Cybersecurity at Machine Speed: AI's Role in Real-Time Threat Response
Post Summary
In healthcare, cybersecurity threats like ransomware and phishing are growing more sophisticated, with attackers exploiting vulnerabilities faster than ever. Traditional security tools often fail to keep up, leaving patient data and clinical operations at risk. AI-powered solutions are stepping in to revolutionize threat detection and response by analyzing data, spotting anomalies, and acting in milliseconds. These systems are reducing response times by 70% and detecting threats with 98% accuracy, all while helping organizations comply with strict regulations like HIPAA.
Key Takeaways:
- AI detects and responds to cyber threats 85% faster than older systems.
- Ransomware attacks in healthcare have surged by 40% in the last 90 days.
- AI tools analyze user behavior, email context, and network traffic to prevent breaches.
- Compliance with regulations demands real-time monitoring and transparency in AI systems.
- Human oversight remains essential for critical decisions and maintaining patient care.
AI's integration into healthcare cybersecurity isn't just about speed - it's about staying ahead of attackers while safeguarding sensitive data and ensuring uninterrupted operations. Up next, learn how AI's real-time capabilities are transforming healthcare security.
Healthcare Cyber Threats That Require Machine-Speed Response
Attack Methods Targeting Healthcare Organizations
Healthcare organizations are under constant siege from cyberattacks like ransomware and phishing, which exploit vulnerabilities in their IT systems. Over the past 90 days alone, ransomware attacks have jumped by 40% [3]. These attacks can cripple essential systems. For instance, in September 2020, a ransomware attack on a university hospital in Düsseldorf, Germany, locked critical systems, forcing patients in need of urgent care to be redirected elsewhere [6].
Phishing remains another major threat. Attackers send deceptive emails that trick staff into revealing sensitive information or installing malicious software. Shockingly, 44% of healthcare organizations still rely on outdated, rules-based email security systems [8], leaving them exposed to these types of attacks.
Traditional security tools, like signature-based detection systems, often fail when faced with zero-day exploits or new, unpredictable attack methods [7] [8]. Attackers are increasingly using legitimate system tools to avoid detection. With healthcare IT environments hosting hundreds of interconnected devices and applications, manual monitoring simply can’t keep up. This complexity has led cybercriminals to adopt more advanced techniques, including the use of AI to amplify their attacks.
How Attackers Use AI Against Healthcare
AI is becoming a powerful weapon in the hands of cybercriminals. Generative AI tools allow attackers to create malware that can bypass detection, forge identities, and even produce deepfakes for fraudulent activities [4] [9]. These AI-generated attacks are particularly dangerous because they can mimic human behavior and language with startling accuracy [4].
"Threat actors are automating reconnaissance and launching customized phishing attacks to deploy malware, such as information stealers, that place organizations across industries at risk of cyber-attack." – Deloitte Cyber Threat Intelligence [9]
The use of AI in cyberattacks is expected to grow significantly, with the generative AI cybersecurity market projected to expand nearly tenfold between 2024 and 2034 [4]. Attackers are already using AI to speed up reconnaissance, pinpoint system vulnerabilities, and execute large-scale, personalized phishing campaigns [9]. Complicating matters further, the inner workings of many AI systems - such as large language models and deep learning algorithms - are often opaque, making it difficult to understand how decisions are made or data is processed [6] [8]. This lack of transparency creates opportunities for attackers to exploit or manipulate these systems. The increasing sophistication of these AI-driven tactics underscores the need for both regulatory oversight and real-time threat detection.
Regulations That Require Fast Threat Detection
As cybercriminals use AI to outmaneuver traditional defenses, healthcare organizations face growing regulatory pressure to detect and respond to threats instantly. In the U.S., laws like HIPAA mandate continuous monitoring and real-time incident response capabilities [3]. Similarly, the HITECH Act enforces strict breach notification rules and imposes steep penalties for non-compliance. Failing to detect and report breaches quickly can result in significant fines and legal consequences.
Regulators are also sharpening their focus on AI transparency [10]. Healthcare organizations must not only ensure that their AI systems comply with HIPAA’s "minimum necessary rule" for data handling but also be able to explain how these systems make decisions. AI-powered tools for predictive analytics, behavioral monitoring, and automated threat response are becoming essential - not just for staying ahead of cybercriminals but also for meeting regulatory demands. By shifting from reactive to proactive security measures, healthcare organizations can better protect sensitive data and reduce the administrative burden of compliance [3].
How AI Enables Real-Time Threat Detection and Response
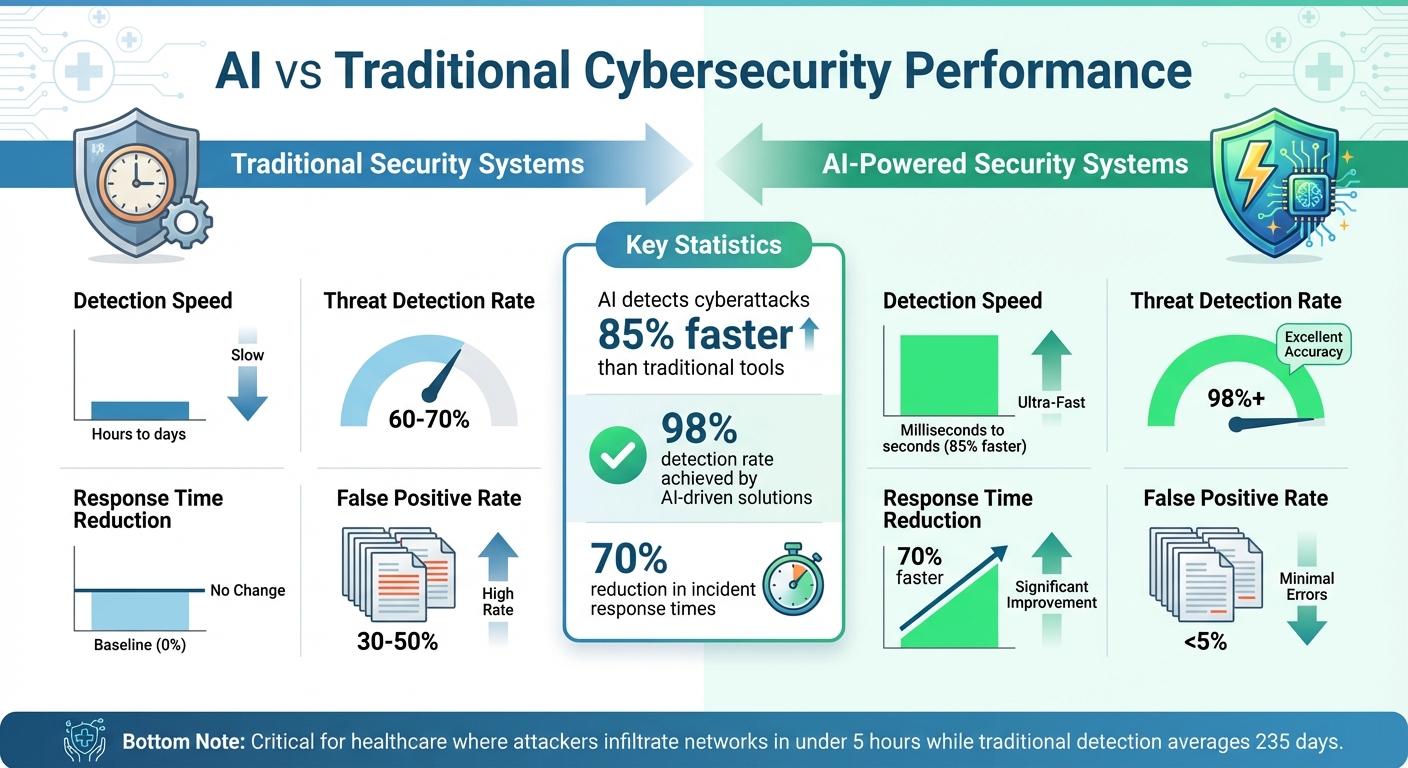
AI vs Traditional Cybersecurity: Speed and Accuracy Comparison in Healthcare
As cyber threats grow more sophisticated, AI has stepped up to provide the rapid, intelligent defenses that healthcare urgently needs to safeguard sensitive data and ensure uninterrupted operations.
AI Detection and Response Technologies
AI plays a pivotal role in healthcare cybersecurity by employing advanced tools that can instantly identify and neutralize threats. Machine learning algorithms analyze network traffic, user behavior, and system logs to detect anomalies, such as unauthorized access to electronic health records (EHRs) [1][11]. Similarly, behavioral analytics creates profiles of typical user activity, flagging suspicious actions like accessing sensitive files late at night or logging in from unusual locations [4][5].
AI-powered Network Intrusion Detection Systems (NIDS) continuously monitor network activity for signs of compromise, while deep learning and natural language processing enhance the system's ability to understand the context and intent behind user actions [4][2]. For email security, AI-driven tools go beyond basic keyword filtering, analyzing tone, metadata, and message context to identify phishing attempts and other threats.
When a threat is detected, autonomous response systems act immediately - no human intervention required. These systems can isolate compromised devices, halt ransomware from spreading, deactivate suspicious accounts, and block unauthorized access attempts [1][11]. This level of automation is particularly critical in healthcare, where swift action can prevent breaches and maintain patient care continuity.
How AI Processes Threats in Milliseconds
AI systems are designed to process vast amounts of real-time data in fractions of a second, leveraging machine learning, deep learning, and anomaly detection [4][1][2].
The advantage of this speed is clear. AI-based threat detection systems identify cyberattacks 85% faster than traditional tools [5], and AI-driven solutions have achieved a 98% detection rate while reducing incident response times by 70% [4]. For example, one Security Operations Center (SOC) that implemented an AI-powered SOAR platform saw response times plummet by 70%. This was made possible because the system automatically correlated logs, enriched alerts with threat intelligence, and initiated response workflows - all without waiting for human input [5].
"AI is now integral in how healthcare cybersecurity systems function. As modeled on the capabilities it ranges from analyzing large data, detecting anomaly, and reacting in real time, which allows for the goal of keeping information about patients safe, and operations stable possible in today's healthcare environment." – Cambridge College of Healthcare & Technology [1]
This ability to act in milliseconds enables AI to contain threats like ransomware before they escalate into major disruptions. For instance, machine learning algorithms have successfully blocked real-time attempts to access patient records without authorization, ensuring data integrity and confidentiality [1].
Matching AI Methods to Healthcare Threats
AI employs a variety of techniques to address specific types of cyberattacks. By aligning the right method with the right threat, healthcare organizations can create stronger, more targeted defenses.
| Healthcare Threat | AI Technique | How It Works |
|---|---|---|
| Ransomware | Behavioral analysis & anomaly detection | Detects unusual file encryption patterns and lateral movement, quarantining systems before ransomware spreads |
| Phishing & spear phishing | Natural language processing & metadata analysis | Analyzes email tone, sender patterns, and metadata to spot impersonation and credential theft attempts |
| Insider threats | User behavior analytics | Flags deviations from normal user activity, like accessing sensitive data at odd hours or downloading large volumes of files |
| Zero-day exploits | Machine learning pattern recognition | Identifies unknown attack signatures by spotting deviations from standard system behavior |
| IoT/medical device attacks | Network monitoring & device behavior profiling | Tracks device communication patterns to detect unauthorized updates or suspicious connections |
| Unauthorized EHR access | Real-time access monitoring & predictive analytics | Monitors access patterns and predicts potential unauthorized attempts based on historical data and user behavior |
This layered approach dramatically improves the speed and precision of threat detection across healthcare systems [2]. With 95% of users reporting that AI-powered cybersecurity enhances prevention, detection, and response efficiency [4], healthcare providers are increasingly turning to these technologies to protect patient data and maintain operational stability. By understanding how these AI methods address specific threats, healthcare organizations can better integrate them into their security strategies.
How to Deploy AI in Healthcare Security Operations
Using AI in healthcare security demands a thoughtful approach to safeguard patient data and ensure clinical operations run smoothly. The goal is to seamlessly integrate AI into existing systems while keeping human oversight at the center for safe and compliant operations.
Connecting AI to Healthcare Security Systems
To make AI effective in healthcare security, it must work hand-in-hand with current systems like firewalls, intrusion detection tools, endpoint protection, and SIEM platforms. This integration can be tricky, especially when dealing with older, legacy systems. AI also needs access to critical data sources - like electronic health records (EHRs), medical devices, network activity logs, and user behavior - to identify potential threats.
Set clear boundaries for automation. Let AI handle straightforward, low-risk tasks, while more sensitive, high-risk decisions should alert human analysts. Rather than acting independently in critical areas, AI should enhance human decision-making by offering detailed, context-rich threat intelligence. This ensures that automated actions align with clinical safety standards and don’t inadvertently disrupt patient care.
Governance and Risk Management for AI Systems
Once AI is integrated, strong governance becomes the backbone of its deployment. Before rolling out AI in live environments, establish governance frameworks to ensure responsible use. Validate AI models with healthcare-specific data to confirm accuracy, monitor for changes in threat patterns (known as model drift), and comply with regulations like HIPAA, HITECH, and ACA §1557, which address bias in patient care tools. Transparency is essential to maintain compliance and build trust.
Regular audits are a must. They help catch false positives that waste time or false negatives that could overlook real threats. Documenting every AI action and decision is equally important for compliance reviews and incident investigations. Given the value of healthcare data on the dark web, these governance practices act as critical safeguards[12].
Keeping Humans in the Decision Loop
Even with strong governance, human oversight remains vital for operational safety. In situations where decisions could impact life-or-death scenarios or disrupt essential healthcare functions, human judgment is irreplaceable[11]. AI alerts should provide analysts with detailed context - not just that a threat exists, but why it was flagged, which systems are affected, and what patient care operations might be at risk.
For complex or unclear threats, human intervention is key. For instance, AI might automatically isolate a workstation showing ransomware activity, but a human should decide whether to disconnect a critical server during peak clinic hours. Training cybersecurity teams in both AI and healthcare operations fosters a collaborative approach where AI and humans work together effectively. This balance accelerates response times while preserving the nuanced judgment needed to protect both data and patient safety[11].
sbb-itb-535baee
How Censinet Enables Machine-Speed Risk Management

With the rise of AI-driven threat detection, healthcare organizations face increasing pressure to manage cybersecurity risks just as swiftly. These risks span across a vast network of vendors, devices, and applications, all while safeguarding patient safety and adhering to strict regulations. Traditional methods - like annual assessments and manual reviews - simply can't keep up with today's ever-changing threat environment. Enter Censinet, a platform that combines centralized risk operations through Censinet RiskOps™ and automated workflows via Censinet AI™, transforming risk management into a seamless, high-speed process.
Managing Third-Party and Supply Chain Risks
Healthcare organizations rely on a wide range of vendors, from electronic health record systems to medical device manufacturers. However, these partnerships can introduce vulnerabilities. Censinet RiskOps™ addresses this by enabling continuous, automated monitoring of vendor and supply chain risks. The platform keeps tabs on vendor security postures, flags new risks as they arise, and updates assessments in real time. This ensures organizations have an up-to-date view of their vendor ecosystem's security landscape. It even goes a step further by identifying risks within a vendor's own network of partners, offering a deeper understanding of potential supply chain exposures.
Censinet RiskOps™: A Centralized Approach to Cyber Risk Management

Censinet RiskOps™ acts as a centralized hub for overseeing both third-party and internal risks. By consolidating risk data, workflows, and mitigation efforts into a single platform, healthcare organizations can streamline their processes and respond to threats faster. This unified approach eliminates the inefficiencies of fragmented systems, giving security teams a clear, real-time view of vulnerabilities across their operations. It also helps prioritize threats based on their potential impact on patient care. Additionally, the platform routes critical findings to the right stakeholders, including members of AI governance committees, ensuring that high-priority issues are addressed without delay.
Censinet AI™: Accelerating Risk Mitigation
Speed is critical when it comes to identifying and addressing risks, and Censinet AI™ takes this to the next level by automating key tasks. What once took days or weeks - like completing risk assessments - can now be done in seconds. Vendors can quickly fill out security questionnaires, while Censinet AI™ compiles and summarizes evidence, documentation, and potential risks, including those from fourth-party connections. This automation allows risk teams to focus on more complex tasks, like analyzing flagged issues or drafting remediation plans. For example, if a vendor's encryption practices are flagged as non-compliant, a human analyst can review the context, validate the findings, and approve the necessary steps to resolve the issue. This balance between automation and human oversight ensures risks are managed efficiently without compromising the careful attention required to protect patient safety.
Building Your Machine-Speed Cybersecurity Program
Expanding on how AI can rapidly respond to threats, this section provides a practical guide to transitioning your security operations toward AI-driven solutions. Shifting from manual methods to automated, AI-enabled threat response requires a well-thought-out plan that considers your current systems, regulatory obligations, and operational challenges. The objective is to move step by step from basic security measures to advanced, automated capabilities.
Steps to Machine-Speed Cybersecurity
Begin by evaluating your current security maturity. Many healthcare organizations rely on manual processes, such as spreadsheets for vendor assessments, occasional vulnerability scans, and reactive responses to incidents. The first step is integrating AI into your Security Operations Center (SOC). This involves deploying AI-powered tools to analyze network traffic, monitor user behavior, and detect anomalies. Make sure your team is trained to interpret and act on AI-generated insights.
The next step is to shift from reactive to proactive security. AI can predict potential threats by analyzing patterns across your network, vendor operations, and threat intelligence feeds [6]. This predictive capability allows you to prevent incidents instead of merely reacting to them, turning security into a proactive safeguard.
Throughout this process, it’s crucial to balance automation with human expertise. AI should manage tasks like continuous monitoring, anomaly detection, and filtering low-risk alerts. Meanwhile, human analysts should focus on complex threats, providing context, and making critical decisions [4][5]. To ensure effectiveness, train AI models with high-quality, unbiased data to minimize false alarms or missed threats, especially when diverse patient populations are involved [11]. Additionally, include strategies for managing emerging AI risks within your clinical risk frameworks.
These steps lay the groundwork for a cybersecurity program tailored to meet the unique challenges of the U.S. healthcare sector.
U.S. Healthcare System Considerations
The U.S. healthcare system faces specific challenges that influence how AI-driven cybersecurity can be implemented. Budget constraints, driven by reimbursement pressures, often limit security spending. However, healthcare providers using AI have reported average savings of $1.9 million [4], making a compelling financial case for adoption.
Healthcare operates around the clock, meaning security systems must function continuously without downtime for updates or maintenance. AI-powered systems excel here, detecting threats 85% faster than traditional tools [5] and achieving a 98% detection rate while reducing response times by 70% in high-risk environments [4]. This level of vigilance aligns with the nonstop nature of patient care.
Regulatory compliance adds another layer of complexity. U.S. healthcare organizations must navigate HIPAA, state privacy laws, FDA rules for medical devices, and new cybersecurity goals set by HHS. Transparency and explainability in AI-driven decisions are vital for building trust with regulators and meeting compliance requirements [11]. Federated learning - a method where AI models are trained across multiple locations without sharing sensitive data - can help ensure compliance while reducing data exposure risks [4].
With these operational factors in mind, tracking your progress becomes essential.
Metrics for Measuring Progress
To evaluate your cybersecurity program’s effectiveness, monitor specific metrics that reflect maturity and improvement over time.
- Detection speed: Measure how quickly your systems identify threats, aiming to shorten this from hours or days to minutes or seconds.
- False positive rates: Track how accurately your AI distinguishes real threats from benign anomalies. Lower rates mean your team spends less time on false alarms.
- Incident response time: Assess how long it takes to contain and resolve a threat after detection.
- Threat detection accuracy: Evaluate the percentage of actual threats your system identifies. In high-risk environments, AI systems have reached 98% accuracy [4], providing a benchmark for healthcare organizations.
- Cost savings: Calculate savings from avoided breaches, reduced manual efforts, and faster response times, offering tangible proof of your program’s value.
| Maturity Level | Detection Speed | False Positive Rate | Threat Detection Accuracy | Response Time |
|---|---|---|---|---|
| Basic | Hours to days | 30-50% | 60-70% | Days to weeks |
| Intermediate | Minutes to hours | 15-30% | 75-85% | Hours to days |
| Advanced | Seconds to minutes | 5-15% | 90-98% | Minutes to hours |
| Machine-Speed | Milliseconds to seconds | <5% | 98%+ | Seconds to minutes |
Review these metrics quarterly to spot trends and refine your strategy. With the market for generative AI in cybersecurity projected to grow nearly tenfold between 2024 and 2034 [4], keeping up with advancements will be critical to maintaining a strong security posture.
Conclusion: AI-Powered Cybersecurity for Healthcare
Healthcare cybersecurity is under immense pressure, with attackers infiltrating networks in under five hours while detections lag behind, averaging an alarming 235 days [13]. This delay puts patient safety, data integrity, and operational stability at serious risk.
AI offers a game-changing advantage by enabling real-time threat detection and response in mere milliseconds. Current AI-powered cybersecurity systems boast over 99% accuracy in identifying intrusions, malware, and phishing attempts [13]. These tools can detect ransomware as it begins, flag unauthorized access to patient records before data is compromised, and automatically contain threats to prevent further network damage. While these advancements are impressive, human oversight remains crucial to ensure effective decision-making and strategic guidance.
"AI is rapidly changing cybersecurity... It has important benefits for defenses. There is an eternal battle of attackers using AI versus the defenders of AI."
- Benoit Desjardins, Cybersecurity Expert, Professor of Radiology at the University of Montreal, CMIO at CHUM [13]
AI's constant monitoring is only part of the solution. Cybersecurity professionals bring essential context to alerts, making sense of complex situations and steering critical decisions. Together, AI and human expertise form a powerful defense against evolving threats.
To build a robust, machine-speed cybersecurity program, organizations need a well-thought-out strategy. This includes evaluating current systems, integrating AI into Security Operations Centers (SOCs), addressing third-party risks, and tracking measurable outcomes. With ransomware attacks in healthcare surging by 40% over the past 90 days [3], the urgency for AI-driven solutions is undeniable. Healthcare providers that adopt these technologies are better equipped to protect patient care, meet compliance requirements, and navigate an increasingly hostile threat environment with confidence.
FAQs
How does AI enhance real-time threat detection and response in healthcare cybersecurity?
AI is transforming how healthcare organizations handle real-time threat detection and response. It can swiftly sift through massive datasets to spot patterns, anomalies, or suspicious activities that might signal a security threat. Unlike manual processes, AI works at lightning speed, delivering quicker and more precise results while cutting down on false alarms.
By automating responses to potential threats, AI helps reduce risks before they escalate. This proactive approach is especially crucial in healthcare, where safeguarding sensitive patient information and adhering to strict regulatory requirements are non-negotiable priorities.
Why is human oversight important in AI-powered cybersecurity systems?
Human involvement plays a crucial role in AI-driven cybersecurity systems, ensuring that automated threat detection and response mechanisms are accurate, ethical, and compliant with regulations. While AI is excellent at analyzing massive datasets and spotting potential threats, it’s human expertise that validates alerts, deciphers complex situations, and makes key decisions in uncertain scenarios.
Blending the speed and efficiency of AI with human judgment allows organizations to minimize false positives, tackle more intricate threats, and handle sensitive information responsibly. This collaboration creates a more dependable and context-sensitive strategy for managing cybersecurity risks.
How does AI help healthcare organizations meet HIPAA compliance requirements?
AI tools play a crucial role in helping healthcare organizations maintain HIPAA compliance by automating essential processes that bolster security and simplify regulatory requirements. These tools are designed to monitor systems continuously, identifying potential risks and preventing unauthorized access to sensitive data, ensuring it stays secure.
They also ensure compliance by applying data encryption standards, creating detailed audit logs for thorough reporting, and enabling proactive threat detection to ward off breaches. By handling these complex tasks automatically, AI not only reinforces security and compliance but also alleviates the administrative workload for healthcare teams, giving them more time to concentrate on patient care.


