The Compliance Nightmare After a Cloud Outage: Breach Notification, Downtime Reporting, and Regulatory Fallout
Post Summary
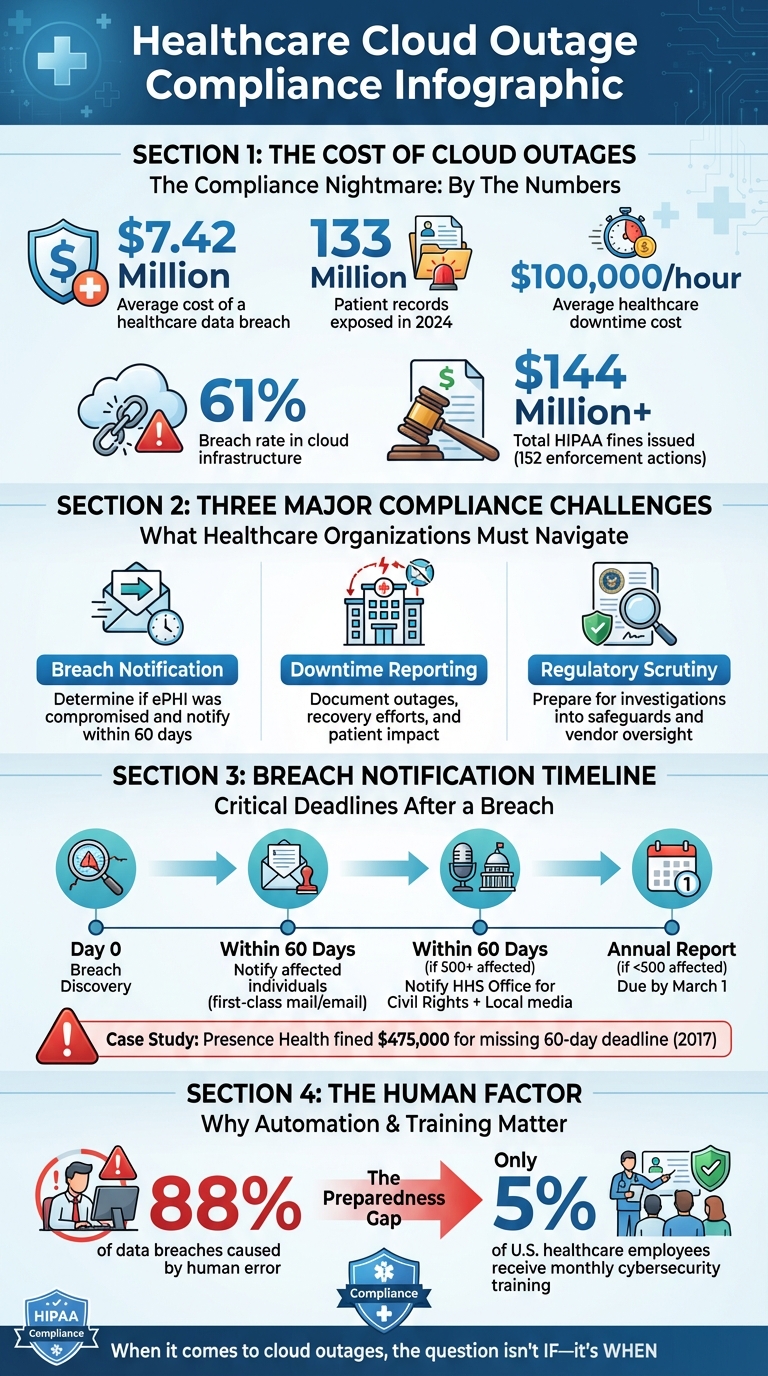
Cloud outages in healthcare are more than just technical problems - they’re compliance minefields. These incidents can lead to breaches of electronic protected health information (ePHI), triggering strict HIPAA rules and potential penalties. The average cost of a healthcare breach is $7.42 million, and with over 133 million patient records exposed in 2024 alone, the risks are only growing.
When systems go down, healthcare organizations face three major challenges:
- Breach Notification: Determining if ePHI was compromised and notifying affected parties within 60 days.
- Downtime Reporting: Documenting system outages, recovery efforts, and patient impact for regulatory compliance.
- Regulatory Scrutiny: Preparing for investigations into safeguards, vendor oversight, and incident handling.
Key steps to manage these risks include conducting thorough risk assessments, maintaining centralized documentation, and leveraging tools like incident tracking systems to streamline compliance efforts. Regular staff training and vendor oversight are also critical to avoid fines and reputational damage.
Cloud outages aren’t a matter of “if” but “when.” Having a clear compliance plan in place can save millions and protect patient trust.
Healthcare Cloud Outage Compliance: Key Statistics and Requirements
Compliance Requirements After a Cloud Outage
When cloud outages occur, they do more than disrupt operations - they activate a series of strict regulatory obligations. For healthcare organizations, these requirements stem from HIPAA mandates, particularly when electronic protected health information (ePHI) is involved. The HIPAA Privacy Rule, Security Rule, and Breach Notification Rule come into play, requiring immediate action and detailed documentation to ensure compliance[2][4].
What Triggers Compliance Requirements During an Outage
Compliance obligations are triggered when an outage compromises the confidentiality, integrity, or availability of ePHI. Under the HIPAA Security Rule, "availability" means data must be accessible and usable on demand by authorized personnel[2][3]. If a cloud outage disrupts access to patient records or interferes with system functionality, it violates this principle.
During such events, healthcare organizations must activate three key compliance mechanisms:
- Risk Analysis and Management: Required under the HIPAA Security Rule to evaluate and address risks[2][3].
- Security Incident Procedures: These outline steps to identify, respond to, mitigate, and document incidents[2][3].
- Breach Notification Requirements: If ePHI is disclosed without authorization, organizations must assess and report the breach within 60 days[5][4].
Some states also enforce downtime reporting if system outages negatively impact patient care.
Recent updates to HIPAA in 2025 have introduced even stricter requirements, including enhanced cybersecurity measures, mandatory risk assessments, and more robust incident response protocols[5][4]. These changes demand that healthcare organizations not only prepare for potential outages but also respond swiftly and effectively when they occur.
Understanding these triggers is essential before diving into breach notifications or documenting downtime. However, putting these protocols into practice often reveals significant challenges.
Common Compliance Obstacles After Cloud Outages
One of the biggest hurdles healthcare organizations face is the lack of visibility into their cloud vendors' systems. When a cloud provider experiences an outage, covered entities often struggle to get real-time information about what happened, which systems were affected, or whether ePHI was compromised. This lack of transparency can delay breach assessments and make it hard to provide accurate incident reports to regulators.
Another challenge is fragmented outage data. Information about the incident is often spread across help desk tickets, vendor communications, system logs, and staff reports. Without a centralized system for documentation, piecing together a complete timeline or assessing the full impact becomes a daunting task. This is especially true when third-party vendors are involved, as accountability can be unclear, further complicating compliance efforts.
Breach Notification Requirements After a Cloud Outage
Determining If an Outage Requires Breach Notification
Not all cloud outages demand breach notifications. Under HIPAA, notifications are only required when an outage compromises the integrity or privacy of ePHI (electronic Protected Health Information). To determine this, healthcare organizations must conduct a risk assessment focusing on four key factors: the nature and extent of the PHI involved, the scope of access, whether the information was actually acquired, and the level of mitigation applied.
HIPAA does outline three specific exceptions where notifications are unnecessary. These include:
- Unintentional access by employees acting in good faith within their job scope.
- Inadvertent disclosures between authorized individuals within the same organization, as long as the information isn't misused.
- Situations where it’s believed, in good faith, that the unauthorized recipient could not retain the information.
However, in the case of cloud outages, these exceptions might not always apply - especially when system-wide issues increase the risk of unauthorized access. Determining whether an outage falls under these criteria is crucial for meeting the notification deadlines outlined below.
Notification Deadlines and Requirements
When a breach is confirmed, healthcare organizations are required to notify affected individuals within 60 days of discovering the breach [6]. Notifications must be in writing, typically sent via first-class mail or email (if the recipient has opted for electronic communication). Failure to meet this deadline can have serious consequences; for instance, Presence Health was fined $475,000 in 2017 for missing the 60-day window [7].
For larger breaches affecting 500 or more individuals, organizations must also notify the HHS Office for Civil Rights and local media outlets serving the impacted area, all within the same 60-day period. Breaches involving fewer than 500 individuals are reported to HHS annually, with reports due by March 1 (or February 29 in leap years) [8]. Notifications must include:
- A summary of the breach.
- Details on the types of information involved.
- Recommended steps for affected individuals.
- Information about the organization’s investigation and mitigation efforts.
- Contact details for further inquiries.
Additionally, organizations must comply with any stricter state-level notification laws that may apply.
Tools and Methods for Faster Breach Notification
Speed is essential when it comes to breach notifications. Pre-designed templates that address all HIPAA requirements can help organizations quickly craft notifications tailored to specific incidents, such as cloud outages or other security breaches.
Centralized incident tracking systems are another valuable tool, consolidating all breach-related information in one place. This is especially helpful when coordinating with business associates, who are also required to notify covered entities promptly.
Automated platforms like Censinet RiskOps™ can significantly speed up the breach determination process. These tools evaluate HIPAA’s four risk factors and document mitigation steps, helping organizations act faster. When paired with continuous monitoring systems that detect potential breaches early, these technologies provide a critical advantage in meeting regulatory deadlines.
Downtime Reporting and Documentation Requirements
While breach notifications focus on data breaches, keeping accurate records of downtime is just as important for maintaining compliance.
Challenges in Tracking and Reporting Downtime
Healthcare organizations often face difficulties in tracking and reporting downtime due to fragmented records spread across clinical systems, cloud infrastructure, and backup processes. This lack of centralization makes it tough to piece together a clear timeline of events. With healthcare systems losing an average of $100,000 per hour of downtime [9], the stakes are high for precise tracking - not just for compliance, but also for business continuity. However, many organizations lack centralized tools to log essential details like timestamps, affected systems, and recovery milestones. Adding to the complexity, different departments may define "downtime" inconsistently, leading to reporting gaps. Without a unified system, it's nearly impossible to meet regulatory standards with accuracy.
What Regulators Expect for Downtime Reporting
Under HIPAA's Security Rule, healthcare organizations are required to document outages, backup protocols, and recovery actions as part of their contingency plans. These audit trails demonstrate accountability and reassure regulators that safeguards were in place to protect electronic protected health information (ePHI) during outages.
Regulatory frameworks like HITECH, HITRUST CSF, and the NIST Cybersecurity Framework emphasize the importance of comprehensive risk management, which includes detailed documentation of outages. On top of federal requirements, state health departments may impose additional reporting obligations, especially when outages impact patient care or safety. Well-maintained documentation not only simplifies audits but also ensures compliance with HIPAA and other regulations [4]. This level of detail is critical for successful audits and post-incident reviews.
Strategies for Effective Downtime Documentation
Using a centralized downtime registry can simplify the documentation process. This system should serve as the single source of truth, capturing every outage with details like timestamps, affected systems, patient impact, and recovery actions. Cloud monitoring tools can further enhance this process by automatically logging system availability, reducing the need for manual data entry.
Solutions like Censinet RiskOps™ offer audit-ready documentation by continuously monitoring cloud infrastructure and automatically collecting evidence of outages and recovery activities [10][12]. These tools create the kind of comprehensive audit trails that regulators expect, helping organizations demonstrate compliance seamlessly during and after cloud-related incidents.
sbb-itb-535baee
Managing Regulatory Investigations and Penalties
When a cloud outage disrupts healthcare operations, being prepared can make all the difference in how regulators respond. Knowing what they look for and how to address their concerns can help mitigate hefty fines and penalties.
What Regulators Examine After a Cloud Outage
Regulators focus on whether the organization had appropriate safeguards in place before the outage. Key areas of scrutiny include:
- Information System Contingency Plan (ISCP): This includes risk management protocols, crisis response strategies, data backup and recovery procedures, business continuity plans, and clearly defined roles and responsibilities [13].
- Business Impact Analysis (BIA): Regulators look for preventative measures, necessary resources, and recovery metrics such as Recovery Point Objective (RPO), Recovery Time Objective (RTO), and Maximum Tolerable Downtime (MTD) [13].
- Technical Security Measures: They assess whether data was encrypted both in transit and at rest, whether Identity and Access Management (IAM) followed least privilege principles, and whether network security, threat detection, and disaster recovery testing were robust.
- Vendor Oversight: This involves ensuring proper due diligence, well-defined Service Level Agreements (SLAs), and consistent monitoring of vendors under the shared responsibility model.
Understanding these focus areas provides a foundation for addressing common compliance gaps.
Compliance Failures Found During Investigations
Investigations often reveal recurring issues that can lead to penalties. These include incomplete risk assessments, poor documentation, weak vendor accountability, insufficient disaster recovery testing, gaps in staff training, and the absence of unified governance frameworks like HITRUST CSF or the NIST Cybersecurity Framework [1].
Steps to Reduce Regulatory Risks
Organizations can take proactive steps to minimize compliance risks and avoid penalties:
- Continuous Monitoring and Audits: Regularly monitor systems and conduct audits to spot vulnerabilities early. Frequent testing of disaster recovery and incident response plans demonstrates preparedness and commitment to business continuity.
- Rigorous Vendor Management: Strengthen vendor oversight by performing thorough due diligence, drafting SLAs with clear uptime guarantees and breach notification requirements, and maintaining ongoing security checks. Tools like Censinet RiskOps™ simplify this process by centralizing third-party risk assessments and automating evidence collection with detailed audit trails.
- Comprehensive Staff Training: Prioritize staff education to ensure every team member understands their role in compliance and data protection. A well-informed team fosters a culture of accountability that regulators value during investigations.
Conclusion: Creating a Compliance Plan for Cloud Outages
Cloud outages aren’t just technical hiccups - they’re compliance nightmares that can cost organizations millions. With downtime racking up an average of $100,000 in losses per hour, being unprepared simply isn’t an option [9]. A well-structured compliance plan transforms potential chaos into a coordinated response, protecting both your systems and your bottom line.
To tackle these challenges, focus your compliance plan on four critical areas: breach identification and notification protocols, systems for tracking and documenting downtime, clear communication processes with regulatory bodies, and measures to ensure vendor accountability. Set specific Recovery Point Objectives (RPO) and Recovery Time Objectives (RTO) for your essential systems, and don’t let these plans gather dust - test them regularly with simulated outages. This isn’t just about satisfying auditors; it’s about having a clear roadmap when systems fail and regulators are at your door.
Centralized tools can simplify your response efforts. For example, platforms like Censinet RiskOps™ use automation to streamline post-incident documentation and maintain detailed audit trails [10][12]. With human error responsible for 88% of data breaches, automation minimizes mistakes when your team is already under pressure [9].
Another key piece of the puzzle? Training. Only 5% of U.S. healthcare employees receive monthly cybersecurity awareness training, even though staff knowledge is critical during compliance emergencies [11]. Regular training ensures everyone knows their role, from IT teams logging downtime to executives managing regulatory communications.
Consider this: the healthcare sector experiences a 61% breach rate in cloud infrastructure, and the Office of Civil Rights has already issued over $144 million in HIPAA-related fines across 152 enforcement actions [11]. A robust compliance plan isn’t a luxury - it’s a necessity. Start with your most critical systems, establish clear protocols, invest in centralized tools, and make training a priority. Because when it comes to cloud outages, the question isn’t if they’ll happen - it’s when.
FAQs
How can healthcare organizations prepare for a cloud outage?
To get ready for a potential cloud outage, start by performing regular risk assessments to pinpoint weak spots in your IT setup. Create a thorough contingency plan that details how to keep operations running during an outage, including strategies for backup systems and recovery processes.
Set up clear communication protocols to quickly inform staff, patients, and partners about any disruptions. Use automated backup and recovery tools to reduce the chances of data loss and keep downtime to a minimum. Additionally, provide ongoing staff training so everyone knows the emergency procedures and can act efficiently when it matters most.
How can healthcare organizations determine if they need to issue a breach notification after a cloud outage?
When determining whether a breach notification is required, healthcare organizations need to conduct a detailed risk assessment. This process includes analyzing the type of protected health information (PHI) involved, assessing if it was accessed or used without proper authorization, and reviewing the steps taken to reduce potential harm. If there's a strong chance that the PHI has been compromised, notification is generally necessary. Acting promptly and keeping thorough documentation of the assessment process is crucial for staying compliant with regulations.
What are the biggest challenges in documenting downtime during a cloud outage?
Documenting downtime during a cloud outage isn’t exactly a walk in the park. You need to pinpoint the exact start and end times, double-check system logs to confirm how long the outage lasted, and consider how interconnected systems might have been affected. On top of all that, ensuring your records align with regulatory reporting standards adds another layer of difficulty.
And here's the kicker: all of this has to be done quickly and accurately to avoid disrupting operations further while staying compliant with healthcare regulations. To tackle this efficiently, having a solid plan, dependable tools, and well-defined processes in place is absolutely critical.


