Regulatory Updates 2025: Vendor Adaptation Tips
Post Summary
Big changes are here for healthcare cybersecurity. The 2025 updates to HIPAA's Security Rule introduce stricter requirements to combat rising cyber threats. Here's what you need to know:
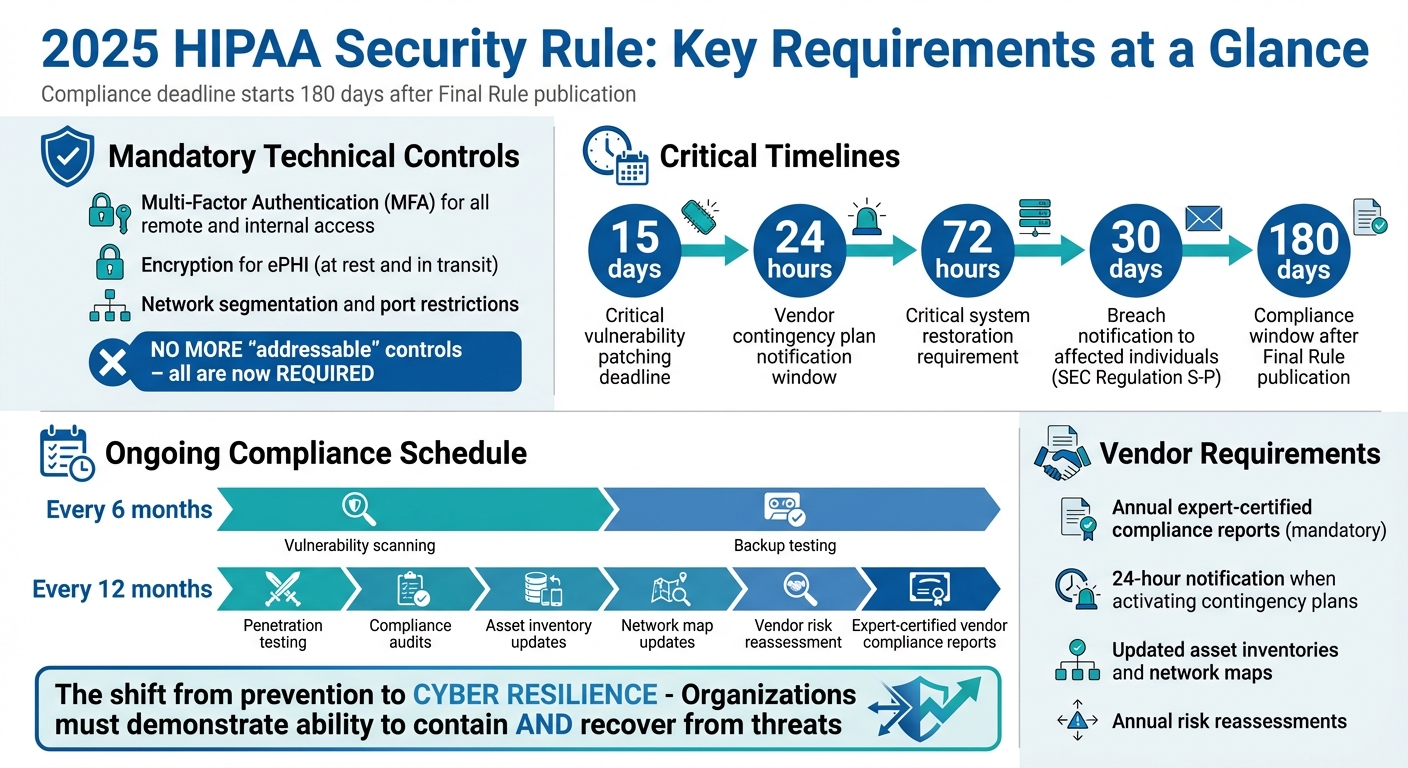
- Mandatory Controls: No more "optional" safeguards - multi-factor authentication (MFA), encryption for ePHI, and network segmentation are now required.
- Tight Deadlines: Critical vulnerabilities must be patched within 15 days, and critical systems restored within 72 hours of an outage.
- Vendor Requirements: Annual expert-certified compliance reports are mandatory, and vendors must notify covered entities within 24 hours of activating contingency plans.
- Risk Management: Organizations must maintain updated asset inventories and network maps, reassess vendor risks annually, and conduct regular audits.
These changes aim to improve resilience against cyberattacks and ensure faster recovery when incidents occur. Adopting tools like Censinet RiskOps™ can simplify compliance and vendor oversight, helping healthcare organizations stay ahead of these requirements.
Act now. The 180-day compliance window starts soon after the Final Rule's publication, and delays could lead to major risks and costs.
2025 HIPAA Security Rule Compliance Requirements and Timelines
Vendor Risk Management: 2025 Requirements
Updating Vendor Risk Management Policies
By 2025, healthcare organizations will need to meet stricter standards for vendor risk management. One key requirement is obtaining annual, expert-certified written confirmation from each vendor, as outlined by the Office for Civil Rights (OCR) at HHS:
"Require that business associates verify at least once every 12 months for covered entities... that they have deployed technical safeguards required by the Security Rule to protect ePHI through a written analysis... and a written certification" [3].
This means vendors must provide a written analysis, certified by a subject matter expert, confirming their compliance with technical safeguards for protecting electronic Protected Health Information (ePHI).
Another major update involves a 24-hour contingency notification rule. Vendors are now required to notify healthcare organizations within 24 hours of activating contingency plans. This could include scenarios like system failures or security incidents that trigger backup procedures [3][6].
Healthcare organizations must also expand their risk assessments to include both current and potential business associates. Additionally, maintaining a technology asset inventory and network map - updated at least every 12 months - is now mandatory. These documents must outline all processes involving ePHI transfers, with formal tracking, documentation, and regular verification required [3][1].
Given the increasing complexity of these compliance requirements, healthcare organizations may benefit from using specialized tools to streamline and manage these processes effectively.
Using Censinet RiskOps™ for Compliance
Censinet RiskOps™ offers a comprehensive solution to help healthcare organizations meet these new standards. Acting as a central hub, the platform simplifies third-party risk assessments, compliance tracking, and ongoing oversight.
One standout feature is its ability to automate the collection of annual certifications, eliminating the need for manual follow-ups. With Censinet RiskOps™, you can easily track which vendors have submitted their expert-certified analyses and identify those that still need to comply.
The platform also leverages AI-driven tools to speed up vendor assessments. It automatically generates summaries of security questionnaires and documentation, highlighting critical integration details and potential risks. This allows your team to handle a higher volume of assessments without losing control, thanks to configurable rules and review processes.
Censinet RiskOps™ goes further by enabling cybersecurity benchmarking and promoting collaborative risk management across healthcare networks. Its command center provides real-time insights into your vendor ecosystem, helping you identify high-risk business associates and prioritize remediation efforts in line with the new regulations. This level of visibility and control is essential for staying compliant in a rapidly evolving regulatory landscape.
sbb-itb-535baee
How to Adapt to 2025 Regulatory Requirements
Running Gap Analyses
To align with the 2025 regulatory updates, start by comparing your current security practices to the new standards. A key change is the elimination of the distinction between "required" and "addressable" controls - going forward, all controls are mandatory unless specific exceptions apply [6]. This shift means you'll need to reassess every control previously deemed "addressable."
Conduct a thorough gap analysis, including an updated asset inventory and a network map that outlines the flow of electronic Protected Health Information (ePHI). These documents should be refreshed at least once a year [3]. Evaluate risks associated with both current and potential associates, and establish an annual written verification process to ensure compliance [6].
Annual compliance audits are essential under the new guidelines. These audits should confirm that all safeguards meet the 2025 requirements. Be meticulous about documentation - auditors will expect proof that you've identified and assessed all reasonably anticipated threats, considering the likelihood of their exploitation.
Tools like Censinet RiskOps™ can simplify this process by offering benchmarking capabilities to measure your compliance against the new standards. Its command center provides real-time insights into gaps across your vendor network, helping you prioritize remediation efforts effectively.
Once you've identified gaps, focus on implementing the required technical safeguards.
Setting Up Technical Safeguards
The 2025 updates mandate several technical controls, so it's time to strengthen your systems. Multi-factor authentication (MFA) is now required for all remote access and internal systems, with very few exceptions [7]. MFA must include at least two factors: something you know (like a password), something you have (such as a token), or something you are (biometric verification) [2].
Encryption is another non-negotiable. All ePHI must be encrypted both at rest and during transmission [3]. To further protect your network, implement segmentation and limit unnecessary ports based on your risk analysis [3]. If you're a medical device vendor, adopting a Secure Product Development Framework (SPDF) is critical to minimizing vulnerabilities throughout the device lifecycle [8].
Patch management is now under stricter timelines. Critical vulnerabilities must be patched within 15 calendar days of identification [6]. Here's a quick breakdown of key requirements and their timelines:
| Requirement | Frequency/Timeline |
|---|---|
| Critical Vulnerability Patching | Within 15 calendar days |
| Vulnerability Scanning | Every 6 months |
| Penetration Testing | Every 12 months |
| Backup Testing | Every 6 months |
| Compliance Audits | Every 12 months |
Censinet AI™ can help streamline vendor risk assessments by summarizing security questionnaires and documentation, pinpointing critical integration details and potential risks.
With technical safeguards in place, the next step is preparing your organization for incident response.
Creating Incident Response Plans
Having a well-documented incident response plan is essential to meet the 2025 requirements. Your plan should include restoration procedures to ensure critical systems are back online within 72 hours of an outage [6]. Test and update this plan annually.
Revise Business Associate Agreements (BAAs) to require subcontractors to notify you within 24 hours of activating contingency plans [6]. This shorter reporting window will demand clear communication channels and streamlined escalation processes.
Regular testing of your incident response plan is crucial. Annual tabletop exercises can help validate your plan by simulating scenarios like ransomware attacks or system outages. Document all findings and corrective actions, as regulators will expect evidence that you're continually improving your response capabilities.
If you fall under SEC Regulation S-P, there's an additional requirement: you must notify affected individuals within 30 days of discovering a breach [7]. Make sure this 30-day notification rule is integrated into your response workflows to avoid compliance issues.
Working Together for Cybersecurity Compliance
Why Collaborative Risk Management Works
The 2025 updates to the HIPAA Security Rule emphasize that cybersecurity is no longer just an internal concern for healthcare organizations - it’s a shared responsibility that extends to their entire vendor network. Published on January 6, 2025, these updates remove the distinction between "required" and "addressable" controls, creating a stricter framework that demands better coordination across the supply chain [12][5].
Collaborative platforms play a crucial role by offering real-time insights into third-party risks, which is especially important when managing security threats in vendor relationships. For instance, Censinet RiskOps™ provides dashboards that help healthcare organizations and their vendors quickly identify vulnerabilities across complex, multi-tier networks. This shared visibility ensures both parties can align on priorities, including the technical controls necessary to meet the new regulations [9][10].
Joint risk assessments add another layer of efficiency by eliminating repetitive questionnaires and standardizing documentation to meet auditor requirements. By using a unified platform, healthcare organizations and vendors can address potential issues proactively - critical under the new 30-day breach notification rule [9]. Although the Office for Civil Rights (OCR) hasn’t conducted HIPAA audits since 2017, that’s expected to change in 2025 [12]. Collaborative platforms make it easier to maintain continuous risk analysis and remediation, helping organizations stay ahead of regulatory scrutiny.
To build on these benefits, incorporating AI tools can help scale and enhance risk management processes even further.
Using AI to Scale Cyber Risk Management
AI-powered tools, like Censinet AI™, simplify the increasingly complex requirements of vendor risk management under the new continuous risk analysis guidelines [13][11]. These tools automate tasks such as summarizing vendor security questionnaires, identifying fourth-party risks, and producing standardized reports based on assessment data.
While AI excels at flagging vulnerabilities and prioritizing threats, human oversight remains indispensable. Risk teams need to interpret nuanced scenarios, like upgrading legacy systems or addressing specific business associate agreements (BAAs), to make informed decisions [9][10]. Platforms like Censinet AI support this balance by offering configurable rules and review processes, ensuring automation complements rather than replaces expert judgment.
AI also acts as a central coordinator for managing critical risk tasks. For example, Censinet RiskOps™ directs key findings and responsibilities to the appropriate teams - whether it’s IT security, compliance officers, or an AI governance committee - ensuring accountability across the organization. With a centralized AI dashboard that aggregates real-time data, organizations can track remediation efforts more effectively and demonstrate compliance during audits.
This "human-in-the-loop" approach allows organizations to scale their operations without sacrificing precision. By processing more vendor assessments, responding rapidly to emerging threats, and maintaining thorough documentation for regulators, organizations can expand their risk management capabilities while keeping experienced professionals at the helm of critical decisions.
HIPAA Security 2025: Turning Proposed Changes into a Practical Action Plan
Conclusion: Getting Ready for 2025 and Beyond
The regulatory updates slated for 2025 mark a shift in focus - from simply preventing cyberattacks to building cyber resilience. Healthcare organizations are now expected to not only block threats but also contain and recover from them quickly. As the Office for Civil Rights (OCR) puts it, "Regulated entities must consider how their security measures support resilience in the face of an adverse event" [4]. In other words, prevention alone isn’t enough anymore; it’s about creating a framework that ensures recovery and continuity. This change pushes organizations to act now, avoiding the far greater costs of unpreparedness.
The financial stakes are high. Waiting to adapt to these changes can lead to expenses far exceeding the upfront investment in compliance. While upgrading technical controls requires time and resources, the alternative - crippling cyberattacks - can shut down hospital networks, disrupt patient care, and create massive recovery costs [8]. Proactively investing in compliance not only minimizes these risks but also strengthens trust with patients and partners, while preparing organizations to face emerging threats [4].
Tools like Censinet RiskOps™ are designed to help healthcare organizations navigate these challenges. This platform centralizes efforts such as gap analyses, vendor assessments, and risk management, with the added scalability of Censinet AI™. By streamlining compliance processes while maintaining critical human oversight, solutions like this enhance an organization’s ability to stay resilient in a rapidly evolving regulatory environment.
The urgency to act is underscored by recent updates, including FDA guidance released on February 3, 2026 [8]. With regulatory scrutiny expected to increase, early adoption of strong security frameworks will separate prepared organizations from those left scrambling [4][8]. The pace of change isn’t slowing, and neither should your efforts to prepare.
FAQs
What should we do first in the 180-day window?
To get started, perform a detailed vendor risk assessment. Look closely at their security measures, compliance records, and incident response strategies to ensure they meet the 2025 regulations, such as HIPAA and FDA cybersecurity standards.
Taking this step early allows you to spot weaknesses and address them before they become bigger issues. Tools like Censinet RiskOps™ can make the process easier by simplifying assessments, organizing data in one place, and offering ongoing monitoring. This approach not only boosts your readiness for tighter compliance rules but also helps tackle emerging cybersecurity challenges.
How do we verify vendors meet the annual expert-certified requirement?
Healthcare organizations can simplify the process of ensuring vendors meet the yearly expert-certified requirements by leveraging reliable platforms like Censinet RiskOps™. These tools take the hassle out of certification tracking by automating the process. They also help confirm that vendors uphold essential security and compliance certifications, such as HITRUST, SOC 2, and ISO 27001, as part of continuous vendor risk assessments. This not only makes compliance more efficient but also cuts down on manual work.
What evidence will auditors expect for patching and recovery deadlines?
Auditors will look for clear documentation that shows timely action on patching and recovery efforts. For example, they’ll expect proof that critical vulnerabilities were addressed within 15 calendar days, as outlined in the proposed 2025 HIPAA Security Rule updates. Keeping your records well-organized and demonstrating adherence to these timelines is crucial for meeting regulatory requirements.


