HIPAA Rules for Supply Chain Vendors
Post Summary
Healthcare organizations rely on vendors like IT providers, billing services, and medical suppliers to manage patient data. These vendors, classified as business associates under HIPAA, must meet strict rules to protect sensitive information. Non-compliance can lead to steep fines, lawsuits, and mandatory corrective actions. Here’s what you need to know:
- Who’s Covered: Any vendor handling Protected Health Information (PHI) or electronic PHI (ePHI), including cloud services, billing firms, and logistics providers.
- Key Rules: Vendors must follow the Privacy Rule, Security Rule, and Breach Notification Rule to safeguard data and report breaches.
- Common Issues: Missing Business Associate Agreements (BAAs), outdated risk assessments, and failure to monitor vendor compliance.
- Solutions: Maintain a detailed vendor inventory, update BAAs regularly, conduct ongoing risk assessments, and use technology to streamline oversight.
With vendors increasingly digitizing operations, HIPAA compliance is more complex but essential for protecting patient data and avoiding penalties.
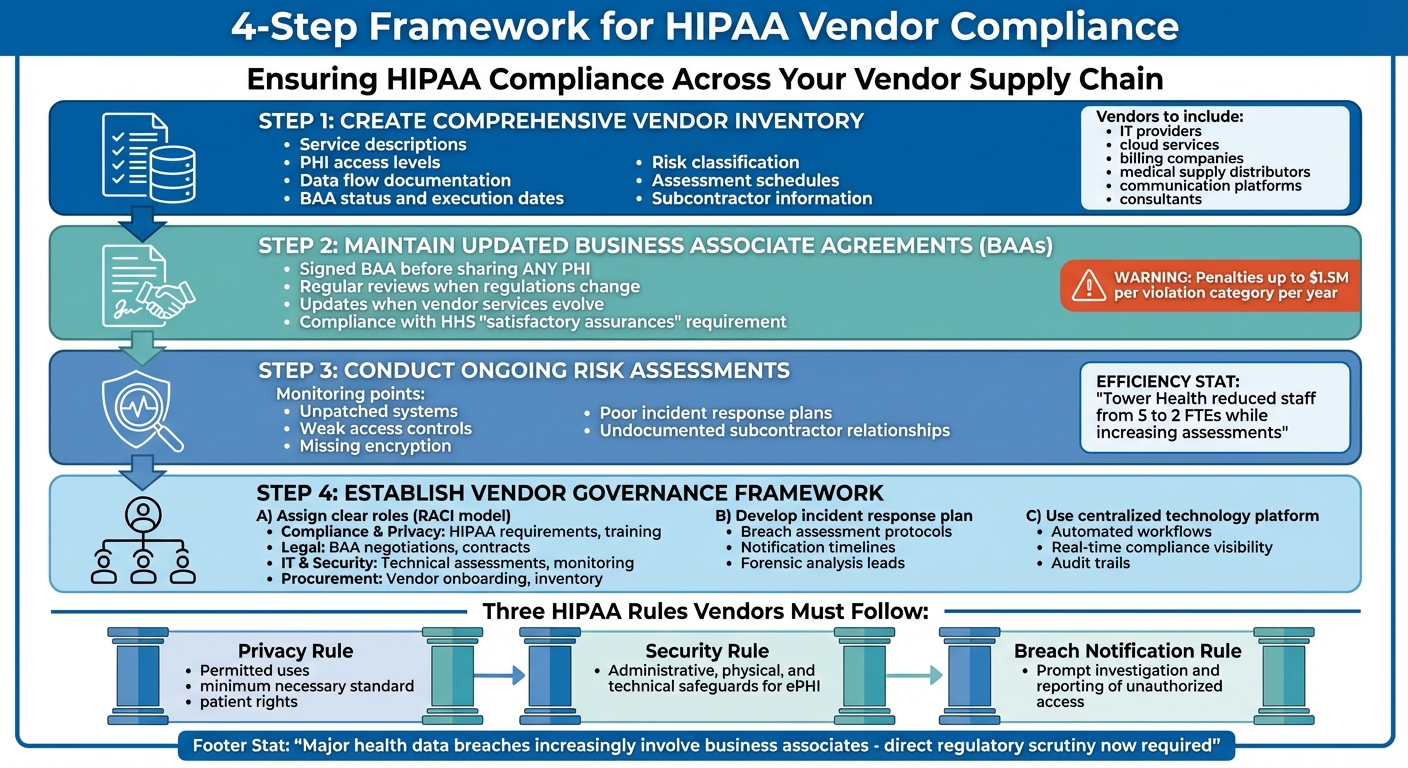
4-Step Framework for HIPAA Vendor Compliance in Healthcare
HIPAA Requirements That Apply to Supply Chain Vendors
Understanding the risks tied to supply chain vendors, it’s essential to outline the specific HIPAA requirements they must follow.
Which Supply Chain Vendors Must Follow HIPAA
Any vendor that handles PHI (Protected Health Information) or ePHI (electronic PHI) for healthcare organizations qualifies as a business associate under HIPAA [4]. This designation includes a wide range of supply chain partners.
Examples of such vendors include IT hosting providers, billing and collections agencies, cloud storage providers, EDI clearinghouses, and patient communication platforms [5][2][7]. Even medical supply distributors fall under HIPAA regulations if they process PHI through order systems or logistics platforms linked to identifiable patient records [7]. Vendors that store encrypted data are also covered if they manage or transmit ePHI [2].
The Department of Health and Human Services (HHS) holds business associates directly accountable for HIPAA compliance, beyond any contractual obligations with covered entities [4]. Additionally, subcontractors working for business associates must adhere to the same rules and secure their own Business Associate Agreements (BAAs) [2][4].
HIPAA Rules Vendors Must Follow
Business associates are required to comply with three main HIPAA regulations: the Privacy Rule, Security Rule, and Breach Notification Rule [2][8][4].
- The Security Rule mandates that vendors implement safeguards - administrative, physical, and technical - to protect ePHI. This includes conducting risk analyses, using role-based access controls, maintaining audit logs, encrypting data, and securing physical facilities [2][7][8].
- The Privacy Rule applies to vendors with access to PHI. These vendors must enforce policies on permitted uses and disclosures, follow the minimum necessary standard, restrict PHI marketing or sales, and support patients' rights via their covered entity partners [2][8].
- The Breach Notification Rule requires vendors to promptly investigate and report any unauthorized access, use, or disclosure of PHI to covered entities [2][7][4].
For instance, an EDI clearinghouse that processes full claim data must comply with the Security Rule, implement Privacy Rule policies (like workforce access controls and minimum necessary standards), and establish breach investigation protocols [2]. On the other hand, a cloud storage provider with no-view access - storing only encrypted PHI while the covered entity retains the keys - must still meet Security Rule requirements, such as securing data centers and monitoring for incidents, though its Privacy Rule obligations are more limited [2][7]. Both types of vendors are classified as business associates, but their compliance measures vary based on their access and risk exposure [5][2].
These rules have led to increased regulatory oversight, significantly influencing compliance practices in recent years.
2025 Changes to HIPAA Vendor Requirements
While no new HIPAA regulations have been introduced for 2025, there’s growing regulatory focus on vendor compliance. A significant number of major health data breaches reported to the HHS Office for Civil Rights (OCR) involve business associates, such as cloud providers, billing firms, and other vendors managing PHI [4]. OCR investigations often highlight missing or inadequate BAAs and poor vendor oversight as key factors in multimillion-dollar settlements and corrective action plans [4][9].
HHS has reinforced that business associates are independently liable for investigations, penalties, and corrective actions - not just their covered-entity clients [4]. This shift has placed vendors under direct regulatory scrutiny, requiring them to establish comprehensive compliance programs. The rise of cloud services, SaaS platforms, and telehealth tools has expanded the number of business associates, making HIPAA compliance more complex across the supply chain [5][2].
Additionally, medical supply and distribution companies are increasingly digitizing their processes and integrating with electronic health record (EHR) systems. This trend brings more logistics and distribution vendors under HIPAA when they handle PHI [6][7]. Leading healthcare organizations are adjusting their procurement strategies to address these compliance challenges. For example, UCSF’s supply chain team uses purchasing forms that flag any vendor involving identifiable patient data as HIPAA-related, triggering privacy and IT security reviews before finalizing contracts [10]. These evolving expectations are shaping how vendors and healthcare organizations approach compliance and governance, as explored in the following sections.
Common Problems with Vendor HIPAA Compliance
Even with clear regulations in place, healthcare organizations often grapple with managing vendor HIPAA compliance effectively. These challenges can leave critical gaps in oversight, increasing the chances of breaches and regulatory actions.
Difficulty Identifying All Vendors That Handle PHI
One major hurdle is pinpointing every vendor that deals with Protected Health Information (PHI). Vendor relationships often extend across IT, procurement, clinical operations, billing, and facilities. Many of these connections are tied to legacy systems or informal contracts, creating blind spots. This makes it tough to track both direct and indirect PHI exposures through services like support systems, backup solutions, analytics platforms, and offshore centers [3][11].
Commonly overlooked vendors include IT managed service providers, cloud storage companies, niche clinical applications, revenue cycle management firms, medical device connectivity services, and subcontractors. Without a detailed inventory of these vendors, organizations risk noncompliance and increased liability during regulatory audits.
The Department of Health and Human Services (HHS) mandates that covered entities secure "satisfactory assurances" - typically through a Business Associate Agreement (BAA) - before engaging vendors that handle PHI [2][8]. Failing to obtain these assurances can result in HIPAA violations, even if no breach occurs. This challenge in identifying vendors often leads to broader issues with BAAs and risk assessments down the line.
Outdated or Missing Business Associate Agreements
Another common issue is the presence of outdated, incomplete, or entirely missing BAAs, coupled with irregular risk assessments. Some vendors may not even realize they qualify as business associates, delaying the adoption of required HIPAA policies until prompted by the healthcare organization [2][5][7].
When BAAs lack critical elements - such as security provisions or breach notification timelines - organizations expose themselves to regulatory penalties, corrective action plans, and potentially costly settlements in the event of a breach. These gaps also complicate efforts to conduct thorough and effective risk assessments.
Lack of Ongoing Vendor Risk Assessment
Many healthcare organizations fall short when it comes to maintaining continuous vendor risk assessments. While initial evaluations might occur during contract signing, they often become outdated as vendors update their infrastructure, experience staff changes, or face new security threats. Static, manual assessments simply can't keep up [1].
Resource limitations often make this problem worse. Terry Grogan, CISO at Tower Health, highlighted the value of automating risk assessments:
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required" [1].
Without ongoing monitoring, organizations risk missing critical issues like unpatched systems, weak access controls, missing encryption, poor incident response plans, or undocumented subcontractor relationships. These gaps not only compromise compliance but also heighten the risk of breaches.
How to Ensure Vendor HIPAA Compliance
Tackling the challenges of vendor HIPAA compliance requires a clear and actionable plan. By focusing on three key practices - maintaining a detailed vendor inventory, keeping Business Associate Agreements (BAAs) up to date, and using technology for continuous monitoring - you can significantly reduce the risks tied to vendor compliance.
Create a Comprehensive Vendor Inventory
Start by creating a centralized list of all vendors and subcontractors your organization works with. This should include IT providers, cloud services, billing companies, medical supply distributors, communication platforms, and consultants[3]. A centralized inventory helps eliminate knowledge gaps across departments like IT, procurement, clinical operations, and facilities.
For each vendor, document their role in handling Protected Health Information (PHI), how data flows through their systems, their hosting locations, and any subcontractor relationships. This allows you to classify vendors by risk level. High-risk vendors - those with extensive PHI access or critical system roles - need more frequent assessments and tighter oversight compared to low-risk vendors who deal with physical goods and no patient identifiers[6][7].
Some key details to include in your inventory are:
- Service descriptions
- PHI access levels
- Data flow documentation
- BAA status and execution dates
- Risk classification
- Assessment schedules
- Subcontractor information
Maintaining this level of detail not only helps manage risks but also meets the Department of Health and Human Services (HHS) requirement to secure "satisfactory assurances" before sharing PHI with third parties[2][4].
Keep Business Associate Agreements Updated
Before sharing any PHI with vendors or subcontractors, ensure a signed BAA is in place[2][3][4]. These agreements must be reviewed and updated regularly, especially when regulations change, vendor services evolve, or their access to PHI increases. Failure to maintain current BAAs has led to significant penalties from the Office for Civil Rights (OCR), with fines reaching up to $1.5 million per violation category per year[7][9].
Using technology can simplify and automate the process of managing and updating BAAs, ensuring nothing falls through the cracks.
Leverage Technology for Risk Assessment and Monitoring
Once your vendor inventory and BAAs are up to date, technology becomes essential for ongoing oversight. Relying on manual processes, like spreadsheets, can quickly become outdated as risks and threats evolve. Tools such as Censinet RiskOps™ allow healthcare organizations to efficiently manage vendor inventories, monitor PHI access and risk levels, automate evidence collection, and continuously track compliance[1].
To measure the success of your vendor compliance program, track performance metrics such as:
- The percentage of vendors with documented PHI data-flow mapping
- The percentage of relevant vendors with current, signed BAAs
- Time taken to complete vendor risk assessments
- The percentage of high-risk vendors reassessed within defined intervals (e.g., annually)
- Average time to address high-severity issues
- The number and severity of vendor-related security incidents each year
These metrics not only highlight areas for improvement but also provide valuable evidence of compliance during audits. Continuous monitoring and proactive risk management are crucial for staying ahead of potential issues.
sbb-itb-535baee
Building a Vendor Governance Framework
Once you’ve updated your vendor inventory, signed BAAs, and set up monitoring tools, the next step is creating a formal governance framework. This framework ensures accountability, defines incident response protocols, and centralizes oversight with the help of technology. It ties all your compliance efforts together, making vendor oversight more structured and responsive.
Assign Clear Roles and Responsibilities
HIPAA requires covered entities to establish policies and procedures for managing business associates, including workforce sanctions for non-compliance [2][4]. Start by appointing a Vendor Risk Owner or forming a dedicated committee. This group, typically reporting to Compliance, Risk, or the CISO, will oversee vendor governance. These assignments work hand-in-hand with your vendor inventory and risk assessments to create a unified compliance approach. Use the RACI model (Responsible, Accountable, Consulted, Informed) to clarify responsibilities across departments:
- Compliance and Privacy teams: Manage HIPAA requirements, training programs, sanctions policies, and policy updates.
- Legal: Handle BAA negotiations, contract reviews, and provide regulatory guidance.
- IT and Security: Conduct technical assessments, monitor vulnerabilities, and investigate incidents.
- Procurement and Supply Chain: Manage vendor onboarding, track spending, and maintain the vendor inventory [2][3][4].
Document these roles, get approval from your compliance committee, and review them annually to keep them aligned with organizational changes.
Develop an Incident Response Plan for Vendor Breaches
If a vendor experiences a data breach, your organization must act quickly to assess the situation, investigate, and determine if HIPAA breach notifications are necessary. Establish a clear plan that outlines responsibilities, assigns leads for forensic analysis and PHI risk evaluations, and sets notification timelines in BAAs to comply with HIPAA requirements [8]. Specify who will handle forensic analysis, assess risks to PHI, draft and send notifications to affected individuals, and liaise with HHS or state regulators. Include flow-down clauses in contracts to ensure subcontractors follow the same protocols [2][3]. Regularly test this plan with tabletop exercises to ensure readiness.
Centralized technology can make managing these processes more efficient and less prone to error.
Use a Centralized Platform for Vendor Governance
Relying on spreadsheets and email for vendor oversight can quickly spiral out of control as the number of vendor relationships grows. A centralized platform, like Censinet RiskOps™, offers a healthcare-specific, cloud-based solution to streamline vendor governance. It centralizes documentation, automates workflows, and provides real-time compliance visibility [1]. Features include audit trails, automated evidence collection, BAA renewal reminders, and routing critical findings to the right stakeholders for review.
"Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with."
- James Case, VP & CISO, Baptist Health [1]
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare."
- Matt Christensen, Sr. Director GRC at Intermountain Health [1]
Conclusion
Key Takeaways for Healthcare Organizations
Staying compliant with HIPAA boils down to four essential actions: keeping an updated vendor inventory, securing legally sound Business Associate Agreements (BAAs) with all business associates, performing ongoing risk monitoring, and establishing clear governance with defined roles and an incident response plan [2][3][4][7][8].
The data from the Office for Civil Rights (OCR) paints a stark picture: vendor-related breaches can compromise hundreds of thousands - or even millions - of patient records in one incident. On top of that, business associates are now directly accountable under HIPAA, not just bound by contracts [4][9]. Organizations that skip regular risk assessments often find themselves in trouble, facing enforcement actions and avoidable breaches [7].
How Technology Simplifies Vendor Compliance
While these core practices lay the groundwork, technology can make compliance much more manageable. As vendor networks grow, relying on spreadsheets, email chains, and disconnected tools becomes chaotic. Purpose-built platforms offer a way out of this complexity. For example, Censinet RiskOps™ centralizes vendor documentation, automates risk assessments, keeps track of BAA renewals, and ensures critical findings are routed to the right people in real time [1].
This platform also connects healthcare organizations with over 50,000 vendors, creating a collaborative risk network that supports secure data sharing and cybersecurity benchmarking [1].
The results speak for themselves. Tower Health, for instance, cut the full-time staff needed for risk assessments from five to two while increasing the number of assessments completed [1]. This kind of efficiency underscores how technology can transform compliance efforts into something both effective and scalable.
FAQs
How can supply chain vendors comply with HIPAA regulations?
To align with HIPAA regulations, supply chain vendors need to prioritize patient data protection and actively address any risks that might arise. Here’s how they can stay on track:
- Perform frequent risk assessments to spot and address any weak points in their systems.
- Put strong data protection measures in place to keep sensitive information secure.
- Use advanced tools, like risk management platforms, to simplify compliance efforts and bolster cybersecurity.
Focusing on these steps helps vendors meet HIPAA standards while fostering trust with healthcare organizations.
What are the HIPAA requirements for vendors that store encrypted PHI?
Vendors handling encrypted Protected Health Information (PHI) must still meet all HIPAA requirements. While encryption helps lower risks, it doesn’t waive the need for strong safeguards and strict access controls. Compliance with the HIPAA Security Rule is mandatory, covering the confidentiality, integrity, and availability of PHI.
To stay compliant, vendors should routinely evaluate their security measures, ensuring they align with HIPAA's data protection standards and effectively address potential risks.
What happens if a supply chain vendor doesn’t follow HIPAA regulations?
Failure to follow HIPAA regulations can result in severe repercussions for supply chain vendors. These consequences might include steep fines, legal proceedings, and a tarnished reputation. Vendors could also find themselves under closer scrutiny from healthcare organizations, potentially jeopardizing crucial business relationships.
Beyond financial and legal risks, non-compliance can disrupt daily operations and erode trust with healthcare partners. In an industry where protecting patient data and adhering to compliance standards are non-negotiable, these breaches can have lasting impacts.


