Scaling IoT Security for Healthcare Networks
Post Summary
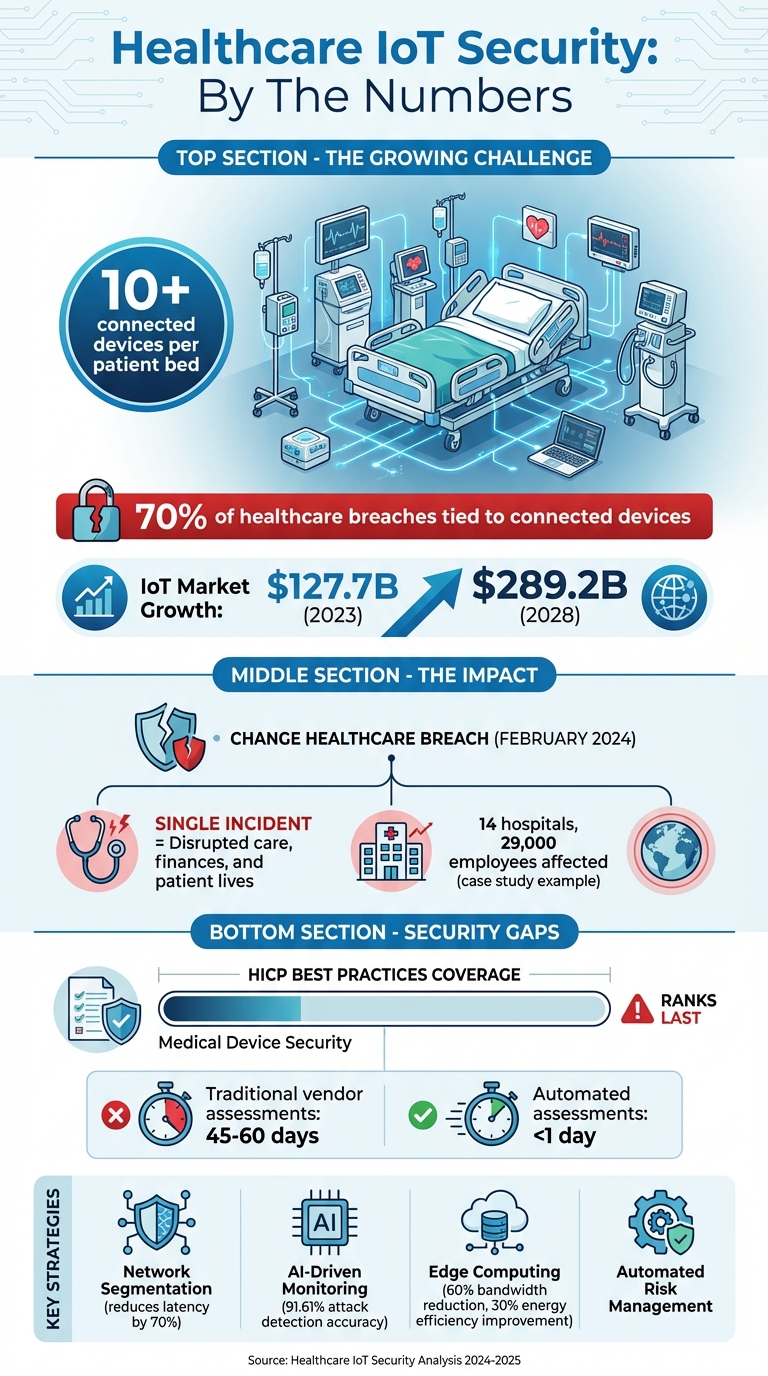
Healthcare IoT is growing fast, but so are the risks. With over 10 connected devices per patient bed, securing these networks is critical - not just for data protection but for patient safety. Cyberattacks like the February 2024 breach on Change Healthcare show how a single incident can disrupt care, finances, and lives.
Here’s the challenge: IoT devices in healthcare are diverse, often outdated, and lack built-in security. Managing them manually is no longer feasible. To address this, healthcare organizations need scalable solutions that balance security with smooth operations. Key strategies include:
- Network segmentation: Isolate devices to limit risks.
- AI-driven monitoring: Detect threats in real-time without disrupting care.
- Edge computing: Process data closer to devices for faster, safer responses.
- Lifecycle management: Secure devices from procurement to retirement.
- Vendor risk assessments: Streamline evaluations to address third-party vulnerabilities.
Regulations like HIPAA and NIST frameworks are pushing healthcare providers to improve IoT security. Tools like Censinet RiskOps™ simplify this process by automating assessments, managing vendor risks, and providing real-time updates.
Why it matters: 70% of healthcare breaches tie back to connected devices. Protecting these systems isn’t just about compliance - it’s about saving lives.
Healthcare IoT Security Statistics and Key Challenges
Navigating the Complexity of IoT Device Vulnerability: The Future State of Medical Device Security
sbb-itb-535baee
Challenges in Scaling Healthcare IoT Security
Scaling IoT security in healthcare isn’t just about adding more tools or hiring extra staff; it’s a complex puzzle involving devices, personnel, and regulatory frameworks. These challenges lay the groundwork for the strategies discussed in the next sections.
Managing Diverse Devices and Interoperability
The healthcare IoT ecosystem is incredibly varied, encompassing everything from wearables to imaging systems. Each device comes with its own operating system, functions, and communication protocols [7]. This diversity makes it tough to establish consistent security standards. For example, a cardiac monitor and an insulin pump may require entirely different protocols, yet both need to securely connect to an EHR system.
Adding to this complexity, many medical devices have limited processing power, memory, and battery capacity. This makes implementing strong encryption or real-time threat detection a challenge. Legacy systems, which were never intended for IoT connectivity or modern cyber threats, further exacerbate vulnerabilities. A 2025 benchmarking study of 69 healthcare and payer organizations revealed persistent gaps in asset management and third-party risk [3]. Without clear visibility into all connected devices, managing risks effectively becomes nearly impossible [5].
Security vs. Operational Efficiency Trade-offs
Tight security measures often clash with the need for seamless clinical workflows [7]. Take a nurse administering medication during an emergency - waiting for multiple authentication steps on a smart infusion pump could delay critical care. In such moments, operational efficiency takes precedence, even if it means potential security risks.
Healthcare facilities frequently rely on wireless networks like Wi-Fi, which are vulnerable to interception, spoofing, and man-in-the-middle attacks [7]. While network segmentation can isolate vulnerable devices and enhance security, it also complicates access to patient data for clinicians. Many devices also lack the ability to perform smooth firmware updates, leaving them exposed to known vulnerabilities. In some cases, hospitals might even need to take essential monitors offline during peak hours to address these issues.
John Riggi, National Advisor for Cybersecurity and Risk at the American Hospital Association, underscores the stakes:
Ransomware and other cyber threats are becoming more targeted and destructive, putting patient lives at risk [6].
These examples illustrate the delicate balance between ensuring security and maintaining operational efficiency - a balance that is critical to patient care.
Meeting Regulatory Requirements While Protecting Patients
Navigating healthcare regulations like HIPAA while scaling IoT security adds another layer of complexity. Organizations must juggle multiple frameworks, including the NIST Cybersecurity Framework 2.0, Healthcare and Public Health Cybersecurity Performance Goals (HPH CPGs), and Health Industry Cybersecurity Practices (HICP) [3][6]. Each framework has unique requirements, assessment processes, and documentation standards.
The statistics are alarming: Medical Device Security ranks last in coverage across all ten HICP best practices for healthcare delivery organizations [4]. Considering that modern hospitals average over 10 connected devices per patient bed, this gap is particularly concerning [4]. Achieving compliance requires collaboration across IT, Risk, Cybersecurity, and Biomedical departments [4]. Greg Garcia, Executive Director of the Health Sector Coordinating Council Cybersecurity Working Group, highlights the urgency:
As healthcare organizations face new federal cybersecurity requirements in the wake of escalating cyberattacks... the Benchmarking Study provides critical guidance and a clear path toward compliance [6].
Balancing regulatory demands with patient care calls for more than just technical fixes - it requires a significant organizational shift to align priorities and resources effectively.
Strategies for Scaling IoT Security in Healthcare
Securing IoT systems in healthcare demands practical strategies that safeguard sensitive data while keeping clinical operations running smoothly. Here are some key approaches to protect healthcare IoT ecosystems without disrupting patient care.
Network Segmentation and Access Controls
Dividing your network into isolated zones is a simple yet effective way to limit threats and secure sensitive information. Using VLANs (Virtual Local Area Networks), you can separate traffic based on device type - dedicating specific segments to clinical systems handling Protected Health Information (PHI), administrative workstations, guest Wi-Fi, and IoT devices like security cameras [11]. HealthDesk IT emphasizes:
HIPAA requires technical safeguards to protect PHI, including network segmentation. VLANs isolate patient data from other network traffic, preventing unauthorized access and containing potential security breaches. [11]
To make this work, apply Zero Trust principles: identify all devices through deep profiling, restrict access so devices only communicate with necessary systems, and continuously monitor network activity [9][10]. Contextual segmentation, instead of relying just on IP-based rules, helps manage both managed and unmanaged devices. For instance, an insulin pump should only connect to specific electronic health record systems. Pair this with an integrated Medical IoT security platform and Network Access Control (NAC) solutions for seamless policy enforcement [9].
Before setting up VLANs, conduct a thorough network assessment to find security gaps and align with HIPAA requirements [11]. Use VLAN-aware switches and firewalls with inter-VLAN routing to enforce segmentation. Also, maintain detailed network maps and ensure guest networks are strictly isolated [11]. This structured approach not only complies with HIPAA but also strengthens your network's overall security.
Once segmentation is in place, advanced monitoring tools can help detect threats as they arise.
Real-Time Monitoring and Threat Detection
With the healthcare IoT market projected to grow from $127.7 billion in 2023 to $289.2 billion by 2028 [12], manual monitoring is no longer practical. AI-driven analytics can process vast data volumes quickly, identifying anomalies like DDoS attacks or ransomware that might otherwise slip through the cracks [7][2]. Passive monitoring ensures full visibility into device traffic without interfering with the performance of medical equipment, making it scalable for thousands of devices [12].
For example, a large healthcare provider in the Midwest with 14 hospitals and 29,000 employees adopted an AI-powered analytics platform using User and Entity Behavior Analytics (UEBA). This system automated anomaly detection, providing real-time visibility across both cloud and on-premises environments [2].
Next-Generation Firewalls (NGFWs) with built-in intrusion detection and prevention systems add another layer of security at the network level [1]. Palo Alto Networks explains the advantage of such tools:
Instead of forcing hospitals to choose between security and patient care, this AI-driven approach applies virtual patches in real-time - protecting vulnerable medical devices at the network level without disrupting their operation. [1]
To handle threats efficiently, consider deploying Security Orchestration, Automation, and Response (SOAR) platforms. These systems automate threat mitigation across large networks while minimizing administrative workload. Multifactor risk scoring, which evaluates both exploitability and asset importance, helps prioritize the most critical threats [2][1].
Edge Computing for Secure Data Processing
Edge computing takes security a step further by processing data closer to IoT devices, reducing latency and enhancing safety - especially when every millisecond counts in patient care. This approach ensures that critical patient metrics are handled locally, allowing for immediate responses during emergencies [13]. A hybrid fog-edge architecture can cut latency by up to 70% compared to cloud-only setups [13].
Edge devices equipped with rule-based filtering and lightweight machine learning models focus on transmitting only essential alerts, such as abnormal readings or high-risk signals. This reduces bandwidth usage by 60% and improves energy efficiency by 30% [13]. For instance, setting clinical thresholds (e.g., a heart rate over 120 bpm) ensures that only crucial alerts use high-priority bandwidth [13].
The combination of edge and fog layers also creates a decentralized defense system. Strong encryption and distributed authentication secure data transfers between edge and cloud systems [13]. AI models deployed at the edge, like Variational Autoencoders, have demonstrated 91.61% accuracy in detecting IoMT-specific cyberattacks, including man-in-the-middle attacks [14]. Intermediate fog nodes can anonymize and compile data, protecting patient information before long-term storage. By deploying local gateways or fog nodes, healthcare organizations can retrofit older medical devices with modern security measures like TLS protocols and token-based access [13]. This ensures even legacy systems benefit from enhanced security.
Device Lifecycle Management and Vendor Security
Managing the entire lifecycle of connected devices is essential for maintaining strong security in today's healthcare environments. With numerous IoT devices in play, automated systems are critical for tracking and safeguarding these assets throughout their use.
Securing Devices from Procurement to Retirement
The security of a device begins long before it connects to your network. During the procurement phase, standardized tools like the Manufacturer Disclosure Statement for Medical Device Security (MDS2) can help identify potential risks early on[4]. This pre-purchase evaluation allows for smarter decisions by flagging vulnerabilities upfront.
Once a device is approved, its identity and security posture must be verified before it can access the network. As outlined in NIST SP 1800-36:
Trust is achieved by attesting and verifying the identity and posture of the device and the network before providing the device with its network credentials - a process known as network-layer onboarding.[15]
To further reduce risks, implement Manufacturer Usage Descriptions (MUD). These help define and enforce the specific network behaviors a device is allowed, minimizing its exposure to attacks[15]. Throughout the device's lifecycle, maintain a centralized digital inventory that includes automated risk assessments and Corrective Action Plans (CAPs) for any identified issues[4]. This requires collaboration across IT, Risk, Cybersecurity, and Biomedical teams, all working together on a unified platform[4].
Ongoing security checks are equally important. For instance, after maintenance, a device's security posture should be reverified before reconnecting it to the network[15]. When a device reaches the end of its life, follow strict decommissioning protocols to ensure all data is securely erased and the device is disposed of properly.
While securing devices internally is vital, evaluating vendor practices is another key aspect of managing overall risk.
Assessing Vendor Security Practices
Traditional vendor assessments, which can take up to 60 days, are often too slow for today’s fast-paced environments. Delta-based reassessments offer a faster alternative, cutting the process down to less than a day[16][17]. Collaborative risk networks simplify this further by enabling vendors to complete standardized questionnaires once and share them with multiple clients, improving both transparency and efficiency[16].
Vendors should be prioritized based on their access to sensitive patient data or their role in managing critical medical devices. High-risk vendors should undergo annual reviews, while those with lower risk profiles can be assessed less frequently[16]. Platforms that automatically update residual risk ratings in real time based on vendor data changes can streamline this process[16]. Additionally, automated alerts can notify you of breaches or ransomware incidents affecting any vendor in your supply chain[16].
For added efficiency, digital risk catalogs now include over 50,000 pre-assessed vendors and products, offering a solid starting point for due diligence[16]. Use risk management platforms to negotiate and document remediation efforts, ensuring a continuous audit trail for compliance and accountability[16]. This centralized approach simplifies vendor management while enhancing security oversight.
Using Censinet RiskOps for Scalable IoT Security
Censinet RiskOps™ is designed to streamline third-party risk management for healthcare IoT ecosystems. By leveraging a cloud-based risk exchange, it keeps up with the demands of thousands of connected devices, enabling healthcare organizations and their vendors to share cybersecurity data instantly.
Simplifying Third-Party Risk Assessments
Traditional risk assessments can take up to 45–60 days, often delaying device procurement and security evaluations[17]. Censinet RiskOps™, however, speeds up this process significantly - reassessments now average less than a day[16]. Thanks to features like 1-Click Sharing, vendors only need to complete standardized questionnaires and upload evidence once to a Cybersecurity Data Room™, which is then accessible to an unlimited number of customers[16].
The platform's Digital Risk Catalog™ provides instant access to pre-assessed risk scores for over 50,000 vendors and products[16]. This allows healthcare organizations to evaluate IoT devices during procurement without starting from scratch. Automated risk scoring updates in real time as vendor data changes, and Active Portfolio Management sends immediate alerts about breaches or ransomware incidents involving any vendor in your portfolio[16]. This eliminates the need for manual tracking and ensures timely notifications for potential security threats.
These automated processes naturally evolve into benchmarking and collaborative strategies, strengthening IoT security across the board.
Benchmarking IoT Security Across Organizations
Beyond speeding up assessments, Censinet RiskOps™ offers tools for continuous benchmarking, helping organizations improve their security programs. With over 100 provider and payer facilities participating in the Censinet Risk Network[16], healthcare organizations can compare their IoT security maturity against industry peers. This benchmarking feature highlights potential vulnerabilities and prioritizes improvements based on proven strategies.
The platform also maintains longitudinal risk records, documenting every assessment, piece of evidence, and remediation effort[18]. These records are valuable during audits or security investigations, providing a comprehensive history of your risk management activities.
Collaborative Risk Management for IoT Devices
Censinet RiskOps™ replaces inefficient communication methods like email and spreadsheets with in-platform remediation negotiation[16]. Corrective Action Plans (CAPs) can be assigned and tracked directly with vendors, ensuring that security gaps are addressed without the need for constant follow-ups. The platform automatically identifies gaps and suggests remediation actions, simplifying the entire process[18].
With Censinet Connect™, completed security questionnaires can be shared beyond your immediate network[16]. This feature is particularly helpful when multiple facilities need to assess the same vendor, reducing redundant work across the healthcare ecosystem.
Additionally, the platform allows organizations to categorize IoT devices by clinical impact and PHI exposure. It then schedules reassessments based on risk levels, such as annual reviews for high-risk devices[18]. This targeted approach ensures that resources are focused on the most critical areas while maintaining oversight across the entire device portfolio.
| Feature | Manual Assessment Process | Censinet RiskOps™ |
|---|---|---|
| Assessment Duration | 45–60 Days[17] | < 1 Day (for reassessments)[16] |
| Data Sharing | Email/Spreadsheets | 1-Click Sharing / Risk Network |
| Risk Scoring | Manual Calculation | Automated / Real-Time |
| Remediation | Manual Follow-up | Automated Corrective Action Plans (CAPs) |
| Visibility | Point-in-time | Continuous / Longitudinal Record |
Future Trends in Healthcare IoT Security
AI and Automation for Threat Detection
Artificial intelligence is transforming IoT security in healthcare by enabling real-time threat detection and response. Advanced hybrid deep learning models - combining Convolutional Neural Networks (CNNs) for spatial data, Long Short-Term Memory networks (LSTMs) for temporal patterns, and Variational Autoencoders (VAEs) for data integrity - are delivering multi-layered defense capabilities. These systems achieve impressive metrics, like an F1-score of 94.3% for anomaly detection and 96.1% accuracy for access classification, improving detection sensitivity by 12–18% [19].
Edge intelligence is playing a critical role in healthcare IoT security. AI models are now optimized for edge devices, such as Jetson Nano and Raspberry Pi, delivering inference latency under 160 milliseconds. Additionally, Trust-Aware Adaptive Controllers are being deployed to automatically quarantine or restrict traffic from devices with low reliability scores [19].
To bolster detection accuracy, healthcare organizations are adopting multi-modal systems that analyze both spatial data (like ECG spikes) and temporal trends (such as long-term vital signs). Incorporating frameworks like the NIST AI Risk Management Framework can help reduce false positives and manage the risks associated with AI-based solutions [3].
Blockchain technology is also stepping in to address data integrity challenges in IoT networks.
Blockchain for IoT Data Security
Blockchain offers a robust solution for securing IoT data in healthcare by ensuring tamper-proof records and creating immutable audit trails. Its decentralized nature allows prediction outcomes and system events to be securely logged and verified without introducing significant latency. For example, lightweight fog-layer blockchain modules can generate blocks in under 20 milliseconds [20].
"By leveraging the immutable and decentralized characteristics of blockchains, prediction outcomes and system events can be securely logged and later verified." – Springer Cluster Computing [20]
Smart contracts are becoming essential for automating device verification, registration, and access permissions. These contracts eliminate single points of failure, enhancing system reliability against cyberattacks [21][22]. Dual-blockchain architectures - public for patient connectivity and private for internal operations - combined with IPFS for off-chain storage, are being adopted to improve efficiency and throughput [22].
To strengthen device authentication, healthcare organizations are implementing the Elliptic Curve Digital Signature Algorithm (ECDSA), which generates unique public-private key pairs for signing data. For devices with limited processing power, proxy devices can step in to manage access and handle complex smart contract executions [22].
As these technologies advance, regulatory frameworks are evolving to ensure their secure implementation.
How New Regulations Will Shape IoT Security
Regulations are increasingly shaping the landscape of IoT security in healthcare. NIST Special Publication 1800-36 is emerging as a key standard, focusing on automated mechanisms to verify device identity and security posture during network onboarding and throughout the device lifecycle [15].
"Establishing trust between a network and an Internet of Things (IoT) device... prior to providing the device with the credentials it needs to join the network is crucial for mitigating the risk of potential attacks." – NIST SP 1800-36 [15]
The Healthcare and Public Health Cybersecurity Performance Goals (HPH CPGs) are becoming a benchmark for assessing cybersecurity maturity across healthcare organizations. A study involving 69 healthcare and payer organizations between September and December 2024 revealed that the February 2024 cyberattack on Change Healthcare has pushed the industry toward stricter third-party risk management and enhanced ecosystem security [3]. Many organizations are aligning their practices with the updated NIST Cybersecurity Framework 2.0 and the NIST AI Risk Management Framework to address risks associated with third-party AI tools in clinical applications [3][8].
To meet these evolving standards, healthcare providers are adopting Manufacturer Usage Description (MUD) standards, which automate rules for how IoT devices communicate on networks [15]. Conducting third-party AI risk assessments, particularly for tools used in clinical decision-making and imaging analysis, is also becoming a regulatory necessity [8]. Verifying device identity and assessing security posture before onboarding are now essential steps to comply with these updated guidelines [15].
Conclusion
Securing IoT systems in healthcare is no longer optional - it’s essential for protecting patient safety and keeping operations running smoothly. With 70% of healthcare breaches tied to connected devices[23][24], the stakes couldn’t be higher. The February 2024 ransomware attack on Change Healthcare highlighted just how devastating a single incident can be, rippling through care delivery, financial systems, and patient outcomes[3].
"The ransomware attack underscored the deep interdependencies among providers, payers, and third-party vendors - revealing how a single disruption within this interconnected ecosystem can cascade across care delivery, financial operations, and patient safety throughout the sector." – Censinet[3]
Addressing these risks requires healthcare organizations to break down silos and promote collaboration among IT, risk management, cybersecurity, and biomedical teams. Medical device security remains a major weak point, as highlighted in the HICP best practices report[4]. To tackle this, organizations need to move beyond manual, one-off assessments and adopt automated, continuous risk management processes.
One example of this approach is Censinet RiskOps™, which offers a comprehensive solution to simplify these challenges. The platform automates the intake of manufacturer security data, maintains a Digital Risk Catalog™ with over 50,000 vendors and products, and reduces reassessment times to less than a day using delta-based reviews[16]. By centralizing third-party risk assessments and enabling collaborative risk management, Censinet helps healthcare systems identify and address vulnerabilities before they disrupt operations, while also ensuring compliance with regulatory standards[16].
As healthcare organizations look to the future, scalable strategies like real-time monitoring, network segmentation, and edge computing will be crucial. Emerging technologies such as AI-driven threat detection and blockchain-based data security, alongside evolving regulations, are reshaping the landscape. By adopting automated, integrated solutions, healthcare providers can turn IoT security from a liability into a competitive edge.
FAQs
What’s the first step to secure all IoT devices across a large hospital network?
To start, compile a comprehensive inventory of all connected IoT devices within the network. Once you have the list, evaluate each device for potential vulnerabilities and assign a risk level to each one. This categorization allows you to focus on the most critical risks first, ensuring your security measures are both efficient and effective. By doing this, you gain a clear picture of your network's weak points and can implement protections tailored to those specific needs.
How can we improve IoT security without slowing down clinical workflows?
To strengthen IoT security in healthcare while keeping workflows running smoothly, focus on real-time monitoring and automated tools that fit naturally into clinical routines. Key strategies include network segmentation, encryption, and AI-powered threat detection to spot potential risks without causing interruptions. Pay extra attention to high-risk devices by prioritizing their updates and monitoring. Additionally, use platforms designed to simplify risk assessments and compliance checks, ensuring patient safety stays intact alongside operational efficiency.
How do we keep vendor and medical device risks updated between annual reviews?
Healthcare organizations should prioritize continuous risk monitoring to stay on top of vendor and medical device risks. This involves real-time tracking of factors like vendor security, compliance status, and operational reliability. Tools such as Censinet RiskOps™ simplify this process by automating assessments, offering user-friendly dashboards, and keeping risk data accurate and up to date.
By categorizing vendors and devices based on their risk levels, organizations can focus their monitoring efforts where they’re needed most. This approach ensures they can tackle emerging threats effectively and maintain compliance without relying solely on annual reviews.


