Top Tools for Predictive Cybersecurity Analytics
Post Summary
Healthcare organizations are under constant threat from cyberattacks targeting patient data, medical devices, and supply chains. Predictive cybersecurity tools are transforming the industry by identifying risks before they escalate, reducing response times by 50%, and cutting investigation durations by 65%. This article highlights seven leading tools that leverage AI and machine learning to protect healthcare systems, streamline third-party risk assessments, and maintain compliance with regulations like HIPAA and the NIST Cybersecurity Framework.
Key Tools Covered:
- Censinet RiskOps™: Focused on healthcare, it automates third-party risk management, providing real-time updates and cutting assessment times to under a day.
- Darktrace: Uses self-learning AI to detect anomalies in medical networks, securing IoT devices and critical infrastructure.
- Splunk Enterprise Security: Offers machine learning-driven risk-based alerting and user behavior analytics to reduce alert fatigue and enhance threat detection.
- IBM QRadar: Combines advanced threat detection with compliance automation, tailored for healthcare's unique needs.
- Palo Alto Networks Cortex XDR: Provides AI-based threat detection and real-time ransomware prevention, securing medical IoT devices.
- Microsoft Sentinel: Cloud-native SIEM with machine learning-driven anomaly detection and seamless integration with multicloud environments.
- CrowdStrike Falcon: Delivers predictive attack analysis and managed services, reducing IT security costs and improving response efficiency.
These tools improve risk visibility, automate workflows, and ensure faster threat mitigation, helping healthcare organizations safeguard sensitive data and patient care systems.
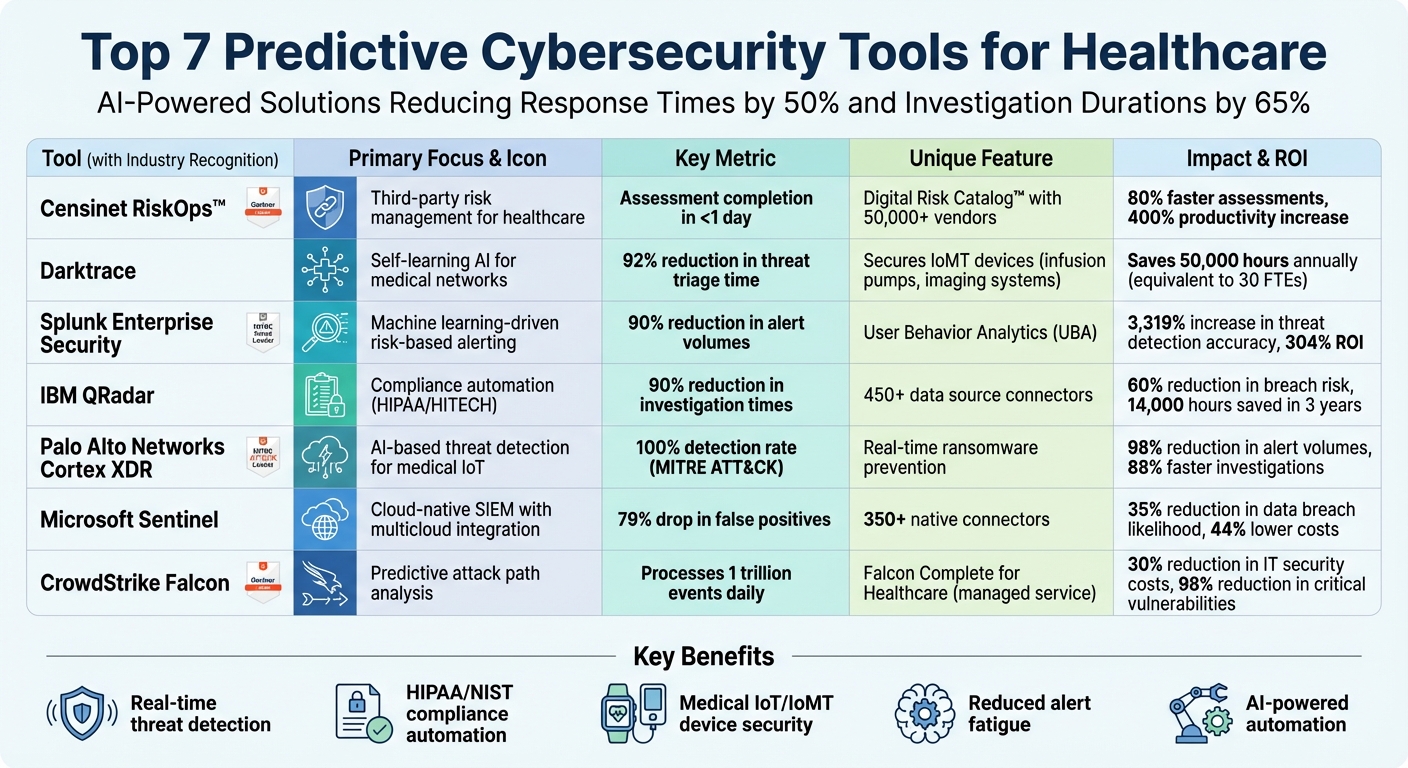
Comparison of 7 Leading Predictive Cybersecurity Tools for Healthcare
1. Censinet RiskOps™
Predictive Analytics Capabilities
Censinet RiskOps™ keeps your third-party risk management sharp with real-time updates to risk scores. This ensures you always have up-to-date visibility into potential threats. Its Portfolio Breach & Ransomware Alerts notify you immediately when a vendor in your network experiences a security breach - saving you the hassle of digging through manual research. The platform flags security gaps like missing Business Associate Agreements or vulnerabilities such as log4j exploits. It also uses predictive logic to categorize third parties based on their potential clinical impact and exposure to PHI (Protected Health Information), automatically scheduling reassessments as needed. By focusing only on what’s changed during reassessments, it cuts completion time to under a day [1]. These capabilities are designed specifically for healthcare, addressing unique risks in the industry.
Healthcare-Specific Features
Built exclusively for healthcare, Censinet RiskOps™ tackles risks in areas like medical devices, clinical applications, research, medical records, and supply chains. As Matt Christensen, Sr. Director GRC at Intermountain Health, puts it:
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare."
The platform’s Digital Risk Catalog™ includes over 50,000 vendors and products, each assessed and risk-scored, creating a detailed risk history for every entity in your network. It also connects over 100 provider and payer facilities, enabling them to share standardized cybersecurity data. This network even tracks Nth-party risks, such as cloud services used by your vendors, enhancing overall risk management efficiency [1][2].
Integration with Existing Systems
Censinet RiskOps™ doesn’t just provide analytics - it replaces outdated tools like spreadsheets and email chains with a cloud-based risk exchange. This system integrates directly into your existing workflows, allowing internal teams and subject matter experts to manage remediations within the platform. This creates a centralized audit trail, simplifying compliance and incident response. James Case, VP & CISO at Baptist Health, shares:
"Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with."
The platform’s One-Click Sharing feature lets vendors instantly share security questionnaires and evidence with unlimited customers, cutting down on administrative work across the healthcare ecosystem [1][2].
Scalability and Automation
With AI-driven automation, Censinet RiskOps™ speeds up gap detection and generates Corrective Action Plans to address issues quickly. Terry Grogan, CISO at Tower Health, highlights the impact:
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required."
This automation empowers healthcare organizations to extend risk management across their entire third-party lifecycle without adding staff. Automated workflows and real-time visibility ensure continuous progress in reducing risks [1][2].
sbb-itb-535baee
2. Darktrace
Predictive Analytics Capabilities
Darktrace leverages self-learning AI to establish a baseline of normal behavior for users, medical devices, and clinical workflows. Instead of depending on historical attack signatures, it continuously adapts to identify subtle deviations that may indicate potential threats[6][9]. Its Cyber AI Analyst streamlines investigations by automating much of the process, cutting threat triage time by 92% and speeding up incident response by tenfold. This efficiency can save organizations as much as 50,000 hours annually - comparable to adding 30 full-time SOC employees to the team[11]. Highlighting its impact, Michael Sherwood, Chief Innovation and Technology Officer at the City of Las Vegas, shared:
"We know we have an AI teammate that is continually learning how our entire ecosystem operates, strengthening our defenses and looking out for any abnormal activity." [11]
Darktrace has also been recognized as a Leader in the 2025 Gartner® Magic Quadrant™ for both Email Security Platforms and Network Detection and Response. Its reach extends to over 10,000 customers in 110 countries[10][12].
Healthcare-Specific Features
Tailored for healthcare environments, Darktrace secures interconnected systems, including medical IoMT devices like infusion pumps and imaging systems, as well as operational technology such as HVAC and power systems[7]. The platform learns the unique patterns of clinical networks, enabling it to differentiate between legitimate medical data transfers and malicious activities[7]. With full visibility into potential attack paths, it identifies and addresses vulnerabilities in patient data repositories and cloud environments[8]. Darktrace also supports compliance with healthcare-specific standards, such as HIPAA, FDA, GDPR, and NIST[8]. This proactive stance is critical for healthcare vendor breach response and long-term resilience. Since many medical devices lack built-in cybersecurity, the platform incorporates these devices into its baseline for anomaly detection, ensuring a comprehensive defense[7]. Furthermore, it seamlessly integrates with existing security infrastructures to enhance overall protection.
Integration with Existing Systems
Darktrace is designed to work alongside major security tools, including Cisco, Microsoft Sentinel, Check Point, Splunk, and QRadar. It also integrates with leading endpoint detection and response (EDR) solutions like Microsoft Defender, CrowdStrike, and SentinelOne. Its one-click EDR integrations enhance AI decision-making by incorporating endpoint alerts. John Eccleshare, Head of Information Security at bet365, remarked:
"Darktrace was the only product that offered that unique insight into the way our network needed to be analyzed and how it works." [11]
The platform can be deployed flexibly, whether as virtual instances (vSensors) in environments like Nutanix or as physical appliances for OT networks[7][13].
Scalability and Automation
Darktrace’s autonomous response capabilities allow it to neutralize threats in real time without disrupting critical clinical operations. It scales effortlessly across complex healthcare ecosystems, correlating threats and delivering complete visibility[11][14]. With 95% of security teams agreeing that AI can enhance the speed and efficiency of cyber defense[11], Darktrace’s automation empowers lean IT teams to prioritize strategic goals instead of constant firefighting. Steve Hutter, Head of Security Operations and Resilience at OneWeb, explained:
"We've seen a reduction in unwanted noise which allows the team to pivot on more strategic work." [11]
The platform's straightforward deployment makes it suitable for targeted areas like email security or for broader implementation across an entire IT/OT stack[6]. These automation and scalability features make Darktrace a strong contender for organizations exploring predictive analytics solutions.
3. Splunk Enterprise Security
Predictive Analytics Capabilities
Splunk Enterprise Security utilizes its Machine Learning Toolkit (MLTK) to power scalable and effective anomaly detection. Commands like fit and apply, along with the DensityFunction algorithm, help identify outlier events in data streams [15][16].
One standout feature is Risk-Based Alerting (RBA), which significantly reduces alert fatigue by assigning risk scores to users and systems. Alerts are triggered only when risk thresholds are exceeded, cutting down alert volumes by as much as 90% [18][19][20]. Dru Streicher, DevOps Lead Engineer at Progressive, highlighted its value:
"With risk-based alerting, we can stitch together a bunch of events to form the story of risk to our environment." [20]
Another key capability is User Behavior Analytics (UBA), which uses machine learning to profile entity behaviors. This helps uncover threats like compromised accounts or insider activities [18]. Organizations leveraging Splunk's unified TDIR platform have reported a 3,319% increase in threat detection accuracy and a 1,645% boost in incident resolution speeds [19]. Additionally, an IDC report noted that Splunk delivers a 304% ROI and cuts annual security costs by $4.89 million [19].
Healthcare-Specific Features
Splunk adapts its capabilities to meet the unique needs of healthcare organizations, which often manage fragmented ecosystems of medical devices, electronic health records (EHR), and cloud environments. Its Asset and Identity Management tools track and categorize assets while using "swim lane" visualizations in the Asset Investigator dashboard to uncover patterns in user and host actions [18]. Nathan Lesser, CISO at Children's National Hospital, emphasized:
"To ensure comprehensive security, we must instrument devices, the cloud, and every touchpoint where data resides. By bringing all that valuable telemetry into the Splunk environment, we gain the visibility needed to protect data - no matter where it lives." [20]
The platform's Common Information Model (CIM) plays a critical role by normalizing data from diverse sources - such as medical devices, EHR systems, and network infrastructure - into a standardized format. This consistency is essential for analyzing sensitive patient data across multiple systems [17][15]. This process is often complemented by automated vendor risk assessments to ensure third-party software meets security standards. Splunk's healthcare-focused approach integrates seamlessly with a wide range of tools, enhancing its ability to provide meaningful security insights.
Integration with Existing Systems
Splunk Enterprise Security supports integration with over 300 third-party tools and enables more than 2,800 automated actions through its connectors [18]. By combining SIEM, SOAR, UEBA, and agentic AI into a single interface, it eliminates the hassle of switching between tools [19]. Features like Federated Search and Federated Analytics allow teams to analyze external data repositories, such as Amazon S3 or Amazon Security Lake, without incurring ingestion costs [19][20]. Moreover, the platform includes built-in integration with Cisco Talos threat intelligence at no extra cost [19]. Olivier Cassignac, Head of Security Incident Detection at La Poste, praised its flexibility:
"The level of customization within Splunk is critical. There are no limits to the tool." [20]
Scalability and Automation
Splunk’s agentic AI capabilities automate tasks like malware reversal and alert triaging, while data model acceleration speeds up predictive searches [15][17][19]. The Splunk Threat Research Team enhances security with over 1,800 prebuilt detections, all aligned with the MITRE ATT&CK framework [20]. Recognized as a leader in the Gartner® Magic Quadrant™ for SIEM for 11 consecutive years, Splunk has also been ranked the #1 SIEM solution across all three Use Cases in the 2025 Gartner® Critical Capabilities for SIEM [19][20].
4. IBM QRadar
Predictive Analytics Capabilities
IBM QRadar leverages User Behavior Analytics (UBA) to establish behavioral baselines, helping it identify unusual activities like compromised credentials or unauthorized access escalations through risk scoring mechanisms [21]. Its Network Detection and Response (NDR) compares incoming network flows against established norms in real time, assigning "outlier scores" to suspicious communications [22]. On the endpoint side, QRadar's Endpoint Detection and Response (EDR) uses hundreds of machine learning models to spot zero-day threats almost instantly [21]. The Magnitude Scoring algorithm further enhances alert prioritization by assigning weights to Relevance (50%), Severity (30%), and Credibility (20%) [23]. This AI-driven approach slashes false positives and cuts investigation times by up to 90% [24][22]. These capabilities are particularly suited for industries like healthcare that demand precise compliance and deployment options.
Healthcare-Specific Features
QRadar addresses the unique needs of healthcare organizations with compliance packs designed to automate regulatory reporting for HIPAA and HITECH [23]. For organizations requiring strict data sovereignty or air-gapped setups, QRadar supports on-premises deployment [24]. Andrew Frank, Manager of IT Security Services at Mohawk College, shared his perspective:
"We wanted a tool that was easy to use, didn't require substantial amounts of training for users to be able to pivot and search through data to both see event logs and do network traffic analysis." [21]
QRadar has proven its effectiveness by helping organizations reduce the risk of major security breaches by 60%. Additionally, automated false-positive detection has saved security teams over 14,000 hours in just three years [22]. Containing breaches quickly is also financially impactful - resolving incidents in under 200 days can save an average of $1.1 million [23].
Integration with Existing Systems
QRadar stands out for its seamless integration with existing healthcare IT systems [23]. With over 450 data source connectors and 370 partner extensions, it can ingest telemetry from endpoints, cloud platforms, and network devices [23]. This unified approach consolidates data from disparate systems, enabling analysts to trace events across the full attack path [22]. Furthermore, QRadar supports open-source Sigma rules, allowing security teams to quickly adapt to emerging healthcare-specific threats by importing crowdsourced threat intelligence [22].
A notable success story comes from Sutherland Global Services, where QRadar's SIEM implementation reduced their Mean Time to Detect (MTTD) from days or weeks to just hours by correlating data across their IT environment [21]. Additionally, QRadar EDR integrates seamlessly with QRadar SIEM without increasing the events-per-second (EPS) count, simplifying licensing concerns [22].
Scalability and Automation
QRadar offers cloud-native log management optimized for rapid analytics, capable of processing millions of events in near real time on platforms like AWS [25]. Its QRadar SOAR component enhances incident response with pre-built workflows tailored to over 180 global data breach and privacy regulations [25]. AI and automation tools streamline alert triage, speeding up the process by 55% [25]. IBM's leadership in the field is underscored by its recognition as a Leader in the 2024 Gartner Magic Quadrant for SIEM - marking the 14th consecutive year it has received this distinction [23]. Users also highlight QRadar's ability to lower total ownership costs by reducing the manual effort needed for investigations and remediation [22].
5. Palo Alto Networks Cortex XDR
Predictive Analytics Capabilities
Cortex XDR leverages AI-based behavioral analysis to identify and neutralize threats effectively. It achieved a 100% detection rate in the MITRE ATT&CK Enterprise Evaluations Round 6 without needing additional configuration [46,47]. By using machine learning, it establishes baseline behavior across endpoints, networks, and cloud environments, flagging anomalies like lateral movement or data exfiltration. With over 400 predefined correlation rules, the platform ensures precise threat detection [28].
The Advanced WildFire feature adds another layer of protection by offering cloud-based sandboxing. This enables real-time file analysis, stopping ransomware from encrypting critical systems, such as those in hospitals, before the threat can execute [26]. In the 2025 AV-Comparatives EPR Test, Cortex XDR scored 99% in both threat prevention and response categories [29]. Additionally, it reduces alert volumes by 98% through intelligent grouping and deduplication, easing the workload for analysts in high-stress environments like healthcare [46,48].
Healthcare-Specific Features
Cortex XDR is designed to address the unique challenges of healthcare security. It integrates seamlessly with Medical IoT Security to safeguard unmanaged clinical devices like infusion pumps, MRI machines, and patient monitors - devices that typically lack standard security agents and can become vulnerabilities [40,45]. The platform's Identity Threat Detection and Response (ITDR) module further strengthens security by monitoring credential theft and insider threats. For example, it can detect "impossible traveler" scenarios, where the same account logs in from geographically distant locations simultaneously [45,46].
A real-world success story comes from Asante Health, which modernized its Security Operations Center using Cortex XDR. This upgrade reduced its mean time to respond (MTTR) from weeks to minutes [29]. Peter Fletcher, Director of Cyber Security at San Jose Water Company, shared his experience:
"Not only did Cortex XDR reduce the number of incidents we had to look at, but the time taken to act on those incidents was also reduced… The X in XDR, for me, is the extension of my team." [30]
Integration with Existing Systems
Cortex XDR excels in bringing together data from various sources. It consolidates telemetry from endpoints, networks, cloud environments, and third-party tools into a single, unified view [45,48]. The platform supports raw log ingestion through protocols like Syslog, Kafka, and NetFlow, enabling healthcare organizations to optimize their current infrastructure without requiring a complete overhaul [27]. It also integrates with HR systems like Workday and identity providers such as SailPoint, improving its ability to detect user-based threats [28].
The platform works hand-in-hand with Cortex XSOAR, enabling automated, playbook-driven incident responses. This standardization significantly reduces investigation times - by as much as 88% - as it provides detailed context and root cause analysis for alerts [46,48]. North Dakota IT (NDIT) demonstrated this efficiency by cutting its open alert volume by 99.6% after implementing Cortex XDR [29].
Scalability and Automation
Cortex XDR's cloud-native design makes it highly scalable, ideal for healthcare systems with multiple locations. It eliminates the need for on-premises log servers, simplifying deployment across large healthcare networks [45,48]. Features like "Search and Destroy" allow for quick threat elimination across endpoints, while "Host Restore" automates remediation by removing malicious files and fixing damaged registry keys. These capabilities collectively reduce total cost of ownership (TCO) by 44% [46,48].
Better, a digital lender, streamlined its security operations with Palo Alto Networks, automating 90% of its threat response processes [29]. To accommodate varying needs, Cortex XDR offers flexible pricing options: XDR Prevent, XDR Pro per Endpoint, and XDR Pro per Gigabyte, making it easier for healthcare organizations to scale based on their data and budget requirements [27].
6. Microsoft Sentinel
Predictive Analytics Capabilities
Microsoft Sentinel brings advanced predictive tools to healthcare cybersecurity, helping organizations transition from reactive to threat intelligence-driven cybersecurity. Using User and Entity Behavior Analytics (UEBA), the platform establishes dynamic behavioral baselines by analyzing historical user activity. This allows it to identify anomalies, such as unusual access patterns. For example, if a clinician's behavior deviates significantly from their department's typical access trends, it could signal unauthorized access to sensitive patient records [33].
The Fusion Correlation Engine takes this a step further by leveraging scalable machine learning algorithms. It condenses millions of low-fidelity alerts into a manageable number of high-fidelity incidents, making it easier to detect sophisticated, multistage cyberattacks that might otherwise slip through the cracks. Organizations using Sentinel have seen a 79% drop in false positives and a 35% reduction in the likelihood of data breaches [35].
Anomaly detection models continuously monitor user behavior, flagging significant deviations. Additionally, Sentinel integrates threat intelligence from both Microsoft and third-party sources. By cross-referencing logs with domain, IP, and URL threat indicators, it provides valuable context for identifying potential attacks [31][32]. Its Behaviors Layer further enhances these insights by mapping data to the MITRE ATT&CK framework, helping organizations understand the "who, what, and why" behind potential threats [33].
Integration with Existing Systems
Microsoft Sentinel’s integration capabilities make it a versatile tool for healthcare organizations. It connects seamlessly with over 350 native connectors and offers a codeless framework for creating custom integrations, making it compatible with niche or legacy healthcare applications [34][35]. The platform consolidates data from multicloud environments like Azure, AWS, and Google Cloud, as well as on-premises infrastructure and third-party security tools, providing a unified monitoring view. Steven Fry, Chief Digital Officer at Salford City Council, highlighted this feature:
"It's not just the Microsoft estate that's in there - it's all the other applications and infrastructure we use ... We have a single pane of glass so we can monitor, detect, and respond." [35]
Sentinel also integrates natively with Microsoft Defender XDR, creating a unified approach to investigations and automated responses across identities, endpoints, and applications. Masaki Onishi, Director of Security Operations Division at NTT Communications, emphasized its efficiency:
"By ingesting logs and alerts from our security solutions into Microsoft Sentinel, we can correlate threat analysis from multiple sources. This automation saves valuable time to resolve incidents." [35]
This level of integration simplifies operations, making Sentinel a powerful tool for managing complex healthcare IT environments.
Scalability and Automation
As a cloud-native solution, Microsoft Sentinel eliminates the need for on-premises infrastructure, scaling effortlessly to meet the needs of growing organizations [34][35]. Users report 44% lower costs compared to traditional SIEM solutions [35]. The platform also features automated attack disruption and a Security Copilot powered by generative AI. This tool summarizes incidents and suggests responses, cutting mean time to resolution (MTTR) by 30% [35].
Chunqui Chen, Director of IT Monitoring and Security Operations Center at Danfoss, praised the platform’s simplicity:
"Setting up Microsoft Sentinel to ingest logs from 20 applications and thousands of devices was a very simple thing." [35]
For cost optimization, Sentinel offers tiered storage options, including analytic and data lake tiers, which are ideal for managing high-volume data and long-term retention [34]. Pricing is flexible, based on the volume of data ingested, stored, and consumed, with a 50 GB promotion available for both new and existing customers [35].
7. CrowdStrike Falcon
Predictive Analytics Capabilities
CrowdStrike Falcon leverages Predictive Attack Path Analysis (APA) to map out potential attack routes, enabling security teams to address vulnerabilities before they’re exploited. Its Predictors of Attack (PoA) feature works in real-time to anticipate threats, giving organizations a proactive edge against breaches [36]. At the heart of this system is the CrowdStrike Threat Graph®, a cloud-scale AI engine that processes over 1 trillion security events daily, analyzing 15 petabytes of data and 2 trillion vertices to uncover new attacks linked to known threat actors [39].
The platform also employs Multi-Level Behavioral Analytics, which uses machine learning to detect unusual activity at the User, Peer, and Company levels. This approach uncovers deviations that might signal insider threats or data breaches [38]. DJ Goldsworthy, VP of Security Operations, highlighted the importance of AI in staying ahead:
"Our adversaries are coming at us with AI PhDs. We need AI at the same level, and Charlotte AI helps us identify and secure vulnerabilities in real time as our environment evolves" [40].
Healthcare-Specific Features
CrowdStrike offers a tailored solution for the healthcare sector: Falcon Complete for Healthcare. This managed service is specifically designed to address staffing challenges in healthcare organizations [37]. It uses a lightweight, no-reboot agent to ensure uninterrupted medical operations and patient care [37]. Tahir Ali, CTO & CISO at Montage Health, shared how CrowdStrike eased their workload:
"The pressure on healthcare is just tremendous... Those things that are extremely important and really time consuming were handed over to CrowdStrike so we had more time to do advanced work for security" [37].
The platform excels in protecting patient data from ransomware attacks while helping organizations comply with privacy regulations by providing unified threat intelligence and visibility [37]. Healthcare organizations using Falcon have reported significant benefits, including a 30% reduction in IT security costs [37]. Additionally, Charlotte AI automates detection triage, saving teams over 40 hours per week and delivering security insights 75% faster than manual methods [40].
Integration with Existing Systems
CrowdStrike Falcon integrates smoothly with existing systems, enhancing operational efficiency. Its Agent Collaboration Framework uses bidirectional APIs to connect with security and IT tools, with Charlotte AI acting as a central "SOC commander" [41][39]. For healthcare, the platform partners with Zscaler to implement zero-trust security, safeguarding medical data and remote access [37]. Through Falcon Fusion SOAR, the platform connects with third-party tools like ServiceNow and Slack, automating tasks like incident ticketing and team communication [38].
Tahir Ali of Montage Health praised Falcon’s performance in their virtual desktop infrastructure (VDI) environment:
"We run a lot of virtual desktop infrastructure (VDI), so we didn't want our endpoint agent slowing down login or boot-up times. CrowdStrike was the superstar of the POC, so we bought it" [41].
Falcon supports a variety of environments, including Windows, Linux, macOS, mobile devices (iOS/Android), and public cloud platforms like AWS, Azure, and Google Cloud. This broad compatibility ensures comprehensive visibility across hybrid setups [37].
Scalability and Automation
Falcon’s cloud-native design ensures effortless scalability without the need for additional hardware or complex restructuring [39]. The platform’s Falcon Fusion SOAR automates workflows, such as creating ServiceNow tickets or sending Slack alerts for critical threats [38]. Daniel Hereford, CISO at Intermex, shared their success:
"Within one year using Falcon Exposure Management, we reduced critical vulnerabilities by 98% in our DMZ, 92% across our entire server board and 86% on all workstations" [42].
The lightweight agent deploys in hours without requiring reboots, ensuring uninterrupted operations in clinical environments [37]. Kevin Tsuei, SVP Information Security Officer at CBC, highlighted the platform’s consolidation benefits:
"The Falcon platform has allowed us to unify our security toolbox. It yields big savings for us, but more importantly, it allows us to focus" [41].
AI, Cybersecurity & The Future of Healthcare
Pricing and Features Comparison
Censinet One™ offers on-demand pricing that adjusts based on your assessment needs and available resources [43]. This approach ensures cost efficiency while maintaining scalable risk management capabilities.
The platform provides three delivery models: Platform, Hybrid Mix, and Managed Services. These options cater to different organizational needs:
- Platform: Tailored for healthcare delivery organizations (HDOs) with strong internal security teams. These teams independently use the Censinet RiskOps™ software to manage cyber risks [43].
- Hybrid Mix: Designed for organizations navigating resource changes or evolving security programs. This model combines software with managed services, allowing you to scale support up or down as needed [43].
- Managed Services: Perfect for HDOs with limited cybersecurity staff. This option fully outsources risk management to Censinet experts, ensuring comprehensive support [43].
| Plan Model | Delivery Method | Best For | Key Features |
|---|---|---|---|
| Platform | Internal use of Censinet RiskOps™ | HDOs with strong internal security teams and workflows | Workflow automation, access to the Digital Risk Catalog™ (50,000+ pre-assessed vendors), and Cybersecurity Data Room™ |
| Hybrid Mix | Software + managed services blend | Organizations with shifting resources or evolving needs | Flexible support that adjusts as needed |
| Managed Services | Fully outsourced to Censinet | HDOs with minimal cybersecurity staff or scaling needs | Complete outsourcing of third-party and enterprise risk management |
All plans leverage AI-powered automation, which reduces assessment times by over 80% and increases productivity by over 400% [44]. This automation not only streamlines risk assessments but also consolidates cybersecurity processes, significantly easing resource demands.
A standout feature across all plans is 1-Click Sharing, enabling vendors to complete standardized questionnaires once and share them with unlimited customers [1]. Additionally, delta-based reassessments ensure that updates take less than a day, providing continuous risk coverage without the need for manual data collection [1].
Conclusion
Healthcare organizations can no longer afford to rely on outdated, reactive cybersecurity measures. Traditional signature-based detection methods deliver only 65–75% accuracy, whereas machine learning-powered predictive analytics achieve an impressive 86–95.7% accuracy for identifying known attacks [3][45]. This difference isn’t just about numbers - it directly affects patient safety and the continuity of care, where every second counts.
Proactive defense is no longer optional; it’s a necessity. Consider this: a major U.S. hospital leveraged AI to detect and neutralize a ransomware attack in just 2.3 seconds, preventing any breach from occurring [4]. Similarly, Milton Keynes University Hospital uses self-learning AI to monitor for anomalies like insider threats, providing round-the-clock protection while minimizing false alerts and downtime [4]. These examples highlight how predictive technologies can safeguard patients by stopping cyber threats before they disrupt healthcare operations.
Looking ahead, the challenges are only growing. By 2026, healthcare systems will face intensified threats, including AI-driven attacks that evolve faster than human detection capabilities, vulnerabilities in third-party vendors, and outdated legacy systems that lack interoperability. Attackers are also shifting tactics, targeting high-value patient data with stealthy extortion campaigns [5]. Alarmingly, nearly 23% of clinicians now rely on unsanctioned AI tools for routine tasks, introducing compliance and security risks that traditional methods simply cannot address [5].
The solutions discussed in this article underscore the urgent need for proactive cybersecurity in healthcare. Research by Chowdhury et al. (2024) demonstrates that hybrid machine learning models significantly enhance cybersecurity, achieving 91.3% accuracy in threat classification and enabling more effective policy development through integrated threat intelligence [3][45]. These advances far surpass the capabilities of reactive approaches.
To meet these challenges head-on, adopting a comprehensive solution like Censinet RiskOps™ is essential. With its 24/7 monitoring, AI-driven automation, and continuous risk assessment, such a platform ensures healthcare organizations can stay ahead of attackers and maintain uninterrupted patient care.
FAQs
What makes cybersecurity analytics “predictive” in healthcare?
Predictive cybersecurity analytics in healthcare leverages advanced tools like machine learning and AI to spot threats before they happen. By examining patterns in network activity, device behavior, and system vulnerabilities, these systems can flag early signs of risk. Features such as AI-powered risk scoring and dynamic modeling allow healthcare organizations to take proactive steps to address potential dangers. This approach not only safeguards sensitive patient information but also helps maintain seamless operations.
How do we choose between cloud and on-prem deployment for predictive security?
Choosing between cloud and on-premises deployment for predictive security in healthcare boils down to a few key considerations: scalability, control, and compliance.
Cloud solutions are known for their flexibility, offering automatic updates and reducing IT overhead. They're a great fit for organizations looking for quick deployment and minimal infrastructure management. On the other hand, on-premises solutions give you tighter control over sensitive data, making them a strong option for meeting strict regulatory requirements.
For more complex healthcare environments, a hybrid approach might be the answer. It blends the flexibility of the cloud with the control of on-premises systems, giving you the best of both worlds. Ultimately, the decision should reflect your organization's specific resources, priorities, and long-term goals.
What data sources should we connect first to get accurate predictions?
To make accurate predictions in healthcare cybersecurity, it's crucial to link data sources that offer real-time, in-depth insights. Some of the most important sources include:
- Electronic Health Records (EHRs): These hold sensitive patient information and can reveal potential risks or unauthorized access attempts.
- Internet of Medical Things (IoMT) devices: Smart medical devices generate data that can indicate unusual activity or vulnerabilities.
- Network activity logs: Monitoring these logs helps detect suspicious behavior or breaches in progress.
- Threat intelligence feeds: These provide updates on emerging risks and attack patterns in the cybersecurity landscape.
- Third-party vendor assessments: Evaluating external vendors ensures their systems don’t introduce vulnerabilities.
By integrating these sources, healthcare organizations can spot risks, detect irregularities, and address weaknesses before they escalate, protecting both patient information and essential systems.


