HITRUST Certification: Third-Party Risk Assessment Role
Post Summary
Healthcare organizations face a tough challenge: managing vendor risks while protecting patient data and complying with regulations like HIPAA. HITRUST certification stands out by integrating various healthcare regulations into a single framework, simplifying compliance and vendor risk management. Here's how HITRUST compares to other frameworks like HIPAA, SOC 2, and ISO 27001:
- HITRUST: Tailored for healthcare, it includes detailed controls for third-party risk management and accepts certifications like SOC 2 or ISO 27001 as evidence. It’s rigorous but resource-intensive.
- HIPAA: Sets a regulatory baseline with Business Associate Agreements (BAAs) and risk management requirements but lacks specific vendor assessment methods.
- SOC 2: Offers independent audits with flexible controls but isn’t healthcare-specific, requiring additional effort to align with healthcare needs.
- ISO 27001: Focuses on a risk-based approach to security management but needs supplementary healthcare-specific standards like HIPAA or HITRUST.
For high-risk vendors handling sensitive patient data, HITRUST is often the best option. A layered approach - using HIPAA as the foundation and combining HITRUST, SOC 2, or ISO 27001 based on vendor risk - ensures thorough risk management. Automated tools like Censinet RiskOps™ can streamline these processes.
1. HITRUST

HITRUST weaves third-party risk management directly into its certification process, making vendor risk evaluations a core requirement for healthcare organizations. Instead of treating vendor assessments as an optional step, this framework ensures they are integral to maintaining compliance.
The evaluation process is tailored to the level of risk a vendor poses. For low-risk partners, self-assessments might suffice, while vendors dealing with sensitive patient data or critical infrastructure undergo more detailed reviews. This ensures that the scrutiny matches the potential risk exposure.
As part of a HITRUST assessment, organizations must demonstrate effective third-party risk management practices. For instance, HITRUST often accepts existing certifications like SOC 2 reports or ISO 27001 certificates as evidence. This reduces the need for redundant audits while still maintaining a high level of assurance. The framework's adaptability allows organizations to scale assessments based on their size and operations.
How this is implemented can vary widely. Smaller healthcare facilities may rely on manual questionnaires to assess vendors, while larger systems often use tools like Censinet RiskOps™ to automate processes and centralize vendor risk data.
HITRUST standards cover a broad spectrum of vendors. Electronic health record providers face stringent assessments, telehealth platforms must show they can securely handle communication and data, and vendors in areas like medical devices or supply chains are evaluated when dealing with PHI or connecting to clinical networks. This ensures that all parties involved maintain robust security and compliance practices.
2. HIPAA
HIPAA takes a regulatory stance on managing third-party risks. Instead of providing a certification, it establishes a set of requirements that covered entities must adhere to. At its core lies the Business Associate Agreement (BAA) - a legal contract that compels vendors handling protected health information (PHI) to implement proper safeguards. However, signing a BAA is just the starting point. Beyond legal agreements, HIPAA emphasizes the need for thorough and documented risk management practices.
Healthcare organizations are required to conduct risk analyses and manage risks, including those tied to third-party vendors. This involves tracing the flow of PHI to external parties, identifying vulnerabilities in those relationships, and documenting steps to address those risks. The Office for Civil Rights (OCR) has consistently reinforced this through enforcement actions, making it clear that simply having BAAs on file is insufficient. Organizations must actively oversee and evaluate their vendors to demonstrate due diligence.
Proper documentation is a cornerstone of HIPAA compliance. This includes maintaining an updated list of business associates and subcontractors handling PHI, ensuring BAAs contain key clauses (like breach notification and termination provisions), and keeping records of vendor risk analyses and ongoing monitoring. For example, in 2018, Anthem, Inc. paid $16 million to OCR after a cyberattack exposed PHI for nearly 79 million individuals. OCR's investigation highlighted Anthem's failure to conduct adequate risk analyses and manage vendor and system risks effectively. Such incidents underscore the importance of a lifecycle-based approach to managing vendor relationships.
HIPAA's flexibility allows organizations to tailor their compliance efforts based on operational complexity, though this can sometimes create inconsistencies. Vendors like cloud-based EHR providers, telehealth platforms, and networked medical devices all require BAAs and thorough security evaluations. Particular attention should be paid to encryption, access controls, and network segmentation. Surveys repeatedly indicate that over half of healthcare data breaches involve third parties or business associates, making vendor oversight a critical operational priority - not just a regulatory formality.
Unlike HITRUST, which offers a consolidated certification process, HIPAA requires ongoing, lifecycle-focused vendor assessments. To simplify this, healthcare organizations can incorporate risk management into every stage of the vendor lifecycle - from procurement to contracting, onboarding, and continuous oversight. Tools like Censinet RiskOps™ help automate these processes, reducing manual effort while ensuring compliance with OCR documentation standards.
Terry Grogan, CISO of Tower Health, shared that adopting Censinet RiskOps allowed them to perform "a lot more risk assessments" while cutting the required full-time employees (FTEs) from 5 to 2. This shift enabled 3 FTEs to return to their primary roles [1].
3. SOC 2
SOC 2 is an attestation, not a certification. It involves a CPA firm evaluating an organization's controls based on the AICPA standards. The resulting report addresses one or more Trust Services Criteria, with security being mandatory. Other criteria - availability, confidentiality, processing integrity, and privacy - are optional. Within these criteria, third-party risk management is addressed under vendor management and risk assessment controls. Organizations must show how they handle the identification, assessment, onboarding, monitoring, and offboarding of service providers that interact with in-scope systems. Similar to HITRUST and HIPAA, SOC 2 emphasizes strict vendor controls tailored to an organization's scope.
Auditors reviewing SOC 2 compliance expect a categorized vendor list that reflects data sensitivity, PHI access, and vendor criticality. They also look for policies governing the vendor lifecycle, contractual controls like BAAs (Business Associate Agreements) for healthcare entities, and evidence of ongoing monitoring. This could include periodic risk assessments, performance evaluations, and security attestations. A 2023 Ponemon Institute study revealed that 54% of organizations experienced a data breach caused by a third party in the previous year, highlighting why vendor-risk controls receive such close attention from auditors.
Many organizations now view SOC 2 Type 2 as a baseline standard for IT and cloud vendors managing PHI. They often layer additional controls to meet HIPAA-specific requirements. For example, when working with cloud EHR vendors, organizations should review the SOC 2 Type 2 report (focused on Security, Availability, and Confidentiality), confirm that PHI controls are included, enforce a BAA with breach notification clauses, and conduct regular reviews. For connected medical device manufacturers, due diligence should extend to areas like network security, patch management, vulnerability management, and adherence to FDA cybersecurity guidance.
SOC 2 offers flexibility, allowing management to define the scope of controls and vendor inclusion. Larger ecosystems naturally require more expansive vendor-risk controls and evidence. While SOC 2 isn't designed specifically for healthcare, many healthcare organizations use SOC 2 Type 2 reports as a prerequisite for SaaS and cloud vendors integrating with PHI or clinical systems. These reports are often supplemented with continuous monitoring tools, such as security ratings and automated questionnaires, to maintain oversight beyond the point-in-time attestation.
Unlike HITRUST's rigid framework, SOC 2 provides principles-based guidance that organizations can adapt to their needs. Healthcare organizations often incorporate vendors' SOC 2 reports into their HITRUST certification process but must still demonstrate how they assess and rely on those reports. Tools like Censinet RiskOps™ can simplify this process by automating vendor inventory management, standardizing security questionnaires aligned with SOC 2 and HIPAA, and tracking attestation expiration dates - reducing manual work and ensuring auditors receive the necessary documentation.
sbb-itb-535baee
4. ISO 27001
ISO 27001 is an international standard for information security management systems (ISMS) that takes a different approach compared to HITRUST. Instead of outlining specific controls, it requires organizations to identify and address risks associated with external parties using a structured management system. Managing third-party risks is a key aspect of ISO 27001, woven into its core risk assessment requirements (clauses 4–6) and supported by Annex A controls focused on supplier relationships. The 2022 update to ISO 27001 strengthened this focus by adding explicit controls for cloud services and more detailed supplier relationship requirements compared to the 2013 version. This structured approach helps organizations align vendor evaluations with broader compliance efforts.
To achieve certification, organizations must provide auditors with clear evidence of supplier risk management. This includes formally integrating supplier risks into the ISMS risk assessment and treatment plan. Key requirements include maintaining a categorized supplier inventory, conducting thorough due diligence (e.g., security questionnaires, SOC 2 or HITRUST reports), incorporating contractual security clauses, and documenting ongoing monitoring efforts.
In practice, ISO 27001 offers flexibility, allowing organizations to adopt a risk-based approach to vendor assessments. For example, a large U.S. health system might classify only 5–15% of its vendors as high risk, applying ISO/HITRUST-style assessments to these vendors while using lighter reviews for lower-risk ones. This tiered approach, supported by standardized questionnaires, helps manage the challenges of overseeing thousands of suppliers. Tools like Censinet RiskOps™ further simplify the process by automating vendor data capture, assessment, and tracking.
For U.S. healthcare organizations, ISO 27001 acts as a foundation that must be combined with HIPAA and HITRUST-specific requirements. This layered approach strengthens vendor risk management. For instance, when assessing a cloud-hosted EHR provider, organizations should apply Annex A controls such as multi-factor authentication, role-based access, robust backup and disaster recovery plans tailored to clinical needs, PHI encryption, and breach notification within 60 days. Similarly, evaluations of connected medical device manufacturers should include secure configuration baselines, patch management protocols, network segmentation strategies, and clear procedures for handling urgent cybersecurity advisories.
ISO 27001 also complements other vendor risk frameworks, making it a valuable tool alongside HITRUST. Many large healthcare organizations and payers now accept ISO 27001 or HITRUST certification as equivalent evidence of a vendor's security maturity. According to a 2022 ISMS.online analysis, global ISO/IEC 27001 certifications increased by over 20% year-over-year, highlighting the growing reliance on this standard for third-party assurance. Its flexibility allows organizations to incorporate various forms of vendor assurance - such as SOC 2, HITRUST, or ISO 27001 certification - into their due diligence processes.
Advantages and Disadvantages
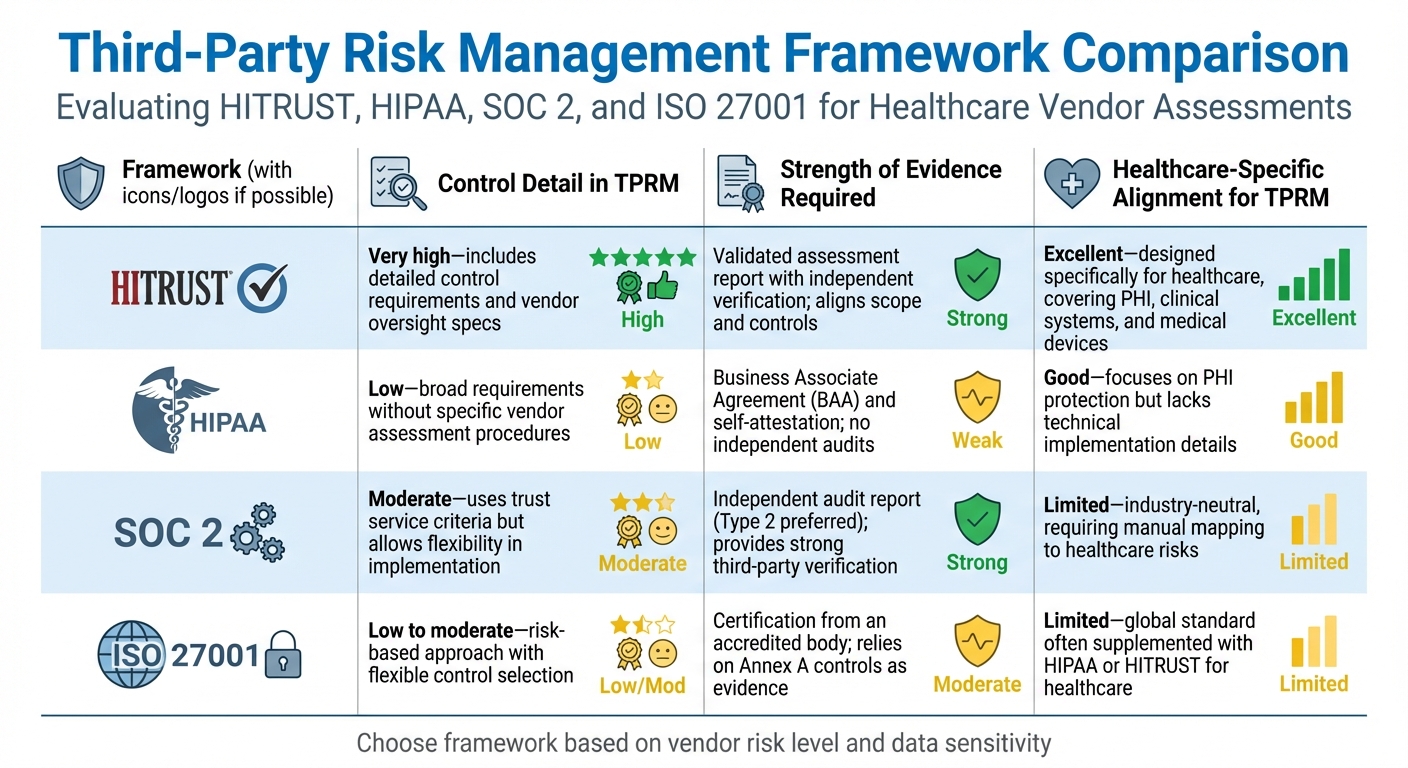
HITRUST vs HIPAA vs SOC 2 vs ISO 27001 Third-Party Risk Management Comparison
HITRUST offers a structured framework with detailed controls tailored to healthcare, making it highly effective for vendor assessments. However, it requires significant time and financial investment. HIPAA, on the other hand, provides a regulatory baseline but lacks specific assessment methods. SOC 2 delivers robust independent verification but isn't healthcare-specific, requiring extra effort to align with industry needs. ISO 27001's risk-based approach allows flexibility, but without strict internal standards, evaluations can vary.
Here's a side-by-side comparison of how these frameworks address key aspects of third-party risk management:
| Framework | Control Detail in TPRM | Strength of Evidence Required | Healthcare-Specific Alignment for TPRM |
|---|---|---|---|
| HITRUST | Very high - includes detailed control requirements and vendor oversight specs | Validated assessment report with independent verification; aligns scope and controls | Excellent - designed specifically for healthcare, covering PHI, clinical systems, and medical devices |
| HIPAA | Low - broad requirements without specific vendor assessment procedures | Business Associate Agreement (BAA) and self-attestation; no independent audits | Good - focuses on PHI protection but lacks technical implementation details |
| SOC 2 | Moderate - uses trust service criteria but allows flexibility in implementation | Independent audit report (Type 2 preferred); provides strong third-party verification | Limited - industry-neutral, requiring manual mapping to healthcare risks |
| ISO 27001 | Low to moderate - risk-based approach with flexible control selection | Certification from an accredited body; relies on Annex A controls as evidence | Limited - global standard often supplemented with HIPAA or HITRUST for healthcare |
This comparison highlights the importance of tailoring vendor risk strategies to align with organizational needs.
Many healthcare organizations adopt a layered approach to vendor risk management. Typically, HIPAA serves as the regulatory foundation. For high-risk vendors, HITRUST or ISO 27001 certifications are often accepted as proof of security maturity. SOC 2 reports are commonly used for cloud service providers. This layered strategy helps balance thoroughness with operational efficiency.
As Matt Christensen, Sr. Director GRC at Intermountain Health, explains: "Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare." [1]
For organizations aiming for HITRUST certification, aligning these frameworks can enhance both compliance and operational workflows. Decisions should consider the organization's specific risk profile, the sensitivity of vendor-handled data, and available resources. Vendors managing critical clinical systems or sensitive PHI often require the rigor of HITRUST, while lower-risk vendors may suffice with SOC 2 reports or ISO 27001 certifications, supplemented by targeted healthcare-specific evaluations. Tools like Censinet RiskOps™ simplify this process by automating assessments, reducing the resource burden for comprehensive third-party risk management.
Conclusion
Each framework brings distinct strengths to third-party risk management. HIPAA establishes a regulatory foundation but offers limited guidance on assessment methods. SOC 2 provides auditor-verified controls, though the depth of these controls can vary. ISO 27001 emphasizes a risk management system but leaves implementation details to the organization. Meanwhile, HITRUST stands out with its detailed, healthcare-specific controls and validated vendor oversight.
For healthcare organizations working with high-risk vendors - those managing sensitive patient data, critical clinical systems, or medical devices - HITRUST certification is often the best choice due to its rigorous and tailored controls. On the other hand, lower-risk vendors, like providers of general office software, may only require a SOC 2 report or ISO 27001 certification, supplemented with healthcare-specific questions to ensure compliance.
A layered strategy works well: use HIPAA as the baseline, HITRUST or ISO 27001 for high-risk vendors, and SOC 2 for cloud service providers. This approach ensures thoroughness without sacrificing operational efficiency. Tools like Censinet RiskOps™ simplify this process by centralizing vendor assessments and compliance tracking in a single healthcare-focused platform.
FAQs
How does HITRUST certification support third-party risk management in healthcare?
HITRUST certification plays a key role in improving third-party risk management by providing a standardized framework specifically designed to address the security and compliance needs of the healthcare sector. It enables organizations to evaluate, verify, and continuously monitor the security measures of their vendors, ensuring they adhere to strict data protection and compliance requirements.
For healthcare organizations, adopting HITRUST means they can more effectively pinpoint and address risks associated with sensitive data, including patient records and medical systems. This not only boosts cybersecurity but also strengthens the organization’s ability to maintain smooth and secure operations.
Why is it important to use a layered approach for managing vendor risks in healthcare?
A layered approach to managing vendor risks in healthcare is essential because it creates multiple defenses, significantly lowering the risk of a single weak spot causing a failure. By tackling vulnerabilities at various levels, this strategy helps protect sensitive patient information, clinical systems, and medical devices.
This approach is particularly effective in healthcare's intricate landscape, where meeting compliance standards like HITRUST demands strong risk management practices. If one safeguard falters, others are ready to step in, reducing the likelihood of breaches and supporting stronger cybersecurity and operational stability.
How does Censinet RiskOps™ simplify third-party risk assessments for HITRUST certification?
Censinet RiskOps™ streamlines the process of third-party risk assessments by automating how vendor data is collected and analyzed. This automation not only saves time but also cuts down on the manual work involved. With real-time insights, organizations can quickly identify and address vulnerabilities, ensuring they stay ahead of risks while meeting compliance standards like HITRUST.
The platform also offers continuous monitoring, keeping risk assessments current as security and compliance needs evolve. This is especially critical for healthcare organizations managing risks tied to sensitive data, medical devices, supply chains, and other key areas.


