in line with HIPAA requirements, healthcare organizations should begin by evaluating these systems for potential vulnerabilities. Older technologies often miss out on important security updates, making them more susceptible to threats. Applying any available patches and updates regularly - even for systems no longer officially supported - can help mitigate these risks.
If replacing legacy systems isn't an immediate option, there are workarounds. Organizations can use strong encryption, multi-factor authentication, and continuous monitoring to shield electronic protected health information (ePHI). Additionally, creating a thorough risk management plan is key. This plan should include regular vulnerability assessments, clear incident response procedures, and evaluations of vendor risks. It's also essential to have Business Associate Agreements (BAAs) in place with third-party partners to ensure patient data remains secure.
Automated risk management tools can be a game-changer. They simplify compliance tasks, provide consistent oversight, and help manage the complexities of aging IT infrastructure while staying aligned with HIPAA standards.


