SOC 2 Audit Prep: Vendor Risk Management Tools
Post Summary
SOC 2 audit preparation involves ensuring that healthcare organizations meet security, availability, and confidentiality standards for managing patient data.
These tools streamline compliance, monitor vendor risks, and ensure patient data is protected, making audits more efficient.
Automated risk assessments, compliance tracking, real-time monitoring, and centralized documentation.
They automate workflows, track compliance, and provide detailed reports to meet audit requirements.
Challenges include managing large vendor networks, ensuring compliance, and maintaining accurate documentation.
Censinet RiskOps™ automates compliance checks, monitors vendor risks, and provides real-time insights to streamline audit preparation.
SOC 2 compliance is critical for healthcare organizations to protect sensitive data and manage vendor risks effectively. Here's what you need to know:
- SOC 2 Basics: Focuses on five trust criteria - security, availability, processing integrity, confidentiality, and privacy.
- Common Challenges: Managing multiple vendors, maintaining documentation, continuous monitoring, and coordinating risk assessments.
- Vendor Risk Management: Tools like Censinet help automate risk assessments, protect patient data, and ensure compliance.
- Key Steps:
- Categorize vendors by access, risk, and compliance.
- Conduct detailed risk analysis (security controls, documentation, testing).
- Monitor vendors continuously with real-time alerts and response plans.
- Technology Solutions:
- Automate risk assessments and compliance tracking.
- Use centralized platforms for vendor data and audit documentation.
Start by defining clear SOC 2 goals, training your team, and implementing the right tools to simplify audits and enhance security.
SOC 2 Academy: Managing Vendor Risk
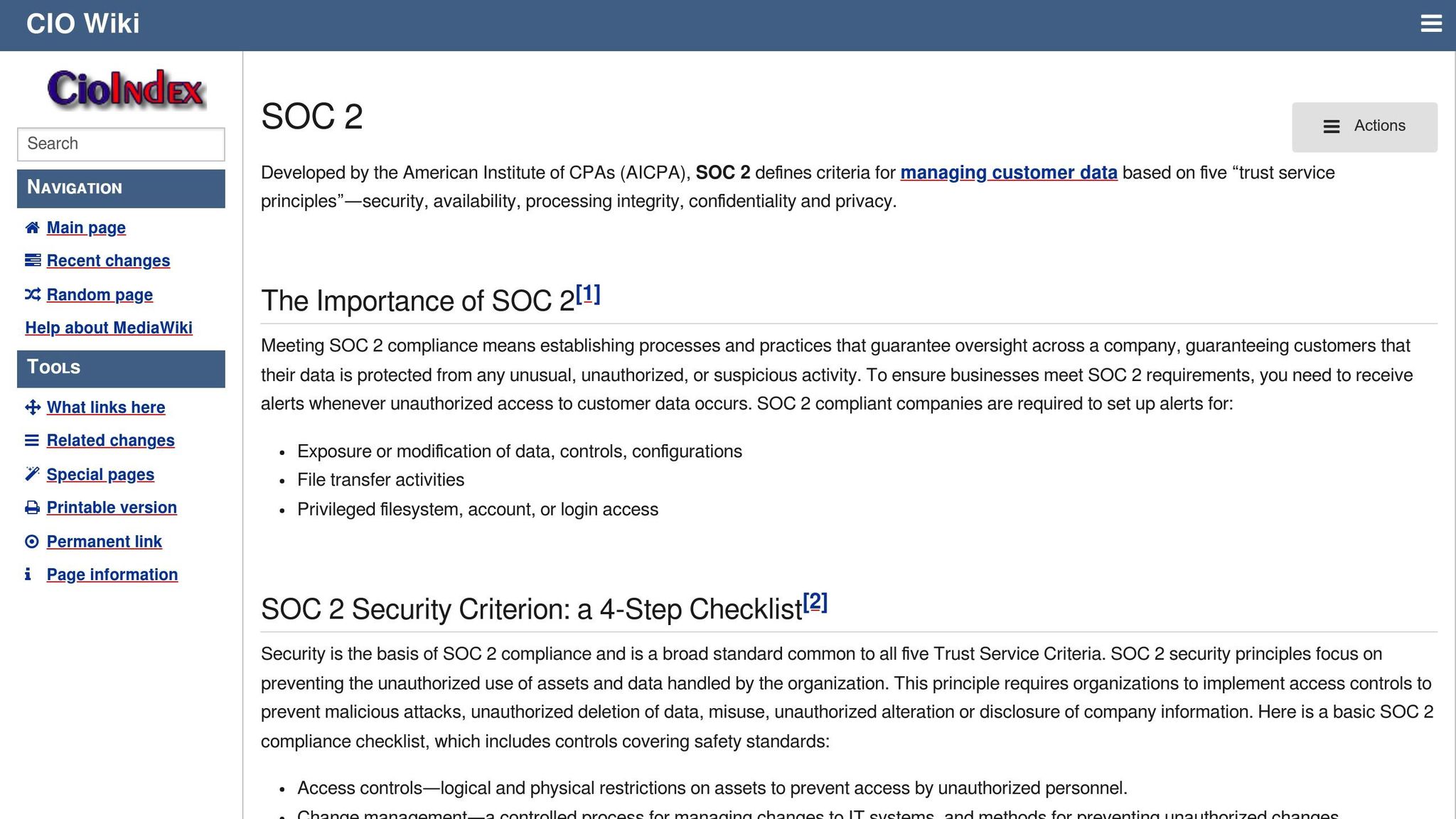
Key Components of Vendor Risk Management
Healthcare organizations must have strong vendor risk management systems to align with SOC 2 requirements. These systems create a structured compliance framework, laying the groundwork for effective vendor oversight.
Vendor Tracking and Categories
Managing vendors starts with categorizing and tracking third-party vendors based on:
- Access Level: Prioritize oversight for vendors with access to PHI.
- Risk Impact: Evaluate potential harm from security breaches.
- Integration Depth: Assess how vendor systems connect to internal networks.
- Compliance Status: Monitor vendor security certifications.
Erik Decker, CISO at Intermountain Health, highlights the value of detailed tracking:
"Censinet portfolio risk management and peer benchmarking capabilities provide additional insight into our organization's cybersecurity investments, resources, and overall program" [1].
After categorizing vendors, thorough risk analysis ensures every risk factor is closely examined.
Risk Analysis and Verification
Building on vendor categorization, a detailed risk analysis examines vendor security practices against SOC 2 standards. This involves:
- Security Control Assessment: Review the vendor’s security measures.
- Documentation Review: Analyze their policies and procedures.
- Compliance Verification: Ensure they meet regulatory requirements.
- Technical Testing: Test the effectiveness of their security measures.
This method provides a well-rounded view of risks while keeping the process efficient.
Vendor Monitoring and Response Plans
Ongoing monitoring is essential for maintaining compliance and addressing threats quickly. Key elements include:
- Real-time Security Alerts: Immediate notifications of incidents.
- Performance Tracking: Regular checks on vendor compliance.
- Incident Response Protocols: Clear procedures for handling breaches.
- Communication Channels: Efficient coordination with vendors.
Modern risk management tools can simplify these tasks while upholding high security standards. By integrating these components, healthcare organizations can better prepare for SOC 2 audits, safeguard patient data, and maintain smooth operations.
sbb-itb-535baee
Using Technology for Vendor Risk Management
Healthcare organizations today rely on digital platforms to simplify SOC 2 compliance and vendor risk management. These tools replace manual processes with automation, improving accuracy while reducing administrative workloads.
Digital Risk Assessment Tools
Modern risk assessment platforms streamline vendor evaluations by automating key processes. With these tools, organizations can:
- Speed up vendor evaluations
- Use consistent assessment criteria
- Monitor compliance requirements effectively
- Automatically generate detailed risk reports
Risk Data Management System
A centralized risk data platform acts as a single source of truth for compliance and security information. By consolidating vendor data, healthcare organizations can maintain better oversight of their vendors and simplify SOC 2 audit preparation.
Key benefits of a robust risk data management system include:
- Real-time updates on vendor compliance
- Automated risk scoring and prioritization
- Centralized storage for documents with version control
- Built-in communication tools for vendor coordination
Audit Documentation Tools
Digital platforms make audit documentation more efficient by automating the collection and organization of evidence needed for SOC 2 audits. These tools ensure detailed audit trails and complete documentation through structured workflows.
Features of modern audit documentation tools include:
- Automated collection and organization of evidence
- Tools for tracking compliance requirements
- Real-time monitoring of documentation progress
- Pre-designed templates for standardized reporting
These solutions not only simplify audits but also set the stage for adopting more comprehensive risk management software.
Implementing Risk Management Software
Setting Risk Management Goals
To effectively implement vendor risk management software, start by defining clear and measurable SOC 2 objectives. Focus on areas like security, availability, confidentiality, processing integrity, and privacy.
Some practical goals to consider:
- Automating risk scoring to simplify vendor evaluations
- Ensuring real-time insights into vendor security practices
Staff Training and System Setup
Proper adoption of risk management tools requires both staff training and seamless system integration. Healthcare organizations must ensure that their teams understand the software's technical features and compliance requirements. Training should include:
- Navigating the software and understanding its functions
- Conducting risk assessments and maintaining proper documentation
- Meeting compliance standards and generating necessary reports
- Linking the software with existing healthcare systems
Once training is in place, keep an eye on progress to ensure the system aligns with changing compliance demands.
Progress Tracking and Updates
Regular monitoring is essential to ensure your risk management software supports SOC 2 compliance effectively. Set up review schedules and define performance metrics to track improvements. For example, healthcare organizations can measure:
- Monthly completion rates for vendor assessments
- Timelines for addressing identified risks
- Staff adoption rates and improvements in efficiency
Next Steps for SOC 2 Audit Preparation
After setting up your vendor risk management framework, it’s time to focus on getting ready for the SOC 2 audit. Healthcare organizations can leverage modern tools to simplify the process while keeping security measures intact.
Experts highlight that automation plays a big role in making risk management more efficient and improving audit readiness. Here are the key areas to prioritize for SOC 2 preparation:
- Speed up risk assessments: Use tools designed to quickly and accurately evaluate vendors. These platforms allow organizations to expand their assessment efforts without needing to hire more staff.
- Improve program visibility: Comprehensive portfolio management and benchmarking tools offer clear insights into cybersecurity investments and how resources are being allocated.
-
Expand risk coverage in critical areas:
- Protecting patient data
- Securing medical devices
- Ensuring compliance with research and IRB standards
- Managing risks in the supply chain
Related Blog Posts
Key Points:
What is SOC 2 audit preparation in healthcare?
SOC 2 audit preparation ensures that healthcare organizations meet the security, availability, and confidentiality standards required to manage patient data securely. It involves assessing risks, monitoring compliance, and documenting processes.
Why are vendor risk management tools important for SOC 2 audits?
Vendor risk management tools are critical for:
- Streamlining Compliance: Ensures vendors meet SOC 2 requirements.
- Protecting Patient Data: Safeguards sensitive information from breaches.
- Improving Efficiency: Automates workflows and reduces manual effort.
- Providing Audit-Ready Documentation: Centralizes records for easy access during audits.
What features should vendor risk management tools include for SOC 2 audits?
Essential features include:
- Automated Risk Assessments: Evaluates vendor risks efficiently.
- Compliance Tracking: Monitors adherence to SOC 2 standards.
- Real-Time Monitoring: Identifies risks and vulnerabilities as they arise.
- Centralized Documentation: Stores vendor contracts, certifications, and compliance records.
- Advanced Reporting: Generates audit-ready reports for SOC 2 requirements.
How do vendor risk tools improve SOC 2 audit preparation?
Vendor risk tools improve audit preparation by:
- Automating Workflows: Reduces manual effort and ensures consistency.
- Tracking Compliance: Monitors vendor adherence to SOC 2 standards.
- Providing Real-Time Insights: Identifies risks and vulnerabilities proactively.
- Generating Reports: Creates detailed documentation for auditors.
What challenges do healthcare organizations face during SOC 2 audits?
Common challenges include:
- Managing Large Vendor Networks: Evaluating risks across numerous vendors.
- Ensuring Compliance: Keeping up with evolving SOC 2 requirements.
- Maintaining Accurate Documentation: Organizing and updating vendor records.
- Resource Constraints: Limited staff and budgets for audit preparation.
How can tools like Censinet RiskOps™ support SOC 2 audit preparation?
Censinet RiskOps™ supports SOC 2 audit preparation by:
- Automating Compliance Checks: Ensures vendors meet SOC 2 standards.
- Monitoring Vendor Risks: Tracks risks in real time to prevent issues.
- Providing Centralized Documentation: Stores all necessary records for audits.
- Enhancing Collaboration: Facilitates communication between teams and vendors.


