Study: 162 New Medical Device Vulnerabilities Found
Post Summary
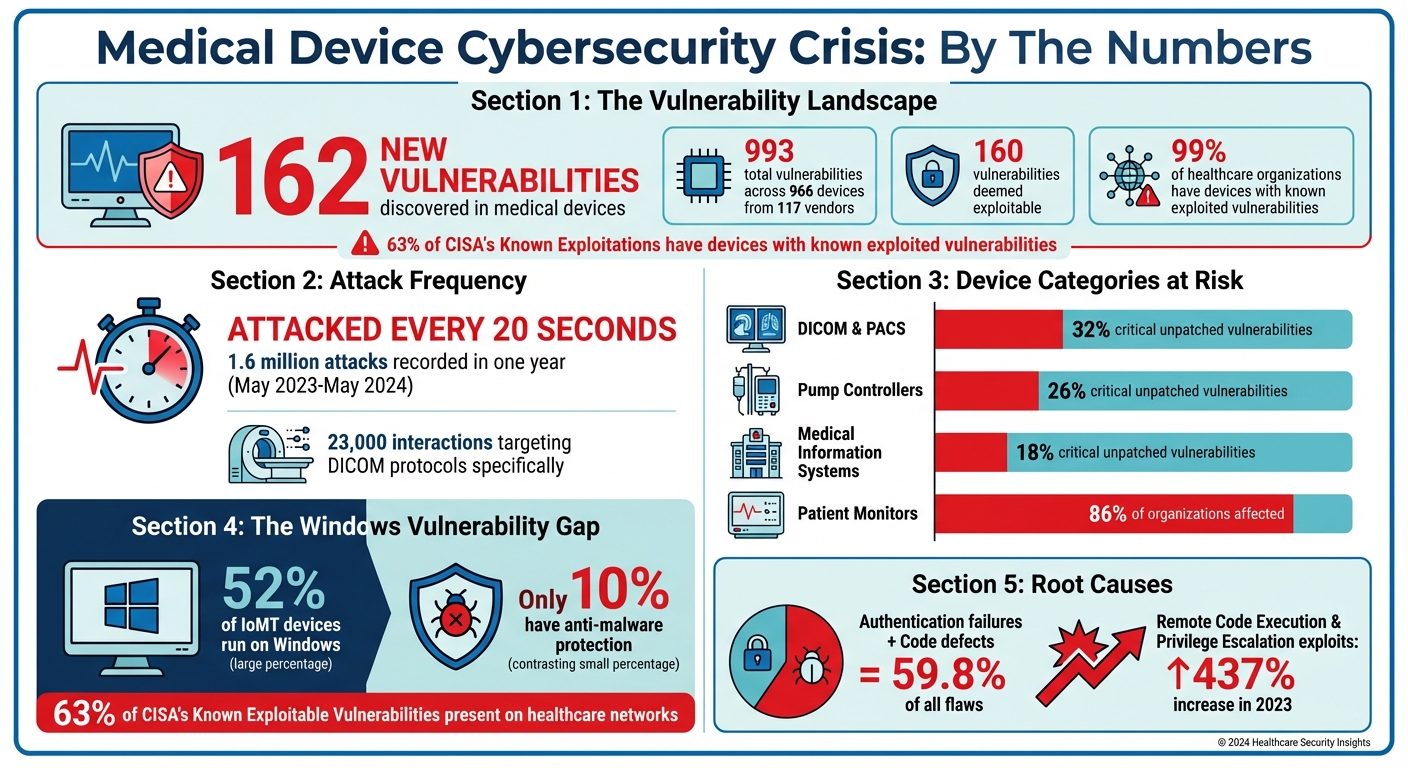
Healthcare is under attack. A new study found 162 vulnerabilities in medical devices that hospitals rely on daily, like imaging systems and patient monitors. These flaws allow hackers to take control, disable life-saving equipment, or steal patient data. Alarming stats include:
- 993 vulnerabilities across 966 devices from 117 vendors.
- Attackers hit simulated devices every 20 seconds, with 1.6 million attacks in a year.
- 99% of healthcare organizations have devices with known exploited vulnerabilities.
The biggest issues? Old, unpatchable devices and weak security. Over half of Internet-connected medical devices run on Windows, but only 10% have malware protection. Imaging systems and pump controllers are especially at risk, with threats like remote code execution and ransomware attacks.
What's the impact? Patient safety is at stake. Hackers can crash monitors, alter data, or delay care when systems are taken offline. Hospitals must act now by isolating devices, conducting regular risk assessments, and using tools like Censinet RiskOps™ to manage vulnerabilities. Cybersecurity in healthcare isn't optional - it's urgent.
Medical Device Cybersecurity Vulnerabilities: Key Statistics and Attack Patterns in Healthcare
House Hearing on Cybersecurity Vulnerabilities in Legacy Medical Devices
sbb-itb-535baee
Analysis of the 162 Medical Device Vulnerabilities
Building on earlier findings, the breakdown below highlights how these 162 vulnerabilities are distributed across different medical device categories and the associated risks.
Device Categories With the Most Vulnerabilities
Certain device categories stand out as particularly prone to vulnerabilities. For instance, pump controllers represent 26% of devices with critical unpatched flaws, with 20% showing extreme exploitability risks[6]. Similarly, medical information systems account for 18% of critical unpatched vulnerabilities[6]. Patient monitoring devices, such as monitors and ECGs, pose another significant concern, as 86% of healthcare organizations report having equipment with known exploited vulnerabilities[3].
| Device Category | Critical Unpatched Vulnerabilities | Primary Security Risks |
|---|---|---|
| DICOM & PACS | 32% | Remote code execution, information disclosure |
| Pump Controllers | 26% | Denial of service, unauthorized access |
| Medical Information Systems | 18% | Data exfiltration, ransomware |
| Patient Monitors | 86% of organizations affected | Known exploited vulnerabilities, insecure connectivity |
Identifying which devices are most vulnerable allows us to better understand the types of weaknesses attackers often target. These vulnerabilities are further explored through honeypot research.
Types of Vulnerabilities Discovered
The analysis of these vulnerabilities reveals recurring issues, primarily stemming from authentication failures and code defects. Together, these two factors account for 59.8% of all medical device security flaws[2]. Another alarming finding is that half of the top 10 vulnerabilities are tied to critical flaws in Windows systems, which enable remote code execution[6].
The situation is further worsened by the fact that 52% of IoMT devices (Internet of Medical Things) run on Windows, yet only 10% of these devices have active anti-malware protection[6]. This leaves hospital networks highly susceptible to malware and ransomware attacks. These insights emphasize the pressing need for ongoing vulnerability assessments and addressing medical device security risks through stronger risk management strategies.
Honeypot Data and Attack Patterns
To better understand how attackers target medical devices, researchers set up honeypot servers that mimicked real healthcare environments. The results revealed a relentless wave of automated attacks.
What the Honeypot Research Revealed
From May 2023 to May 2024, Forescout Technologies deployed honeypots designed to simulate medical settings. Under the guidance of Daniel dos Santos, Head of Security Research at Forescout Research – Vedere Labs, these honeypots recorded a staggering 1.6 million simulated attacks - roughly one every 20 seconds. The attacks primarily focused on DICOM and PACS systems, with 23,000 recorded interactions specifically targeting DICOM protocols [6][8]. Most attacks involved automated scans aimed at HTTP services. Barry Mainz, CEO of Forescout, shed light on the attackers' motives:
"The increasing prevalence of IoMT devices has introduced new cybersecurity risks, and cybercriminals are taking advantage to exploit vulnerabilities for financial gain through ransom payments or the sale of patient data on the dark web." [6]
The exposure of these systems has surged in recent years. DICOM servers saw a 27.5% increase between August 2022 and May 2024, while overall internet exposure for DICOM systems has grown by 286% since 2017. This heightened visibility makes them attractive targets. Attackers often exploit unencrypted communications to intercept or alter medical images, opening pathways for malware distribution or the theft of sensitive patient data, including personally identifiable information (PII), medical records, and treatment histories [6][8].
These findings reflect the challenges seen in actual cyber incidents, as discussed below.
Cases of Exploited Vulnerabilities
Honeypot data aligns closely with real-world exploitation trends. For example, in May 2024, the Cybersecurity and Infrastructure Security Agency (CISA) and Microsoft identified active exploitation of vulnerabilities (CVE-2023-43208 and CVE-2023-37679) in NextGen Healthcare's Mirth Connect platform. These vulnerabilities allowed nation-state and ransomware groups to breach login gateways and access sensitive healthcare data [9].
Imaging systems are particularly vulnerable. Alarmingly, 8% of hospital imaging systems have known exploited vulnerabilities (KEVs) tied to ransomware attacks [3]. As Team82 from Claroty highlighted:
"A successful cyberattack that impacts imaging systems can devastate triage efforts, and any re-routing of patients to other facilities because of an inability to conduct proper imaging can add significant delays to care and put lives at risk." [3]
Another key finding from the honeypot research is that attackers often target outdated systems running unsupported operating systems. Daniel dos Santos emphasized the importance of proactive measures:
"A single weak point can open the door to sensitive patient data. That's why identifying and classifying assets, mapping network flow of communications, segmenting networks, and continuous monitoring are essential." [6]
What These Vulnerabilities Mean for Healthcare Organizations
This research sheds light on the real-world dangers these vulnerabilities pose to healthcare systems. From patient safety to operational efficiency, the risks are both immediate and far-reaching. Researchers identified 993 vulnerabilities across 966 medical products, with 160 of them deemed exploitable [1]. These numbers highlight the critical need for action.
Effects on Patient Safety and Care
When medical devices are compromised, the consequences for patient safety can be severe. For instance, attackers exploiting flaws in patient monitors can remotely control the devices, crash them, or alter the data they display. This can mislead clinicians, creating dangerous discrepancies between displayed information and a patient’s actual condition [10][12]. Health-ISAC has warned:
"If hackers gain unauthorized access to medical records or alter patient data, it can result in misdiagnosis, incorrect treatment plans, or delayed care. In severe cases, patients' lives could be at risk." [1]
The ripple effects extend beyond individual devices. For example, when imaging systems are taken offline, hospitals may need to divert patients to other facilities, causing significant delays in treatment.
A stark example came in January 2025, when the FDA and CISA issued urgent warnings about vulnerabilities in the Contec CMS8000 and white-labeled Epsimed MN-120 patient monitors. These devices were found to connect automatically to a hard-coded IP address (202.114.4.119) upon startup, streaming patient data via the Line Printer Daemon protocol. This vulnerability (CVE-2025-0626 and CVE-2025-0683) enabled unauthorized remote code execution and the exfiltration of Protected Health Information (PHI). By July 2025, Contec addressed the issue by releasing a patch that disabled networking entirely, limiting the devices to local monitoring only [10][11][12].
Building management systems are another point of vulnerability. Attackers can disrupt temperature-controlled environments critical for storing medications like insulin or even disable elevators used for transporting patients to surgery or imaging areas [5]. Alarmingly, Remote Code Execution and Privilege Escalation exploits in medical devices surged by 437% in 2023 [1], reflecting the growing sophistication of these attacks.
Risks From Legacy Devices and IoMT
The challenges don’t end with immediate patient care. Legacy devices and the Internet of Medical Things (IoMT) create systemic cybersecurity gaps. Many legacy devices, often more than a decade old, were not designed with modern security standards in mind. Updating or patching them is often impractical, leaving them particularly vulnerable to cyberattacks [6].
IoMT devices further expand the attack surface. Across 351 hospitals, an estimated 2.25 million IoMT devices are in use [5]. Yet, only 10% of these devices run anti-malware protection due to software and certification limitations [6]. Shockingly, nearly all hospitals and healthcare delivery organizations rely on connected devices with known vulnerabilities [5].
Martin Fisher, Managing Partner at Kiraso Partners LLC, highlights the challenges with aging clinical devices:
"This is not, 'Oh my gosh!' like this has never happened before, especially with clinical devices that are getting older and older, and were built in a time when there was no such concept as threat modeling." [11]
Network architecture weaknesses add another layer of risk. Critical medical equipment is sometimes placed on "guest networks", making it easier for attackers to bridge into internal systems and gain deeper access to hospital infrastructure [7]. In fact, 63% of vulnerabilities listed in CISA's Known Exploitable Vulnerabilities catalog are present on healthcare networks [7]. These persistent problems emphasize the need for stronger risk management strategies.
How to Reduce Medical Device Cybersecurity Risks
Securing medical devices is a critical task for healthcare organizations. With 993 vulnerabilities identified across 966 medical products [1], reducing risks requires consistent assessments, advanced risk management tools, and collaborative strategies.
Regular Vulnerability Assessments
Frequent vulnerability assessments are the backbone of a strong medical device security program. These evaluations help identify potential weak points before attackers can exploit them. Phil Englert, VP of Medical Device Security at Health-ISAC, highlights the importance of this approach:
"Healthcare organizations must prioritize cybersecurity measures, employ robust cybersecurity practices, conduct regular risk assessments, and stay updated on the latest security threats and technologies to proactively protect against cyber threats." [1]
In addition to assessments, network segmentation plays a key role. Devices should be isolated from business networks using firewalls, placed on separate low-privilege subnets, and shielded by reducing their internet exposure. Proactively blocking malicious IP addresses, as advised by CISA, further strengthens defenses [12].
User authentication failures and code defects are among the leading causes of vulnerabilities [4]. Focusing assessments on these areas can lead to noticeable improvements in security. Adopting frameworks like the NIST Cybersecurity Framework (CSF) and aligning with HIPAA requirements also provides a structured method to address risks [13].
Platforms like Censinet RiskOps™ build on these practices, offering tools that simplify and enhance medical device risk management.
Using Censinet RiskOps™ for Risk Management
Once vulnerabilities are identified, managing them effectively becomes the next challenge. Censinet RiskOps™ simplifies this process with its Medical Device Security Analyzer, a tool designed to assess the cybersecurity posture of devices by examining hardware, software, and network connections for weaknesses.
The platform uses a risk matrix to generate clear scores and tailored remediation advice. By inputting device-specific details, users receive actionable recommendations, such as updating firmware or isolating systems. This helps prioritize which devices need immediate attention based on factors like outdated software or unpatched vulnerabilities.
Censinet RiskOps™ can analyze multiple devices simultaneously, offering a detailed view of individual risks alongside a facility-wide cybersecurity assessment. The platform also aids compliance with FDA, HIPAA, and ISO 14971 standards by providing actionable insights and remediation strategies.
Beyond technical tools, collaboration and AI-driven solutions further bolster cybersecurity efforts.
Collaborative Risk Management and AI Tools
No single organization can address medical device security in isolation. Collaborative risk management is essential, especially as healthcare remains a top target for advanced cyberattacks. The role of external researchers has grown significantly, with 68% of advisories now referencing their contributions, compared to just 7% before the FDA's 2016 guidance [4].
AI-powered tools enhance collaboration by automating visibility into healthcare supply chain security challenges and scaling risk management across vast datasets. For instance, Censinet AI™ accelerates risk assessments by enabling vendors to complete security questionnaires in seconds, automatically summarizing documentation, and generating detailed risk reports. This balance of human oversight and automation improves efficiency without sacrificing accuracy.
Participation in information-sharing communities like Health-ISAC further strengthens defenses. These communities provide access to peer insights, real-time alerts, and proven best practices [1]. Such collaborative efforts address vulnerabilities that could impact patient safety. Larry Pesce, Director of Product Security Research and Analysis at Finite State, stresses the urgency:
"The rise of weaponized exploits demands immediate, collective action to safeguard not only our technological integrity but, ultimately, patient safety." [1]
Conclusion
The discovery of 162 new IoMT vulnerabilities highlights the urgent need for healthcare to adopt a more proactive approach to cybersecurity. With 32% of DICOM workstations and PACS systems harboring critical unpatched flaws and cyberattacks striking every 20 seconds[6], the stakes couldn't be higher.
A major hurdle lies in legacy devices, many of which are over a decade old. These systems were never designed for internet connectivity, making them incompatible with modern security measures. Yet, they remain essential for patient care[6]. Compounding the issue, 52% of IoMT devices run on Windows, but only 10% of them have active anti-malware protection[6]. This gap leaves healthcare networks exposed, putting both patient safety and operational continuity at risk.
To address these vulnerabilities, healthcare organizations need to rethink their risk management strategies. Instead of relying on reactive patching, the focus should shift to continuous monitoring and integrating security throughout the device lifecycle[2][4]. Platforms like Censinet RiskOps™ can help by identifying vulnerabilities and prioritizing fixes based on real-world risk.
Ultimately, securing medical devices is about more than just deploying advanced technology - it requires unified efforts across the healthcare ecosystem. The risks extend far beyond data breaches. With healthcare institutions experiencing 1.6 breaches per day and 63% of CISA's Known Exploitable Vulnerabilities present on healthcare networks[6][7], every unpatched vulnerability threatens patient care. Measures like network segmentation, continuous monitoring, and collaboration through platforms like Health-ISAC offer crucial layers of defense against increasingly sophisticated threats.
FAQs
Which medical devices are most at risk?
Connected medical devices are among the most vulnerable to cybersecurity threats. This includes devices relying on the DICOM standard, as well as IoMT (Internet of Medical Things), IoT (Internet of Things), OT (Operational Technology), and IT systems. These devices often come with multiple security flaws and high levels of exposure, making them prime targets for cyberattacks.
The risk is particularly pronounced in countries like the United States, India, Germany, Brazil, Iran, and China. Their connectivity, while beneficial for healthcare operations, also opens the door to potential threats. This creates serious challenges for healthcare providers, as both organizational security and patient safety can be compromised.
Why can’t some devices be patched?
Some devices can't be patched because of regulatory requirements, outdated software that vendors have stopped supporting, or the potential for operational disruptions that involve downtime. On top of that, the need to prioritize patient safety while implementing cybersecurity measures adds another layer of complexity to the patching process.
What are the fastest steps hospitals can take now?
Hospitals can tackle medical device vulnerabilities efficiently by starting with a detailed risk assessment. This helps identify and rank devices that require updates or replacements. To bolster security, implement strategies such as network segmentation, strong authentication protocols, and ensuring firmware is updated regularly. For older, legacy devices, prioritize monitoring and threat detection to mitigate risks. Partnering with cybersecurity professionals and leveraging tools like Censinet RiskOps™ can simplify risk management and enhance overall protection.


