Top Tools for Secure PHI Disposal in Healthcare
Post Summary
Properly disposing of Protected Health Information (PHI) is more than a legal obligation - it’s critical for safeguarding patient privacy and avoiding costly penalties. Healthcare organizations must follow HIPAA and NIST 800-88 guidelines to ensure PHI is destroyed securely, whether in paper or electronic formats. Mishandling PHI can lead to significant financial losses, data breaches, and reputational damage.
Here’s a quick rundown of the best tools for secure PHI disposal:
- Cross-Cut Shredders: Ideal for paper, these devices shred documents into tiny, unreadable pieces.
- Data Wiping Software: Overwrites or erases digital media following strict standards.
- On-Site Hard Drive Shredders: Physically destroys hard drives, ensuring data is irretrievable.
- Chain-of-Custody Tracking Software: Tracks PHI from collection to destruction, ensuring compliance.
- Certificate of Destruction Generators: Documents proof of proper disposal for audits.
PHI Disposal Regulations in the United States
In the U.S., healthcare organizations must adhere to two key frameworks when disposing of Protected Health Information (PHI): HIPAA (Health Insurance Portability and Accountability Act) and NIST Special Publication 800-88. HIPAA establishes the legal standards for compliance, while NIST 800-88 provides a technical guide for securely sanitizing electronic media. Together, these frameworks ensure that patient data is completely destroyed and cannot be recovered[2].
The stakes couldn’t be higher. Regulators actively monitor PHI disposal practices, and improper handling has led to enforcement actions, including multimillion-dollar penalties.
HIPAA Requirements
Under HIPAA, both the Privacy Rule (45 CFR 164.530) and Security Rule require covered entities and business associates to implement safeguards - administrative, technical, and physical - throughout PHI’s lifecycle, including its disposal. While the Privacy Rule doesn’t prescribe specific destruction methods, it does mandate that PHI be rendered unreadable and unusable. For paper records, the Department of Health and Human Services (HHS) recommends methods like cross-cut shredding, burning, pulping, or pulverizing. For electronic PHI, the Security Rule requires organizations to establish policies for the final disposition of ePHI and associated hardware or media, including procedures for media reuse[2].
To comply with HIPAA, organizations must:
- Develop written policies for disposing of both paper and electronic PHI.
- Train employees on secure destruction methods and the risks of improper disposal.
- Use secure storage solutions, such as locked shred bins, before destruction.
- Document every disposal action, especially when third-party vendors handle the process, using certificates of destruction.
- Sign a Business Associate Agreement (BAA) with any disposal vendor, as the covered entity remains responsible for PHI even after its transfer to the vendor[2].
NIST 800-88 Guidelines
NIST Special Publication 800-88 provides a detailed roadmap for media sanitization, outlining three main methods: Clearing, Purging, and Destruction.
- Clearing involves techniques like overwriting to prevent basic data recovery, making it suitable for media reuse.
- Purging employs more advanced methods, such as cryptographic erasure, secure erase, or degaussing, ensuring data recovery is impossible - especially when media leaves the organization’s control.
- Destruction physically damages the media through methods like disintegration, pulverization, melting, incineration, or shredding, rendering data completely unrecoverable[2].
It’s important to note that simply deleting files or reformatting drives doesn’t meet sanitization standards. Organizations must select sanitization methods based on factors like the type of media, the sensitivity of the data, whether the media will be reused or discarded, and the operational context. Every sanitization action should be thoroughly documented and verified using certificates of destruction, chain-of-custody records, or sanitization logs to ensure compliance with both HIPAA and NIST 800-88 during audits[2].
Next, we’ll explore the tools that can help organizations meet these requirements.
Tools for Secure PHI Disposal
To comply with regulatory guidelines, healthcare organizations rely on specialized tools designed for the secure destruction of Protected Health Information (PHI). These tools ensure adherence to both HIPAA and NIST 800-88 standards for disposing of paper records, digital media, and hardware.
Cross-Cut Shredders for Paper Documents
When it comes to paper-based PHI, cross-cut shredders are the go-to solution. These shredders reduce documents into tiny particles - sometimes as small as 1 mm × 5 mm (0.04 in. × 0.2 in.) - meeting stringent DIN 66399 P-4 to P-7 standards. Unlike strip-cut shredders that leave long paper ribbons, cross-cut and micro-cut models turn documents into confetti-like fragments, making reconstruction nearly impossible. Brands like Fellowes Powershred and Aurora offer models that meet HIPAA-compliant certifications, including NAID AAA and DoD standards [2]. For industrial needs, some shredders can pulverize paper to particles as small as 2.4 mm (3/32 in.), aligning with NIST 800-88 guidelines [2]. In high-volume environments like clinics or hospitals, it’s worth investing in shredders with continuous-duty motors, jam protection, and advanced safety features.
Data Wiping Software for Digital Media
For digital media, data wiping software provides a secure way to erase PHI. Tools like DBAN offer free, multi-pass overwriting, while more advanced options like BitRaser and Blancco support both clearance and cryptographic erasure [2]. Blancco, for instance, complies with DoD 5220.22-M standards and generates detailed, audit-ready reports for each erasure, ensuring HIPAA compliance [2]. For solid-state drives (SSDs), cryptographic erasure or physical destruction is often necessary [2].
On-Site Hard Drive Shredders
When dealing with large volumes of retired or failed drives, on-site hard drive shredders provide a highly secure solution. These devices physically destroy storage media, ensuring that sensitive information is rendered irretrievable before it ever leaves the facility. Models like the SEM Model 0101, Intimus Crypto 500, and Garner PD-747 meet NIST 800-88 standards through methods like disintegration and pulverization [2]. Large healthcare facilities using on-site shredders for over 10,000 drives annually have reported zero incidents of PHI reconstruction [2]. Additionally, keeping destruction on-site reduces the risks associated with transporting media off-premises, maintaining a secure chain of custody.
Chain of Custody Tracking Software
Chain-of-custody software ensures accountability from the moment PHI-bearing media is collected until its final destruction. Platforms like Shred-X, Recycle Track International (RTI), and DocuShred use features like barcode scanning, GPS tracking, and blockchain technology to monitor the entire process in real-time [2]. These tools create comprehensive audit trails by documenting every handler, timestamp, and location change, which supports HIPAA compliance. For example, integrating RTI’s chain-of-custody software has been shown to significantly reduce breach risks [2]. This structured tracking works seamlessly alongside physical and digital destruction methods, adding an extra layer of security.
Certificate of Destruction Generators
To demonstrate compliance during audits, certificate-of-destruction tools provide essential documentation. Platforms such as Certify LLC, ShredderDocs, and Iron Mountain’s portal generate detailed certificates that outline the media type, destruction method, date, and relevant accreditations [2]. These certificates serve as legal proof that PHI was destroyed properly and align with HIPAA and NIST guidelines [2]. Many vendors now offer cloud-based solutions, automatically creating tamper-proof PDF certificates and securely storing them - eliminating the need for paper logs and enhancing recordkeeping efficiency.
PHI Disposal Methods and Tools Comparison
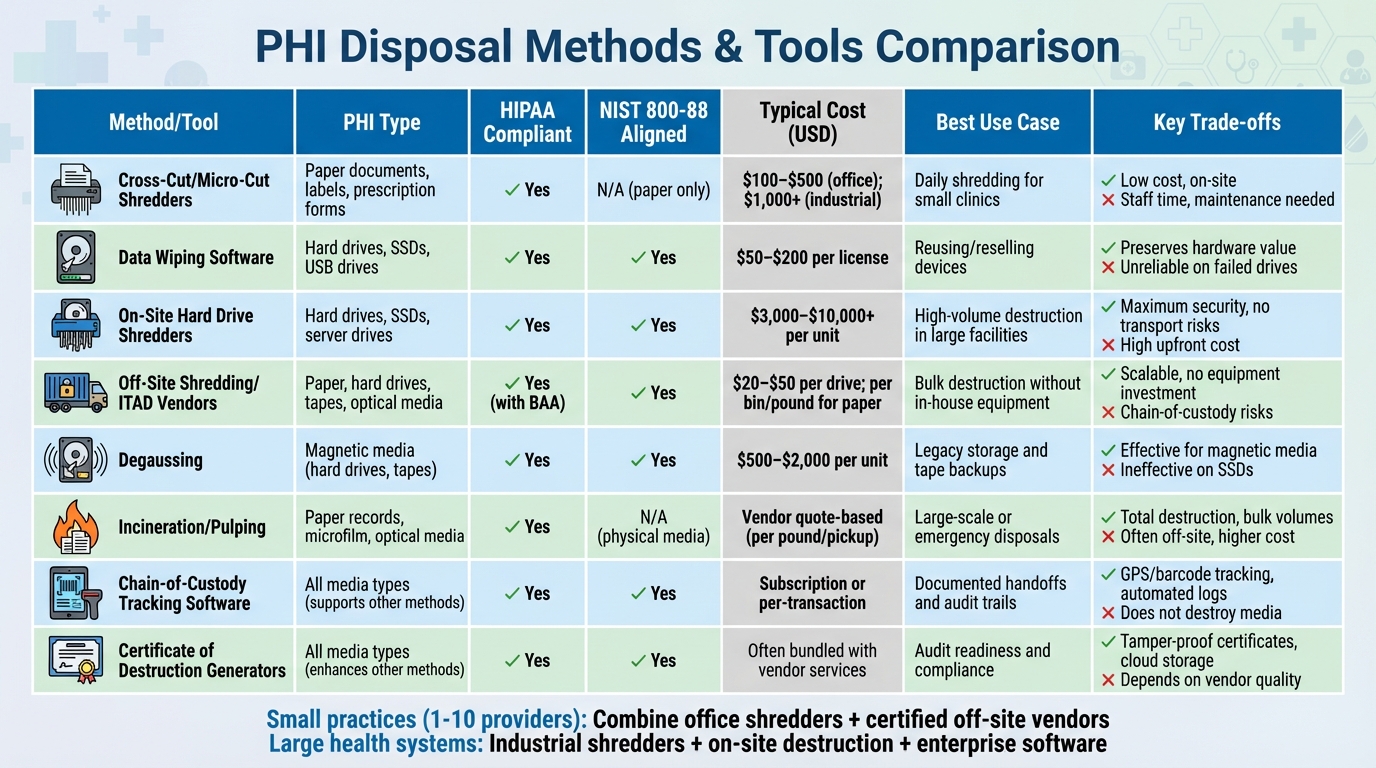
PHI Disposal Methods Comparison: Costs, Compliance, and Use Cases
Choosing the right PHI disposal method depends on factors like media type, volume, budget, and compliance requirements.
Comparison Table
Here’s a detailed comparison of various disposal methods to help you make an informed decision:
| Method/Tool | PHI Type | HIPAA Compliant | NIST 800-88 Aligned | Typical Cost (USD) | Best Use Case | Key Advantages | Key Limitations |
|---|---|---|---|---|---|---|---|
| Cross-Cut/Micro-Cut Shredders | Paper documents, labels, prescription forms | Yes | N/A (paper only) | $100–$500 (office); $1,000+ (industrial) | Daily shredding for small clinics or practices | Low per-use cost; on-site destruction; no vendor dependency | Requires staff time; maintenance; noise and dust; unsuitable for electronic media |
| Data Wiping Software | Hard drives, SSDs, USB drives, digital media | Yes | Yes | $50–$200 per license | Reusing or reselling electronic devices | Preserves hardware value; produces audit reports; cost-effective | May require cryptographic erase for SSDs; unreliable on failed drives; needs technical expertise |
| On-Site Hard Drive Shredders | Hard drives, SSDs, server drives, copier drives | Yes | Yes | $3,000–$10,000+ per unit | High-volume drive destruction in large facilities | Maximum security; no off-site transport risks; prevents PHI reconstruction | High upfront cost; requires dedicated space and power; not for paper |
| Off-Site Shredding/ITAD Vendors | Paper, hard drives, tapes, optical media | Yes (with BAA) | Yes | $20–$50 per drive; per bin/pound for paper | Bulk destruction for practices without in-house equipment | Scalable; no equipment investment; handles mixed media | Chain-of-custody risks; ongoing vendor fees; needs careful vetting |
| Degaussing | Magnetic media (hard drives, tapes) | Yes | Yes | $500–$2,000 per unit | Legacy storage and tape backups | Effective for magnetic media; reusable equipment | Ineffective on SSDs and flash media; renders media unusable; requires verification |
| Incineration/Pulping | Paper records, microfilm, optical media | Yes | N/A (physical media) | Vendor quote-based (per pound/pickup) | Large-scale or emergency disposals | Total destruction; handles bulk volumes; minimal reconstruction risk | Often off-site; requires licensed facilities; higher per-unit cost |
| Chain-of-Custody Tracking Software | All media types (supports other methods) | Yes | Yes | Subscription or per-transaction | Ensures documented handoffs and audit trails | Tracks media with barcodes/RFID, GPS monitoring, and automated logs | Does not destroy media; must pair with destruction methods |
| Certificate of Destruction Generators | All media types (enhances other methods) | Yes | Yes | Often bundled with vendor services | Ensures audit readiness and compliance | Produces tamper-proof certificates stored in the cloud | Does not destroy media; depends on vendor quality |
Small practices (1–10 providers) often find a combination of tools effective. For instance, using an office-grade cross-cut shredder for daily paper PHI and certified off-site vendors for periodic electronic media destruction balances cost and compliance. Business Associate Agreements (BAAs) and Certificates of Destruction ensure accountability.
Larger health systems, on the other hand, may invest in industrial shredders, on-site hard drive destruction equipment, and enterprise-grade wiping software. These are often supplemented by vendor programs for overflow or specialized media like optical discs.
To further enhance disposal security, integrated risk management tools can centralize oversight. Platforms like Censinet RiskOps™ streamline vendor risk assessments, monitor third-party adherence to HIPAA and NIST 800-88 standards, and store critical documentation such as certificates, BAAs, and policies. While not physically destroying media, such platforms provide centralized tracking and compliance support, helping organizations maintain secure and accountable PHI disposal practices.
sbb-itb-535baee
How Censinet Supports PHI Disposal Management
When it comes to securely disposing of Protected Health Information (PHI), physical destruction and data-wiping methods are essential. But they’re just one part of the equation. Censinet RiskOps™ adds a critical governance layer, ensuring that the entire process is secure and compliant. The platform centralizes oversight of all vendors involved in PHI disposal - like shredding companies, IT asset disposition providers, e-waste recyclers, and off-site storage partners. This streamlined approach allows healthcare organizations to evaluate, monitor, and document disposal risks effectively, laying the groundwork for thorough third-party risk assessments.
Third-party risk assessments are a key feature of Censinet RiskOps™. The platform uses standardized questionnaires based on NIST SP 800-88 controls to evaluate vendors handling PHI at the end of its lifecycle. These questionnaires cover essential areas such as chain-of-custody, secure transport, and incident reporting. Vendor responses are scored to identify potential gaps, such as missing certificates of destruction, weak data-wiping protocols, or unclear retention policies. This process ensures that any issues are flagged before contracts are signed or renewed. Terry Grogan, CISO at Tower Health, shared that the platform allowed three full-time employees (FTEs) to return to their primary roles, while two FTEs handled a significantly higher volume of risk assessments with ease [1].
Beyond the initial assessment, the platform acts as a centralized repository for audit documentation. It stores critical records like Business Associate Agreements (BAAs), certificates, and activity logs, creating a comprehensive, time-stamped audit trail. This trail tracks every detail, from the decision to decommission assets to the final destruction process, including vendor pickup and transportation. With dashboards and reports, privacy officers and CISOs can demonstrate due diligence, monitor compliance progress, and address any unresolved issues.
If disposal gaps are identified, collaborative remediation workflows within the platform ensure swift action. For instance, if a reassessment reveals that a long-time shredding vendor lacks itemized certificates of destruction or fails to align with NIST 800-88 standards, the platform can assign tasks to address these issues. It enables hospitals to request updated documentation, amend contracts, and track progress. Once the vendor provides the necessary evidence - such as updated policies or sample certificates - the hospital can upload these artifacts, mark the remediation as complete, and lower the residual disposal risk. All of this is done while maintaining a transparent, auditable record of corrective actions.
Conclusion
Proper disposal of Protected Health Information (PHI) isn't just a HIPAA requirement - it’s a cornerstone for maintaining patient trust. Unfortunately, improper disposal is still a frequent cause of reportable data breaches. To address this, tools like cross-cut shredders, NIST SP 800-88-compliant wiping software, audited hard drive shredding, and chain-of-custody tracking offer reliable, repeatable methods that are easier to manage, monitor, and scale compared to informal practices.
But compliance is only part of the equation. Secure disposal tools offer practical benefits, too. For instance, standardized shredders and centrally managed sanitization software simplify training, reduce inconsistencies across departments, and make audits more efficient. By partnering with trusted vendors and maintaining clear documentation, healthcare organizations can avoid costly fallout such as remediation efforts, forensic investigations, patient notifications, and damage to their reputation. Additionally, a well-executed disposal program minimizes dormant PHI that could otherwise become a liability in a breach, strengthening the organization’s overall cybersecurity defenses.
This is where platforms like Censinet RiskOps™ prove invaluable. The platform centralizes oversight of disposal vendors, streamlining processes through structured third-party risk assessments. It also consolidates critical documents - like Business Associate Agreements, certificates of destruction, and audit logs - into a single repository. If gaps in disposal practices are identified, the platform’s collaborative workflows enable swift action and transparent tracking. This allows healthcare organizations to reduce administrative burdens while handling a higher volume of risk assessments with fewer resources, all while demonstrating due diligence.
To fully realize these benefits, healthcare leaders should embed PHI disposal into their broader risk management strategies. This means clearly defining disposal requirements in enterprise policies, retention schedules, and IT asset lifecycle processes, with executive oversight assigned to privacy, security, or compliance officers. Regular audits, supported by platforms like Censinet RiskOps™, can ensure approved tools are consistently used, securely store media awaiting destruction, and maintain complete, accessible documentation. By integrating PHI disposal into ongoing risk management efforts, organizations can achieve continuous compliance and safeguard patient data throughout its entire lifecycle.
FAQs
What are the best tools for securely disposing of PHI in healthcare?
When it comes to securely disposing of Protected Health Information (PHI), tools like Censinet RiskOps™ stand out as tailored solutions for the healthcare sector. This platform is specifically designed to help organizations manage risks related to patient data while ensuring sensitive information is handled with care and disposed of securely.
By using specialized technologies, healthcare providers can simplify risk assessments, strengthen cybersecurity measures, and stay compliant with stringent data protection laws. These tools play a critical role in securely managing PHI disposal, minimizing breach risks, and protecting patient trust.
What role do HIPAA and NIST 800-88 guidelines play in disposing of PHI securely?
When it comes to securely disposing of Protected Health Information (PHI), HIPAA and NIST 800-88 guidelines set the standard. HIPAA mandates that PHI must be destroyed in a way that ensures it cannot be reconstructed or accessed again. This can involve methods like physical destruction or secure electronic disposal processes.
On the other hand, NIST 800-88 dives deeper into the technical details, offering specific data sanitization techniques. These include shredding, degaussing, and cryptographic erasure - methods designed to make data completely unrecoverable. Together, these guidelines ensure healthcare organizations can adopt disposal practices that safeguard patient privacy while maintaining strong data security.
Why is maintaining a chain of custody crucial for PHI disposal?
Maintaining a chain of custody is a critical step in ensuring that protected health information (PHI) is securely managed during the disposal process. It involves detailed documentation that tracks who accessed the data, when it was handled, and how it was managed, creating a clear trail of accountability.
This meticulous process plays a key role in preventing unauthorized access, minimizing the chances of data breaches, and staying compliant with HIPAA regulations. By adhering to a strict chain of custody, healthcare organizations safeguard sensitive patient information while upholding both legal requirements and ethical responsibilities for data security.


