Medical Device Patching: Challenges and Solutions
Post Summary
Medical device patching is a critical yet complex process in healthcare. Unlike standard IT updates, patching medical devices involves balancing cybersecurity, patient safety, and clinical workflows. Delayed or inconsistent patching can lead to serious risks, from patient harm to regulatory violations. Here’s what you need to know:
-
Key Challenges:
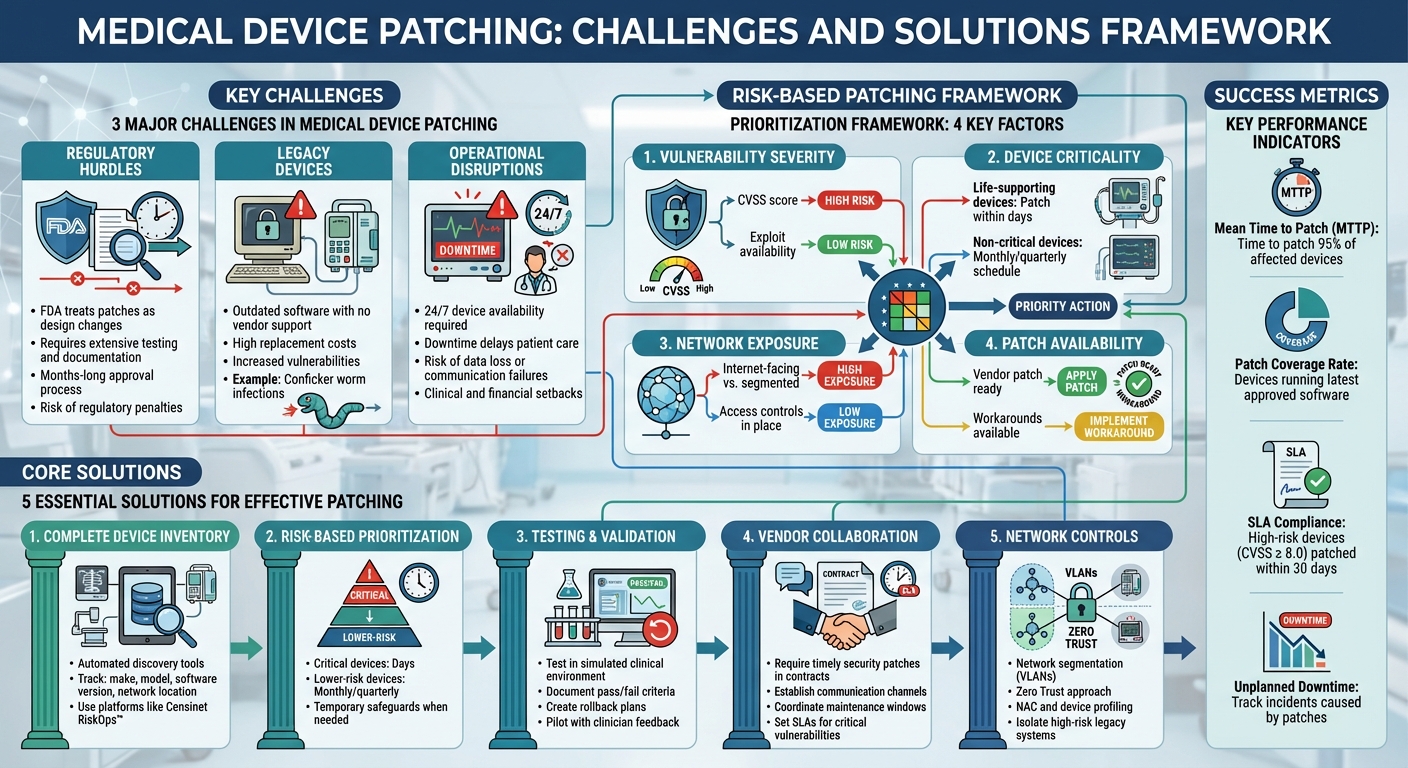
- Regulatory Hurdles: FDA treats patches as design changes, requiring extensive testing and documentation.
- Legacy Devices: Many devices run outdated software with no vendor support, increasing vulnerabilities.
- Operational Disruptions: Patching often requires downtime, which can disrupt patient care.
-
Solutions:
- Risk-Based Patching: Prioritize updates based on device criticality and vulnerability severity.
- Inventory Management: Use automated tools to maintain an accurate list of devices and their statuses.
- Vendor Collaboration: Partner with manufacturers for timely patches and clear deployment processes.
- Network Controls: Implement segmentation and access restrictions for devices that can’t be patched.
Medical Device Patching Framework: Risk-Based Approach and Best Practices
Challenges in Medical Device Patching
Healthcare organizations face tough hurdles when it comes to patching medical devices. These challenges primarily revolve around strict regulatory demands, outdated equipment that no longer gets support, and the risk of disrupting patient care. Medical devices sit at the crossroads of patient safety, regulatory compliance, and operational continuity, making patching a complex and delicate process. Let’s delve into the specifics of these issues.
Regulatory and Safety Requirements
The FDA requires manufacturers to treat patches as formal design changes, which means they must undergo the same rigorous processes as any other device modification. This includes detailed engineering analysis, verification, validation, and comprehensive documentation of every step involved in addressing vulnerabilities and deploying fixes [1][3][10]. Once manufacturers complete their part, healthcare providers must test the patches in their own environments, assess how they might impact patient safety and clinical workflows, and develop deployment and rollback plans [3].
This level of scrutiny makes the rapid patching cycles common in standard IT environments nearly impossible for medical devices. Industry experts have called the recertification process after a patch "a significant challenge", as every change must be thoroughly documented, justified, and proven safe before it can be re-released [1]. The time it takes to move from identifying a vulnerability to deploying a patch can stretch for months, given the extensive regulatory and clinical engineering resources required [3][6].
Safety and liability concerns add another layer of complexity. Both manufacturers and hospitals worry that even small software changes could unintentionally alter device behavior, degrade performance, or introduce new risks - especially for high-risk devices. If a patch is faulty or insufficiently tested, it could lead to regulatory penalties or malpractice lawsuits if patient harm occurs [1][3][10]. For clinicians and administrators, the risk of disrupting device availability often outweighs the perceived benefits of improved cybersecurity, reinforcing a "better safe than sorry" mindset [1][3].
Legacy Devices and Unsupported Software
Hospitals often rely on medical devices running outdated software or operating systems that no longer receive vendor support. These legacy devices remain in use because replacing them is expensive, and they continue to fulfill their clinical roles effectively. High replacement costs and tight budgets make it difficult to justify the significant investment needed to upgrade these systems.
However, unsupported devices create serious security vulnerabilities. Without vendor patches, healthcare organizations are left exposed to new threats. While they can implement compensating controls like network segmentation or restricted access, these measures add complexity and don't eliminate the risks entirely. A well-known example of this is the Conficker worm infection, which highlighted the dangers of delayed or missing patches [3].
Operational Disruptions
In critical care environments like emergency departments, ICUs, and operating rooms, medical devices must be available around the clock. Downtime - whether planned or unplanned - can lead to delayed care, manual workarounds, or even increased clinical errors [3][6]. Patching often involves taking devices offline, rebooting systems, or running post-update checks, all of which can disrupt workflows. This can reduce room throughput, extend procedure times, or require patient rescheduling, resulting in both clinical and financial setbacks [1][3].
For devices used in high-acuity settings, patching can also lead to issues like data loss or communication failures [6]. To minimize disruptions, clinical leaders and biomedical engineers often delay patches, scheduling them during maintenance windows, off-hours, or periods of low patient volume. This practice, however, extends the time between identifying a vulnerability and addressing it, leaving devices exposed for longer periods [3][6]. When there’s no immediate evidence of active exploitation, organizations sometimes prioritize operational stability over cybersecurity, opting to delay patches [3][5]. Past experiences with patches causing malfunctions or workflow changes have further cemented a "don’t fix what isn’t broken" attitude among clinicians [1].
Core Principles for Effective Medical Device Patching
Healthcare organizations must adopt a structured approach to patching medical devices - one that carefully balances patient safety, regulatory requirements, and cybersecurity concerns. Below are key principles to guide patching programs in clinical environments.
Prioritizing Patient Safety and Risk Management
When it comes to patching medical devices, patient safety is the top priority. Unlike typical IT systems, these devices have a direct impact on patient care, making it critical to assess the risks of applying or delaying a patch. A risk-based decision-making process should consider three main factors:
- Potential patient harm: What could happen if a vulnerability is exploited? For example, could it lead to incorrect dosages, delayed diagnoses, or loss of critical therapy?
- Impact of downtime or malfunction: Can the device be safely taken offline for patching? Is backup equipment available to maintain care during this time?
- Likelihood of cyber exploitation: What does current threat intelligence suggest about the risk of this vulnerability being exploited, especially given the device's network exposure?
For high-severity vulnerabilities on life-critical devices, organizations may need to schedule off-hours patching with close clinical oversight. Lower-risk vulnerabilities on non-critical equipment might be better managed through network controls until a scheduled maintenance window. Documenting these decisions - and gaining approval from a multidisciplinary team that includes clinical engineering, biomedical staff, IT security, and clinical leadership - is essential. This ensures that patching strategies balance cybersecurity needs with the realities of patient care.
Lifecycle and Security-by-Design Approaches
Building security into medical devices from the outset is far more effective than trying to address it later. The FDA’s cybersecurity guidance emphasizes that devices should be designed to support secure and efficient patching, including features like cryptographic signing of updates, rollback capabilities, and secure remote update mechanisms [1] [3] [10].
Healthcare organizations can reinforce this during procurement by requiring vendors to meet specific security standards, such as providing documented patch service agreements and ensuring devices are built for easy vulnerability management.
Adopting a lifecycle approach further strengthens security. This begins with vendor cybersecurity assessments, moves through centralized onboarding and continuous vulnerability monitoring, and ends with validated patch testing and secure device retirement. Manufacturers that implement modular designs, automated testing, and streamlined update mechanisms help reduce regulatory hurdles and speed up patch deployment [1] [3]. By embedding security throughout a device’s operational life, organizations can address challenges posed by regulatory requirements and legacy systems more effectively.
Collaborative Governance and Shared Responsibility
Effective patching isn’t just about technology - it’s about collaboration. Manufacturers, IT teams, clinical engineers, and biomedical staff must work together under clear governance structures where everyone understands their role.
Manufacturers should engage with clinical and IT teams early in the process to align device design with real-world deployment needs. Features like modular software for partial updates, automated testing, secure remote update capabilities, and rollback options are critical for smooth operations.
Standardized change management practices are also key. These should include clinical sign-offs for patches affecting patient care, maintenance schedules aligned with periods of low device usage, and clear communication templates for clinical staff. These templates should outline expected downtime, affected devices, backup procedures, and escalation paths.
Regular tabletop exercises and post-incident reviews can help healthcare organizations prepare for zero-day vulnerabilities and emergency patches. This ensures fast responses without compromising patient safety or compliance [1] [3].
Shared responsibility extends beyond individual organizations. Collaborative risk networks, like those supported by platforms such as Censinet RiskOps™, allow hospitals and vendors to share cybersecurity data and best practices. This collective effort strengthens patching practices across the healthcare ecosystem, helping to mitigate disruptions while maintaining security and compliance.
Practical Solutions to Medical Device Patching Challenges
Building a Complete Medical Device Inventory
To patch vulnerabilities effectively, healthcare organizations need an accurate and up-to-date inventory of their connected medical devices. Yet, many still struggle with incomplete records, which makes it nearly impossible to identify affected devices when a security issue arises [3][9]. Large hospitals can have tens of thousands of devices from hundreds of vendors, and without centralized tracking, many vulnerable devices go unnoticed or remain misconfigured [3][9].
The solution? Start with automated discovery tools like network scanning, passive monitoring, and Network Access Control (NAC) systems. These tools help uncover unmanaged or "shadow" devices and reconcile them with existing records [9]. A robust inventory should include details like the device's make, model, software version, network location, clinical function, assigned owner, and vendor support status. Platforms such as Censinet RiskOps™ offer cloud-based solutions to centralize this data, making it easier to manage risk across devices and vendors. Experts agree that specialized tools are critical to navigating the complexity of healthcare's device ecosystem.
Once you’ve built an accurate inventory, you can focus on prioritizing and addressing vulnerabilities.
Implementing Risk-Based Patching Frameworks
Not every patch demands the same urgency. Prioritize based on factors like the vulnerability's severity (CVSS score, exploit availability), the device's role in patient care (life-supporting vs. non-critical), network exposure (internet-facing or segmented), and the availability of vendor patches or workarounds [6][8][9]. Critical vulnerabilities on life-support devices should be addressed within days, while lower-risk devices can follow monthly or quarterly schedules [8][9].
When immediate patching isn’t an option, temporary safeguards like network segmentation, strict authentication, and enhanced logging can help reduce risk [7][4][8][9]. For legacy devices or those under strict FDA approvals, these network-based defenses might be your primary line of protection until patches become available.
After prioritizing vulnerabilities, thorough testing ensures patches improve security without disrupting clinical operations.
Improving Testing, Validation, and Change Management
Before deploying patches, test them in a simulated clinical environment [1][3][5]. This step is crucial to confirm that clinical functions remain intact, vulnerabilities are mitigated, and no new issues - like latency or instability under typical loads - are introduced [10][3].
Document test results with clear pass/fail criteria, create rollback plans, and pilot patches with clinician feedback before rolling them out widely - especially for high-risk or life-support devices [3][6]. A structured change management process ensures smoother implementation. This includes documenting risk assessments, scheduling patches during maintenance windows (like nights or weekends), informing clinicians about potential downtime, and monitoring devices after deployment [3][5][9].
Strengthening Vendor Collaboration
Vendors play a key role in patching efforts. Think of them as partners, not obstacles. Contracts and Business Associate Agreements (BAAs) should require vendors to provide timely security patches, a Software Bill of Materials (SBOM), MDS2 cybersecurity documentation, and clear deployment instructions [3][6][5][8]. Set up communication channels like advisories, portals, or mailing lists to stay updated on new vulnerabilities and patches [6][8].
Coordinate patching schedules with vendors and clinical teams. For example, schedule maintenance windows during low-traffic periods (like overnight or weekends in ICUs) and segment device fleets to avoid complete downtime - patching half the devices at a time ensures continued capacity [1][3]. Bundling multiple vendor updates into the same maintenance window can also save time. For high-risk devices, involve vendors in joint testing, and establish service-level agreements (SLAs) for responding to critical vulnerabilities [1][6][5].
Using Network Controls for Additional Security
For devices that can’t be patched, layered network defenses provide critical protection. Network segmentation separates medical devices from general IT systems and the internet, using VLANs and internal firewalls to limit lateral movement of threats [7][4][8][9]. Adopting a Zero Trust approach with strong authentication and least-privilege access further enhances security [8][9].
Network Access Control (NAC) and device profiling tools can help identify and classify medical devices, enforce appropriate policies, and quarantine non-compliant or compromised devices [9]. For high-risk legacy systems, isolate them behind application gateways or jump hosts, disable unnecessary services, and tightly control remote access [7][4][8][9]. These measures not only protect the devices themselves but also prevent them from being exploited as entry points to attack other parts of the hospital network [3][9].
sbb-itb-535baee
Measuring Success and Continuous Improvement
Defining Metrics and Key Performance Indicators (KPIs)
Tracking performance is crucial for healthcare organizations to ensure effective patch management. One key metric is Mean Time to Patch (MTTP) for critical vulnerabilities. This measures the time from when a vulnerability is disclosed - whether through ICS-CERT, an FDA alert, or a vendor bulletin - to when 95% of affected devices are patched [2][3]. Breaking this data down by severity level and device category can help pinpoint bottlenecks.
Other essential metrics include the percentage of high-risk devices patched within policy-defined Service Level Agreements (SLAs). For example, devices with vulnerabilities rated CVSS ≥ 8.0 should ideally be patched within 30 days [2][3]. Additionally, monitor your patch coverage rate, which reflects the proportion of medical devices running the latest vendor-approved software or firmware. Keep an eye on exception rates for devices operating under accepted risks or compensating controls [2].
It’s equally important to track unplanned downtime caused by patches and security incidents involving medical devices - especially those tied to delayed patches [2][3]. These metrics collectively help balance cybersecurity goals with the needs of clinical operations and patient safety.
Benchmarking and Risk Analytics
Once you’ve established your KPIs, comparing your performance to industry peers can highlight gaps and guide investments. This is where benchmarking comes into play. Tools like Censinet RiskOps™ allow healthcare organizations to measure their cybersecurity posture, including medical device risks, against industry standards and similar institutions. As Brian Sterud, CIO of Faith Regional Health, explains:
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters."
Benchmarking can answer key questions: How does your MTTP for critical vulnerabilities on devices like infusion pumps compare to peer hospitals? What percentage of your devices still rely on outdated operating systems like Windows 7, and how does that stack up against the industry average [2][3]? Are you relying more heavily on risk acceptances and compensating controls than your peers [2]? Platforms like Censinet RiskOps™ aggregate data from a network of healthcare organizations and over 50,000 vendors, providing insights that help determine whether your patching strategy is keeping pace or falling behind. This data-driven approach supports smarter resource allocation and helps make the case for additional investments when needed.
Adapting to Emerging Trends and Regulations
The cybersecurity landscape - and the regulations shaping it - are constantly shifting. To stay ahead, healthcare organizations need adaptable governance structures. Establish a cross-functional medical device cybersecurity committee that includes members from clinical engineering, IT security, compliance, and clinical leadership. This group should meet regularly - monthly or quarterly - to review patching dashboards, investigate missed SLAs, and update policies based on findings [2][3]. The committee should also have clear protocols for risk acceptance, emergency patching for zero-day vulnerabilities, and criteria for taking devices offline when risks become unacceptable [3][10].
Keep up with evolving guidelines like the FDA’s premarket and postmarket cybersecurity recommendations, HIPAA Security Rule requirements, and new state or federal mandates [3][6]. When new threats like ransomware or zero-day vulnerabilities arise, add specific response metrics - such as the time from alert to mitigation - and incorporate threat intelligence into your patch prioritization [8][10].
Regularly update playbooks to account for new technologies, including cloud-connected or AI-enabled devices, without overhauling governance structures each time. Use lessons from past incidents, near-misses, or delayed patches to refine testing processes, change management, and vendor contracts [3][5]. These ongoing refinements are key to building a proactive patching strategy that safeguards patient safety and ensures operational resilience.
Conclusion
Addressing medical device patching is one of the toughest challenges in healthcare cybersecurity. The stakes are high - patient safety, device functionality, and regulatory compliance all hang in the balance. Each patching decision is a delicate balancing act, requiring careful consideration of both technical and clinical impacts, as even small changes can affect device performance or patient outcomes.
To tackle these obstacles, healthcare organizations need to adopt practical, risk-focused strategies. A well-structured, risk-based approach ensures cybersecurity efforts align with patient safety while enabling timely fixes without disrupting care. The starting point? A complete and accurate inventory of medical devices. This inventory helps identify which devices are vulnerable to emerging threats. From there, a risk-based framework allows organizations to prioritize patching efforts based on the clinical importance of each device and its exposure to risk. Rigorous testing, validation, and change management processes are essential to ensure patches don’t interfere with device functionality or disrupt clinical workflows. When immediate patching isn’t possible, measures like network segmentation, access controls, and close collaboration with vendors can provide additional layers of protection.
As threats continue to evolve, healthcare organizations must also focus on improving governance, processes, and technology. Independent safety organizations now rank cybersecurity threats and vulnerable technology as major risks to health technology, highlighting the critical importance of addressing unpatched devices to protect patient safety [11]. Tracking performance through key metrics, benchmarking progress, and updating policies in line with FDA guidance and industry standards are essential steps for staying ahead of emerging threats.
The key to success lies in clear governance and effective collaboration across teams. Cross-functional governance ensures timely and informed patching decisions, while healthcare-specific platforms like Censinet RiskOps™ can streamline efforts by centralizing risk assessments, benchmarking cybersecurity performance, and coordinating remediation across medical devices, clinical systems, and supply chains.
FAQs
What are the biggest challenges in updating legacy medical devices?
Updating older medical devices presents a tough set of challenges. Many of these devices rely on outdated firmware that no longer gets security updates, making them easy targets for cyberattacks. On top of that, they often struggle to work with modern systems, which can make upgrading them a risky move that might disrupt their functionality. To make matters worse, manufacturers may no longer offer support for these devices, leaving healthcare providers without the tools or expertise needed to address these problems.
These obstacles underline the need for strong cybersecurity practices and careful risk management to safeguard patient data and maintain the reliability of healthcare systems.
What’s the best way for healthcare organizations to prioritize medical device patching?
Healthcare organizations can tackle medical device patching more effectively by using a risk-based approach. This means focusing first on devices with vulnerabilities that could significantly impact patient safety or disrupt critical operations.
To stay ahead of potential threats, tools like continuous monitoring systems can be invaluable. These systems help track emerging risks in real time. Pairing this with a risk management platform simplifies the process, ensuring resources are directed where they’re needed most while keeping up with industry regulations. By addressing the most critical devices first, organizations can take a proactive stance on both cybersecurity and patient safety.
What is the vendor's responsibility in ensuring medical devices are securely patched?
Vendors play a crucial role in safeguarding medical devices by delivering firmware updates and security patches that address vulnerabilities. These updates are essential for reducing risks to both patient safety and data privacy. By working hand-in-hand with healthcare organizations, vendors ensure these patches are applied promptly and effectively.
Beyond just providing updates, vendors often extend technical support and offer guidance to help healthcare teams manage the patching process. This partnership is key to maintaining compliance with security standards and defending against ever-changing cyber threats.


