5 Steps for Third-Party Cloud Audit Coordination
Post Summary
A third-party cloud audit is an independent assessment of a cloud environment to ensure compliance with security, performance, and regulatory standards like HIPAA and GDPR.
They ensure patient data security, regulatory compliance, and vendor accountability while identifying vulnerabilities and mitigating risks.
Steps include defining the audit scope, assembling a multidisciplinary team, gathering documentation, conducting risk assessments, and reviewing controls.
Challenges include managing vendor cooperation, addressing shared responsibility gaps, and ensuring access to necessary data and configurations.
Best practices include automating compliance monitoring, maintaining clear documentation, and leveraging frameworks like CSA CCMv4.0 for standardized audits.
Organizations can streamline audits by using tools like Censinet RiskOps™, automating evidence collection, and ensuring clear vendor contracts with compliance clauses.
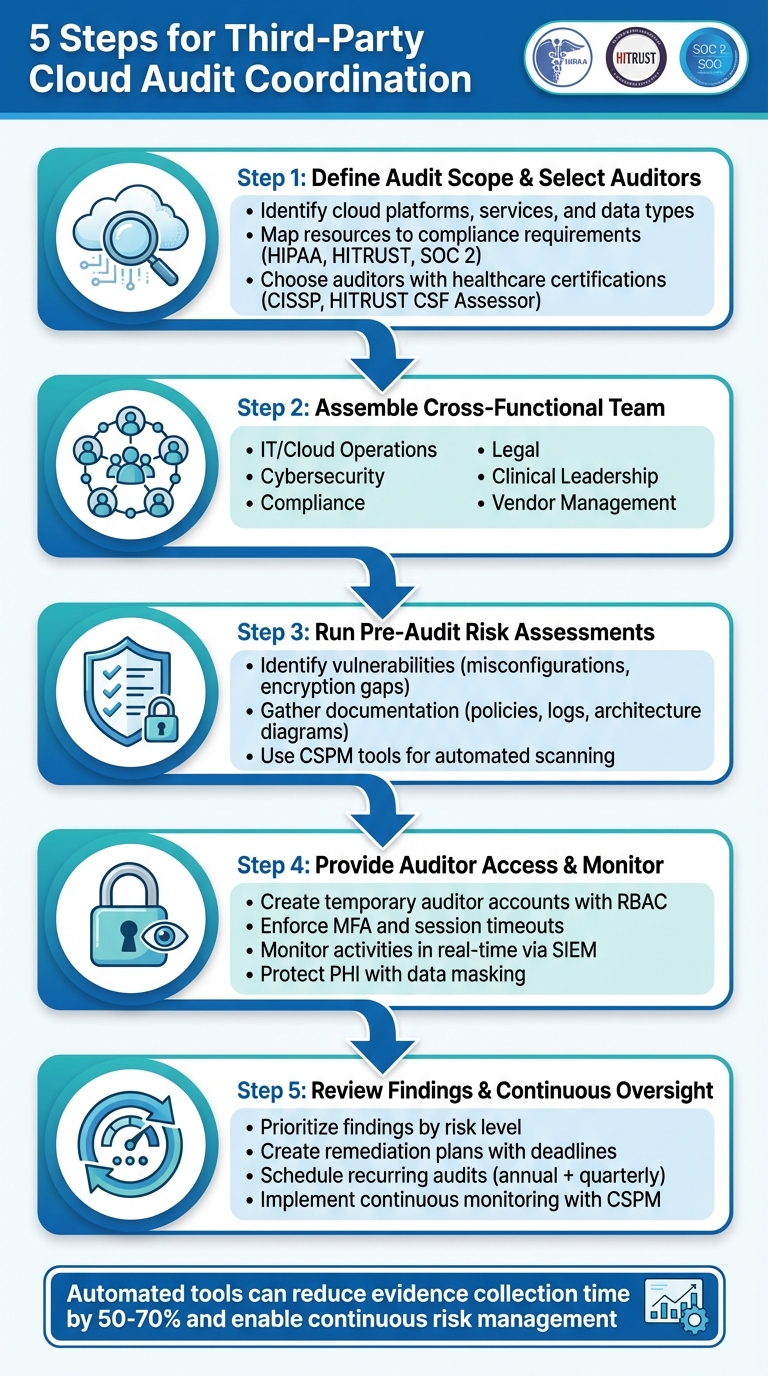
Healthcare organizations must ensure their cloud systems meet compliance standards like HIPAA, HITRUST, and SOC 2. Properly managing third-party cloud audits can uncover risks, improve security, and ensure patient data is protected. Here's how to streamline the process in five steps:
- Define the Audit Scope: Identify cloud platforms, services, and data types to focus on. Map resources to compliance requirements like HIPAA or HITRUST.
- Select Qualified Auditors: Choose auditors experienced in healthcare cloud environments with certifications like CISSP or HITRUST CSF Assessor.
- Assemble a Cross-Functional Team: Include representatives from IT, compliance, legal, clinical operations, and vendor management, assigning clear roles.
- Prepare with Risk Assessments: Identify vulnerabilities like misconfigured security settings and gather necessary documentation.
- Plan for Continuous Oversight: Address findings, implement regular audits, and use tools for real-time monitoring and ongoing risk management.
Automated tools like Censinet RiskOps™ simplify audit coordination, reduce manual effort, and enhance collaboration across teams.
5 Steps for Third-Party Cloud Audit Coordination in Healthcare
Step 1: Set Audit Scope and Choose Qualified Auditors
The first step in organizing a third-party cloud audit is establishing a clear scope. Without precise boundaries, resources can be wasted, and critical vulnerabilities might be missed. Healthcare organizations must define which cloud platforms, services, accounts, and data types fall within the audit's focus - and just as importantly, which do not.
The shared responsibility model adds another layer of complexity. While cloud providers like AWS, Azure, or Google Cloud handle the security of their infrastructure, your organization is responsible for configurations, access controls, data, and workloads. If the scope isn’t clearly defined, auditors may spend time on areas outside your control while overlooking risks that are your responsibility.
To ensure a focused audit, start by mapping your cloud assets and compliance obligations.
Map Cloud Resources and Compliance Requirements
Begin by cataloging all cloud resources that handle patient data. This includes production and non-production environments, disaster recovery systems, and third-party tools like electronic health records (EHRs), picture archiving and communication systems (PACS), and patient portals. Clearly document which cloud providers and accounts fall within the audit’s scope. For example, this might include three AWS accounts hosting your EHR, an Azure subscription for analytics, and a SaaS telehealth platform.
Once you've inventoried your resources, align them with your compliance needs. For example, if your organization must meet HIPAA requirements, identify how each cloud service supports HIPAA Security Rule safeguards like access controls, audit trails, and encryption. For HITRUST certification, map your cloud infrastructure to the relevant Common Security Framework (CSF) controls. Tools like Cloud Security Posture Management (CSPM) platforms can simplify this process by scanning for misconfigurations and comparing your setup against compliance standards.
Platforms such as Censinet RiskOps™ can further streamline the process of inventorying resources and mapping compliance needs.
With your resources documented and compliance requirements mapped, the next step is to select auditors who truly understand the unique challenges of healthcare cloud environments.
How to Select the Right Auditors
When choosing auditors, prioritize those with extensive experience in healthcare cloud environments. Look for professionals who understand how patient data flows through cloud systems and are familiar with HIPAA’s technical safeguards. Certifications like HITRUST CSF Assessor, CISA, CISSP, CCSP, and ISO 27001 Lead Auditor are key indicators of expertise. Additionally, ask for references from healthcare-specific audits and review case studies to confirm their familiarity with your cloud platforms.
Create a detailed RFP (Request for Proposal) that outlines the audit’s objectives, scope, timeline, and deliverables, such as risk assessments and remediation plans. Specify evaluation criteria, including healthcare experience, certifications, pricing, and client references. Ask for demonstrations of their audit tools and methodologies, particularly CSPM platforms or API-based evidence collection methods. Choose a team that not only understands the shared responsibility model but also has a clear process for tracking and addressing remediation efforts.
Matt Christensen, Sr. Director of GRC at Intermountain Health, notes: "Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare."
This insight applies equally to auditors - general cloud expertise isn’t enough. You need professionals with a deep understanding of healthcare's unique requirements.
Step 2: Create a Cross-Functional Audit Team
To run an effective third-party cloud audit, you need more than just one department's input. Healthcare cloud environments touch multiple areas, including IT, compliance, legal, and clinical operations. That’s why it’s essential to form a team with representatives from IT/cloud operations, cybersecurity, compliance, legal, internal audit, clinical leadership, and vendor management. Each member brings unique expertise to the table.
For instance, your IT team understands the technical setup and can pull system logs. The security team evaluates potential threats and designs controls. Compliance staff connect regulatory requirements, like HIPAA, to the necessary controls. Legal counsel reviews business associate agreements and interprets regulatory obligations. Clinical leaders ensure that security measures don’t interfere with patient care. Meanwhile, the vendor management team works with third-party providers to gather evidence, such as SOC 2 reports and HITRUST certifications. This diverse collaboration ensures every aspect of the audit is covered, with clearly defined roles for a smoother process.
Assign Team Roles and Responsibilities
Once your team is in place, assigning clear roles is crucial to avoid confusion and missed tasks. A RACI matrix (Responsible, Accountable, Consulted, Informed) can help identify who handles what. For example, your IT team might be Responsible for gathering configuration evidence, while your Chief Information Security Officer (CISO) is Accountable for the audit's overall success. Compliance officers are often Consulted on risk-related decisions, and executive leaders are Informed through regular updates. This structure ensures every team member’s expertise is used effectively.
Use Technology to Improve Team Collaboration
When your team spans multiple departments - and vendors operate outside your organization - keeping everyone on the same page can be a challenge. Tools like Censinet Connect™ simplify the process by allowing vendors to share completed security questionnaires and supporting documents directly with your team, speeding up evidence collection [1]. A centralized platform keeps all audit documentation in one place, reducing miscommunication and redundant work.
James Case, VP & CISO at Baptist Health, shared his experience: "We eliminated spreadsheets and streamlined vendor collaboration." [1]
With everyone - from compliance officers to vendor risk managers - accessing the same real-time data, it’s easier to track progress and stay aligned. For managing audit findings, Censinet RiskOps™ helps assign tasks, set deadlines, and monitor remediation plans across the team [1]. This streamlined approach ensures your cross-functional team works efficiently and stays focused on the audit’s goals.
Step 3: Run Pre-Audit Risk Assessments and Gather Documentation
Preparing for an audit means tackling vulnerabilities and organizing the necessary evidence ahead of time. This step involves two key actions: evaluating your cloud environment for security gaps and gathering the documentation auditors will expect. Taking care of these tasks early can save you from last-minute stress and help resolve issues before they become audit findings.
Assess Cloud System Risks
Start by conducting a thorough risk assessment to identify common misconfigurations, such as issues with encryption, network security groups, storage permissions, logging, backups, and patching. Tools like Cloud Security Posture Management (CSPM) can simplify this process by scanning your environment for problems like overly permissive security groups, unencrypted databases, publicly accessible storage buckets, or disabled logging [2][3].
For access controls, ensure all critical actions - like authentication, data access, configuration changes, and administrative tasks - are logged centrally. Double-check that your log retention policies align with HIPAA requirements and your internal standards [4]. Don’t overlook third-party integrations, as these external connections can introduce vulnerabilities.
If you’re in the healthcare sector, platforms like Censinet RiskOps™ can provide tailored insights by evaluating your cybersecurity program against industry benchmarks. This approach helps pinpoint security gaps before auditors identify them [1]. Once vulnerabilities are identified, start collecting the evidence that corresponds to them without delay.
Collect Required Documentation Efficiently
Auditors typically request a standard set of evidence, which includes network and architecture diagrams (covering VPCs, subnets, firewalls, security groups, and data flows), security policies and procedures, incident response plans, configuration baselines, change-control records, logging configurations, and sample logs [2][3][4]. If your documentation is scattered across emails, local drives, and shared folders, manual collection can be time-consuming and prone to errors.
Automation tools can make this process far more efficient. Solutions like Censinet RiskOps™ and Censinet Connect™ allow vendors to share completed security questionnaires and supporting documents directly with your team [1]. Meanwhile, Censinet AITM enables vendors to fill out security questionnaires quickly, automatically generating evidence summaries and risk reports [1].
The time savings are substantial. For example, Terry Grogan, CISO at Tower Health, shared:
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required" [1].
sbb-itb-535baee
Step 4: Provide Auditor Access and Monitor Activities
Once your documentation is ready, the next step is to grant auditors controlled access to your cloud environment. This requires striking a balance: auditors need enough access to perform their tasks, but sensitive patient data and PHI must remain protected. The solution lies in implementing secure access protocols and keeping a close watch on all auditor activities.
Set Up Secure Access for Auditors
To stay aligned with HIPAA compliance, it's crucial to limit unnecessary exposure to PHI. Instead of sharing existing credentials, create temporary auditor accounts specifically for this purpose. Use role-based access control (RBAC) to ensure auditors only have permissions they absolutely need - typically limited to read-only access for logs, configurations, and documentation. If access to production PHI is unavoidable, make sure the data is masked or de-identified.
For cloud platforms like AWS, Azure, or GCP, enforce multi-factor authentication (MFA) and set strict session timeouts. Document every access request, including the auditor's name, the reason for access, the resources required, and security team approvals. This creates a clear, auditable trail that demonstrates compliance with HIPAA regulations.
Tools like Censinet RiskOps™ can simplify this process. It provides a secure platform for sharing cybersecurity and risk information with third parties while keeping sensitive systems out of direct reach [1].
Monitor Audit Activities in Real-Time
Granting access is just the first step - real-time monitoring is equally critical to identify and manage potential risks. Use your SIEM system to log every auditor action, from authentication attempts to data queries, configuration views, and file downloads. Centralize logs from all key services to get a clear, consolidated view of auditor behavior [4]. Set up automated alerts for suspicious activities like failed logins, attempts to access restricted resources, or unusual data transfers.
Cloud Security Posture Management (CSPM) tools can also play a valuable role during audits. They automatically identify misconfigurations, such as open containers, and suggest immediate fixes [2]. This kind of automated monitoring reduces manual effort while ensuring compliance remains intact [2][4].
Dashboards are another useful tool, allowing you to track audit progress in real time. Platforms like Censinet RiskOps™ provide centralized oversight of auditor actions and risk data, helping teams stay on top of workflows and quickly address any issues [1]. This integrated approach not only supports immediate decision-making but also strengthens long-term compliance efforts.
Step 5: Review Findings and Plan for Continuous Oversight
Once you've received the audit report detailing findings and compliance gaps, the next step is to turn these insights into a proactive approach to managing risks. This ensures that your audit isn't just a one-time event but becomes part of an ongoing risk management strategy.
Prioritize and Address Audit Findings
Start by assessing the risk level of each finding based on its potential impact on patient safety, the exposure of Protected Health Information (PHI), and operational continuity. Issues like exposed storage buckets, weak access controls, or unpatched vulnerabilities should be addressed immediately as high-priority risks [2][3]. To organize this process, create a risk register that assigns specific ownership and deadlines to each issue [3].
Your remediation plan should be detailed and actionable. For instance, if the audit highlights misconfigured cloud permissions, your plan might involve tightening Role-Based Access Control (RBAC) policies, conducting targeted staff training, and scheduling follow-up checks to ensure the issue is resolved. Document each step thoroughly, and provide regular updates to leadership and regulators to maintain transparency.
Tools like Censinet RiskOps™ can simplify this process by centralizing vendor risk data and automating third-party risk assessments. This platform offers a unified view of risks across PHI, clinical applications, medical devices, and supply chain services [1]. By streamlining these tasks, your team can focus more on resolving issues and less on managing complex spreadsheets.
Establish Recurring Audits and Continuous Monitoring
After addressing the audit findings, it's essential to set up a system for ongoing oversight. Schedule regular audits - such as annual comprehensive reviews complemented by quarterly or monthly spot-checks for high-risk areas - to ensure consistent security [3]. Pair these efforts with continuous monitoring using tools like Cloud Security Posture Management (CSPM), which can detect misconfigurations and policy violations in real time [2][3][4].
To ensure security becomes an integral part of your operations, embed audit processes directly into your DevSecOps and cloud workflows. This allows configuration and security checks to occur automatically as systems evolve [2][4]. Transitioning from periodic reviews to continuous oversight helps identify and resolve issues before they escalate into compliance violations. Platforms like Censinet RiskOps™ use AI to enable proactive risk management, reducing the need for reactive, manual processes [1].
Brian Sterud, CIO at Faith Regional Health, emphasized: "Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters" [1].
Incorporate audit findings into your ongoing improvement efforts by updating policies, refining controls, and verifying changes [5]. This creates a feedback loop where each audit not only strengthens your security framework but also better prepares you for the next review.
Conclusion
Coordinating third-party cloud audits demands a well-organized approach. By breaking the process into five clear steps - defining the scope and choosing auditors, assembling a cross-functional team, conducting pre-audit risk assessments, managing auditor access, and ensuring continuous oversight - healthcare organizations can turn audits into a manageable, repeatable process. This approach not only fulfills compliance requirements but also improves overall efficiency while safeguarding patient safety.
A structured method makes cloud compliance more manageable. Instead of scrambling to gather evidence manually before every audit, organizations can achieve ongoing readiness through continuous monitoring. This is especially critical in healthcare, where cloud systems directly impact clinical operations, the security of protected health information (PHI), and patient care. Industry guidelines increasingly recommend annual security audits combined with continuous monitoring to quickly identify and address any misconfigurations.
Censinet RiskOps™ is designed to support this process by automating third-party risk assessments, enabling cross-functional collaboration, and maintaining continuous oversight across vendors, medical devices, and supply chain services [1]. By streamlining these tasks, Censinet RiskOps™ allows healthcare organizations to allocate resources to more strategic priorities while ensuring a smooth audit process.
Adopting an integrated audit strategy shifts the focus from one-off audits to ongoing risk management. This proactive approach helps healthcare organizations detect and resolve potential issues before they escalate into compliance breaches or security threats. Automated tools like Censinet RiskOps™ can reduce evidence collection time by 50–70%, minimizing manual errors and allowing teams to focus on reducing risks strategically [2]. When audit processes are embedded into DevSecOps and cloud workflows, security checks happen automatically as systems evolve, reinforcing the principles of continuous monitoring and risk management outlined in the five-step framework.
FAQs
How can I make sure my cloud audit meets HIPAA and HITRUST requirements?
To ensure your cloud audit meets HIPAA and HITRUST requirements, begin by setting up well-defined controls that focus on critical areas such as data privacy, security, and breach response. Regularly perform risk assessments that are specifically tailored to the unique needs of the healthcare industry, and make sure your policies stay up-to-date with any regulatory changes.
Keep detailed documentation of your audit procedures and put safeguards in place to protect Protected Health Information (PHI) and other sensitive patient data. Leveraging tools designed for healthcare risk management can simplify compliance efforts and help you stay aligned with HIPAA and HITRUST standards.
What should I consider when choosing a healthcare cloud auditor?
When choosing a healthcare cloud auditor, focus on those with certifications in healthcare cybersecurity and compliance, like HITRUST. It's equally important to select auditors who have practical experience with healthcare cloud systems, clinical applications, and managing protected health information (PHI). Make sure they are knowledgeable about industry standards and have demonstrated success in performing risk assessments and addressing compliance challenges specific to the healthcare sector.
What are the benefits of continuous monitoring for cloud audits?
Continuous monitoring enhances the cloud audit process by providing real-time insights into compliance and spotting potential risks early on. This approach allows healthcare organizations to stay aligned with regulations, protect sensitive patient data, and cut down on manual workloads.
By quickly addressing vulnerabilities, continuous monitoring helps streamline audits, reduce interruptions, and bolster risk management across healthcare cloud systems.
Related Blog Posts
Key Points:
What is a third-party cloud audit?
- Definition: A third-party cloud audit is an independent evaluation of a cloud environment conducted by external auditors to assess compliance with security, performance, and regulatory standards. These audits verify that cloud service providers and their clients adhere to frameworks like HIPAA, GDPR, and SOC 2.
- Purpose: To ensure data security, regulatory compliance, and vendor accountability while identifying vulnerabilities and risks.
Why are third-party cloud audits important in healthcare?
Importance:
- Protects sensitive patient data, including ePHI, from breaches and unauthorized access.
- Ensures compliance with healthcare regulations like HIPAA, GDPR, and HITECH.
- Holds vendors accountable for maintaining secure cloud environments.
- Identifies vulnerabilities and provides actionable recommendations to mitigate risks.
What are the key steps in coordinating a third-party cloud audit?
Steps:
- Define the Audit Scope: Identify the cloud resources, services, and data to be audited, and align them with applicable regulations and standards.
- Assemble a Multidisciplinary Team: Include IT, security, legal, and compliance experts to oversee the audit process.
- Gather Documentation: Collect cloud service agreements, security policies, access controls, and previous audit findings.
- Conduct Risk Assessments: Evaluate risks related to data storage, access controls, and third-party integrations.
- Review Controls and Configurations: Audit IAM, encryption, network security, and backup procedures.
- Test Compliance Measures: Perform penetration tests, vulnerability scans, and disaster recovery drills.
- Document Findings: Record strengths, weaknesses, and compliance gaps, and develop a remediation plan.
What challenges exist in third-party cloud audit coordination?
Challenges:
- Vendor Cooperation: Ensuring vendors provide access to necessary data and configurations.
- Shared Responsibility Model: Addressing gaps in responsibilities between cloud providers and healthcare organizations.
- Complex Configurations: Managing diverse cloud environments with varying security controls.
- Resource Constraints: Allocating time and expertise for thorough audits.
What are the best practices for third-party cloud audit coordination?
Best Practices:
- Automate Compliance Monitoring: Use tools to continuously monitor cloud environments for compliance.
- Maintain Clear Documentation: Standardize documentation for cloud architecture, security controls, and audit findings.
- Leverage Frameworks: Use frameworks like CSA CCMv4.0 to standardize audit processes and ensure thorough evaluations.
- Establish Vendor Contracts: Include compliance verification clauses and audit rights in vendor agreements.
- Train Staff: Educate teams on cloud compliance requirements and audit processes.
How can healthcare organizations streamline third-party cloud audits?
Streamlining Strategies:
- Use platforms like Censinet RiskOps™ to automate evidence collection and risk assessments.
- Implement compliance automation tools to reduce manual effort and improve accuracy.
- Maintain a centralized repository for audit documentation and findings.
- Collaborate with vendors to ensure timely access to data and configurations.


