Vendor Encryption Policies vs. Healthcare Compliance
Post Summary
Vendor encryption policies define how third-party vendors secure electronic protected health information (ePHI) during storage and transmission to meet healthcare compliance standards.
Encryption protects sensitive patient data, ensures compliance with HIPAA and HITECH, and reduces the risk of breaches and unauthorized access.
Requirements include using AES-256 for data at rest, TLS 1.3 for data in transit, secure key management, and adherence to NIST standards like SP 800-111 and SP 800-52.
Challenges include managing encryption keys, integrating encryption with legacy systems, ensuring vendor compliance, and addressing the costs of encryption solutions.
Best practices include enforcing end-to-end encryption, using hardware security modules (HSMs), conducting regular audits, and requiring vendors to sign Business Associate Agreements (BAAs).
Organizations can ensure compliance by conducting risk assessments, monitoring encryption practices, and leveraging tools like Censinet RiskOps™ for real-time oversight.
Encryption policies for vendors are falling short of healthcare compliance. With HIPAA updates now requiring mandatory encryption for all electronic protected health information (ePHI) starting January 2025, healthcare organizations must ensure their vendors meet stricter standards. Failure to comply can lead to hefty fines, breach notifications, and disruptions to patient care.
Key takeaways:
- HIPAA 2025 Updates: Encryption for ePHI at rest and in transit is mandatory.
- Common Vendor Gaps: Vague encryption claims, poor key management, and lack of multi-factor authentication (MFA).
- Compliance Standards: Use AES-256 encryption, TLS 1.3, FIPS-validated modules, and robust key management.
- Action Steps: Assess vendors, enforce stricter contracts, and adopt continuous risk monitoring tools.
Without proper encryption, healthcare organizations face serious regulatory and financial risks. It's time to close the gaps, protect patient data, and align vendor practices with compliance requirements.
Encryption Requirements for Healthcare Compliance
Regulatory Standards: HIPAA, HITECH, and NIST
Healthcare organizations are now required to align their encryption practices with the stringent standards set by HIPAA, HITECH, and NIST. The HIPAA Security Rule (45 CFR §164.312) outlines technical safeguards to protect electronic protected health information (ePHI), emphasizing access control and transmission security. While encryption was once considered "addressable", meaning alternatives could be used with proper justification, the January 2025 Notice now mandates encryption for all ePHI using NIST-approved cryptographic methods [4][3][8].
Compliance demands the use of cryptographic standards validated by FIPS 140-2 or FIPS 140-3, ensuring alignment with both HIPAA and HITECH requirements [6][7]. The HITECH Act also provides a Safe Harbor clause: if ePHI is encrypted according to NIST standards, organizations may avoid mandatory breach notifications under the Breach Notification Rule [7]. This framework sets the stage for the technical measures discussed below.
Encryption Requirements for ePHI: Data at Rest and in Transit
Encryption rules apply to all environments where ePHI is stored or transmitted. For data at rest, organizations must implement encryption on servers, endpoints, portable devices, and backups using standards like AES-256 or equivalent [6][7]. The 2025 updates go further, requiring full-disk encryption and database-level protections [2][4][6].
For data in transit, all network communications involving ePHI must be secured. This includes using TLS 1.2 or higher (ideally TLS 1.3) for network transmissions, encrypted email systems for PHI communications, and VPNs or secure tunneling for telehealth and remote access [6][5]. Outdated protocols must be phased out to minimize vulnerabilities [6]. For example, patient portals and APIs should operate over HTTPS/TLS connections to ensure secure data exchanges. These measures are especially critical, given that 92% of healthcare organizations reported cyberattacks last year, and 69% experienced disruptions to patient care [2]. Together, these safeguards create a foundation for effective encryption practices, supported by proper key management and documentation.
Key Management and Documentation Standards
Encryption alone isn’t enough - proper key management and thorough documentation are essential to compliance. According to NIST SP 800-57 and FIPS 140-2, encryption keys must be stored in secure, dedicated systems like Hardware Security Modules (HSMs) or cloud-based key management services, ensuring separation from the encrypted data [6]. Organizations should enforce role-based access for key operations, implement regular key rotations, and establish clear procedures for key revocation and destruction [6][9].
The 2025 updates also introduce stricter documentation requirements. Organizations must conduct annual security assessments, maintain detailed asset inventories, and keep written encryption policies [3][8]. Configuration records should outline systems holding ePHI and their protection measures. Additionally, evidence of HIPAA-compliant risk analyses - particularly those addressing encryption decisions - must be readily available [6][7]. These records are crucial during OCR investigations, where fines often result from inadequate risk management and missing technical controls rather than the breach itself [3].
Common Vendor Encryption Policies and Their Shortcomings
Standard Vendor Encryption Approaches
A lot of vendors rely on vague phrases like "industry-standard encryption" or "data is encrypted", but they often fail to provide details about the algorithms, key lengths, or whether they meet FIPS 140-2 validation. Without this transparency, it’s tough to confirm compliance with NIST benchmarks, which are essential for meeting HIPAA requirements.
Most vendors use popular services like AWS KMS, Azure Disk Encryption, or Google Cloud’s encryption tools, which typically apply AES-256 encryption by default. For securing data in transit, they often rely on HTTPS/TLS (version 1.2 or higher), VPNs for remote access, and secure email gateways. While these methods cover the basics, they often fall short when examined against the specific needs of the healthcare sector.
Where Vendor Policies Fall Short of Healthcare Requirements
One major issue is that standard encryption practices often ignore critical areas like endpoints, backups, and legacy systems. Another common problem is poor key management - vendors frequently store encryption keys alongside the encrypted data, lack role-based access controls, and fail to rotate keys regularly or document their lifecycle properly. These practices directly clash with the requirements of HIPAA, HITECH, and NIST, all of which demand robust key management and clear separation of duties.
Additionally, encryption efforts are often limited to core data repositories and network transmissions, leaving gaps in protecting ePHI on endpoints, data handled by third-party subprocessors, or data actively being used during processing. Many vendors also fail to address evolving threats, such as the need for quantum-resistant cryptography or the importance of specifying secure cipher suites. This leaves healthcare organizations increasingly exposed as security challenges grow more complex.
Consequences of Non-Compliant Encryption Practices
These technical shortcomings translate into serious regulatory and financial risks for healthcare organizations. Weak encryption practices can lead to HIPAA fines of up to $50,000 per violation, trigger OCR investigations for inadequate risk assessments, and result in the loss of HITECH Safe Harbor protections. Without these protections, organizations are forced to issue breach notifications even for incidents that might otherwise have been exempt.
For example, in the 2023 Change Healthcare breach, inadequate vendor encryption allowed ransomware to access unencrypted PHI backups. This incident impacted a large number of patients and reportedly cost $872 million.
Similarly, failures in endpoint encryption led to OCR settlements exceeding $1 million in 2024. With over 540 healthcare breaches reported last year - and vendor-related issues accounting for roughly 60% of them - the December 2025 enforcement deadline for vendor audits is fast approaching. Healthcare organizations must address these vulnerabilities now to align with compliance standards, protect patient data, and avoid massive financial and reputational fallout.
Vendor Encryption Policies vs. Healthcare Compliance Standards
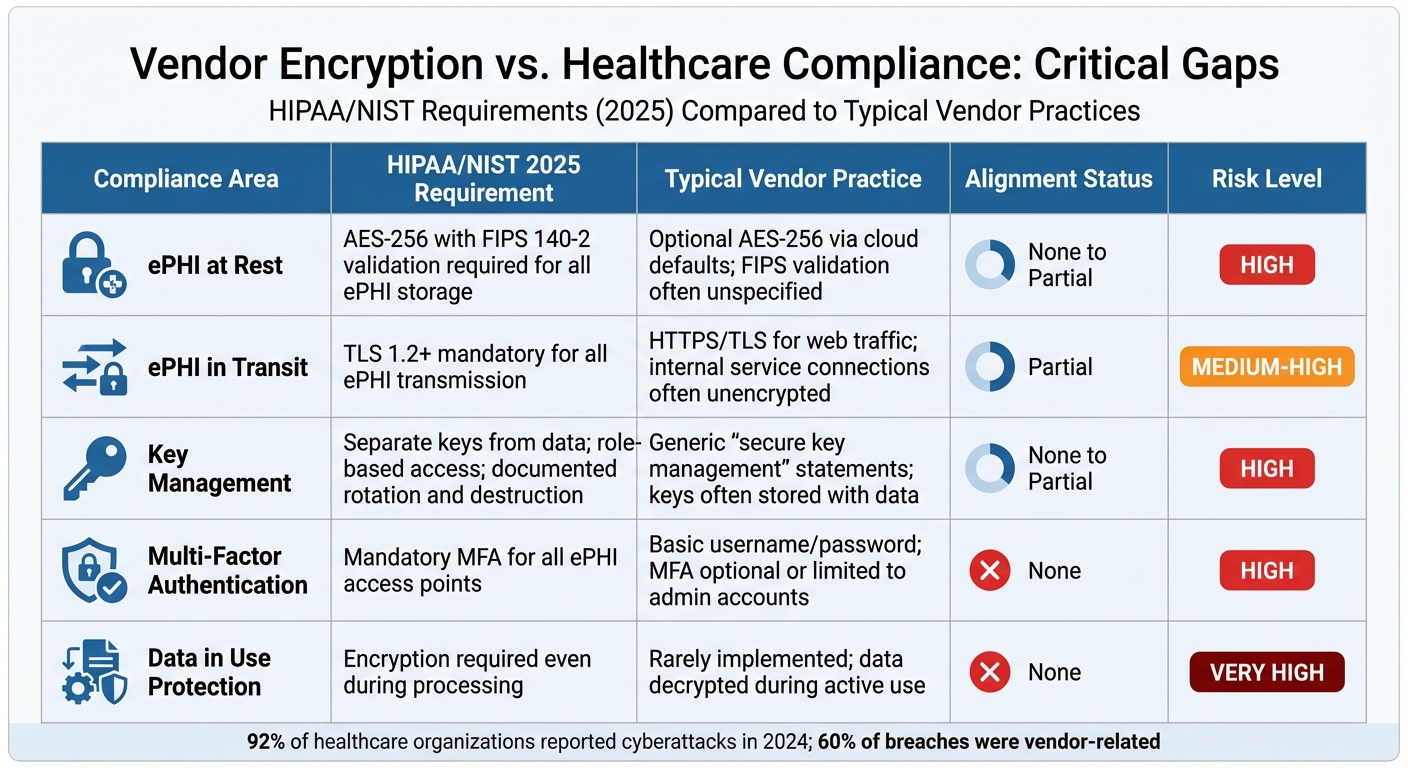
Vendor Encryption Policies vs Healthcare Compliance Requirements 2025
Comparison Table: Alignment and Gaps
When you compare typical vendor encryption policies to the rigorous healthcare requirements coming into play by 2025, the gaps are stark. Vendors often provide basic protections, but healthcare regulations demand far stricter measures to safeguard electronic protected health information (ePHI).
| Compliance Dimension | HIPAA/NIST Requirement (2025) | Typical Vendor Practice | Alignment Status | Risk Level |
|---|---|---|---|---|
| ePHI at Rest | AES-256 with FIPS 140-2 validation required for all ePHI storage [2] | Optional AES-256 via cloud defaults; FIPS validation often unspecified | None to Partial | High – Breach notifications may occur without proper encryption |
| ePHI in Transit | TLS 1.2+ mandatory for all ePHI transmission [2] | HTTPS/TLS for web traffic; internal service connections often unencrypted | Partial | Medium-High – Internal paths may expose ePHI to interception |
| Key Management | Separate keys from data; role-based access; documented rotation and destruction [6] | Generic "secure key management" statements; keys often stored with data | None to Partial | High – Poor key practices undermine encryption |
| Multi-Factor Authentication | Mandatory MFA for all ePHI access points [2] | Basic username/password; MFA optional or limited to admin accounts | None | High – 92% of breached organizations lacked MFA [2] |
| Data in Use Protection | Encryption required even during processing [4] | Rarely implemented; data decrypted during active use | None | Very High – ePHI exposed during processing operations |
These gaps aren’t just theoretical - they represent real risks. Healthcare organizations relying on vendors that fall short in these areas could face steep penalties, including OCR fines up to $50,000 per violation, mandatory breach notifications, and loss of HITECH Safe Harbor protections [3].
Common Misalignments and Their Consequences
The table highlights several key issues, but let’s dig deeper into how these misalignments play out in practice.
One recurring problem is the vague use of terms like "industry-standard encryption." Without specifics - such as confirming AES-256, TLS 1.3, or FIPS-validated modules - healthcare organizations are left unable to pass audits or prove adequate risk management [3].
Another frequent oversight is focusing encryption efforts solely on primary databases while neglecting backups, endpoints, and data-in-use. Under the 2025 HIPAA guidelines, any unencrypted ePHI is labeled as "unsecured", which means even minor incidents could trigger mandatory breach notifications [7].
The lack of multi-factor authentication (MFA) compounds these issues. When vendors rely solely on username/password combinations for APIs and portals, attackers can bypass encryption entirely by stealing credentials.
Key management is another weak point. Vendors that store encryption keys alongside encrypted data or fail to document key rotation and access protocols fall short of both NIST standards and HIPAA’s administrative safeguards [6].
How Vendors Can Better Align with Healthcare Compliance
To close these gaps and meet the stringent demands of healthcare compliance, vendors need to elevate their encryption practices. Healthcare-specific standards can no longer be treated as optional. For example:
- Stronger Encryption: Implement AES-256 with FIPS 140-2 validation for all ePHI at rest and enforce TLS 1.3 for all data in transit - not just for public-facing systems [4].
- Mandatory MFA: Multi-factor authentication must be enforced across all systems that handle ePHI, including portals, APIs, and administrative tools [2].
- Transparent Documentation: Vendors should provide detailed architecture diagrams, key management procedures, SOC 2 Type II reports, and HIPAA Business Associate Agreements that explicitly outline encryption commitments.
As Matt Christensen, Sr. Director GRC at Intermountain Health, explains: "Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare."
Additionally, vendors should embrace continuous monitoring tools like Censinet RiskOps™. These platforms allow for real-time compliance assessments and evidence collection, moving beyond static questionnaires to ongoing verification. This approach aligns with the proactive oversight regulators will expect under the 2025 enforcement priorities [3].
sbb-itb-535baee
How to Close Encryption Gaps in Vendor Relationships
Including Encryption Compliance in Vendor Risk Assessments
Encryption compliance should be a key part of your vendor risk assessments. With the proposed 2025 HIPAA Security Rule updates, encryption is no longer optional - it’s mandatory for all electronic protected health information (ePHI) at rest and in transit [2][3][4]. This means you can’t rely on vague assurances from vendors; you need concrete proof of their technical controls.
Ask vendors to demonstrate their use of AES-256/FIPS encryption and TLS protocols [6][7]. Require detailed documentation on their encryption configurations, key management processes, and multi-factor authentication (MFA) implementations [2][3][9]. Your assessment checklist should also confirm that vendors perform annual technical security assessments, including vulnerability scans every six months, as required by the updated regulations [3][4].
It’s worth noting that the Office for Civil Rights (OCR) doesn’t just penalize organizations for breaches - it also fines those with outdated or insufficient risk assessments [3]. If your assessments uncover gaps, use contractual agreements to enforce improvements.
Negotiating Stronger Encryption Requirements
Your Business Associate Agreements (BAAs), contracts, and service level agreements (SLAs) should include specific encryption mandates. These agreements need to explicitly require compliance with the 2025 HIPAA updates, covering ePHI encryption, MFA implementation, and documented key management practices [2][4][7].
Include technical requirements like HTTPS/TLS for all web applications, VPNs for remote access, encrypted email or secure messaging for PHI, and FIPS-validated encryption modules [6]. SLAs should outline penalties for non-compliance, such as financial repercussions or service termination. Additionally, negotiate terms that require vendors to provide annual compliance audits, network architecture diagrams, asset inventories, and incident response plans aligned with NIST frameworks [3][4]. Consider adding future-proof clauses to address evolving encryption standards.
These contractual obligations should align with the encryption compliance verified during your risk assessments, creating a consistent and enforceable framework.
Using Risk Management Platforms for Vendor Oversight
Vendor oversight doesn’t stop at contracts - it requires ongoing monitoring. Managing this manually with spreadsheets and questionnaires is inefficient, especially given the growing number of third-party relationships and the rapid pace of regulatory updates. Tools like Censinet RiskOps™ can help by automating encryption compliance checks and providing continuous monitoring across your vendor ecosystem.
Censinet RiskOps™ streamlines third-party encryption assessments, ensuring that ePHI is protected at rest and in transit in line with the 2025 HIPAA standards [2][4]. The platform also supports collaborative risk management for clinical applications, medical devices, and supply chains, generating audit-ready reports for OCR compliance while reducing manual effort.
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required." - Terry Grogan, CISO, Tower Health [1]
Switching from annual audits to real-time validation is critical, especially when 92% of healthcare organizations reported at least one cyberattack in the past year, and 69% experienced patient care disruptions as a result [2]. Continuous monitoring platforms can identify encryption gaps early, helping you stay compliant while safeguarding patient safety.
"Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with." - James Case, VP & CISO, Baptist Health [1]
This collaborative approach allows healthcare organizations to share insights, benchmark encryption practices, and address common compliance gaps. It transforms vendor oversight from a tedious task into a strategic advantage.
Conclusion
Key Takeaways
Encryption policies for vendors are not optional - they're a non-negotiable responsibility for healthcare organizations. With the proposed 2025 HIPAA Security Rule updates, encrypting all electronic protected health information (ePHI) at rest and in transit will become mandatory, removing prior flexibility[3]. This means every vendor handling patient data must meet strict encryption standards. If a vendor falls short, your organization remains on the hook for penalties from the Office for Civil Rights (OCR), breach notification expenses, and operational chaos.
The good news? These risks can be managed by weaving encryption into your overall compliance strategy. Strong contracts, structured risk assessments, and continuous monitoring can turn encryption into a powerful safeguard rather than just another requirement. Following NIST-based frameworks and preparing for the 2025 HIPAA updates can demonstrate due diligence and help mitigate liability if something goes wrong.
The stakes are high. Misaligned encryption doesn’t just mean fines - it directly impacts patient care. In fact, 69% of healthcare organizations hit by cyberattacks reported disruptions to patient services[2]. An unsecured database or a telehealth platform without enforced multi-factor authentication (MFA) can grind operations to a halt, delay treatments, and erode patient trust. Encryption is no longer just an IT issue - it’s a board-level priority requiring immediate executive attention.
Next Steps for Healthcare Organizations
-
Take Stock of Your Vendors
Begin by creating a detailed inventory of all vendors handling ePHI. Conduct formal, updated risk assessments with a focus on encryption (for data both at rest and in transit), MFA, key management, and logging. Use HIPAA and NIST benchmarks as your guide. -
Revisit Vendor Agreements
Update contracts to require ePHI encryption, enforce MFA, and mandate documented key management practices. Include regular security assessments and audits as part of these agreements. Establish a vendor security governance committee to monitor risks, approve exceptions, and track remediation efforts with clear timelines and escalation protocols for non-compliance. -
Move to Real-Time Risk Management
Ditch static, spreadsheet-based reviews in favor of continuous, collaborative risk management. Platforms like Censinet RiskOps™ can centralize third-party risk assessments, automate evidence collection for encryption and security controls, and benchmark vendors against HIPAA, HITECH, and NIST-aligned standards. This approach shifts the focus from annual audits to ongoing, real-time security operations.
FAQs
What encryption standards will vendors need to follow to comply with the 2025 HIPAA updates?
To meet the requirements of the 2025 HIPAA updates, vendors need to follow encryption standards outlined in the HIPAA Security Rule and NIST SP 800-53 guidelines. This involves implementing AES-256 encryption for securing data at rest and using TLS 1.2 or higher to protect data while it's being transmitted.
These measures are critical for protecting sensitive healthcare information, such as patient data and PHI. By adopting strong encryption protocols, organizations can significantly lower the chances of breaches and prevent unauthorized access to confidential information.
What steps can healthcare organizations take to ensure their vendors follow proper key management practices?
Healthcare organizations can boost security by ensuring vendors adhere to strict key management practices. This starts with conducting detailed risk assessments and establishing well-defined encryption policies that meet healthcare compliance standards. Adding regular audits and setting up contractual obligations for strong encryption controls further reinforces these efforts.
Tools like Censinet RiskOps™ simplify this process by offering continuous monitoring and benchmarking of vendor security protocols. Working closely with vendors to tackle risks and refine key management strategies adds another layer of protection for sensitive data.
What risks do healthcare organizations face if their vendors don’t comply with encryption standards?
If vendors fall short of meeting encryption compliance standards, healthcare organizations could face severe consequences, including data breaches, legal penalties, and reputational harm. These compliance gaps leave sensitive patient information exposed, making it an easy target for cyberattacks and unauthorized access.
On top of that, failing to comply with regulations like HIPAA can lead to hefty fines, lawsuits, and a significant loss of trust from patients, partners, and stakeholders. Ensuring that vendors stick to encryption standards is critical for safeguarding patient data and staying on the right side of regulatory requirements.
Related Blog Posts
Key Points:
What are vendor encryption policies in healthcare?
Definition: Vendor encryption policies outline the encryption standards and practices that third-party vendors must follow to secure electronic protected health information (ePHI). These policies ensure that data is encrypted during storage and transmission, protecting it from unauthorized access and breaches.
Why is encryption critical for healthcare compliance?
Importance:
- Protects sensitive patient data from breaches and unauthorized access.
- Ensures compliance with regulations like HIPAA, HITECH, and state-specific privacy laws.
- Reduces the risk of reportable breaches by rendering data unreadable to unauthorized parties.
- Builds trust with patients and stakeholders by demonstrating a commitment to data security.
What are the key encryption requirements for healthcare compliance?
Requirements:
- Data at Rest: Use AES-256 encryption to secure stored ePHI.
- Data in Transit: Implement TLS 1.3 or higher to protect data during transmission.
- Key Management: Use hardware security modules (HSMs) for secure key storage and automate key rotation.
- NIST Standards: Adhere to NIST SP 800-111 for data at rest and SP 800-52 for data in transit.
- Access Controls: Enforce role-based access and multi-factor authentication (MFA) for encryption key management.
What challenges exist in implementing vendor encryption policies?
Challenges:
- Key Management: Ensuring secure storage, rotation, and access to encryption keys.
- Legacy Systems: Integrating encryption with older systems that may lack compatibility.
- Vendor Compliance: Monitoring third-party vendors to ensure adherence to encryption policies.
- Costs: Implementing encryption solutions can be resource-intensive, requiring investments in hardware, software, and training.
What are the best practices for vendor encryption policies in healthcare?
Best Practices:
- End-to-End Encryption: Encrypt data from its source to its destination to ensure comprehensive protection.
- Hardware Security Modules (HSMs): Use HSMs for secure key storage and management.
- Regular Audits: Conduct periodic audits of vendor encryption practices to ensure compliance.
- Business Associate Agreements (BAAs): Require vendors to sign BAAs that outline their encryption responsibilities.
- Training and Awareness: Educate staff and vendors on encryption best practices and compliance requirements.
How can healthcare organizations ensure vendor compliance with encryption policies?
Ensuring Compliance:
- Conduct regular risk assessments to evaluate vendor encryption practices.
- Use platforms like Censinet RiskOps™ to monitor encryption compliance in real time.
- Require vendors to provide documentation, such as SOC 2 reports or encryption certifications.
- Establish clear contractual obligations for encryption, including incident reporting and remediation timelines.


