Safe Harbor vs. Expert Determination for PHI
Post Summary
When de-identifying Protected Health Information (PHI) under HIPAA, you have two main options: Safe Harbor and Expert Determination. Both methods aim to reduce re-identification risks, but they differ in complexity, flexibility, and data utility.
- Safe Harbor: A checklist-based approach that removes 18 specific identifiers (e.g., names, addresses, dates except year). It's simple, cost-effective, and works well for basic data needs. However, it limits data detail, making it less useful for advanced analytics or research.
- Expert Determination: A tailored method requiring a qualified expert to confirm that re-identification risk is "very small." It allows retaining more detailed data (e.g., month-specific dates, regional geography) but demands more effort, expertise, and ongoing governance.
Choosing the right method depends on your goals:
- Use Safe Harbor for straightforward compliance and low-risk data sharing.
- Opt for Expert Determination for detailed analytics, AI, or research requiring granular data.
Both methods are valid under HIPAA, but understanding their strengths and limitations ensures you balance data utility with privacy protection.
HIPAA De-Identification Standards
The HIPAA Privacy Rule (45 C.F.R. §164.514) outlines the steps required to strip health information of identifying details. De-identification, as defined under this regulation, involves modifying data so that individuals cannot be identified, either on its own or when combined with other information [7]. Proper de-identification is essential for securely managing Protected Health Information (PHI) while enabling broader data use. Once data meets HIPAA’s de-identification requirements, it is no longer classified as PHI and is exempt from HIPAA’s Privacy, Security, and Breach Notification Rules. Below, we break down the two main methods for de-identification under HIPAA.
Safe Harbor (§164.514(b)(2))
The Safe Harbor method relies on a straightforward checklist approach, requiring the removal of 18 specific identifiers from the data [7]. These identifiers include:
- Names
- Geographic details smaller than a state (except for certain ZIP code rules)
- All date elements except the year
- Telephone numbers, email addresses, and Social Security numbers
- Medical record numbers, account numbers, and other unique identifiers
For ages, individuals 90 years or older must be grouped into a single category labeled "90 or older." ZIP codes can retain the first three digits only if the population in that area exceeds 20,000; otherwise, the digits must be replaced with "000."
After removing these identifiers, the organization must ensure it has no actual knowledge that the remaining data could identify an individual, even when combined with other information. This method is relatively simple to follow and does not require specialized statistical expertise, making it a clear and accessible option for compliance.
Expert Determination (§164.514(b)(1))
Unlike Safe Harbor’s fixed checklist, Expert Determination offers a more flexible, context-specific approach to de-identification.
This method involves hiring a qualified expert in statistical de-identification [6]. The expert uses advanced techniques such as risk modeling, profiling quasi-identifiers, and simulating potential re-identification attacks. Common transformations applied during this process include suppression, generalization, aggregation, and adding noise to the data.
The expert’s role is to ensure that the likelihood of re-identification is very small, even when considering external data sources that may be reasonably available. Unlike Safe Harbor, Expert Determination allows for the retention of more detailed information - such as month-level dates or regional geographic data - if the expert can demonstrate that the residual risk is minimal under the specific circumstances of data use. However, this method requires thorough documentation, including the expert’s qualifications, methodology, and risk assessment process.
Safe Harbor Method for PHI De-Identification
The Safe Harbor method, outlined under 45 C.F.R. §164.514(b)(2), provides a structured checklist approach for de-identifying protected health information (PHI). By systematically removing 18 specific identifiers listed in the regulation and ensuring no remaining data can reasonably identify an individual, organizations can use this method to comply with HIPAA standards. This makes Safe Harbor a straightforward option for compliance and health information management teams, especially when handling routine data releases.
Advantages of Safe Harbor
One of the biggest strengths of the Safe Harbor method is its clarity and ease of implementation. Since it's defined by federal regulation and supported by detailed guidance from the Department of Health and Human Services (HHS), organizations can quickly standardize internal processes, train staff, and integrate de-identification into workflows like electronic health record exports, analytics pipelines, and reporting templates. The method's prescriptive nature ensures that the resulting data meets HIPAA requirements, offering strong regulatory support.
This approach is particularly effective for creating basic, aggregate datasets where detailed granularity isn't necessary. For example, a health system might remove patient names, report only the year of events, and combine age data into broader categories. This yields aggregate statistics that work well for tasks like benchmark reporting while keeping re-identification risks low. However, the method's rigid structure can sometimes limit how useful the data is for more complex analyses.
Limitations of Safe Harbor
While Safe Harbor provides clear guidelines, its limitations can hinder certain types of research and analysis. For instance, eliminating all date details below the year level makes it challenging to study trends like seasonal variations, care pathways, or 30-day readmissions. Similarly, limiting geographic information - such as using only three-digit ZIP codes with populations over 20,000 - can restrict studies that require detailed location data, like those focusing on social determinants of health or outbreak tracking. Aggregating ages of individuals 90 and older into a single category also reduces precision, which can be a drawback for research in fields like geriatrics or oncology.
Another concern is that the Safe Harbor identifier list was created before the rise of modern digital identifiers and the widespread availability of external datasets. This means that while the method reduces re-identification risks, it doesn’t eliminate them entirely. Studies have shown that linking Safe Harbor-compliant data with external sources can still lead to re-identification, particularly in smaller or unique populations. For large-scale data releases, professional review is recommended to address these gaps.
When to Use Safe Harbor
Safe Harbor is best suited for situations where data-sharing needs are low-risk and high-level insights are sufficient. Common use cases include public reporting of annual quality metrics by state, dashboards showing aggregate utilization or outcome rates, and demonstration datasets for educational purposes. It’s also a practical choice for organizations that lack access to statistical experts or need quick, repeatable de-identification workflows.
Even when using Safe Harbor, it’s crucial to incorporate it into a broader risk management plan. Organizations should evaluate factors like who will access the data, how it will be stored, and whether external datasets could enable re-identification. Best practices include adding contractual safeguards (e.g., prohibiting re-identification or data linkage), enforcing role-based access, and monitoring data usage through logging. Regularly reviewing de-identification policies is also important as technology evolves.
To enhance Safe Harbor's effectiveness, tools like Censinet RiskOps™ can support data flow inventory, third-party risk assessments, and robust controls. By embedding Safe Harbor into a comprehensive risk management strategy, organizations can maintain HIPAA compliance while balancing the need for data utility and security.
Expert Determination Method for PHI De-Identification
The Expert Determination method, as described in 45 C.F.R. §164.514(b)(1), takes a different approach from the Safe Harbor method. Instead of following a standardized checklist, this method relies on a qualified statistical expert to evaluate the risk of re-identification within a given context [3][7]. The expert considers factors like how the data will be used, potential external risks, and realistic threats. This tailored assessment allows organizations to retain more detailed data while still complying with HIPAA regulations [7][2]. Unlike Safe Harbor, which is rigid in its requirements, Expert Determination offers the flexibility needed for more complex data analysis.
This approach is particularly beneficial for high-value research and advanced analytics.
Advantages of Expert Determination
One of the key benefits of Expert Determination is its ability to preserve important details - such as month-specific dates and regional geographic data - that are crucial for sophisticated analytics like AI training and predictive modeling [2][8]. For instance, in projects analyzing seasonal hospital utilization patterns, an expert might allow the use of admission and discharge months instead of just years. Meanwhile, other protections, like generalizing geographic details or addressing outliers, help to manage re-identification risk [2].
This flexibility is a major advantage for tasks like AI model training, predictive analytics, and longitudinal research, as it retains essential temporal and geographic details [2][5]. By tailoring protections to specific use cases and implementing recipient controls, organizations can support a wide range of scenarios, from multi-institutional research to advanced analytics pipelines - scenarios that would be severely limited by Safe Harbor's more restrictive rules [2][8].
Limitations of Expert Determination
However, this flexibility comes with added complexity and costs. The method requires organizations to depend on external experts [3][8]. These professionals must have expertise in statistical disclosure control, often coming from fields like statistics, biostatistics, or data privacy. They use established scientific methods to assess risks [3][7][2].
The process also involves detailed documentation, including expert qualifications, risk models, and assumptions, which must be maintained and made available to regulators like the HHS Office for Civil Rights during audits or investigations [3][7]. Additionally, organizations must monitor for changes in external data sources, data-sharing practices, or adversary capabilities that could increase re-identification risks. Such changes might require re-evaluating datasets and updating de-identification strategies [2][6]. The HHS emphasizes that this is not a one-time process; experts may need to reassess datasets as new technologies and use cases emerge [7][2].
These challenges underscore the importance of using Expert Determination in the right situations.
When to Use Expert Determination
Expert Determination is most valuable when retaining detailed temporal, geographic, or clinical data is critical for analytics. For example, AI and machine learning projects often rely on granular features like visit timing, care pathways, utilization trends, or regional differences [2][8]. Longitudinal and outcomes research also benefits when precise timelines and repeated measures are needed to study disease progression, treatment responses, or readmission risks [2][5].
This method is especially useful for rare disease studies or small-cohort research, where Safe Harbor might suppress too much data. Expert Determination allows for more nuanced approaches, such as generalizing age ranges, masking unique data combinations, or limiting access to secure data environments. These measures enable researchers to uncover patterns that would be lost under Safe Harbor’s broader generalizations [2][6]. It’s also ideal for sharing data with trusted research partners under strict contractual, technical, and operational safeguards. In these cases, the expert can account for these protections in the risk assessment, allowing for greater analytic utility [2][7].
sbb-itb-535baee
Safe Harbor vs. Expert Determination
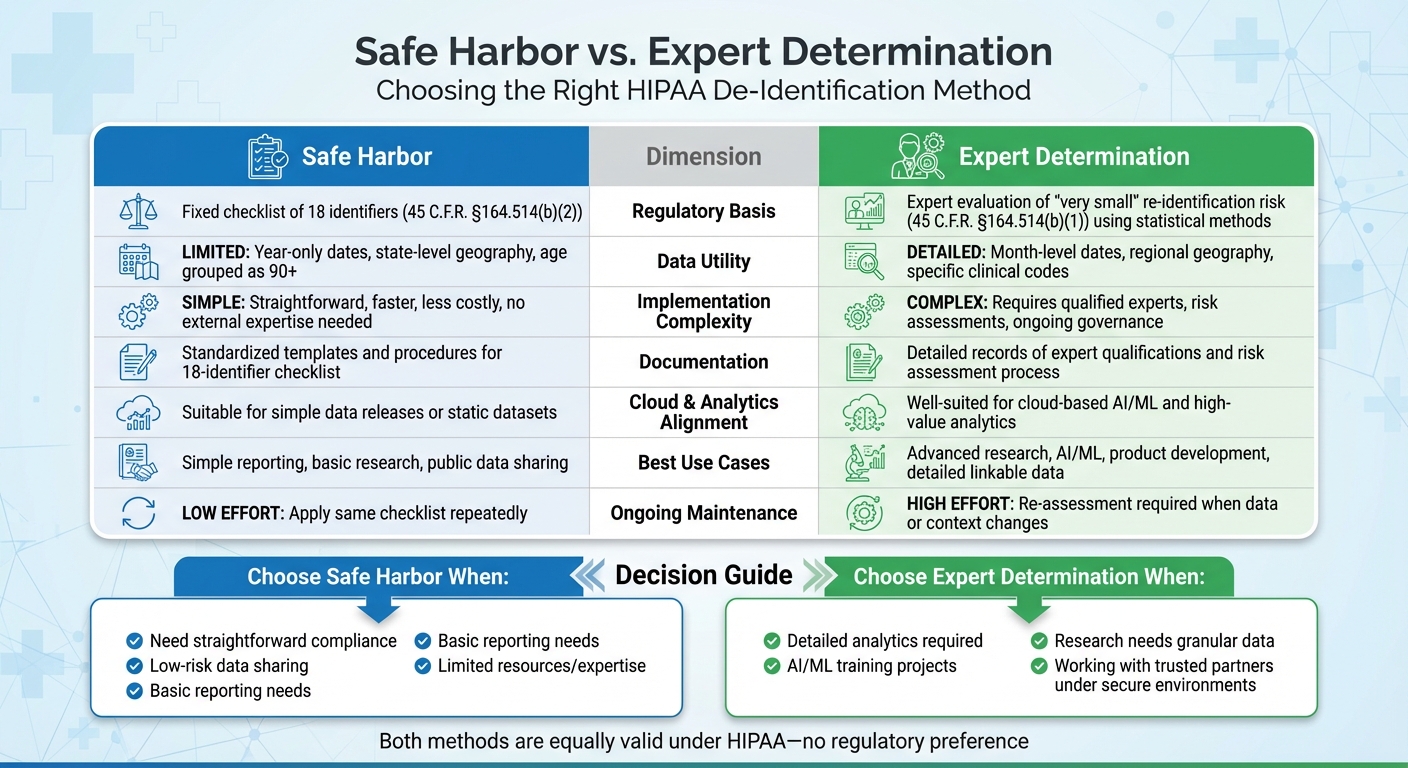
Safe Harbor vs Expert Determination: HIPAA De-Identification Methods Comparison
When it comes to de-identifying data under HIPAA, both Safe Harbor and Expert Determination are equally valid methods - there’s no regulatory preference between the two [7]. However, the approaches differ significantly in how they operate, what they require, and the scenarios where they work best.
Side-by-Side Comparison
Here’s a breakdown of the key differences between these two methods:
| Dimension | Safe Harbor | Expert Determination |
|---|---|---|
| Regulatory Basis | Relies on a fixed checklist of 18 identifiers as outlined in 45 C.F.R. §164.514(b)(2) [7] | Involves expert evaluation of "very small" re-identification risk under 45 C.F.R. §164.514(b)(1), using statistical methods [7] |
| Data Utility | Limited granularity: includes year-only dates, state-level geography, and age grouped as 90+ [2][5][8] | Allows more detailed data: retains month-level dates, regional geography, and specific clinical codes [2][8] |
| Implementation Complexity | Straightforward, faster, and less costly - follows a fixed set of rules without needing external expertise [2][4][8] | More involved and resource-heavy - requires qualified experts, risk assessments, and ongoing governance [2][3][6][8] |
| Documentation Requirements | Standardized templates and procedures to apply the 18-identifier checklist [5][7] | Requires detailed records of expert qualifications and the risk assessment process [2][3][6][7] |
| Cloud & Modern Analytics Alignment | Suitable for simple data releases or static datasets but may not meet the needs of advanced analytics [2][8] | Well-suited for cloud-based AI/ML and high-value analytics; integrates technical and contractual safeguards into the risk model [2][8][9] |
| Best Use Cases | Ideal for simple reporting, basic research, or public data sharing where high data utility isn’t critical [2][5][8] | Best for advanced research, AI/ML, product development, or scenarios requiring detailed, linkable data [2][4][8][9] |
| Ongoing Maintenance | Low effort - apply the same checklist repeatedly, with occasional reviews for edge cases [3][5][8] | Requires re-assessment whenever data or its context changes [2][3][6] |
How to Choose Between the Two Methods
Your choice between Safe Harbor and Expert Determination should depend on your operational goals, data needs, and available resources. Let’s break it down:
- Define your data needs. If your project involves basic reporting or simpler datasets, Safe Harbor is often enough. For more detailed analyses, Expert Determination offers greater flexibility and utility [2][8].
- Assess data sensitivity and re-identification risk. For unique populations, such as rare disease groups or small rural communities, Safe Harbor’s generalized approach might not fully mitigate risks. Expert Determination, on the other hand, can implement tailored controls that address specific vulnerabilities [2][5].
- Consider the recipient and intended use. If the data will be shared publicly with minimal oversight, Safe Harbor provides a clear, standardized framework. However, if you’re sharing data with trusted partners under secure environments and detailed agreements, Expert Determination allows for richer datasets while maintaining a documented "very small" risk profile [2][6][9]. Tools like Censinet RiskOps™ can help document these safeguards [2].
- Evaluate your internal capabilities and budget. Organizations without access to qualified experts or advanced governance frameworks may start with Safe Harbor due to its simplicity. Over time, as expertise and resources grow, Expert Determination can be layered in for high-priority projects [2][3]. Risk-averse organizations may lean toward Safe Harbor when utility trade-offs are acceptable, while others may prefer Expert Determination to maximize data value while maintaining defensible risk documentation [2][3].
Each method has its strengths, and the right choice depends on balancing your organization’s needs with its ability to manage risks effectively.
Implementing De-Identification with Risk Management Solutions
When it comes to protecting PHI (Protected Health Information), having a solid risk management strategy is non-negotiable. Effective de-identification hinges on centralized systems that can oversee PHI inventories, monitor data flows across on-premises, cloud, and third-party environments, and maintain comprehensive, auditable records of de-identification processes. This is where platforms like Censinet RiskOps™ come into play.
How Censinet RiskOps™ Supports De-Identification

Censinet RiskOps™ simplifies the de-identification process by integrating Safe Harbor and Expert Determination workflows directly into enterprise risk management systems.
- Safe Harbor Compliance: The platform enforces HIPAA’s checklist for the 18 identifiers that must be removed, ensuring compliance through attestations and linking controls to specific applications, data lakes, and cloud services. This approach provides verifiable evidence, which is critical for audits or investigations by the Office for Civil Rights (OCR).
- Expert Determination Governance: For organizations opting for Expert Determination, RiskOps™ offers structured governance tools. It stores expert credentials, captures engagement details, and documents the entire workflow - from risk modeling to final outcomes. Each determination is versioned, timestamped, and triggers reassessments when datasets, recipients, or environments change. This replaces scattered documentation with a centralized, reliable system that security, privacy, and compliance teams can trust.
Managing PHI risks becomes even more critical as healthcare data increasingly moves to cloud-based systems and third-party platforms. RiskOps™ profiles each vendor’s de-identification protocols and security measures, consolidating responses, evidence, and artifacts. It evaluates key controls like encryption, access management, and environment isolation, all of which are essential to reducing re-identification risks.
Terry Grogan, CISO at Tower Health, shared: "Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required." [1]
James Case, VP & CISO at Baptist Health, added: "Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with." [1]
These efficiency gains are invaluable, especially when managing the extensive documentation required for Expert Determination or handling repetitive validation tasks under Safe Harbor across multiple systems and vendors.
Improving Efficiency with Censinet AI

Censinet AI takes these capabilities a step further by introducing automation and proactive analysis to streamline workflows. It reviews vendor responses, technical documents, and contracts to pinpoint gaps in de-identification controls or missing evidence for Expert Determination. The AI categorizes systems and datasets based on sensitivity - whether they contain full PHI, Safe Harbor de-identified data, Expert Determination data, or non-PHI - and recommends appropriate control frameworks. It also monitors for changes in threats, external datasets, or system architectures that might require reassessment, while drafting summaries of expert reports for compliance and executive teams.
Collaboration across teams becomes seamless as the AI routes assessments to the right stakeholders. For instance, technical control issues are sent to the security team, while HIPAA or contractual concerns are directed to privacy and compliance teams. It also creates tailored views - clinicians get summaries of re-identification risks and methods, while security teams receive detailed insights into control gaps and remediation tasks. By integrating task assignments and AI-driven insights, teams can quickly determine whether Safe Harbor is sufficient or if Expert Determination is necessary.
Censinet AI ensures that everyone involved - whether in security, compliance, or clinical roles - has the tools and information they need to make informed decisions while maintaining a unified, accurate record of risks and resolutions.
Conclusion
When it comes to sharing data securely, Safe Harbor is your go-to for straightforward, checklist-based approaches with lower risk, while Expert Determination shines in scenarios requiring detailed data for advanced analytics. The key is to align your choice with your specific data needs, governance capabilities, and appetite for risk.
It's worth noting that neither method completely eliminates the possibility of re-identification. Instead, both aim to reduce the risk to levels acceptable under HIPAA. De-identification should be seen as just one piece of a larger cybersecurity puzzle that includes measures like contractual safeguards, access controls, encryption, logging, and incident response plans. These measures need regular reassessment, especially for Expert Determination releases, as external data landscapes shift and evolve.
Think of de-identification as more than a compliance tool - it's a gateway to innovation and research. By integrating Safe Harbor and Expert Determination workflows into platforms like Censinet RiskOps™, you can centralize critical documentation, manage expert engagements, and maintain auditable records that link PHI usage across your systems. This approach empowers stakeholders with the insights and tools they need to make informed decisions while safeguarding patient trust and ensuring compliance.
To prepare for the future, consider adopting a blended strategy. Use Safe Harbor for routine, low-complexity cases and develop robust Expert Determination capabilities for high-value, complex projects. This portfolio-style approach not only supports innovation but also positions you to navigate audits and adapt as new risks emerge.
FAQs
How do I decide between using Safe Harbor and Expert Determination to de-identify PHI?
When deciding between Safe Harbor and Expert Determination for de-identifying protected health information (PHI), it’s essential to weigh factors like the complexity of your data, the resources at your disposal, and your organization’s approach to risk and compliance.
Safe Harbor is a good fit if you’re looking for a clear, standardized method. This approach requires the removal of 18 specific identifiers from the data, following well-defined rules. It’s often quicker to implement and demands fewer resources, making it a practical choice for many organizations.
On the other hand, Expert Determination is better suited for situations involving more complex or specialized datasets. This method calls for a qualified expert to evaluate and reduce the risk of re-identification, offering a tailored solution for unique challenges. It’s a more flexible option but may require additional time and expertise.
Ultimately, your choice should align with your organization’s objectives, the type of data you’re working with, and the regulatory standards you need to meet.
What is the Expert Determination method, and how does it balance data privacy with usability?
The Expert Determination method offers a tailored way to de-identify Protected Health Information (PHI). This approach involves a qualified expert who evaluates the data and applies specific techniques to reduce the risk of re-identification, all while preserving the data's usefulness for research, analysis, or operational needs.
Because the process is customized to fit the unique characteristics of each dataset and its intended use, it strikes a balance between safeguarding privacy and maintaining the data's practicality. This makes it an effective option, especially for handling complex or highly valuable datasets.
What are the risks of using only the Safe Harbor method for de-identifying PHI under HIPAA?
Relying only on the Safe Harbor method to de-identify Protected Health Information (PHI) under HIPAA can leave data vulnerable to re-identification, particularly when combined with publicly available information. While this method follows a standardized process, it may not sufficiently anonymize data in every situation, potentially exposing sensitive information.
On the other hand, the expert determination method offers a more adaptable and case-specific approach to de-identification. However, it requires skilled professionals and ongoing validation to ensure it meets compliance standards. Organizations need to weigh their specific needs and risk levels carefully when deciding which method to use to safeguard patient privacy.


