How HITRUST Certification Reduces Cloud Vendor Risks
Post Summary
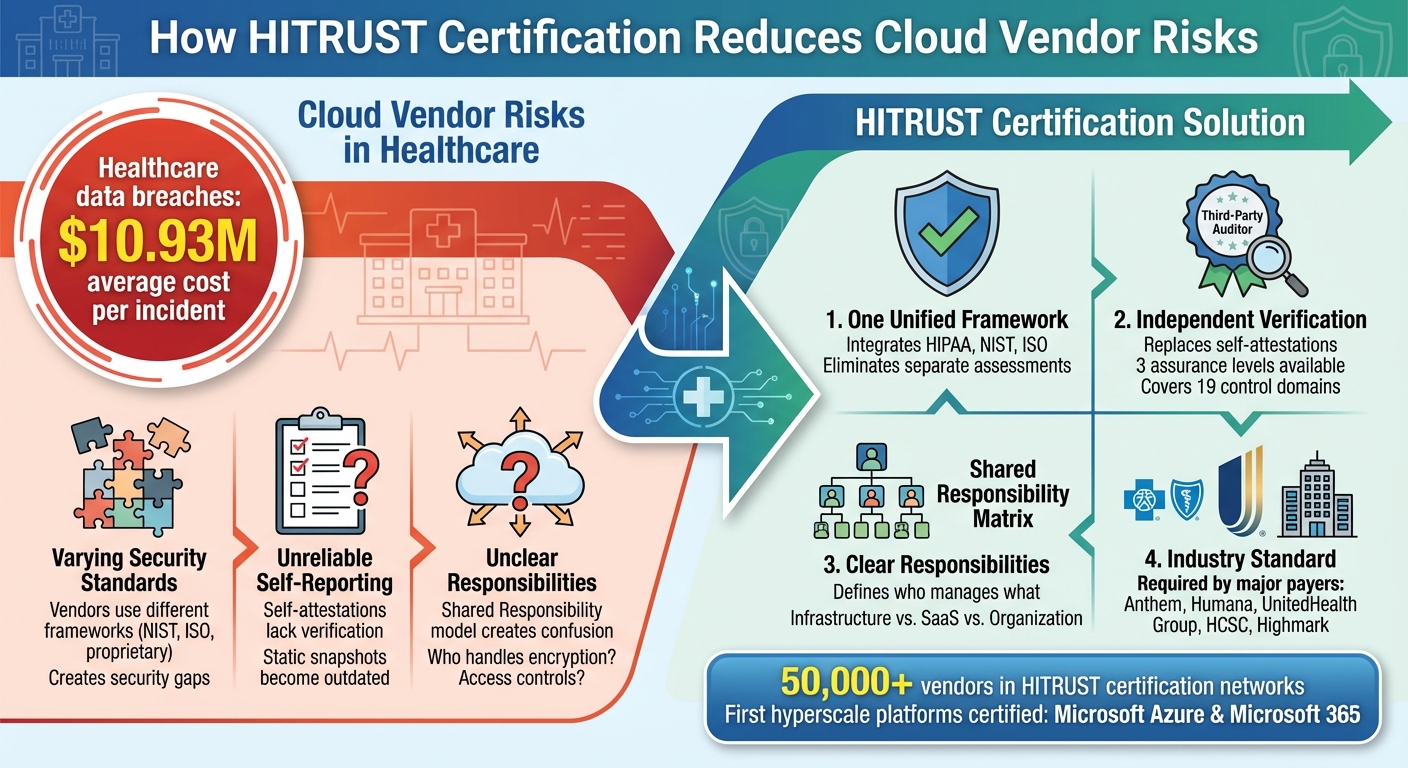
HITRUST certification simplifies managing cloud vendor risks in healthcare. With rising data breach costs - averaging $10.93M per incident in healthcare - organizations need stronger safeguards for sensitive patient information. HITRUST provides a unified framework that integrates multiple regulations like HIPAA, NIST, and ISO, ensuring vendors meet stringent security standards.
Key benefits include:
- Independent Verification: Replaces unreliable self-attestations with third-party audits.
- Streamlined Compliance: One framework covers multiple regulatory requirements, saving time.
- Clear Roles: Defines security responsibilities in cloud environments, reducing confusion.
- Stronger Vendor Contracts: Incorporates HITRUST requirements into agreements for better accountability.
Healthcare providers like Anthem and Humana now require HITRUST certification for vendors, making it a critical tool for reducing risks and maintaining compliance.
How HITRUST Certification Reduces Cloud Vendor Risks in Healthcare
Main Risks When Working with Cloud Vendors
HITRUST's structured approach sheds light on the risks tied to cloud environments and how standardized frameworks aim to tackle them.
Varying Security Standards Across Vendors
Cloud vendors come with their own security playbooks - some align with NIST, others with ISO, while a few rely on proprietary methods that may not suit healthcare's specific needs. This mix-and-match approach can lead to inconsistent security measures across vendors. For example, one vendor might focus on securing data at rest but neglect data in transit, while another does the reverse. This forces healthcare organizations to cobble together a patchwork of protections, often leaving gaps in critical areas like safeguarding patient data and meeting HIPAA requirements.
Problems with Vendor Self-Reporting
Vendor questionnaires and self-attestations often paint a rosy picture of security practices, emphasizing policies over proven, tested measures. Without independent audits or ongoing monitoring, these self-reports offer only a fleeting snapshot of a vendor's security posture. This static approach can quickly become outdated, leaving organizations in the dark about whether a vendor's protections are effective. These gaps in self-reporting also blur the lines of shared security responsibilities, making it harder to identify who is accountable for specific risks.
Unclear Security Responsibilities in Cloud Services
The shared responsibility model in cloud setups often leads to confusion about who manages what. Is the infrastructure provider responsible for encryption? Does the SaaS vendor handle access controls? Or does the healthcare organization take the lead? Without clear boundaries, these unanswered questions create vulnerabilities. Standards from leading cloud services emphasize the importance of clearly defining roles to avoid these security gaps and protect sensitive patient data.
How HITRUST Certification Reduces Cloud Vendor Risks

HITRUST certification streamlines the often fragmented approach to security compliance by providing a unified framework tailored specifically to the healthcare industry's needs.
One Framework for Multiple Compliance Requirements
HITRUST CSF brings together various security and privacy domains - like access control, endpoint security, mobile device security, and incident management - into one certifiable framework. This framework aligns directly with key regulations such as HIPAA, NIST, and ISO, making it easier for healthcare organizations to meet their compliance requirements [2]. Instead of conducting separate assessments for each regulation, organizations can rely on this consolidated framework, which simplifies the evaluation of multiple vendors. By eliminating the need to cross-check different security frameworks, HITRUST CSF ensures a more streamlined and efficient process for verifying whether vendors meet specific regulatory standards. It also establishes a solid foundation for independent validation of security measures.
Third-Party Verification of Security Controls
HITRUST replaces self-attestations with independent assessments, ensuring that critical security controls are thoroughly verified. These assessments cover key areas like access control, endpoint and network protection, encryption, logging and monitoring, incident response, business continuity/disaster recovery, and physical/environmental security [4][3]. For cloud vendors, this means demonstrating compliance with measures such as multi-factor authentication, encryption of PHI, data segregation for tenants, continuous vulnerability management, reliable backups, recovery time objectives, and well-documented incident communication processes [4][2].
HITRUST offers three levels of assurance, allowing organizations to adjust the depth of verification based on vendor risk and the sensitivity of the data involved [2]. Leading U.S. payers, including Anthem, HCSC, Highmark, Humana, and UnitedHealth Group, now require most of their vendors to achieve HITRUST certification, signaling that independent verification has become a standard expectation rather than an added bonus [3]. This level of scrutiny enhances accountability and ensures clearer definitions of security roles, as outlined in the next section.
Defining Security Responsibilities in Cloud Environments
HITRUST's framework doesn't just unify and verify security measures; it also clarifies responsibilities through its Shared Responsibility Matrix. This tool explicitly defines whether specific protections - like encryption, access controls, patch management, or incident response - fall under the purview of the infrastructure provider, the SaaS vendor, or the healthcare organization. Such clarity is crucial for avoiding misunderstandings, especially when organizations mistakenly assume their cloud vendor is managing a security task that actually falls within their own responsibilities.
During contract negotiations and implementation, healthcare organizations can use HITRUST's guidance to clearly document which party is accountable for each control. This creates a detailed audit trail and minimizes the risk of security gaps being overlooked, ensuring a more secure and transparent partnership.
sbb-itb-535baee
How to Use HITRUST in Vendor Risk Management
Adding HITRUST Requirements to Vendor Contracts
Incorporating HITRUST into your procurement policies starts with updating agreements like Business Associate Agreements (BAAs) and Master Service Agreements (MSAs). These updates should specify the required HITRUST certification level based on the vendor's role. For example, vendors managing lower-risk tasks might only need a self-assessment, while those handling medium-risk operations should undergo validated assessments. High-risk vendors, especially those processing sensitive patient information, should meet full HITRUST certification standards.
For cloud services such as Microsoft Azure and Microsoft 365 - the first hyperscale cloud platforms to achieve HITRUST CSF certification - you can directly reference their certification scope in your contracts. This ensures clarity about which security responsibilities fall under the provider and which remain with your organization [2]. By addressing these details upfront, you eliminate confusion and set enforceable security expectations from the beginning. This clarity also simplifies vendor assessments down the line.
Simplifying Vendor Assessments with HITRUST
Accepting HITRUST certification can drastically reduce the time and effort required for vendor assessments. Instead of relying on lengthy questionnaires, you can use HITRUST documentation as the sole proof of a vendor's security measures. This shift not only saves time but also allows your team to focus on managing actual risks rather than chasing paperwork.
By streamlining the assessment process, your team can allocate resources more effectively. Once a vendor's certification is verified, the focus shifts to maintaining efficient data management for ongoing risk oversight.
Managing HITRUST Data with Risk Management Platforms
Keeping track of multiple HITRUST certifications manually is a daunting task. That's where centralized platforms come into play. Tools like Censinet RiskOps™ simplify the process by consolidating HITRUST certification data with overall vendor risk information. This platform offers a streamlined way to store, monitor, and act on security documentation.
With over 50,000 vendors in its network, Censinet Connect™ facilitates seamless sharing of HITRUST certifications and other security documentation. This feature accelerates due diligence, particularly early in the vendor evaluation process.
James Case, VP & CISO of Baptist Health, shared his experience: "Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with." [1]
Platforms like this not only simplify data management but also foster collaboration, making vendor risk management more efficient and effective.
Conclusion
HITRUST certification does more than just reduce vendor risks - it plays a key role in strengthening security governance across the healthcare industry.
Key Advantages of HITRUST for Healthcare Organizations
HITRUST certification offers an independent review of security measures, ensuring the protection of PHI across 19 control domains [2]. This third-party validation provides healthcare organizations with a trusted standard for maintaining compliance and safeguarding sensitive information.
One standout benefit is how it simplifies vendor assessments. With HITRUST certification becoming a requirement for many leading health plans, the time spent on evaluations is significantly reduced [3]. This allows security teams to concentrate on addressing real risks instead of being bogged down by administrative tasks. Additionally, partnering with HITRUST-certified providers like Azure or Microsoft 365 can make contract negotiations smoother. By referencing their certification scope, organizations can expedite approvals and clearly outline security responsibilities [2].
Strengthening Vendor Relationships with HITRUST
HITRUST certification doesn’t just enhance security - it also improves vendor relationships. Its three assurance levels - self-assessment, validated, and CSF-certified - enable organizations to tailor requirements based on risk. Low-risk vendors face less stringent demands, while high-risk vendors handling sensitive PHI must meet full certification standards [2].
This approach fosters transparency and trust. Vendors and healthcare organizations gain a shared understanding of security roles, reducing confusion and potential conflicts. Tools like Censinet RiskOps™ further simplify this process by centralizing HITRUST certification data alongside broader vendor risk information. This makes it easier to track compliance and manage documentation, paving the way for stronger partnerships built on shared security goals. The result? A more streamlined, secure framework for protecting patient data and managing vendor relationships effectively.
FAQs
How does HITRUST certification help healthcare organizations manage cloud vendor risks?
HITRUST certification offers healthcare organizations a structured way to handle cloud vendor risks by establishing a clear framework for security and compliance. It ensures that vendors meet strict standards for safeguarding sensitive patient information and complying with regulations such as HIPAA.
With HITRUST in place, healthcare providers can better evaluate and oversee third-party vendors, minimizing risks and strengthening their cybersecurity defenses. This certification builds confidence and simplifies the risk management process, helping to keep vital systems and data protected.
Why is HITRUST certification a more trustworthy option than vendor self-attestations?
HITRUST certification stands out as a dependable choice because it involves an independent, third-party assessment to confirm adherence to rigorous security and privacy standards. This process ensures an objective and consistent evaluation, minimizing the chances of exaggerated or inaccurate claims.
In contrast to self-attestations, which depend entirely on a vendor's internal reporting, HITRUST certification offers healthcare organizations greater assurance in a vendor's security measures. This becomes especially crucial when handling sensitive data, such as patient records or Protected Health Information (PHI), where trust and accountability are non-negotiable.
How does HITRUST certification help define security roles in cloud environments?
HITRUST certification provides healthcare organizations and cloud vendors with a clear, standardized framework for defining security roles. This framework lays out specific controls, responsibilities, and expectations, making it easier for both parties to understand what’s required to safeguard sensitive data.
By following HITRUST standards, organizations can minimize confusion, enhance teamwork, and bolster security measures in cloud environments - especially when handling patient data or other essential information.


