Shared Responsibility Model: Vendor vs. HDO Roles
Post Summary
In healthcare, moving to the cloud means security responsibilities are split between cloud vendors and healthcare delivery organizations (HDOs). Vendors secure the infrastructure - like data centers and hardware - while HDOs manage their data, system configurations, and access controls. Misunderstanding these roles can lead to compliance failures, such as HIPAA violations, which often result in fines.
Key takeaways:
- Vendors: Handle physical security, hardware, and regulatory audits. They ensure infrastructure is secure but aren't responsible for customer-side misconfigurations.
- HDOs: Protect patient data by managing encryption, access controls, and compliance. They bear legal responsibility for how data is handled within their systems.
A clear division of responsibilities ensures better risk management and protects sensitive patient information. Both parties must work together to prevent security gaps, with HDOs taking extra care to configure systems correctly and monitor for vulnerabilities.
Full SANS Webcast | Decoding the Shared Responsibility Model: Securing Cloud Environments Together
1. Cloud Vendors
Cloud vendors take charge of securing the core infrastructure: physical data centers, hardware, networking, and the virtualization layer that separates customer workloads. Essentially, they manage the backbone of operations - datacenters, networking equipment, and the software that enables multiple customers to share resources securely. While the vendors maintain the "building", healthcare delivery organizations (HDOs) are responsible for securing their "rented space"[1][6].
Infrastructure Security
The responsibility for physical security lies squarely with the cloud vendor. They control access to datacenters using tools like surveillance cameras, biometric locks, and on-site security personnel. They also safeguard the physical components - servers, routers, switches, and cabling - that support cloud services. On top of this, vendors manage the hypervisor, the software that creates and isolates virtual machines, ensuring that one customer's data remains separate from another's[1][3].
When it comes to software and hardware vulnerabilities, vendors handle patching at the infrastructure level[4]. If a critical flaw is discovered, the cloud service provider (CSP) addresses it without requiring intervention from the HDO. Additionally, vendors enforce strict internal controls, limiting which of their employees can access administrative tools that oversee storage, memory, and network interfaces[2].
Compliance Management
Cloud vendors also play a key role in meeting regulatory requirements. Under HIPAA, they are considered Business Associates as soon as they store or process electronic protected health information (ePHI). The Department of Health and Human Services (HHS) clarifies this in its guidance: "Lacking an encryption key does not exempt a CSP from business associate status and obligations under the HIPAA Rules"[2]. This makes it mandatory for vendors to sign a Business Associate Agreement (BAA) before handling any ePHI.
To ensure compliance, vendors undergo regular third-party audits, such as SOC 2, ISO 27001, and ISO 27017 certifications. These audits confirm the effectiveness of their security controls. Vendors also provide audit documentation and compliance reports to help HDOs during their own evaluations. For instance, Google Cloud employs over 700 security engineers to uphold these standards[7]. However, it's important to note that while vendors ensure their systems are compliant, they are not responsible for HDO misconfigurations - a common issue that has led to significant penalties[5].
Next, we’ll explore the responsibilities and challenges faced by Healthcare Delivery Organizations.
2. Healthcare Delivery Organizations (HDOs)
Cloud vendors may handle the security of their infrastructure, but healthcare delivery organizations (HDOs) hold the legal responsibility for protecting the data and applications they manage on those platforms. Under HIPAA regulations, HDOs are accountable for ensuring proper security configurations, access controls, and data protection measures - even if patient data is stored on a vendor’s servers.
Data Protection
HDOs must take proactive steps to encrypt protected health information (PHI) both at rest and during transmission. Vendor tools can assist, but merely migrating to the cloud doesn’t guarantee security. A telling example occurred in 2026 when a small pediatric clinic moved its billing records to an AWS S3 bucket but failed to configure access restrictions or enable encryption. Although AWS provided a signed Business Associate Agreement (BAA) and secured its physical infrastructure, the clinic’s negligence led to a patient complaint, a federal investigation, and a hefty $150,000 fine.
To avoid such pitfalls, HDOs must secure operating systems, databases, and applications by applying timely patches, enforcing strict access controls, and maintaining comprehensive backup and recovery protocols. These practices form the foundation for effective compliance oversight.
Compliance Management
Conducting a detailed risk analysis is a critical requirement for HDOs to identify vulnerabilities in their cloud environments. The HIPAA Security Rule outlines specific standards, including risk analysis, risk management, and regular system activity reviews. The HHS Office for Civil Rights underscores this responsibility:
"A CSP is not responsible for the compliance failures that are attributable solely to the actions or inactions of the customer." – HHS Office for Civil Rights
HDOs must regularly monitor audit logs, such as AWS CloudTrail, to detect unauthorized access to PHI. Neglecting these responsibilities can lead to severe penalties. For instance, the Office for Civil Rights has penalized entities storing ePHI for thousands of patients on cloud servers without proper BAAs, highlighting the risks of overlooking compliance requirements.
To simplify risk management, some HDOs turn to specialized platforms. Tools like Censinet RiskOps™ allow organizations to automate risk assessments, audit log reviews, and collaborative risk management processes. These solutions help ensure compliance while safeguarding sensitive patient data.
Identity and Access Management
Effective identity and access management builds on the foundation of data protection and compliance. HDOs must enforce strict controls for user identities and accounts, incorporating measures such as unique user IDs, role-based permissions, and lifecycle management. As stated by HHS.gov:
"Where only the customer controls who is able to view the ePHI maintained by the CSP, certain access controls, such as authentication or unique user identification, may be the responsibility of the customer." – HHS.gov
Multi-factor authentication (MFA) is essential for all administrative and high-privilege accounts. Even when using "no-view" services, HDOs must enforce rigorous authentication protocols to protect encrypted data.
sbb-itb-535baee
Pros and Cons
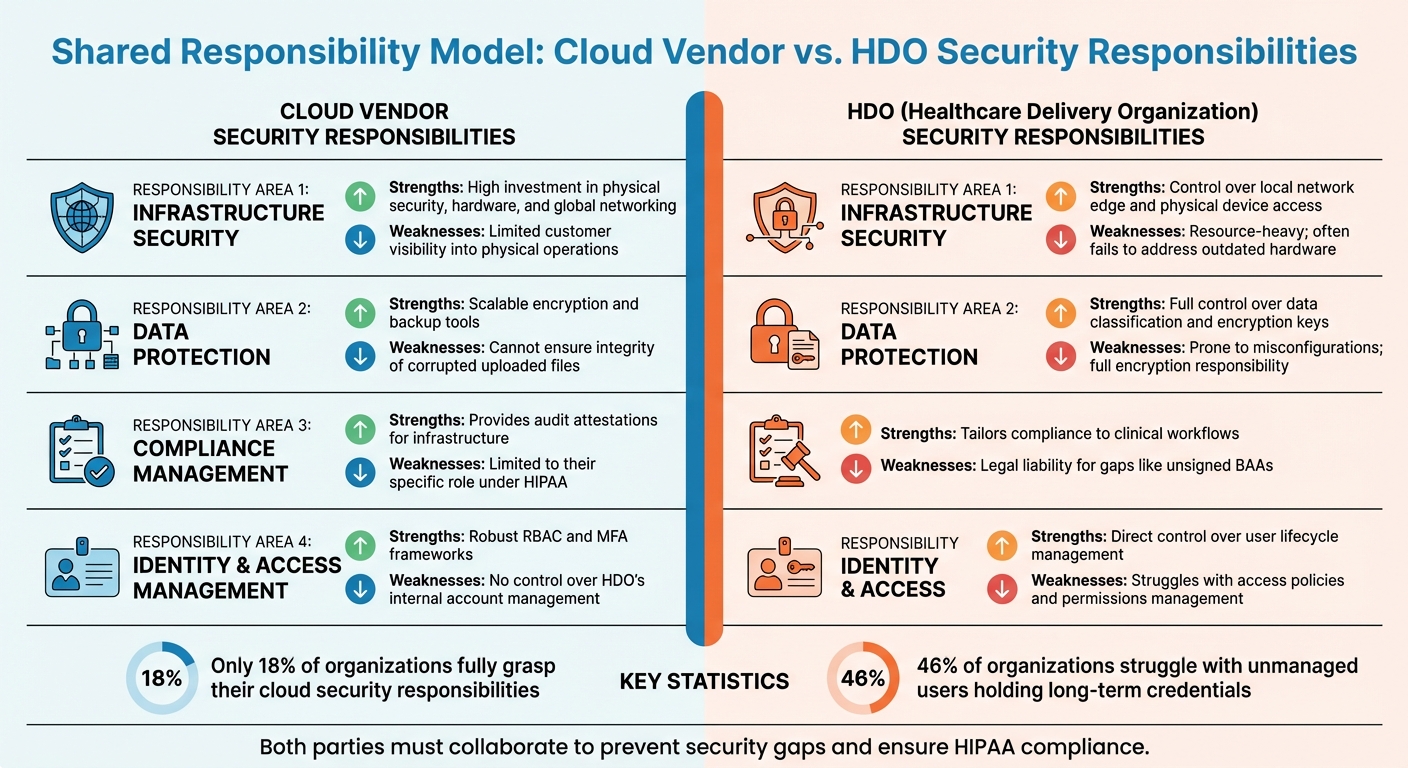
Cloud Vendor vs HDO Security Responsibilities in Healthcare
This section dives into the pros and cons of the roles defined by the shared responsibility model, focusing on how cloud vendors and healthcare delivery organizations (HDOs) contribute to security across four key domains. By clearly outlining responsibilities, this model helps healthcare organizations identify security gaps and make smarter investments. Let’s break down where each party excels and where challenges arise.
Cloud vendors shine in infrastructure security, thanks to their extensive investments in physical infrastructure. On the other hand, HDOs handle guest operating systems and applications but don’t have direct control over the physical components - adding complexity to their role.
For data protection, cloud vendors offer scalable encryption tools and storage solutions while operating on a "no-view" basis. However, HDOs are tasked with making critical encryption decisions, managing data classification, and ensuring governance. This often leads to issues like misconfigurations, which can have serious consequences.
When it comes to compliance management, vendors provide audit attestations (e.g., SOC 2 and HITRUST reports), which help meet regulatory requirements. But HDOs bear the brunt of compliance responsibility, including implementing Complementary User Entity Controls (CUECs) and ensuring legal compliance. For instance, failing to secure a signed Business Associate Agreement (BAA) can expose them to liability. Alarmingly, only 18% of organizations fully grasp their cloud security responsibilities.
Identity and access management highlights another stark contrast. Cloud vendors provide strong frameworks like role-based access control (RBAC) and multi-factor authentication (MFA). However, they don’t oversee how HDOs manage internal user accounts. This gap is significant - nearly 46% of organizations struggle with unmanaged users holding long-term credentials, and many cloud breaches stem from HDO misconfigurations.
Here’s a quick comparison of strengths and weaknesses across these responsibility areas:
| Responsibility Area | Cloud Vendor Strengths | Cloud Vendor Weaknesses | HDO Strengths | HDO Weaknesses |
|---|---|---|---|---|
| Infrastructure Security | High investment in physical security, hardware, and global networking | Limited customer visibility into physical operations | Control over local network edge and physical device access | Resource-heavy; often fails to address outdated hardware |
| Data Protection | Scalable encryption and backup tools | Cannot ensure integrity of corrupted uploaded files | Full control over data classification and encryption keys | Prone to misconfigurations; full encryption responsibility |
| Compliance Management | Provides audit attestations for infrastructure | Limited to their specific role under HIPAA | Tailors compliance to clinical workflows | Legal liability for gaps like unsigned BAAs |
| Identity & Access Management | Robust RBAC and MFA frameworks | No control over HDO’s internal account management | Direct control over user lifecycle management | Struggles with access policies and permissions management |
This comparison underscores the need for HDOs to strengthen their internal controls to complement vendor-provided security measures. To address these challenges, many organizations are adopting cybersecurity and risk management platforms, such as Censinet RiskOps™, which simplify risk assessments and enable continuous monitoring.
Conclusion
In the shared responsibility model, defining roles with precision is key to maintaining secure cloud operations in healthcare. This model clearly outlines responsibilities: cloud vendors handle the infrastructure - such as data centers, hardware, and networking - while healthcare delivery organizations (HDOs) are tasked with securing their systems, applications, and data.
Collaboration between these parties is critical to avoid security gaps. While a signed Business Associate Agreement (BAA) clarifies roles, it doesn’t transfer compliance obligations. As the U.S. Department of Health and Human Services (HHS) has stated, “A CSP is not responsible for the compliance failures that are attributable solely to the actions or inactions of the customer” [2]. This emphasizes that HDOs remain accountable for issues like misconfigurations, weak access controls, or breaches caused by their own security lapses.
The consequences of noncompliance can be severe, with significant penalties highlighting the importance of adhering to clearly defined roles. To mitigate risks, both vendors and HDOs must conduct comprehensive risk assessments and document their responsibilities in detail.
HDOs play a crucial role in configuring security settings, enabling encryption, enforcing multi-factor authentication, and managing audit logs. While vendors provide the tools, it’s up to HDOs to implement and manage them effectively. Platforms like Censinet RiskOps™ can simplify this process by supporting risk assessments and continuous monitoring across vendor relationships.
This discussion underscores the importance of infrastructure, data protection, compliance, and identity management as pillars of a strong security strategy. By routinely evaluating risks and fine-tuning their controls, HDOs can leverage vendor capabilities to enhance patient data security. Protecting sensitive information requires a clear understanding of the shared responsibility model. When vendors secure the foundation and HDOs manage their layers effectively, healthcare organizations can confidently embrace cloud technologies while safeguarding patient data.
FAQs
What responsibilities do cloud vendors have in the shared responsibility model for healthcare organizations?
In the shared responsibility model, cloud vendors take charge of securing the foundational infrastructure that powers cloud services. This includes safeguarding hardware, physical data centers, network controls, and virtualization layers.
Meanwhile, healthcare delivery organizations (HDOs) handle the security and management of their own data, applications, user access, and configurations within the vendor's infrastructure. This setup ensures both parties collaborate to protect sensitive information, such as patient data and PHI (protected health information).
What steps can healthcare organizations take to prevent compliance issues when using cloud services?
To avoid compliance issues with cloud services, healthcare delivery organizations (HDOs) need a clear grasp of their responsibilities under the shared responsibility model. This means regularly assessing the risks associated with cloud providers, ensuring security settings are properly configured, and maintaining control over sensitive data like Protected Health Information (PHI). Additionally, signing Business Associate Agreements (BAAs) with cloud vendors is crucial. These agreements clearly define each party's role in protecting electronic PHI and ensuring compliance with HIPAA regulations.
Some key steps HDOs can take include encrypting data both when it's stored and while it's being transmitted, enforcing role-based access controls to limit access to sensitive information, and continuously monitoring cloud environments for any misconfigurations or vulnerabilities. Tools like Censinet RiskOps™ can make these tasks more manageable by offering streamlined assessment processes and better visibility into potential risks, enabling HDOs to protect patient data and remain compliant with ease.
Why is it crucial for healthcare organizations to manage their own cloud security settings?
Healthcare delivery organizations (HDOs) play a critical role in protecting sensitive patient data when using cloud services. While cloud providers supply the infrastructure and some security features, it's up to HDOs to configure and manage their own security controls under the shared responsibility model.
Neglecting these responsibilities can result in serious risks, like misconfigured systems or unauthorized access, potentially exposing protected health information (PHI) and other vital data. By clearly understanding their obligations within this model, HDOs can take proactive steps to minimize risks and strengthen their overall security defenses.
Related Blog Posts
- “Inside the HIPAA Wall of Shame: Trends, Lessons, and a Path Forward”
- Patient Safety and Vendor Risk: The Hidden Threats Healthcare Organizations Must Address
- The Hidden Cost of Cloud Dependency: What the AWS Outage Means for HIPAA Compliance
- Cloud Vendor Risk Management for Healthcare: Security, Compliance, and Continuity


